Trust has quietly become the backbone of digital identity and global onboarding. When someone opens a bank account or creates a crypto wallet, the system must verify them quickly and accurately. Businesses are now expected to stop fraud, protect privacy, and still approve legitimate users without delay. Regulations are stricter and fraud tactics are more advanced, so manual verification simply cannot keep up.
That shift is why global KYC identity platforms are gaining real momentum. Tools like Sumsub prove what scalable verification looks like with capabilities such as biometric face matching, liveness detection, global watchlist screening, and automated compliance workflows.
Over the years, we’ve built multiple global identity and verification platforms powered by AI-driven identity intelligence and RegTech automation frameworks. As we’ve this expertise, we’re writing this blog to discuss the steps to build a Sumsub-like global KYC identity platform. Let’s start!
Key Market Takeaways for Global KYC Identity Platforms
According to Databridgemarketresearch, the global e-KYC market is gaining momentum as organizations continue shifting toward digital onboarding and stronger compliance standards. Industry projections suggest the market, valued at roughly USD 800 million in 2024, may grow to more than USD 3.3 billion by 2032. This rapid expansion is being fueled by rising fraud risk, growing regulatory pressure, and a broader expectation that identity verification should be fast, seamless, and secure. For many sectors, especially finance and fintech, e-KYC has become a foundational requirement rather than an optional upgrade.
Source: Databridgemarketresearch
Within this growing space, companies such as Jumio and Trulioo have emerged as influential leaders. Jumio focuses on automating verification through biometric checks, document validation, and machine-learning-based fraud detection, serving industries that depend on high-assurance identity verification.
Trulioo takes a global data network approach, enabling businesses to verify customers in real time across more than 190 countries. Both platforms are recognized for reducing onboarding friction while supporting strict regulatory compliance.
The market is also being shaped by strategic partnerships aimed at improving coverage and verification accuracy. A recent example is the collaboration between KYC360 and LSEG Risk Intelligence, which brings together extensive compliance data, identity verification tools, and advanced screening capabilities.
What is the Sumsub Platform?
Sumsub is a unified verification and compliance platform built to help companies onboard users securely, meet global regulatory requirements, and fight fraud without disrupting the user experience.
In simple terms, Sumsub works like a digital checkpoint: it confirms that every user is legitimate, compliant with regulations, and not a risk before they access sensitive systems or financial services.
The platform focuses on solving three core challenges:
- Identity Verification: Prove users are real people using real documents.
- Compliance: Meet global AML, KYC, and regional regulatory requirements with ease.
- Fraud Prevention: Block deepfakes, stolen credentials, synthetic identities, and other types of fraud before they escalate.
Here are some of its features,
1. Single-Click Verification
Users who have already completed verification with any Sumsub-powered platform can onboard again instantly without uploading documents or taking selfies. This removes friction, improves completion rates, and turns verification from a slow step into an advantage for platforms working within shared ecosystems like crypto or fintech.
2. Drag-and-Drop Workflow Builder
Compliance teams can create and modify verification flows without writing code or waiting on developers. They can tailor requirements by user type, country, or risk level and instantly deploy changes, ensuring onboarding stays aligned with evolving regulations and business needs.
3. Smart Document Capture
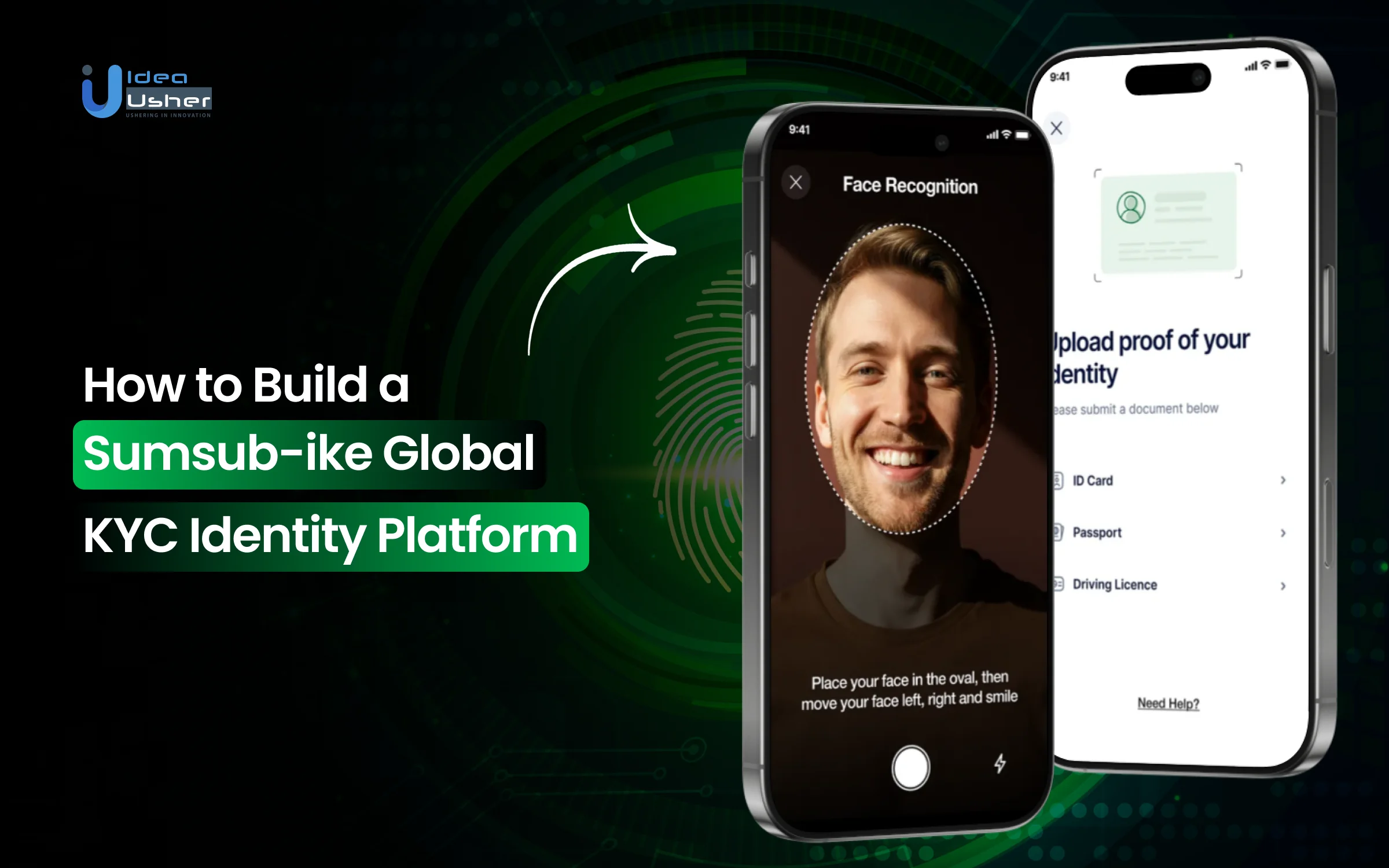
The mobile SDK helps users submit high-quality document images on the first try by detecting blur, glare, cut-off edges, and poor lighting in real time. With helpful prompts guiding the user through adjustments, failed uploads and repeated attempts are significantly reduced.
4. Interactive Liveness Check
Instead of relying on static selfies, Sumsub uses quick interactive challenges such as following a dot or turning the head to confirm the user is physically present. The process takes only a few seconds and provides strong protection against spoofing, deepfakes, and replay attacks.
5. Smart Localized Flows
Users automatically see verification steps tailored to their region, including document types and regulatory requirements specific to their country. With support for more than 14,000 documents across 220+ jurisdictions, onboarding feels intuitive instead of confusing or repetitive.
6. Real-Time Case Management
Review teams access all user verification data in a single dashboard, including documents, liveness footage, historical checks, and risk indicators. They can make decisions or request additional information with one click, supported by AI suggestions that improve accuracy and speed.
7. Continuous Risk and Sanction Monitoring
After initial onboarding, the platform continues screening users against updated sanction lists, PEP records, and adverse media sources. If a user’s risk profile changes, the system flags the case, helping businesses maintain compliance over time, not just at signup.
8. Developer Testing Sandbox
Developers can explore and test the full API using simulated scenarios before integrating it into their product. This reduces uncertainty, accelerates implementation timelines, and allows teams to validate logic and responses early in the development process.
How Does the Sumsub Platform Work?
The Sumsub platform works by capturing user documents and biometrics through a secure SDK that guides the process step by step. Once submitted, its backend engines verify authenticity, match faces, and run compliance checks using real-time risk intelligence. After processing, the system applies business rules to either approve access, request more information, or escalate the case for review.
Phase 1: User Submission (Capture and Data Intake)
User interaction begins with Sumsub’s embedded interface. This may be a mobile SDK integrated into a native app or a browser-based widget. The user is guided through a structured onboarding sequence:
Document capture
The system automatically detects if the document edges are visible, whether hologram zones are readable, or if lighting conditions obstruct machine-readable zones (MRZ). It identifies the specific document type and country before upload.
Liveness verification
A short proof-of-presence sequence confirms that the individual is physically present. Movement, response timing, and facial geometry are captured to build a biometric reference model.
Additional data requests
Depending on compliance requirements, users may be prompted for secondary authentication such as proof of address, banking information, corporate registration documents, or regulatory declarations.
Technical processes running silently in the background include:
- On-device preprocessing: Resizing, compression, and format normalization ensure the upload is optimal without degrading forensic detail.
- End-to-end encryption: All captured data is encrypted before leaving the device and remains encrypted in transit and storage.
- Device intelligence: Signals such as operating system, GPU capabilities, time zone alignment, input method, IP reputation, and emulator or automation flags are logged for fraud analysis.
This phase establishes the raw input data the platform will analyze.
Phase 2: AI Engine + Intelligence Layer
Once captured, the submission enters Sumsub’s multi-layered automated analysis pipeline. The platform typically completes these tasks within 2–7 seconds, running multiple validation models in parallel.
Step 1: Document Authentication & Forensic Screening
Sumsub evaluates the uploaded identity document against a large internal reference dataset covering 14,000+ supported document variations across 220+ jurisdictions. Checks include:
- Visual security elements: Holograms, kinegrams, optically variable ink, raised text, UV features, and document layout patterns.
- Pixel-level tampering detection: Inconsistencies in lighting, noise patterns, compression artifacts, and layered photo manipulations.
- MRZ and barcode parsing: Cross-checking encoded zones against visible printed data to detect mismatch fraud.
- OCR extraction: Text is accurately captured from multilingual scripts, including languages with diacritics, cursive elements, or mixed alphabets.
Metadata such as issue date, expiration date, issuing authority, and checksum structure is validated to confirm document legitimacy.
Step 2: Biometric Identity Verification
Simultaneously, the platform performs biometric matching:
- Facial recognition: The user’s selfie or video frame is compared to the document portrait using landmark-based and deep-learning similarity algorithms.
- Liveness classification: The video is scored against anti-spoofing models trained to detect printed photos, replayed videos, screen reflections, deepfake textures, irregular blink patterns, and abnormal rendering artifacts.
- Behavioral signal validation: The system assesses micro-behavior patterns such as camera movement stability, latency, and environmental consistency.
The output is a biometric confidence score indicating the likelihood that the person is genuine and matches the submitted document.
Step 3: Risk Intelligence and Compliance Screening
The platform enriches the identity data by checking:
- Sanctions and PEP lists (OFAC, UN, EU, FCA, MAS, and others)
- Regulatory risk profiles based on geography
- Fraud attempt history within the Sumsub network
- IP risk scoring, proxy detection, and device reputation databases
- Cross-checks against adverse media and law enforcement data sources
All information is translated into a single risk score tailored to the client’s jurisdiction and regulatory obligations.
Phase 3: Decisioning, Routing, and Lifecycle Enforcement
Step 4: Rules Engine and Workflow Logic
Sumsub applies the client’s verification logic using configurable conditions. These rules determine whether the case is:
- Instantly approved,
- Queued for secondary checks,
- Escalated for manual review,
- Routed to enhanced due diligence (EDD), or
- Automatically rejected.
Example logic may include:
IF biometric_match > 95% AND document_valid = true AND risk_score < 25 → Approve
IF risk_score between 25–60 → Manual review
IF VPN_detected = true AND region = HighRisk → Request additional proof
IF KYC_level = Tier2 → require address verification
Step 5: Final Result and Platform Action
Possible outcomes:
- Immediate Approval: The onboarding completes in under 30 seconds with no human intervention.
- Manual Review: Cases are routed to trained reviewers with a structured evidence pack containing anomalies, extracted text, video segments, metadata, and AI recommendations.
- Additional Verification Needed: The system prompts the user to correct or supplement the submission.
- Rejection: If multiple validation layers indicate inconsistencies, the system issues a compliant decline response.
Step 6: Post-Verification Continuous Monitoring
Once a user is verified, the system continues to monitor them and quietly rechecks them against updated sanctions and PEP lists. If something risky happens, like an unusual transaction or an expired document, the platform may trigger re-verification or alert a reviewer. This ongoing oversight helps maintain compliance and strengthens long-term fraud protection.
What is the Business Model of the Sumsub Platform?
Sumsub runs a SaaS compliance platform that charges businesses for identity verification, fraud prevention tools, and automated onboarding flows. Clients normally subscribe to a plan, and may also pay based on verification volume if their user activity grows or spikes. This model lets Sumsub scale revenue efficiently, while delivering measurable compliance value to fintech, crypto, and other high-risk digital industries.
Sumsub uses a hybrid SaaS revenue model that includes subscriptions and consumption-based pricing.
Subscription Tiers
Companies pay a recurring platform fee based on features, usage allowances, and support level. Smaller organizations typically start with core verification features while large enterprises opt for advanced automation and case management tools.
Usage-Based Pricing
Clients pay per verification, AML check, business verification, or monitored transaction. This model scales naturally with onboarding volumes and makes costs predictable relative to business growth.
Premium Add-ons
Additional revenue comes from specialized modules, including advanced AI fraud detection, workflow customization, analytics dashboards, and Unilink integrations. This layered model increases average revenue per customer and encourages long-term product adoption.
Industry estimates suggest that Sumsub generates annual revenue in the range of $94M to $100M with strong revenue per employee and a steadily growing headcount.
Financial and Market Performance
Sumsub has demonstrated strong revenue growth and increasing profitability. The company reported more than £1M in profit during 2022 and is estimated to have exceeded £3M the following year. Earlier estimates placed total revenue around $45M in 2022 and current estimates indicate nearly double that figure based on expanded market penetration.
Client case studies consistently report improvements including higher onboarding completion rates, faster verification speeds, fewer manual reviews, and significant reductions in fraudulent user attempts. These outcomes contribute directly to customer retention and increased usage over time.
Funding History
Sumsub’s growth has been supported by multiple funding rounds, including:
- Seed round in 2017 led by Flint Capital and Ilya Perekopsky
- Series A round in 2020 valued at roughly $6M with participation from MetaQuotes
- Series B round in 2022, valued at approximately $30M, led again by Flint Capital
Across all rounds, the company has raised more than $36M, supporting international expansion, infrastructure scaling, and ongoing product development.
Other Business Models for Global KYC Identity Platforms
As the digital identity verification market matures, companies are experimenting with different revenue models to serve distinct customer profiles, address regulatory pressures, and support onboarding patterns. While hybrid SaaS plus usage pricing has become a common standard, several alternative structures have proven just as viable.
Some emphasize flexibility and scale, while others focus on compliance guarantees or developer-led product adoption. Together, these models illustrate how diverse and strategically complex the identity infrastructure economy has become.
1. Transaction-Based Pure Play Model
This model represents the simplest value exchange. Clients only pay for completed verifications with no subscription commitments. It has been especially effective for companies like Veriff and iDenfy that targeted early stage, cost-conscious platforms looking for predictable variable pricing instead of long onboarding contracts.
How It Works in Practice:
Veriff is a clear example. Pricing typically ranges from $1.50 to $2.50 per verification, with meaningful volume discounts:
- 1,000 to 10,000 monthly checks: approximately $2.10 each
- 10,001 to 50,000: roughly $1.80 each
- 50,001 to 200,000: roughly $1.50 each
- 200,001 or more: enterprise negotiated pricing
This structure reduces procurement friction and aligns spend to user acquisition cycles, making it ideal for crypto platforms, marketplace ecosystems, and gaming businesses with unpredictable verification spikes.
iDenfy demonstrates how aggressive pricing can fuel growth. With rates between $1.50 and $4.00 per check, the company reported more than 300 percent year-over-year revenue growth and now generates over $15 million annually.
2. Enterprise Licensing With Compliance Guarantees Model
In heavily regulated industries, compliance is not optional. Financial services, travel, insurance, and high-risk crypto institutions often require guarantees around accuracy, response time, and regulatory continuity. Companies like Jumio and AU10TIX have built premium enterprise businesses around these needs with long-term contracts and dedicated support frameworks.
Premium Pricing for Risk Mitigation:
Enterprise agreements often include:
- Guaranteed accuracy and uptime
- Dedicated compliance and success teams
- 24/7 implementation and technical support
- Regulatory monitoring and ongoing compliance adaptation
Annual contract values commonly range from $500,000 to more than $5 million, depending on scale and requirements. On a per-verification basis, pricing typically includes:
- Standard identity verification: $3 to $8
- Enhanced due diligence: $15 to $25
Some providers back these agreements with compliance insurance or penalty clauses worth over $1 million per enterprise client.
Jumio has secured contracts with global financial institutions and leading crypto exchanges, resulting in approximately $150 million in ARR in 2023 with retention rates above 95 percent and average contract terms between three and five years.
3. Freemium and Developer-First Ecosystem Model
Inspired by the success of API-first platforms such as Stripe and Twilio, several KYC providers have adopted developer-first go-to-market strategies. The goal is to make experimentation effortless so that engineers can build verification into onboarding flows before the business formally commits. Onfido is one of the most notable companies using this approach.
Tiered Access Structure:
- Free tier: up to 500 monthly checks with basic verification
- Growth tier: approximately $0.75 to $1.50 per check
- Pro tier: approximately $0.50 to $1.00 per check for large volumes
- Enterprise tier: fully customized pricing and capability access
The conversion funnel is the strategic engine. About 97 percent of users begin on the free plan. Roughly 42 percent convert to paid usage within six months. Paying users generate an average of $8,500 per month, which creates a strong recurring base.
Over time, Onfido has onboarded more than 15,000 companies and more than 50,000 developers. More than 150 workflow extensions and integrations have emerged from the ecosystem, many of which are monetized.
How to Build a Sumsub-like Global KYC Identity Platform?
Building a Sumsub-like KYC platform starts with a compliance-focused architecture that stores and processes identity data in line with regional rules. You would then add AI verification, biometric matching, and a risk engine that adapts to behaviour and jurisdiction, so the system can intelligently approve or escalate users.
We’ve done this for multiple clients already, and we know the technical roadmap that ensures the platform performs reliably and stays compliant.
1. Compliance Architecture
We architect a cloud environment that respects regional data sovereignty by configuring sovereign cloud infrastructures, assigning regional storage zones, and implementing a central control plane that manages identity flows without violating cross-border regulations or compliance frameworks.
2. AI Verification Stack
We develop a verification stack that includes document authenticity detection models, biometric face matching with liveness validation, and device fingerprinting systems to identify tampering, prevent spoofing, and block repeat fraud attempts across different user environments and platforms.
3. Risk and Orchestration
We build a real-time scoring system that evaluates identity submissions using risk algorithms and behavioural indicators, then power it with a no-code workflow builder so compliance teams can adjust rules, escalation logic, and verification paths without developer involvement.
4. AML and Screening
We connect the platform to multiple AML intelligence providers, sanctions lists, PEP watchlists, and adverse media signals, while also enabling continuous rescreening and Travel Rule compliance for high-risk financial and crypto-driven onboarding scenarios.
5. Secure SDKs
We create secure SDKs that optimize identity capture across camera types, lighting conditions, and network environments, while embedding anti-spoofing protections and transport-level encryption to safeguard biometric and personal data during every interaction.
6. Review and Audit
We develop internal compliance modules, including review dashboards, structured case queues, escalation workflows, and forensic-grade audit logging so teams can perform oversight, respond to flagged cases, and maintain readiness for regulatory audits.
Key Challenges of a Sumsub-like Global KYC Identity Platform
Building an enterprise-grade global identity verification platform is not just an engineering challenge. The hardest problems appear when regulation, fraud innovation, operational scale, and user experience collide. After deploying KYC platforms for fintech, crypto, gaming, and regulated financial institutions across continents, these are the recurring challenges that determine whether a platform succeeds or fails.
1. Data Localization and Regulatory Conflicts
Global KYC systems must operate within drastically different privacy environments. User onboarding in Germany, Singapore, Brazil, and the United States is subject to regulations that often contradict each other. A single centralized infrastructure cannot meet the requirements of GDPR, LGPD, PDPA, and U.S. regulatory expectations simultaneously.
The Reality
- Over 200 jurisdictions with inconsistent data rules
- Conflicts between the right to deletion and AML investigative retention
- Strict requirements for where biometric and PII data can reside
- Compliance risk when all traffic is routed to one global data center
Solution: Distributed Encrypted Data Zones
- Regional data pods store and process raw identity data within legal boundaries
- Encrypted metadata is shared globally as anonymized risk signals
- User traffic is routed based on country, IP location, or declared jurisdiction
- A single dashboard allows compliance teams to monitor activity without violating regional privacy laws
2. False Positives and Conversion Loss
Verification workflows often reject legitimate customers because the system overcorrects for fraud risk. Overly strict rules typically punish users with slightly damaged documents, inconsistent lighting, or common names that trigger sanctions alerts.
Root Causes
- Detection thresholds tuned too aggressively
- Name matching logic returning false sanctions hits
- Binary approval models with no contextual evaluation
- Uniform rules applied across regions with different document standards
Solution: Dynamic Risk-Based Verification
- Contextual risk scoring evaluates behavioral signals, device data, and geography
- Tiered verification adapts requirements based on detected risk
- Human review decisions continuously retrain detection models
- Thresholds can be tested and optimized through ongoing experimentation
3. Deepfake and Synthetic Identity Fraud
Fraud has evolved beyond stolen IDs and poor-quality printouts. Deepfake face swaps during video checks, AI-generated documents, and synthetic identity profiles are now common and increasingly difficult to detect with traditional KYC checks.
Emerging Attack Patterns
- Real-time face replacement during video liveness checks
- AI-generated or modified identity documents
- 3D printed masks bypassing basic liveness detection
- Coordinated bot-driven attack waves targeting weak validation layers
Solution: Layered Adversarial Identity Defense
- Deepfake detection models identify texture irregularities and unnatural micro-expressions
- Behavioral biometrics analyzes movement, timing, and interaction style
- Randomized liveness tasks prevent pre-recorded or automated responses
- Cross-validation checks ensure document data, facial biometrics, and behavioral signals align logically.
Digital Identity Platforms Cut Banking Costs by 80–90% for Businesses
Digital identity platforms reduce banking costs by automating verification, reducing reliance on branches, and streamlining compliance through AI and secure credential checks. A 2019 analysis showed digital accounts are 80–90% cheaper to provide than traditional in-branch onboarding, and that margin will likely grow as systems mature.
So if a business wants scale, speed, and lower operational burden, digital identity quickly shifts from an upgrade to an essential infrastructure layer.
The Real Cost of Traditional Onboarding
Opening an account in person feels simple to the customer. From the bank’s perspective, it’s anything but.
Direct Cost Drivers:
| Operational Element | Cost Weight | Notes |
| Staff involvement | High | 2–3 employees spending up to 60 minutes per onboarding |
| Physical documents | Medium | Printing, scanning, archival, retrieval, secure disposal |
| Compliance labor | High | Manual identity checks, AML review, exception case handling |
| Branch infrastructure | Very High | Rent, utilities, security systems, insurance, depreciation |
Hidden Indirect Costs:
- Limited reach: branches cap market penetration
- Restricted operating hours: onboarding tied to business hours
- Human error: manual systems lead to 15–20% correction loops
- Scalability ceiling: onboarding grows linearly — more customers = more staff
When everything is counted, traditional onboarding typically costs $75–$150 per customer, and in high-regulation markets (like the EU or Singapore), even more.
The Digital Identity Model
Digital onboarding compresses what used to take an hour, three staff members, and multiple systems into a streamlined digital flow:
- User captures ID and facial biometrics via mobile or web
- The system verifies identity via automated document and biometric integrity checks
- Sanctions and politically exposed person (PEP) lists auto-screen
- Compliance logs, timestamps, and audit records are generated instantly
Onboarding costs drop to $5–$15 per customer, with processing time measured in seconds rather than hours.
1. Zero Physical Banking Footprint
Digital identity platforms remove the need for branches, filing rooms, storage, and identity hardware, which shifts banking from fixed real estate to elastic cloud infrastructure. Because the entire onboarding layer is virtual, banks avoid rent, physical compliance storage, and hardware renewal cycles, which can drive up to a 95% reduction in real estate and facility-linked onboarding costs.
2. Workforce Efficiency and Redistribution
Instead of multiple employees verifying documents, escalating cases, and managing approvals, digital identity creates an automation-first workflow in which AI handles 85–95% of checks, with humans only stepping in for flagged cases. This shift allows one compliance manager to oversee what once required a full branch team, and banks report onboarding throughput improving by 20–30× per full-time employee.
3. Automated Document Processing
Manual identity verification requires scanning, visual inspection, data entry, and form validation, which slows onboarding and introduces errors. Digital identity replaces this stack with OCR and biometric integrity checks that operate with over 99.5% accuracy, and this automation cuts document handling costs by roughly 85–90%.
4. Instant Global Reach
Traditional geographic expansion requires licensing, leasing, staffing, and localization, which often takes a year or more, while digital onboarding replaces this with configuration of rules, language packages, and regulatory presets. Because deployment is software-driven rather than physical, time to market drops from 12–24 months to an average of 3–6 weeks.
Tools & APIs Needed for a Sumsub-like Global KYC Identity Platform
Building a global KYC solution on the scale of Sumsub or Onfido isn’t about choosing a single tech stack. It’s about assembling an ecosystem where security, compliance, machine learning, infrastructure, and user experience operate together. Each component exists to solve a specific regulatory, operational, or fraud-prevention challenge rather than functioning in isolation.
1. Cloud Architecture
A platform built for global financial and compliance environments cannot operate from a single region. It needs a distributed multi-cloud model including AWS, GCP, Azure, or a hybrid.
Key requirements include:
- Data sovereignty as a baseline expectation to comply with GDPR, PIPL, and national ID regulations
- A separation of control planes from data planes so metadata can be coordinated globally without transferring protected assets
- Multi-region failover spanning at least three geographic recovery zones
- Elastic resource scaling for onboarding spikes driven by regulatory deadlines, seasonal financial activity, or crypto adoption cycles
2. Kubernetes and Docker
Kubernetes becomes foundational once the system evolves into dozens of microservices. Containerization ensures:
- Deployment consistency across development, staging, testing, and production
- Independent scaling of compute-intensive services such as OCR or liveness detection
- Immutable runtime environments suitable for audit requirements
- Efficient resource allocation across globally distributed clusters
2. AI, Biometrics, and Document Intelligence
Fraud detection drives the core value of a KYC platform. Machine learning is not a single model. It is a continuously evolving set of models that are retrained against emerging fraud behavior.
TensorFlow and PyTorch
Teams constantly refine detection models to recognize forged IDs across thousands of document types and synthetic manipulations. These frameworks also support liveness and anti-deepfake models that combine behavioral cues, visual patterns, and timing signals. Alongside this, anomaly detection models help uncover synthetic identities and coordinated fraud networks.
OpenCV
Before verification, documents must be cleaned and normalized by reducing glare, correcting alignment, and segmenting. OpenCV also detects embedded security features such as holograms, microtext, UV ink, or IR layers. Once processed, consistent biometric vectors and identity fields are extracted for accurate matching.
Deepfake Defense Requires Continuous Adaptation
As fraud tools evolve, detection systems must adapt just as quickly. Multimodal signals such as rPPG patterns, texture inconsistencies, and device data help differentiate real users from AI-generated content. Continuous adversarial training and hardware-level authenticity checks strengthen the platform against emerging deepfake attack techniques.
3. Event Streaming
A single verification triggers parallel tasks like identity parsing, biometric validation, AML checks, and device profiling. Kafka or AWS Kinesis makes this possible by coordinating concurrent workflows, maintaining immutable event logs, enabling replay for audits or model improvements, and synchronizing data globally while respecting residency rules.
Compliance, Screening, and Verification Integrations
Government and third-party integrations require resilient fallback logic and standardized data models to handle inconsistent regional formats. They must also enforce country-specific rules around data retention, sharing, and approved verification methods.
Watchlists and Sanctions Monitoring
Screening must run continuously, using subscription-based access to sanctions, PEP, and adverse media data. Fuzzy matching and relationship mapping help detect name variations, indirect associations, and hidden ownership links.
Address Verification and Utility Consumers
Address validation relies on OCR and NLP to interpret regional formats, then cross-checks results against telecom, financial, or bureau data. Behavioral and IP signals add another layer of consistency and fraud detection.
4. Security and Cryptography
Encryption is not enough when dealing with identity and biometric information.
HSMs Are Required
Hardware security modules enable:
- Secure and isolated key storage
- Cryptographic processing in tamper-resistant environments
- Compliance with banking, eID, and data protection requirements
- High-throughput performance under heavy onboarding volume
End-to-End Encryption Applied Everywhere
Sensitive data must be secured at all stages, including:
- Field-level encryption within databases
- Zero-knowledge proof techniques when applicable
- Secure enclaves for biometric processing
- Forward-secure communication protocols
5. SDKs and Client-Side Intelligence
User experience defines conversion. The platform must operate seamlessly across native iOS, Android, and web environments.
Key priorities include:
- Direct access to camera hardware with real-time feedback
- A consistent API layer across Swift, Kotlin, and React Native
- Adaptability to varied device performance and network quality
WebAssembly for Local Acceleration
Running OCR and preprocessing locally provides:
- Faster onboarding flows
- Reduced necessary bandwidth
- Optional offline verification in limited-connectivity regions
- Improved privacy posture by avoiding unnecessary file uploads
Conclusion
Building a Sumsub-like global KYC platform isn’t just another software sprint; it’s the foundation for compliance infrastructure, fraud prevention, and a scalable SaaS engine. Suppose you architect it right with a modular verification pipeline, adaptive machine learning models, and a regulatory framework that evolves with jurisdictional requirements. In that case, the platform can shift from being a backend requirement to a strategic product that drives trust, reduces fraud losses, and unlocks global onboarding without friction.
Looking to Develop a Global KYC Identity Platform?
IdeaUsher can help you build a global KYC identity platform by integrating biometric verification, secure document parsing, and compliance-ready workflows. Their developers might design APIs that scale across regions and work with evolving regulatory standards. You would also get continuous support for testing, deployment, and performance tuning so the platform stays accurate and resilient.
Why Build With Us?
- 500,000+ Hours of Code & Ex-MAANG/FAANG Expertise: Our battle-tested engineers, with roots in tech giants, design for scale, security, and seamless user experience from day one.
- More Than Just KYC Checks: We build full-cycle platforms that integrate smart onboarding, real-time fraud nets, AML screens, and transaction monitoring into a single, powerful engine.
- Focus on Your Business Logic: We handle the daunting tech, global data compliance, adversarial AI models, and no-code orchestration, so you can focus on growth and conversion.
Let’s build the identity verification platform that becomes your competitive moat.
Work with Ex-MAANG developers to build next-gen apps schedule your consultation now
FAQs
A1: It usually takes eight to fourteen months because you need to design secure data pipelines, integrate biometric verification, and meet regulatory requirements across multiple regions, and this timeline may stretch if you add advanced AI risk scoring or complex workflow automation.
A2: If you are operating at high verification volume and have long-term product ambition, then owning the platform will usually become more cost-efficient after scale, because you remove vendor markup and gain flexibility to optimize infrastructure and compliance operations over time.
A3: Yes, and many companies do exactly that by offering per verification or per user billing models, and once you stabilize compliance logic and automation, you can expand with add-ons like risk scoring, AML screening, and fraud modules, which increase revenue predictably.
A4: When biometric systems are designed with strong encryption, tokenized storage, and optional on-device inference, they often outperform traditional verification methods because biometric templates are harder to spoof and can be validated against liveness checks and continuous trust signals.