In a world filled with data breaches, online snoops, and geo-restrictions, VPNs have emerged as the caped crusaders of the internet. They’re like your trusty sidekick, working tirelessly to protect your sensitive information and unlock a realm of boundless possibilities.
We’re here to ignite your inner tech genius and show you how to create a Virtual Private Network like DotVPN – a one-of-a-kind digital creation that’ll leave users in awe. Imagine wielding the power to offer others a secure escape from the clutches of cyber threats and censorship.
Now, let’s dive deep into the thrilling world of VPNs. We’ll uncover the secrets behind their popularity, explore the quirks and features that make them so irresistible, and explore a sample VPN application to better understand the expectations of the intended users, and guide you on your quest to create a VPN masterpiece that’ll make even the most seasoned tech enthusiasts do a double take.
- What is DotVPN?
- Market Insights
- How Does a VPN Software Work?
- Must-Have Features of VPN Software
- An Example of a Virtual Private Network
- How to Develop a VPN like DotVPN?
- Tech Stack Required for VPN Development
- 9. Project Management Tool
- Factors Influencing the Cost of Developing a VPN Like DotVPN
- Top 5 Alternatives to DotVPN
- Future Opportunities for Business Owners and Entrepreneurs in VPN Development
- Conclusion-
- FAQs
What is DotVPN?
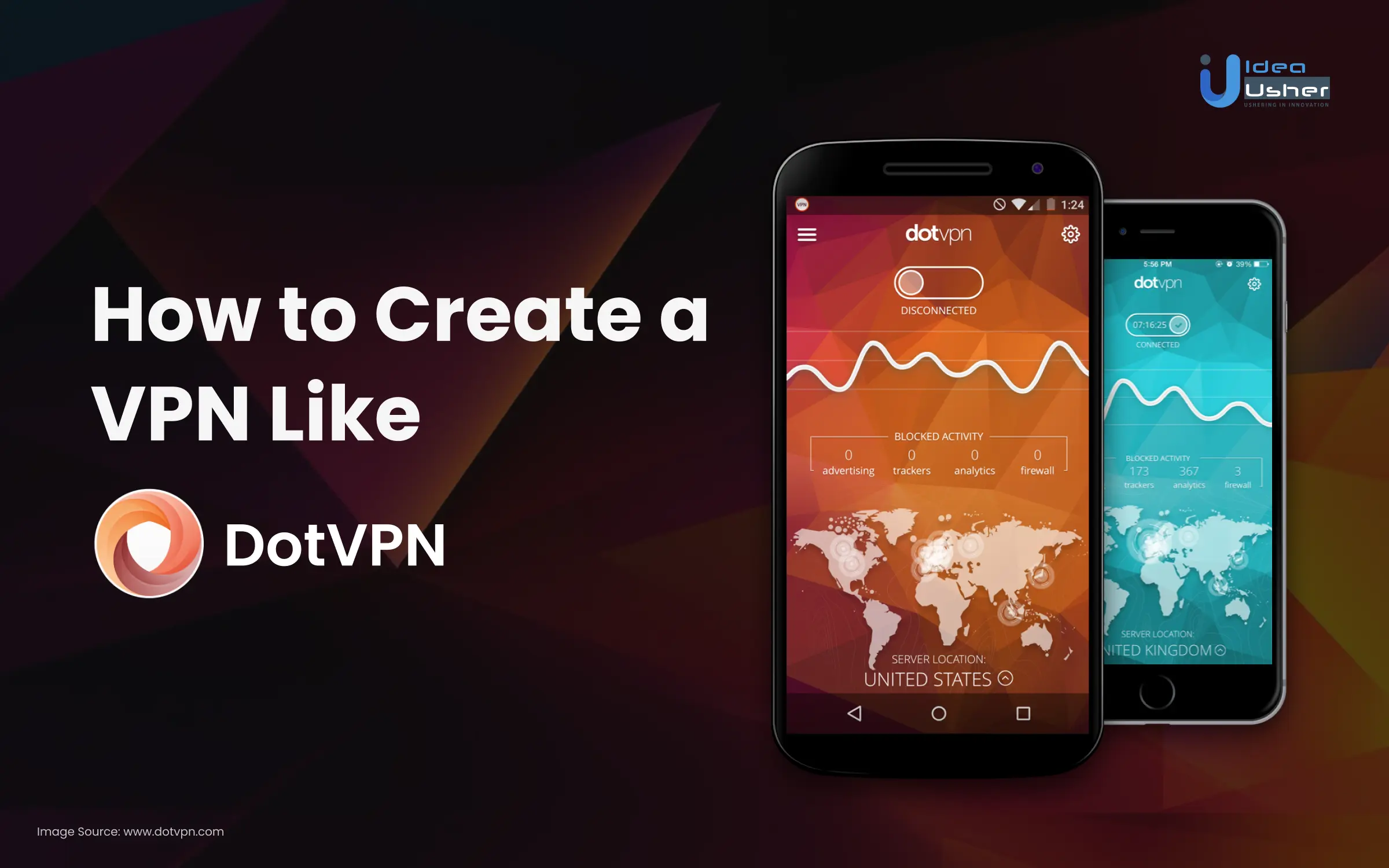
DotVPN is a top-notch VPN extension made exclusively for Chrome users. It’s designed to provide you with a secure, private, and unrestricted browsing experience. What sets DotVPN apart is its unique sign-up process that doesn’t require a password. You can simply sign up using your email account and gain access to its high-speed VPN service.
When you use DotVPN, you can enjoy an extra layer of security while browsing the web. It encrypts your internet traffic, making it extremely difficult for anyone to snoop on or monitor your online activities. This encryption ensures that your data remains confidential and secure, especially when you connect to public Wi-Fi networks that are prone to hacking attempts.
But that’s not all—DotVPN also lets you bypass geographic restrictions and access content that might be blocked in your region. It does this by routing your internet traffic through servers located in different countries. By connecting to a server in a specific location, you can appear as if you’re browsing from that country, opening up access to region-restricted websites, streaming platforms, and online applications.
Market Insights
(Credits: precedenceresearch.com)
But here’s the exciting part: it’s projected to soar even higher in the coming years, potentially reaching around USD 358.64 billion by 2032. That’s a staggering compound annual growth rate (CAGR) of 22.04% from 2023 to 2032!
So, why is the VPN market experiencing such tremendous growth?
Well, it all comes down to our increasing need for secure and private internet connections.
With rising concerns over data privacy and cybersecurity, individuals and organizations are seeking ways to protect their online activities from prying eyes. VPNs provide an excellent solution, encrypting our internet traffic and shielding our data from potential threats.
Another contributing factor to the expanding VPN market is the surge in remote work and the widespread adoption of cloud-based services.
As more and more people work from home or connect to business networks remotely, the demand for reliable and secure VPN connections has skyrocketed. VPNs enable employees to access company resources securely and privately, regardless of their physical location.
This growth in the VPN market isn’t limited to specific industries either. It spans across various sectors, demonstrating the universal need for enhanced online security and privacy measures. Whether it’s banking, healthcare, e-commerce, or any other field that deals with sensitive data, VPNs have become indispensable tools for safeguarding information and maintaining confidentiality.
How Does a VPN Software Work?
When you use a VPN, it sets up a secure and encrypted connection between your device and a remote server operated by the VPN provider. This connection works like a virtual tunnel that shields your data from potential threats.
To establish this connection, you activate the VPN on your device. It then sends a request to the VPN server, initiating the process. Once connected, all the data traveling between your device and the VPN server is encrypted. Encryption ensures that your data is converted into a jumbled mess that is virtually impossible for anyone else to decipher.
Now, here’s the interesting part.
Instead of your data going directly to your Internet Service Provider (ISP), it gets routed through the VPN server. The VPN server acts as an intermediary, making it appear as if your data is coming from the server itself rather than your device. This way, your actual IP address assigned by your ISP is masked, making it harder for others to track your location or identity.
By going through the VPN server, your data gains an additional layer of security. It becomes protected from potential interception or monitoring by hackers, government agencies, or other prying eyes. This is especially important when you’re using public Wi-Fi networks, which are notorious for their lack of security.
Another benefit of using a VPN is the ability to access restricted content.
Let’s say you want to watch a TV show or access a website that’s only available in a specific country. By connecting to a VPN server in that country, you can appear as if you’re browsing from there, bypassing the geographical restrictions and gaining access to the desired content.
VPNs are also great for privacy and anonymity. They prevent your ISP, network administrators, or other entities from tracking or monitoring your online activities. With your data encrypted and your IP address masked, it becomes challenging for anyone to trace your internet usage back to your device. This is particularly important if you value your online privacy and want to keep your browsing habits private.
VPNs use different tunneling protocols to establish and maintain the encrypted connection. These protocols, such as OpenVPN, IPsec, L2TP, and WireGuard, vary in terms of security and performance.
Thus, a VPN creates a secure and private environment for your internet browsing. It encrypts your data, routes it through a remote server, masks your IP address, and allows you to access restricted content while maintaining your online privacy.
Whether you want to protect your sensitive information, browse anonymously, or access content from around the world, a VPN is an invaluable tool that keeps you safe and in control of your online experience.
Must-Have Features of VPN Software
Let’s explore the features that ensure that the VPN software provides a secure, private, and user-friendly experience, protecting your online activities and data while offering convenience and control over your VPN usage.
1. OS Support
The VPN should be compatible with major operating systems like Windows, macOS, Android, iOS, and ideally offer support for Linux as well.
2. Simultaneous Connections
The ability to connect multiple devices simultaneously is important. VPNs may impose limits on the number of simultaneous connections, so choose one that suits your needs.
3. Split Tunneling
This feature allows users to choose which apps or traffic should go through the VPN and which ones should bypass it. It provides flexibility and control over VPN usage.
4. Bandwidth
The VPN should offer unlimited bandwidth to ensure fast and uninterrupted browsing, streaming, and downloading without restrictions.
5. Customer Support
Look for VPN providers that offer responsive and helpful customer support, preferably with options like live chat, email, or a knowledge base to address any issues or inquiries.
6. Money-Back Guarantee
A reputable VPN should offer a money-back guarantee, typically for 30 days, to allow users to test the service risk-free and get a refund if not satisfied.
7. No-Logs Policy
Privacy is a key aspect of VPNs. Ensure that the VPN has a strict no-logs policy, meaning it does not collect or store any user activity logs or personally identifiable information.
8. Payment Methods
Look for VPNs that offer various payment options, including anonymous methods like cryptocurrencies, to protect your privacy during the subscription process.
9. Encryption Types
The VPN should use strong encryption protocols like AES-256 to secure your data and communications, ensuring that they cannot be intercepted or decrypted by unauthorized parties.
10. VPN Protocols
Choose a VPN that supports reliable and secure VPN protocols like OpenVPN or WireGuard, providing a secure and efficient connection between your device and the VPN server.
11. VPN Automation Features
Look for features like automatic connection on startup or reconnecting to the last used server to ensure a seamless and always-on VPN experience.
12. Kill Switch
A kill switch is an essential feature that automatically disconnects your internet connection if the VPN connection drops, preventing any data leaks or exposure.
13. Leak Protection
The VPN should provide DNS leak protection, IP leak protection, and WebRTC leak protection to ensure that your real IP address and other sensitive information are not exposed.
14. Malware & Ad Blockers
Some VPNs offer additional features like built-in ad blockers and malware protection to enhance your online security and improve your browsing experience.
15. IP Address Options
VPNs that offer options such as dedicated IP addresses or IP shuffling provide additional customization and flexibility for specific needs or to bypass certain online restrictions.
An Example of a Virtual Private Network
Let’s take a closer look at DotVPN as an example of VPN software. DotVPN stands out as a user-friendly VPN solution that offers seamless compatibility across various devices, including personal computers, smartphones, and tablets. Let’s delve into some key highlights of DotVPN:
- DotVPN is a user-friendly VPN software that offers easy access to a secure and open internet.
- It has both a free version and a premium version with enhanced features.
- DotVPN can be used on PCs, smartphones, and tablets.
- Features include encryption, privacy protection, and impressive connection speeds.
- It provides browser extensions for popular browsers like Chrome, Firefox, and Opera.
- Mobile apps are available for Android and iOS devices.
- The premium version offers additional features such as tracker and analytics blocking, an integrated firewall, and protection against DDoS attacks.
- DotVPN has a strict zero-logging policy.
- Its intuitive user interface allows for one-tap connection and disconnection.
- It ensures Wi-Fi security by blocking unregistered inbound connections and protecting against hacker attacks, DDoS attacks, and packet sniffers.
- DotVPN allows users to bypass ISP throttling and choose their virtual location from over 10 countries.
How to Develop a VPN like DotVPN?
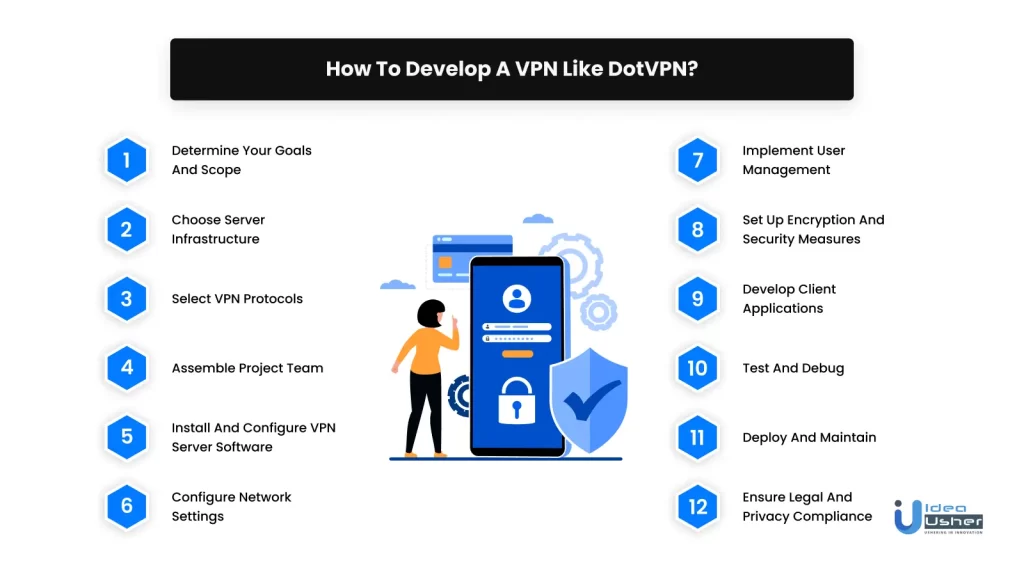
Creating a VPN similar to DotVPN involves several steps. Here is a detailed guide on how to create a VPN like DotVPN, covering all the steps mentioned earlier:
1. Determine your goals and scope
- Clearly define the purpose of your VPN and identify the target audience.
- Specify the features and functionalities you want to offer, such as encryption, server locations, and protocol support.
2. Choose server infrastructure
- Decide whether to set up your own physical servers or use a cloud provider.
- Select the appropriate hardware or cloud infrastructure based on your anticipated server capacity and scalability requirements.
3. Select VPN Protocols
- Research and choose the VPN protocols that align with your goals and provide the desired level of security and performance.
- Popular options include OpenVPN, IPSec, L2TP/IPSec, and WireGuard.
4. Assemble Project Team
Create a project team consisting of roles such as project manager, IT architect, business analysts, UI designers, web developers, Android developers, iOS developers, testers, and DevOps engineers.
5. Install and configure VPN server software
- Install the chosen VPN server software on your servers or cloud instances.
- Follow the documentation or guidelines provided by the software vendor for correct installation.
- Configure the server software to set up the desired encryption, authentication, and tunneling settings.
6. Configure network settings
- Set up IP addressing and routing for your VPN servers.
- Configure firewall rules to allow VPN traffic and protect against unauthorized access.
- Set up port forwarding to ensure proper traffic flow through the VPN.
7. Implement user management
- Develop a user registration and authentication system to manage VPN users.
- Store user credentials securely, such as using hashed and salted passwords.
- Consider implementing additional security measures like two-factor authentication for enhanced user protection.
8. Set up encryption and security measures
- Implement encryption algorithms, such as AES (Advanced Encryption Standard), to secure data transmission.
- Enable security protocols like TLS (Transport Layer Security) for added protection.
9. Develop client applications
- Design and develop client applications for various platforms, such as Windows, macOS, iOS, and Android.
- Include features like server selection, protocol selection, and connection status indicators.
10. Test and debug
- Conduct thorough testing to ensure the stability and security of your VPN.
- Address any issues or bugs discovered during testing.
11. Deploy and maintain
- Launch your VPN service and make it available to users.
- Regularly update and maintain your server software to address security vulnerabilities.
- Monitor server performance and ensure scalability to accommodate growing user demand.
12. Ensure legal and privacy compliance
- Familiarize yourself with legal requirements and regulations related to VPN services in your jurisdiction.
- Implement privacy measures, such as a strict no-logs policy, to protect user data and privacy.
Tech Stack Required for VPN Development
Given below is a detailed tech stack required for developing a VPN similar to DotVPN:
1. Development Methodology
Agile methodology for iterative development.
2. Development Approach
- Utilize a managed cloud services platform like AWS to focus on development instead of IT infrastructure management.
- Use WordPress as the content management system (CMS) for website development.
- Implement core features using APIs and SDKs.
- Enhance test coverage with a test automation aid like pCloudy.
3. Managed Cloud Services Provider
- Sign up with AWS (Amazon Web Services), which offers Amazon Elastic Compute Cloud (EC2) as the Infrastructure-as-a-Service (IaaS) solution.
- Utilize AWS Amplify, the Mobile-Backend-as-a-Service (MBaaS) offering from AWS, for handling cloud infrastructure, persistent storage, user management, push notifications, and easy integration of third-party APIs.
4. WordPress Theme and Plugins
- Choose a responsive WordPress theme like Marketica for selling digital products online.
- Utilize WooCommerce, a popular eCommerce platform, for implementing eCommerce features in the WordPress site.
5. API Solution for VPN
- Use the PureVPN API solution, which provides a comprehensive set of features including security and optimization. Register with PureVPN to access their API documentation.
6. Payment Gateway API Solution
- Sign up with Braintree, a payment gateway API solution provider, which offers features like global reach, support for popular payment methods, security, scalability, and ease of integration. Use Braintree Direct for web, Android, and iOS platforms.
7. Bulk SMS API Solution for Push Notifications
- Sign up with Twilio’s Programmable SMS solution, which enables easy integration of push notification features in your mobile app. Refer to Twilio’s documentation for API integration.
8. Test Automation Aid
- Utilize pCloudy, a test automation aid, which provides over 5,000 device-browser combinations on the cloud for comprehensive testing of your mobile app.
9. Project Management Tool
- Use Trello, a robust project management tool, to manage the Agile project using the Scrum technique. Conduct daily stand-up meetings, sprint review meetings, and sprint retrospective meetings.
10. UI Design Resources
- Refer to the “Human Interface Guidelines” for designing the iOS app UI.
- Utilize “Material Design 3” for designing the Android app UI.
11. Chrome Extension Development
- Configure necessary files like the “manifest.json” file.
- Test the extension using the “chrome://extensions” page.
- Introduce required styling elements.
- Publish the extension to the Chrome Web Store.
12. Android App Development
- Code the app using Java and Android Studio as the IDE.
- Integrate SDKs/APIs for PureVPN, Braintree Direct, and Twilio.
- Test the app using Espresso and the pCloudy device lab.
- Publish the app to the Google Play Store following their submission guidelines.
13. iOS App Development:
- Code the app using Objective-C and Xcode as the IDE.
- Integrate APIs/SDKs for Twilio, Braintree, and PureVPN.
- Test the app using XCTest and pCloudy device lab.
- Submit the app to the Apple App Store following their submission process.
By following this detailed tech stack, you can develop a VPN like DotVPN with the required features and functionality.
Factors Influencing the Cost of Developing a VPN Like DotVPN
Factors listed below should be carefully considered when estimating the total cost of developing a VPN software solution like DotVPN. Proper planning and budgeting for both direct and indirect costs will help ensure the successful implementation and ongoing support of the VPN software.
1. Hardware and Software Costs
The initial investment in dedicated VPN hardware devices and software licenses contributes to the direct cost of developing a VPN software solution. This includes the cost of purchasing VPN devices and any necessary software components.
2. Setup Costs
Setting up a VPN software solution for a large enterprise can be time-consuming and complex. It may involve procurement, basic setup, and deployment activities, which can consume significant labor hours.
3. Ongoing Maintenance
VPN devices require regular updating, refinement, and security patching to ensure optimal performance and protection. Ongoing maintenance activities, including after-hours updates and addressing any technical issues, contribute to the long-term cost of maintaining the VPN software.
4. User Support
Providing technical support for end users, including assisting them in setting up the VPN software on their devices and addressing any issues they may encounter, requires dedicated time and resources. The amount of user support needed can vary but should be considered when estimating the overall cost of developing a VPN software solution.
5. Two-Factor Authentication
If implementing two-factor authentication for enhanced security, there may be additional costs associated with supporting various two-factor solutions. This could include the use of third-party services or the management of machine certificates, which require additional configuration and support hours.
6. Potential Indirect Costs
Indirect costs can arise from potential compromises to network security, connectivity issues, and the need for additional equipment. For example, if an end user’s Windows network is routed through the VPN network, it can expose the internal network to malware and cybersecurity threats.
Connectivity issues with IPsec VPNs can result in calls to the help desk and lost productivity. Minor network fluctuations can also lead to potential file corruption, resulting in support costs for file restoration and lost work. Additionally, maintaining a fleet of corporate laptops pre-configured with VPN settings may be necessary for remote users, adding to equipment and support costs.
Top 5 Alternatives to DotVPN
Let’s look at alternatives to DotVPN that offer various features and levels of privacy and security.
1. Proton VPN
Proton VPN is a privacy-focused VPN service that prioritizes user confidentiality. It does not keep logs of user activities and ensures secure browsing through encrypted VPN traffic. With Proton VPN, you can browse the internet with peace of mind, knowing that your privacy is protected.
2. Mullvad
Mullvad is a paid and open-source VPN service that focuses on user privacy and security. It supports multiple VPN protocols, including WireGuard and OpenVPN, and offers strong encryption.
3. Windscribe
Windscribe is a paid and open-source VPN service that prioritizes user privacy and security. Mullvad ensures a secure and private browsing experience and offers features like split tunneling and a distraction-free mode
4. Psiphon
Psiphon is a freemium and open-source VPN service that allows you to bypass censorship and provides encrypted VPN. It offers anonymity and the ability to hide your IP.
5. Snowflake Tor
Snowflake Tor is a free and open-source VPN service that focuses on privacy and bypassing censorship. It operates on a decentralized infrastructure and ensures no tracking or use of personal data.
Future Opportunities for Business Owners and Entrepreneurs in VPN Development
The future of VPN development holds immense opportunities for business owners and entrepreneurs who are ready to dive into this dynamic market. Here are some key future opportunities to consider:
1. Market Growth
The global market for Virtual Private Network (VPN) is estimated to be valued at US$44.6 billion in 2022 and is projected to reach a substantial size of US$137.7 billion by 2030, with a CAGR of 15.1% during the period from 2022 to 2030, as per GlobeNewsWire. This growth is driven by the rising awareness of online privacy and security, which has led to a significant demand for VPN services among individuals and businesses alike.
2. Expansion into Emerging Markets
As the VPN market expands globally, there are promising opportunities in emerging markets, particularly in regions like Asia and Latin America. These markets are witnessing rapid internet adoption and an increasing need for secure online connections. By targeting these regions and adapting VPN services to their specific needs, entrepreneurs can tap into new customer bases and establish a strong presence in these growing markets.
3. Customization and Niche Offerings
The evolving VPN landscape opens doors for entrepreneurs to provide customized VPN solutions tailored to specific user needs. This includes niche offerings such as VPNs for gamers, VPNs for remote workers, or VPNs with specialized features for particular industries. By catering to specific user segments and addressing their unique requirements, entrepreneurs can carve out a distinct market position and build a loyal customer base.
4. Enhanced Privacy Features
Privacy concerns are likely to remain a top priority for internet users, fueling the demand for VPNs that offer advanced privacy features. Entrepreneurs can seize the opportunity by developing VPN solutions with cutting-edge encryption protocols, zero-logging policies, and additional privacy-enhancing features. By prioritizing user privacy and delivering robust security measures, VPN businesses can differentiate themselves and attract privacy-conscious customers.
5. Mobile VPN Solutions
With the proliferation of smartphones and mobile devices, there is a growing need for VPN services optimized for mobile platforms. Entrepreneurs can develop mobile-first VPN applications with user-friendly interfaces, seamless connectivity, and features tailored for mobile use cases. The mobile VPN market presents a significant opportunity for entrepreneurs to tap into the vast user base of mobile device users who seek secure internet access on the go.
6. Partnership Opportunities
Collaborations and partnerships with other tech companies, content providers, or ISPs can unlock new opportunities in the VPN market. By integrating VPN services into existing platforms or bundling them with complementary products, entrepreneurs can reach a wider audience and enhance the value proposition of their offerings. Strategic partnerships can also enable access to exclusive content, expanded network infrastructure, or distribution channels, fostering business growth and market penetration.
7. Innovations in Technology
The VPN landscape is continuously evolving, driven by technological advancements and changing user needs. Entrepreneurs who stay at the forefront of these innovations can leverage emerging technologies such as blockchain, artificial intelligence, or decentralized VPN architectures to create disruptive VPN solutions. By embracing innovation and exploring new possibilities, entrepreneurs can gain a competitive edge and pioneer the next generation of VPN services.
Conclusion-
In conclusion, creating a VPN like DotVPN is a challenging yet rewarding endeavor for entrepreneurs and business owners. The increasing demand for online privacy and security, coupled with the exponential growth of the VPN market, presents a lucrative opportunity for those willing to venture into this domain.
By following the necessary steps, including defining the project scope, choosing the right development methodology, and assembling a skilled team, you can embark on the journey of creating your own VPN software. Leveraging the right technology stack, such as managed cloud services, WordPress, and API solutions, will enable you to develop a robust and user-friendly VPN application.
If you are aspiring to create a VPN like DotVPN, Idea Usher is the perfect partner to turn your vision into reality. With our expertise in software development and a deep understanding of the VPN market, we are equipped to provide you with comprehensive solutions that meet your specific requirements.
At Idea Usher, we believe in transforming ideas into successful ventures. Our team of skilled developers, designers, and project managers will work closely with you to bring your VPN concept to life. From crafting a user-friendly interface to implementing robust security features, we ensure that your VPN software stands out in the competitive market.
Contact Idea Usher today!
Email: [email protected]
Phone: +1-6284324305
FAQs
Q. What is a VPN?
A VPN, or Virtual Private Network, is a secure and private network connection that allows users to access the internet while keeping their online activities and data encrypted and protected. It creates a virtual tunnel between the user’s device and the VPN server, ensuring that all internet traffic is encrypted and routed through the server, making it difficult for anyone to intercept or track the user’s online activities.
Q. What is DotVPN used for?
A: DotVPN is a VPN service that provides encryption for your browser connection, especially when using public Wi-Fi networks. It creates a secure VPN connection to protect your internet activity and allows you to access restricted content while maintaining your privacy. DotVPN also ensures that your connection details are not recorded.
Q. Is DotVPN free?
A. Yes, DotVPN offers a free version of its service. Free users can enjoy unlimited data usage, access to servers in the US and France, and a firewall. However, to unlock additional features such as access to all servers, faster speeds, ad blocker, and audio/video streaming capabilities, users need to upgrade to DotVPN’s monthly or yearly plan.
Q: What are the key features to consider when creating a VPN like DotVPN?
A: When creating a VPN like DotVPN, key features to consider include strong encryption protocols like AES, secure tunneling, split tunneling functionality, no-logs policy for user privacy, kill switch to prevent data leaks, IP/DNS leak protection, and simultaneous device connections.
Q: Can I monetize my VPN service similar to DotVPN?
A: Yes, you can monetize your VPN service by offering premium subscription plans with additional features and benefits. You can also implement affiliate programs, partner with advertisers, or offer white-label solutions to other businesses. Additionally, you can explore partnerships with content providers or integrate ad placements within the VPN client application.








Vrinda Sharma