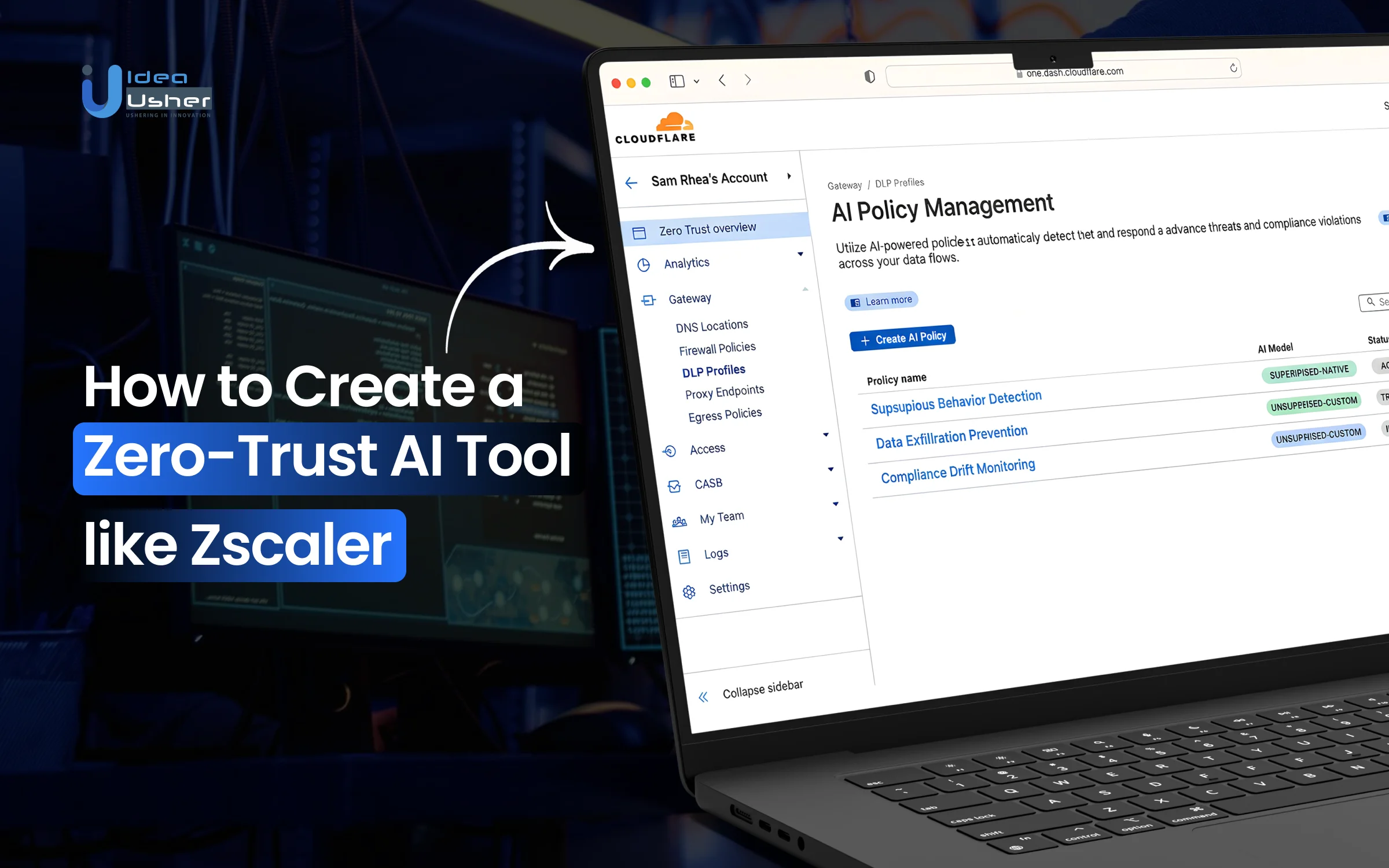
As workforces go remote and systems move to the cloud, the traditional secure network perimeter has disappeared. Users, devices, and applications connect from everywhere, making trust-based security outdated. This is the reason why organizations are adopting Zscaler-like zero-trust AI tools that assume nothing is safe by default, continuously verifying every user, request, and connection to ensure robust, modern network security.
AI-powered zero-trust security emphasizes context, behavior, and continuous risk assessment over static rules. By analyzing identity signals, device posture, network activity, and usage patterns in real time, it detects threats early, dynamically restricts access, reduces false positives, adapts to new attacks, and enforces policies without disrupting users or operations.
In this blog, we’ll explore how to build a zero-trust AI tool similar to Zscaler, the core features it requires, and the technology stack behind it. As we have helped numerous enterprises to build their AI solutions, IdeaUsher has the expertise to create a scalable, intelligent zero-trust security solution.

What is a Zero-Trust AI Tool, ZScaler?
Zscaler’s Zero-Trust AI Tool is a cloud cybersecurity platform that uses the Zero Trust security model (never trust, always verify) with AI analytics to protect users, applications, data, and AI in real time. It automates threat detection, access, and data protection, helping enterprises secure distributed networks and AI workloads more effectively than traditional firewall/VPN systems.
It’s popular because it delivers cloud-native, scalable Zero Trust security that replaces legacy VPNs and firewalls, uses real-time AI-driven threat detection with automated access control, supports hybrid work and cloud apps, and hides applications from the internet to reduce attack surfaces and prevent lateral movement without IP-based access.
- Proxy-based TLS/SSL inspection at scale: Zscaler’s cloud-native proxy inspects all encrypted traffic in real time and brokers identity- and policy-aware connections between users and apps, improving security granularity and preventing lateral threat movement.
- Unified CASB + DLP enforcement: Integrated cloud access security broker (CASB) and data loss prevention (DLP) provide API-level visibility and control across SaaS apps, identifying and protecting sensitive data.
- Multitenant, globally distributed proxy cloud: The Zero Trust Exchange runs on a multitenant, globally distributed architecture, enabling full TLS/SSL inspection and policy enforcement at scale without bottlenecks.
- Fine-grained microsegmentation: Zero Trust microsegmentation enforces application- and session-level access controls, eliminating broad network access and drastically reducing lateral movement paths for attackers.
A. Business Model: How Zscaler Operates
Zscaler operates a cloud-native SaaS business model that delivers Zero Trust security as a subscription service, replacing legacy network appliances with a scalable, AI-enabled cybersecurity platform.
- Cloud-delivered SaaS platform: Security services are provided entirely through Zscaler’s global cloud, eliminating hardware deployments.
- Zero Trust architecture: Uses identity-based, least-privilege access to secure users, apps, and data across distributed environments.
- Modular platform expansion: Customers can add capabilities (ZIA, ZPA, ZDX, workload protection, AI security layers) as their needs grow.
- High-engagement usage model: Continuous traffic inspection and policy enforcement create strong customer stickiness and recurring usage.
- Ecosystem-integrated: Deep integrations with identity providers, cloud platforms, and endpoint tools increase platform dependence.
- Global scalability: Multitenant cloud enables consistent performance and security for enterprises of all sizes without infrastructure overhead.
B. Revenue Model: How Zscaler Generates Revenue
Zscaler’s revenue comes primarily from recurring subscription contracts for access to its cloud Zero Trust security offerings. These are typically structured as annual or multi-year agreements and billed based on metrics such as:
- Number of users/licenses
- Features or security modules selected
- Service tier or bundle level
Revenue highlights:
- Subscription revenue accounts for the vast majority (≈97%) of total revenue, driven by SaaS access and support services.
- Professional services, including implementation support, training, and consulting, contribute a small supplementary share.
- Annual Recurring Revenue (ARR) is a key metric used by investors and management, reflecting predictable, high-visibility recurring revenue; Zscaler has surpassed $3 billion in ARR.
How a Zero-Trust AI Tool Works?
A Zero-Trust AI tool continuously verifies identities, monitors network activity, and enforces least-privilege access, enhancing security, reducing threats, and providing enterprises with proactive, intelligent threat detection capabilities.
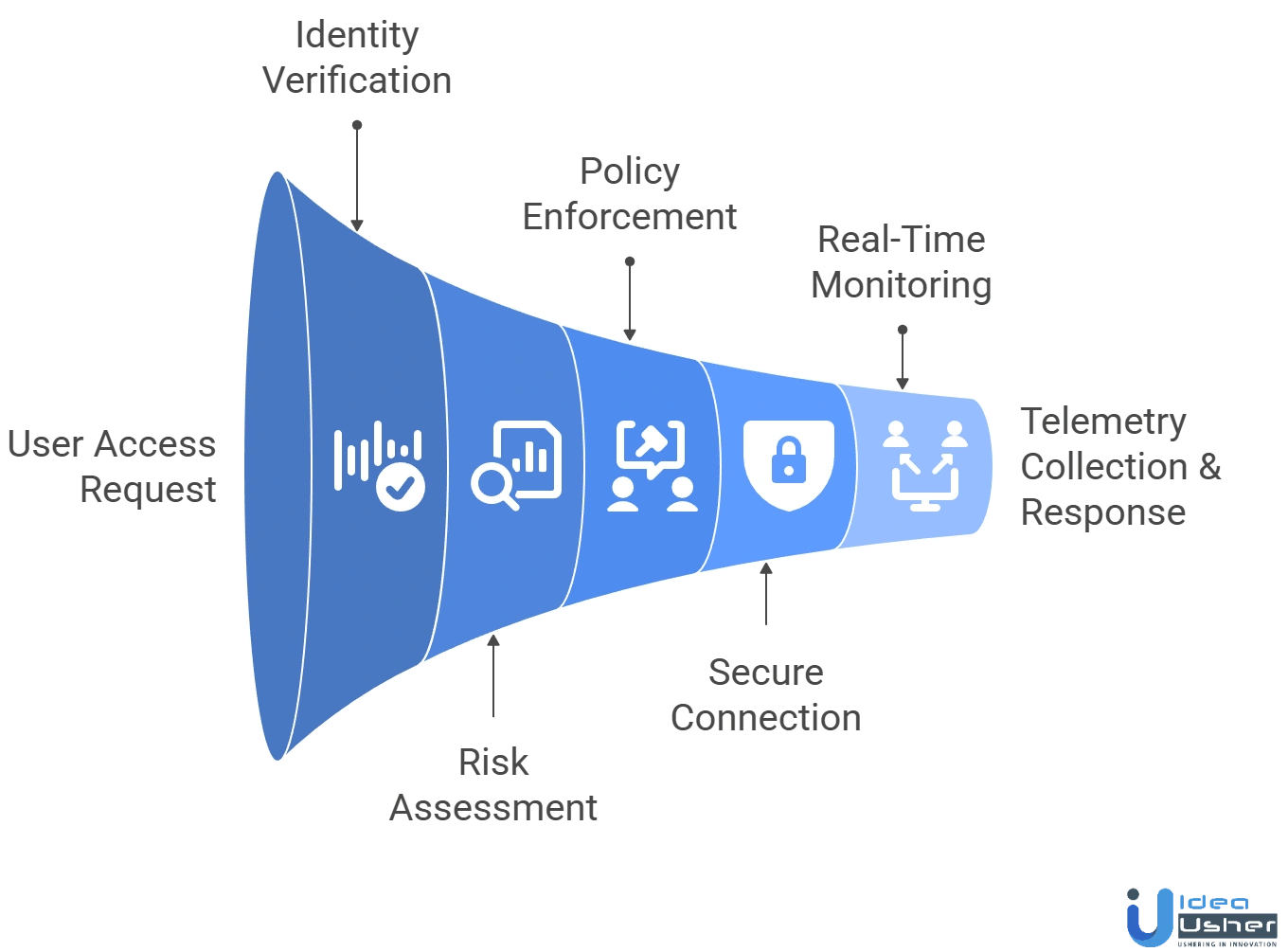
1. Identity Verification & Device Trust Evaluation
The platform verifies user identity via federation, MFA, SSO, and checks device compliance and health signals. This ensures only trusted, authenticated users and devices access the system, establishing zero trust.
2. Context Collection & AI Risk Scoring
AI analyzes behavioral patterns, location, usage history and CASB visibility, using behavioral baselining and AI governance to assess risk. These insights inform access control decisions before application or data interaction.
3. Policy Evaluation & Access Decision
Zero Trust policies use adaptive access, identity signals and segmentation to decide permissions. DLP classifiers and CASB rules evaluate data sensitivity and SaaS behaviors, ensuring users get only the minimum required access.
4. Secure User-to-Application Connection
The platform creates an encrypted path via inspection engines and connectors. Micro segmentation blocks network exposure, limiting access to approved apps, reducing lateral movement risks, and enhancing internal environment visibility.
5. Real-Time Policy Adjustments
During the session, AI analyzes telemetry, anomalies, and data interactions. DLP engines, CASB monitors, and scoring models adjust permissions or revoke access as behavior shifts or threats increase risk.
6. Logging, Telemetry Collection & Threat Response
The platform logs all events and audits compliance. Telemetry helps refine AI models, while threat engines trigger automated responses like isolation or segmentation when malicious patterns or unauthorized data actions are detected.
Core Principles Behind Zero-Trust Architecture
Zero-trust architecture enforces strict identity verification and least-privilege access across networks. Understanding its core principles guides platform design, ensuring security, compliance, and resilience in modern enterprise environments.
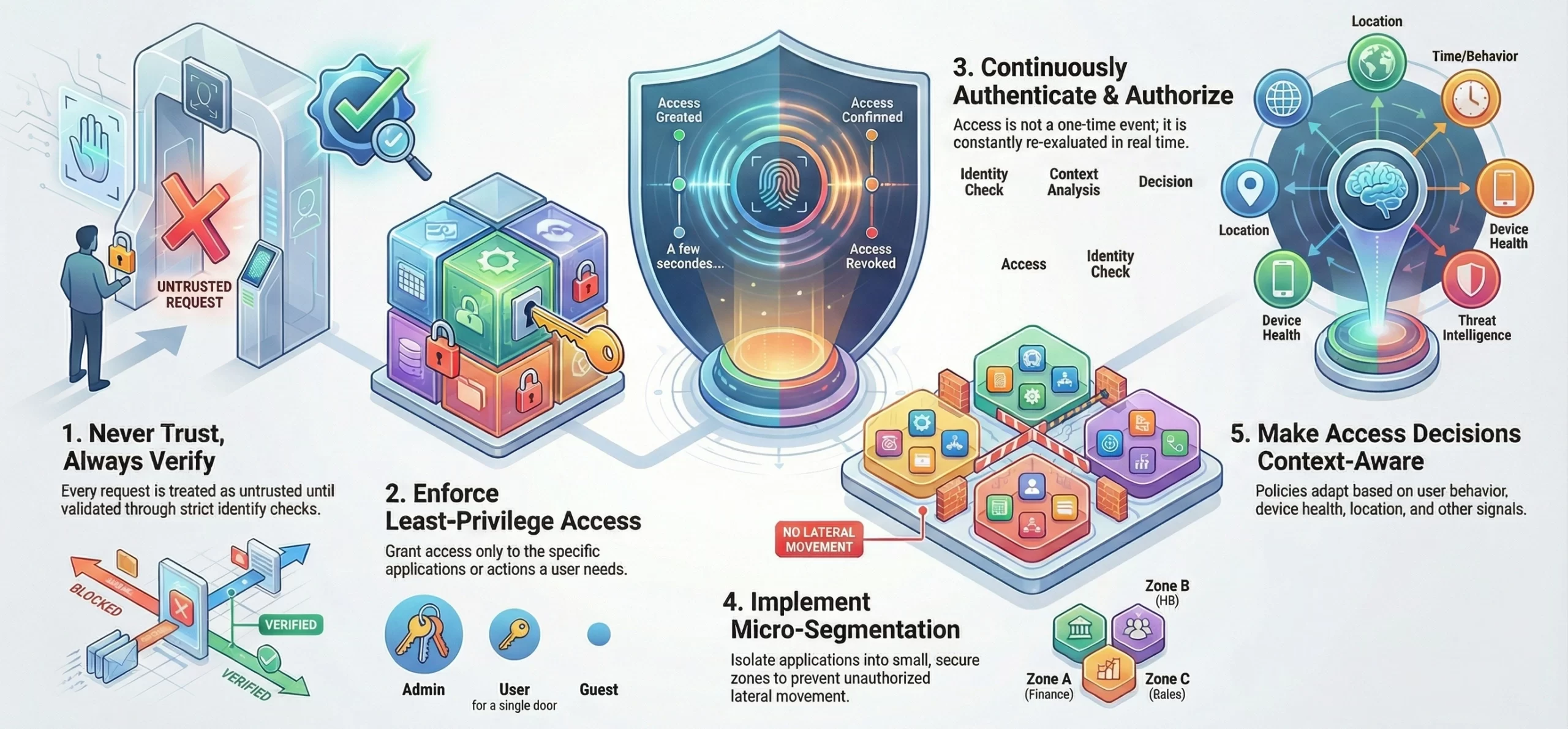
1. Never Trust, Always Verify
This principle shapes the platform so every request is treated as untrusted until validated. The system performs identity checks, device posture evaluation and session-level verification before allowing any interaction. This forces the platform to operate with strict verification checkpoints throughout the access workflow.
2. Least-Privilege Access
Platform design limits access to exactly what a user or workload needs. Permissions are not network-wide but scoped to specific applications or actions. This requires finely tuned policy engines, granular entitlement structures and controlled pathways that prevent unnecessary exposure to internal assets.
3. Continuous Authentication & Authorization
Access is not granted once and forgotten. The platform continually reassesses trust signals like behavior changes, device risk or unusual context. This demands real-time telemetry processing, adaptive policy reevaluation and session-level monitoring to ensure access remains appropriate at every moment.
4. Micro-Segmentation
Instead of broad network zones, the platform isolates applications and workloads into smaller, independent segments. Each segment has its own access rules and verification steps. This requires identity-based routing, application cloaking and segmented control planes that minimize lateral movement opportunities.
5. Context-Aware Access Decisions
Access decisions are informed by factors such as user behavior, device health, location and activity patterns. This pushes the platform to integrate contextual data sources, implement AI-driven risk scoring and build dynamic policies that shift in real time based on evolving conditions.
What 96% Organizational Support and 81% Adoption Plans Mean for Zero Trust AI Tools?
The global zero trust security market was valued at USD 34.26 billion in 2024 and is projected to reach USD 161.60 billion by 2034, growing at a CAGR of 16.78% from 2025 to 2034. Driven by widespread organizational commitment, zero trust has shifted from a forward-looking concept to a vital, actively adopted enterprise priority.
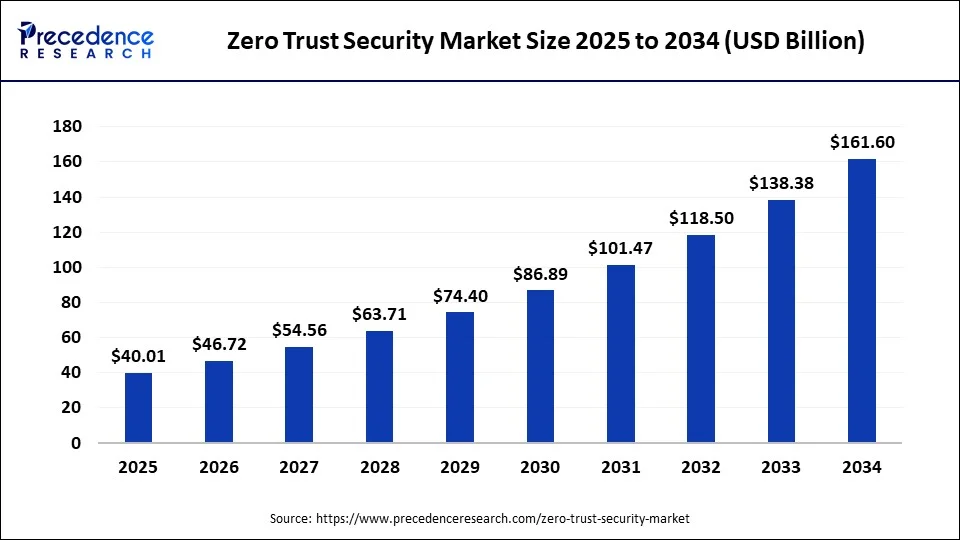
Zero trust has shifted from evaluation to active adoption, with 96% of organizations favoring the model and 81% planning implementation within 12 months. VPN replacement is accelerating, as 65% plan to retire legacy services this year, a 23% increase, creating strong demand for AI-powered zero-trust platforms.
A. The Zero Trust Adoption-Resilience Gap & Market Opportunity
Despite widespread zero trust adoption, many organizations struggle to achieve cyber resilience, revealing a significant market opportunity for solutions that deliver measurable security outcomes and operational effectiveness.
- PwC’s 2025 Global Digital Trust Insights shows only 2% achieved cyber resilience, despite 66% of tech leaders ranking cyber risk as top priority.
- A Deloitte survey found that 47% of organizations see aligning cybersecurity with regulatory requirements as a top driver for their cybersecurity strategy
- Government zero trust adoption at 72% versus 55% in the private sector provides powerful validation, reducing perceived risk and enabling your client to leverage federal trust to shorten enterprise sales cycles.
- Gartner forecasts 87% year over year ZTNA growth with sustained 51 % annual expansion, confirming the market is still in a high growth phase where innovative entrants can win share.
B. Trends in Zero Trust Spending, Adoption & Governance
Zero trust spending and adoption continue to rise as regulatory pressure, executive oversight, and evolving threat landscapes push organizations to prioritize governance-driven, enterprise-wide security strategies.
- PwC reports that 77% of organizations expect cyber budgets to rise, with 54% prioritizing secure cloud networking for zero trust.
- Meanwhile, 65% plan to replace VPNs this year, a 23% increase, with Gartner citing VPN replacement as the top ZTNA driver.
- Buyer priorities concentrate on secure cloud networking at 54% and identity and access management at 46%, defining the highest-demand capabilities shaping zero trust platform evaluations.
- Deloitte reports 48% of cyber-mature organizations review zero trust at the board level quarterly, with 26% doing so monthly, elevating it from an IT initiative to executive governance.

Use Cases of Zero-Trust AI Tools in Various Industries
Zero-Trust AI tools help organizations across industries secure sensitive data, monitor user activity, and prevent unauthorized access. Key use cases highlight enhanced protection, compliance, and operational efficiency in modern enterprise environments.
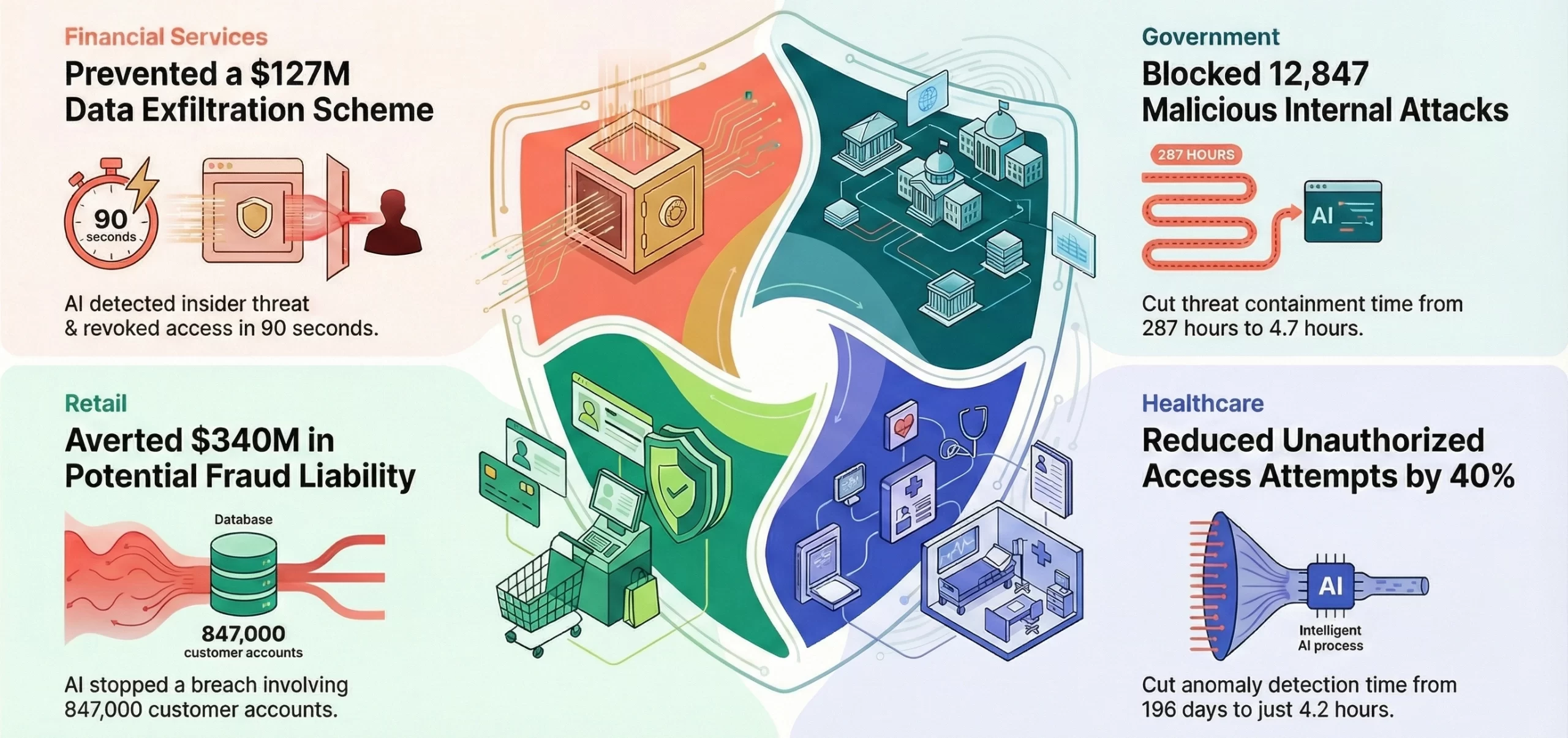
1. Healthcare
Hospitals and research institutions use Zero Trust AI to secure patient records, medical devices, and telehealth systems, restricting access by identity, device hygiene, and detecting abnormal queries.
Example: Cleveland Clinic implemented zero-trust architecture protecting 6 million patient records across 220 locations. AI monitors detected a 40% reduction in unauthorized access attempts, blocking 847 suspicious login attempts daily and reducing mean time to detect anomalies from 196 days to 4.2 hours.
2. Financial Services
Banks and fintech companies protect transactions and customer data, granting access only to authorized systems while AI monitors behavioral anomalies to prevent insider threats.
Example: Goldman Sachs uses zero-trust AI monitoring for 35,000 employees in 40+ countries. The system detected an analyst accessing 4,200 customer portfolios over 72 hours and 400% above normal. AI revoked access within 90 seconds, uncovering an attempted $127 million data exfiltration scheme.
3. Government and Public Sector
Agencies secure classified data, remote access, and inter-department communication, granting app-specific access and using AI to monitor device integrity and suspicious lateral movement.
Example: The U.S. Department of Defense deployed Zero Trust Reference Architecture across 3 million users and 15,000+ applications, blocking 12,847 lateral movement attempts in 2024, cutting mean threat containment from 287 hours to 4.7 hours while processing 2.3 billion events daily.
4. Retail and eCommerce
Retailers protect POS, inventory, and customer data, restricting staff access to defined modules while AI detects anomalies like bulk exports signaling potential fraud.
Example: Target implemented zero-trust AI across 1,931 stores, monitoring 1.8 billion annual transactions worth $109 billion. AI detected contractor access to 847,000 accounts during off-hours, preventing a breach with $340 million in potential fraud liability.
5. Technology & SaaS Providers
Tech companies secure development platforms, production APIs, and customer services, restricting engineer access to microservices while AI monitors irregular API calls or privilege escalations.
Example: Microsoft Azure uses zero-trust AI to protect 400+ million users across 60+ datacenter regions, processing 200+ trillion authentication requests annually. AI blocked privilege escalations in 847 Kubernetes clusters, securing 34,000 workloads and $4.7 billion in customer data within 6 seconds.
Key Features of a Zscaler-like Zero-Trust AI Tool
A Zscaler-like Zero-Trust AI Tool uses cloud-native architecture, AI threat detection, and policy-based controls to secure users, apps, and data. These key features improve visibility, reduce attack surfaces, and enforce real-time security across hybrid environments.

1. Zero Trust Identity-Driven Access
This feature verifies user, device and workload identity for every session and applies least privilege access using continuous authentication signals. Access routes directly to applications without exposing networks, which reduces attack surfaces and blocks lateral movement through enforced session-level isolation in distributed environments.
2. Cloud Native Global Platform
The platform operates across distributed cloud points to provide consistent security controls and low-latency traffic inspection close to users. Its multitenant architecture scales elastically, enabling unified policy enforcement for remote workforces, branch locations and cloud workloads through edge-based processing rather than physical appliances.
3. AI Enhanced Threat Detection
AI models analyze telemetry signals to identify anomalies, zero-day patterns and malicious behaviors in real time. Continuous learning refines detection accuracy and strengthens proactive risk mitigation for evolving threats across encrypted traffic, cloud applications and hybrid work environments using behavioral baselining techniques.
4. Full TLS or SSL Inspection
The proxy-based architecture decrypts, inspects and re-encrypts encrypted traffic to expose hidden threats inside SSL or TLS streams. This provides deep visibility into modern attack vectors and maintains performance through cloud-scale packet processing and dynamic certificate handling instead of hardware appliances.
5. Generative AI Security Controls
The platform applies governance for generative AI tools by monitoring prompts, enforcing data boundaries and controlling authenticated access. These controls reduce data leakage risks and help enterprises adopt AI responsibly while protecting regulated information and sensitive intellectual property through controlled AI interaction layers.
6. AI Security Posture Management
AI SPM discovers and analyzes AI models, data flows and service connections while mapping compliance gaps. Automated classification and risk scoring help security teams enforce policies, improve visibility into shadow AI usage and maintain strong governance across complex AI ecosystems through continuous configuration analysis.
7. Integrated Data Protection
Unified DLP and CASB functions classify sensitive data, manage SaaS usage and block unauthorized transfers. This creates centralized data protection across web, private applications and endpoints, helping organizations maintain compliance and visibility through a single policy framework tied to contextual access signals.
8. Micro Segmentation & App-Only Connectivity
User sessions connect directly to authorized applications instead of networks. This removes broad network access and enforces granular segmentation based on identity and context. Applications remain invisible on the internet, decreasing exposure to scanning, exploitation and lateral threat activity through zero trust session brokering.
9. Unified Threat & Data Protection
A single platform combines a secure web gateway, cloud firewall, CASB and ZTNA functions for comprehensive defense. Centralized inspection and policy correlation simplify operations, improve detection fidelity and minimize fragmentation caused by standalone point products across enterprise environments through a unified control plane.
10. Adaptive AI-Driven Policy Orchestration
The platform employs adaptive AI to analyze user behavior, device posture, data sensitivity, and application context, then automatically adjusts zero trust policies in real time. This minimizes manual setup, avoids policy drift, and provides precise access control using dynamic risk scoring and automation.

How to Create a Zero-Trust AI Tool like Zscaler?
Creating a Zscaler-like Zero-Trust AI Tool uses cloud-native architecture, AI-driven threat detection, and policy-based access controls. Our developers build scalable, real-time Zero Trust solutions through a dedicated development process.
1. Consultation
We begin by analyzing your security environment, access workflows and compliance boundaries to determine how a zero trust architecture should operate within your ecosystem. Our developers identify identity flows, data exposure risks and AI governance needs to establish a precise foundation for the platform.
2. Threat Modeling & Requirement Mapping
Our developers conduct structured threat modeling to understand adversary behaviors, access pathways and potential misuse scenarios. We map these insights into functional security requirements, ensuring the platform supports identity-centric controls, granular segmentation and AI-driven risk reasoning from the earliest stage.
3. Zero Trust Architecture Design
We design the core architecture by defining how identities, applications and data interact inside a policy-driven trust model. This includes shaping access flows, segmentation logic and session-level isolation so the platform enforces continuous verification and controlled connectivity across distributed environments.
4. AI Framework & Policy Logic Design
We outline the AI components that evaluate user behavior, contextual risk signals and data handling patterns. Our developers structure adaptive policy logic that allows the platform to learn from telemetry, recommend access decisions and support automated enforcement with high precision.
5. Platform Development & Integration
We build the platform’s functional layers, including identity validation workflows, traffic inspection pipelines, policy engines and data protection modules. Each component is integrated to support real-time decision making, ensuring seamless user-to-application connectivity without exposing internal networks.
6. Security Controls Implementation
We incorporate advanced security controls such as micro segmentation rules, application cloaking and continuous posture evaluation. These controls help maintain least privilege access while preventing unauthorized lateral movement and enabling the platform to respond dynamically to changing threat and usage conditions.
7. AI Model Training & Optimization
Our developers train AI models on behavioral patterns, access logs and contextual signals to improve accuracy and resilience. The models are refined to support predictive threat detection and adaptive access recommendations that reduce manual policy adjustments across complex environments.
8. Compliance & Data Governance Setup
We establish compliance-aligned configurations that manage sensitive data flows, user access privileges and audit requirements. This ensures the platform supports regulatory governance while enabling safe usage of generative AI systems, internal applications and cloud services across all user groups.
9. Testing & Validation
We execute extensive testing cycles, including trust boundary validation, policy stress tests and AI behavior assessments. The platform is hardened to ensure robust access enforcement, reliable threat detection and consistent performance under heavy traffic and distributed workloads.
10. Deployment & Monitoring
We deploy the platform within your environment, enable detailed observability dashboards and fine-tune access policies based on real usage signals. Continuous monitoring allows us to implement iterative improvements, ensuring the platform evolves alongside emerging threats and operational requirements.
Cost to Build a Zscaler-like Zero-Trust AI Tool
The cost to build a Zscaler-like Zero-Trust AI Tool depends on cloud infrastructure, AI integration, and security features. These factors help plan budgets for scalable, real-time, enterprise-grade Zero Trust solutions.
| Development Phase | Description | Estimated Cost |
| Consultation | Defines scope through environment assessment and zero trust planning. | $4,000 – $7,000 |
| Threat Modeling & Architecture | Outlines trust boundaries and security architecture for the platform. | $6,000 – $12,000 |
| Zero Trust Core Development | Builds identity verification and segmentation controls. | $18,000 – $34,000 |
| AI Framework & Policy Engine | Develops contextual risk models and adaptive policy logic. | $16,000 – $30,000 |
| Platform Integration & Traffic Handling | Integrates inspection pipelines and session routing components. | $12,000 – $18,000 |
| Security Controls & Data Protection | Adds micro segmentation and data governance rules. | $8,000 – $14,000 |
| Testing & Validation | Executes policy testing and system hardening for stability. | $7,000 – $12,000 |
| Deployment & Optimization | Handles deployment setup and continuous optimization. | $8,000 – $12,000 |
Total Estimated Cost: $67,000 – $128,000
Note: Development costs vary with project size, AI complexity, compliance, and integration challenges. Broader coverage, telemetry, or advanced policy automation can also increase the budget.
Consult IdeaUsher to get a tailored cost estimate and a clear roadmap for developing a secure, scalable Zscaler-like Zero-Trust AI platform aligned with your product vision.

Cost-Affecting Factors to Consider During Development
Key factors affecting development costs include cloud infrastructure, AI integration, security features, and scalability requirements, essential for building a Zscaler-like Zero Trust AI solution.
1. Scope & Feature Complexity
Broader requirements such as multi layer zero trust controls, AI driven policy engines and extensive monitoring dashboards increase development time, customization needs and overall project expenditure.
2. AI Model Sophistication
Advanced AI features like adaptive risk scoring, behavioral analytics and automated policy orchestration require larger datasets, iterative training cycles and expert tuning, which raises both development and operational costs.
3. Integration Requirements
Connecting the platform with identity systems, enterprise applications and traffic sources requires careful workflow mapping and secure API orchestration, influencing development timelines and integration-related expenses.
4. Security & Compliance Needs
Projects requiring strict data governance, regulatory alignment and enhanced audit capabilities demand additional configuration, validation and security controls, which contribute directly to overall development cost.
5. Scalability & Performance Expectations
Supporting high traffic volumes, distributed users and low latency inspection capabilities requires optimized architecture and robust infrastructure planning, increasing both upfront engineering efforts and long-term maintenance costs.
Suggested Tech Stacks for Zero-Trust AI Tool Development
Developing a Zscaler-like Zero-Trust AI Tool requires a robust tech stack combining cloud-native platforms, AI/ML frameworks, secure networking, and scalable databases. Choosing the right technologies ensures high performance, security, and reliability.
| Category | Suggested Technologies | Purpose |
| AI/ML Frameworks | TensorFlow, PyTorch, Scikit-learn | Enable behavior analysis, risk scoring, and intelligent detection across the zero-trust environment. |
| Cloud Infrastructure & Edge Deployment | AWS, Azure, Google Cloud | Provide scalability, global reach, and reliable low-latency enforcement for security processes. |
| Identity & Access Management (IAM) | OAuth 2.0, OpenID Connect, Keycloak, Auth0 | Manage secure authentication, SSO, and identity validation before granting access. |
| Zero Trust Policy & Security Tools | OPA, Vault, OpenSSL | Support policy decisions, encryption, and secure handling of sensitive credentials. |
| Networking & Traffic Processing | Envoy Proxy, Nginx, HAProxy | Enable traffic inspection, secure routing, and controlled user-to-app connectivity. |
| Containerization & Orchestration | Docker, Kubernetes | Allow scalable deployment, modular services, and stable operation of all platform components. |
| Monitoring, Telemetry & Logging | Prometheus, Grafana, ELK Stack | Provide system visibility, anomaly insights, and data needed to refine AI models. |
Challenges & How Our Developers Will Solve These?
Building a Zscaler-like Zero-Trust AI Tool involves challenges like secure cloud integration, real-time threat detection, and scalability. Our developers address these with expert AI implementation, optimized architecture, and robust security solutions.
1. Complex Identity Mapping Across Multiple Systems
Challenge: Managing fragmented identities across directories creates inconsistent trust signals that weaken a unified zero-trust architecture during user access flows.
Solution: We consolidate identities using context-aware schemas, automated mapping logic and consistent validation layers that bring all identity sources under one reliable trust framework.
2. Building Accurate AI Models
Challenge: Insufficient or noisy behavioral data restricts reliable AI risk scoring and reduces early anomaly detection precision across the zero-trust environment.
Solution: We build structured refinement pipelines, synthesize behavioral signals and train models iteratively to create stronger AI detection capabilities even when original datasets are imperfect.
3. Ensuring Low Latency
Challenge: Intensive traffic inspection may increase latency and interrupt secure user-to-application connectivity in distributed networks.
Solution: We design distributed inspection points, optimize routing paths and streamline policy evaluation to maintain fast and stable zero trust connectivity without degrading user experience.
4. Preventing Lateral Movement
Challenge: Complex hybrid environments create unseen pathways that enable attacker lateral movement if not segmented precisely.
Solution: We implement application-level segmentation, identity-guarded sessions and strict trust boundaries that minimize privileged pathways and strengthen zero-trust segmentation across all environments.
Conclusion
Building a Zscaler-like Zero-Trust AI Tool empowers organizations to enforce strict access controls and continuously monitor network activity, ensuring security without compromising efficiency. Such a platform minimizes risks, protects sensitive data, and adapts to evolving threats, giving businesses the confidence to operate safely in complex digital environments. By combining AI-driven intelligence with a zero-trust framework, companies can detect anomalies, prevent unauthorized access, and maintain compliance standards effectively. Investing in this approach strengthens security posture while supporting seamless digital operations and business growth.
Why Build Your Zero-Trust AI Platform with IdeaUsher?
Designing a Zscaler-like Zero-Trust AI tool requires deep expertise in identity-based access control, AI-driven threat detection, and secure cloud-native architectures. At IdeaUsher, we help enterprises and product founders translate Zero-Trust security principles into scalable, production-ready platforms.
Why Work With Us?
- Zero-Trust Architecture Expertise: We design identity-first security frameworks with continuous verification, policy enforcement, and real-time risk scoring.
- AI-Driven Security Engineering: Our teams build AI models for behavioral analysis, access anomaly detection, and adaptive threat response.
- Enterprise-Grade Compliance: We align platform design with enterprise security standards and regulatory requirements from day one.
- Proven Platform Delivery: Our portfolio reflects experience building complex security, fintech, and enterprise-grade platforms.
Explore our portfolio to understand how we deliver secure, scalable AI solutions for various industries.
Reach out to us to discuss your Zero-Trust AI platform idea and get expert guidance on architecture, timelines, and execution.
Work with Ex-MAANG developers to build next-gen apps schedule your consultation now
FAQs
A Zero-Trust AI platform uses cloud-native infrastructure, AI and machine learning models, identity management systems, secure APIs, and real-time monitoring tools. Popular choices include Python, Kubernetes, cloud IAM services, and behavioral analytics engines.
Key features include continuous user verification, adaptive access control, AI-driven threat detection, real-time monitoring, and secure remote access. These ensure that every network interaction is authenticated and potential threats are identified proactively.
Integration involves connecting the platform with existing identity providers, endpoints, cloud services, and network tools using secure APIs. This ensures seamless authentication, continuous verification, and policy enforcement without disrupting existing enterprise workflows.
The platform must comply with standards like GDPR, SOC 2, ISO 27001, and industry-specific regulations. Compliance ensures secure data handling, audit readiness, and trust from enterprise clients during market entry and scaling.