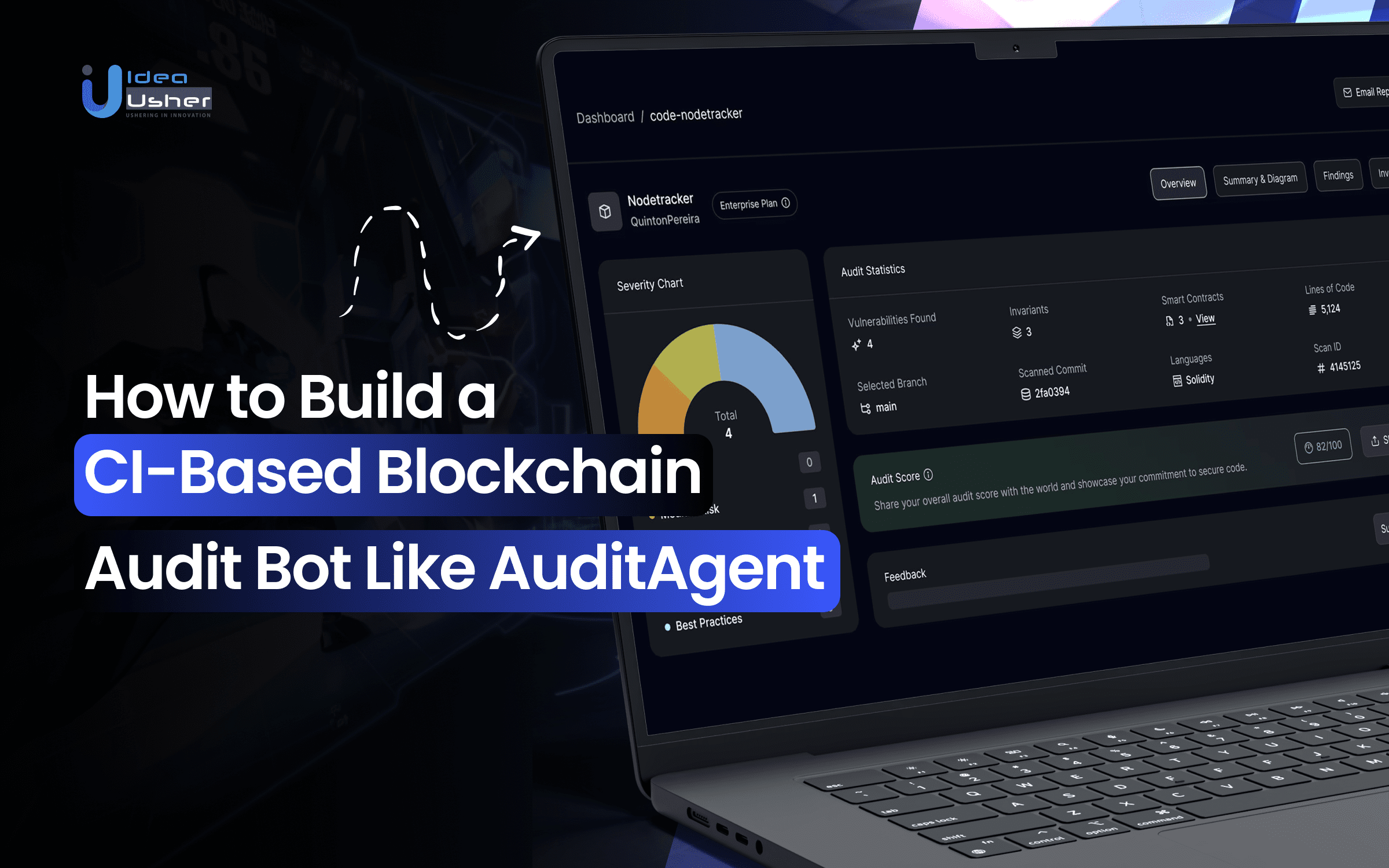
As blockchain technology grows, so do the risks, especially when it comes to smart contract security. With billions of dollars at stake, even the smallest vulnerability can lead to huge financial losses. Manual audits have their place, but they just can’t keep up with the pace of development these days. Here, CI-supported audit bots play their role, working behind the scenes to continuously scan code for vulnerabilities as developers push new updates.
It’s like having an extra layer of protection built right into your workflow, catching potential issues early before they snowball into something much worse. It’s a smarter, faster way to stay secure.
With our experience building CI-based blockchain audit bots that automatically run security tests and integrate seamlessly into development workflows, IdeaUsher can ensure both high-severity vulnerabilities and minor inefficiencies are detected, optimizing not only security but also performance. So, we’re sharing this blog to help you understand how to automate your smart contract security in a way that enhances both safety and development efficiency.
Key Market Takeaways for CI-Based Blockchain Audit Bots
According to MarketUS, the blockchain security market is set for remarkable growth, projected to skyrocket from $4.3 billion in 2024 to $877.1 billion by 2034. This growth reflects a rising need for stronger, scalable security as blockchain becomes more embedded in industries like finance, supply chains, and digital assets. North America is currently leading the way, holding more than 37% of the market share in 2024.
Source: MarketUS
CI-based blockchain audit bots are becoming increasingly popular due to their ability to automate crucial security tasks like compliance checks and smart contract audits. These bots integrate AI with blockchain data, offering continuous monitoring, anomaly detection, and real-time vulnerability assessments, significantly improving efficiency and reducing the need for manual intervention.
Major firms like PwC and Ernst & Young are embracing these technologies. PwC’s audit system, for instance, has helped reduce manual reconciliation time by up to 90% and flagged millions in suspicious transactions. Similarly, EY’s blockchain analyzer uses advanced methods like zero-knowledge proofs to ensure asset authenticity while maintaining privacy, demonstrating the growing role of automation in blockchain security.
What is a CI-Based Blockchain Audit Bot?
A CI-based blockchain audit bot is an automated tool integrated into Continuous Integration systems to scan smart contract code for potential vulnerabilities before it’s deployed. This bot functions like an automated spellcheck for security flaws, providing instant feedback as the code is updated or committed. It identifies and flags issues that could lead to exploits, saving time and reducing the risk of costly errors.
How It Fits Into CI/CD Pipelines
- GitHub Actions/GitLab CI: The bot is triggered automatically when code is pushed to the repository, ensuring that security scans are part of the development workflow.
- Real-Time Scanning: It inspects every change for possible risks such as reentrancy attacks or gas inefficiencies, alerting the development team immediately.
- Blocking Vulnerable Code: If critical vulnerabilities are detected, the bot can prevent the code from being deployed, acting as a security gate that stops harmful updates.
For example, when a developer pushes Solidity code, the bot might flag an unchecked call.value() as a potential reentrancy risk, preventing a vulnerability from reaching production.
What is AuditAgent by Nethermind?
AuditAgent is Nethermind’s AI-powered audit bot designed to automate the auditing of Ethereum smart contracts. It utilizes AI models and advanced techniques like static analysis, symbolic execution, and multi-agent simulations to identify vulnerabilities that traditional tools might miss.
Key Components of AuditAgent
- AI-Powered Detection: The bot leverages AI models trained on historical exploit data, such as the Nomad Bridge hack, to identify security issues. It goes beyond simple syntax checks and can spot business logic flaws like incorrect fee structures.
- Continuous Pre-Audits: Instead of waiting for a one-off audit, AuditAgent scans every Git commit, making the security review process continuous.
- Structured Fix Suggestions: When a vulnerability is found, AuditAgent provides actionable code patches (e.g., advising the developer to replace transfer() with call() to prevent gas starvation).
Unique Features of AuditAgent
- MAS Attacker Modeling: It can simulate coordinated attacks like flash loans and price oracle manipulations to predict potential exploit scenarios.
- Tokenomics Validation: AuditAgent also evaluates the economic setup of smart contracts, checking for issues like unbalanced liquidity pools or other tokenomics vulnerabilities.
How AuditAgent Differs From Traditional Audit Tools
| Feature | Traditional Tools | AuditAgent |
| Analysis Type | Static rules (e.g., Slither) | AI + symbolic execution |
| Business Logic Checks | Limited | Validates tokenomics & game theory |
| Attack Simulation | Single-contract flaws | Multi-agent exploit scenarios |
| Output | Generic warnings | Actionable fixes with code snippets |
For instance, while a traditional tool might flag a missing onlyOwner modifier, AuditAgent might simulate a full governance takeover, testing for potential vote manipulation under attack scenarios.
Why Are Businesses Adopting CI-Based Blockchain Audit Bots?
Businesses use CI-based blockchain audit bots to prevent costly exploits, speed up development, and stay compliant with regulations. They also help build trust by continuously securing code.
- Prevent Costly Exploits: With billions lost in smart contract hacks each year, CI bots like AuditAgent help prevent vulnerabilities from being deployed in the first place, saving businesses from expensive breaches.
- Faster Development Cycles: CI-based audit bots enable developers to detect and fix issues as they go, eliminating delays associated with waiting for manual audits.
- Regulatory Compliance: Automated auditing is crucial for complying with increasing regulations like MiCA (EU) and the SEC (US), which require strict security practices for blockchain projects.
- Competitive Advantage: Projects that prioritize continuous security audits can attract more users and investors, enhancing their market reputation and trustworthiness.
How a CI-Based Audit Bot Like AuditAgent Works?
AuditAgent works by integrating into your CI/CD pipeline, automatically scanning every commit and pull request for vulnerabilities. It uses AI to understand code intent, detect logic flaws, and prioritize risks based on severity. The bot then provides actionable feedback, helping developers catch issues early without disrupting the workflow.
1. Differentiating Benign vs. Malicious Code Patterns
Unlike traditional static analyzers, which primarily rely on rule-based detection (e.g., “check for reentrancy”), AuditAgent leverages advanced AI and Machine Learning (ML) models to better understand the context of the code. Here’s how:
AI Models for Semantic Solidity Understanding: AuditAgent uses models from OpenAI, Anthropic, or custom Large Language Models to:
- Understand Code Intent: For example, it can determine if a function is meant to be restricted to admins.
- Detect Logic Deviations: It checks for unexpected behaviors, such as a function that allows arbitrary token minting when it shouldn’t.
Detecting Business Logic Flaws: Traditional tools often miss vulnerabilities that involve economic and governance logic. AuditAgent specifically looks for:
- Tokenomics Exploits: Problems like flawed staking rewards.
- Access Control Bypasses: Issues such as missing onlyOwner checks.
- Oracle Manipulation Risks: Vulnerabilities like price feed dependencies being exploited.
LLMs for Contextual Analysis: By using LLMs, AuditAgent reads documentation (NatSpec comments) and compares the code against known attack patterns to ensure the code aligns with its intended behavior. For instance, it may check if the code resembles past exploits, like the Nomad Bridge hack.
2. Integrating With Development Pipelines
Audit bots like AuditAgent are designed to fit seamlessly into CI/CD pipelines, ensuring security checks are automated and integrated throughout the development process:
CI/CD Platform Support: AuditAgent can be integrated with popular CI platforms like:
- GitHub Actions
- GitLab CI/CD
- Jenkins
- CircleCI
Automated Scanning Triggers
Scans are triggered in real-time at various stages to catch vulnerabilities. The bot checks every commit for critical flaws as soon as changes are made, runs a full analysis of pull requests before merging, and performs periodic branch scans (e.g., nightly) to maintain ongoing security.
Feedback Without Blocking Developers:
In non-blocking mode, the bot alerts developers through PR comments, allowing them to fix issues without blocking merges. In blocking mode, it halts deployment for critical vulnerabilities, ensuring that only secure code is pushed to production.
3. Orchestrating Multiple Analysis Techniques
AuditAgent employs a hybrid security analysis stack to detect and analyze vulnerabilities using multiple techniques:
| Technique | Tool Example | Purpose |
| Static Analysis | Slither, Semgrep | Conducts fast syntax-level checks |
| Symbolic Execution | Mythril, KEVM | Identifies edge-case paths |
| Fuzzing | Echidna, Foundry | Tests with random inputs for unknown flaws |
| Formal Verification | Certora, SolCMC | Provides mathematical proof of correctness |
AI-Powered Prioritization: AuditAgent’s AI models help prioritize vulnerabilities, so developers aren’t overwhelmed with hundreds of low-severity findings. It:
- Ranks vulnerabilities by likelihood (e.g., “High: Reentrancy in withdraw()”).
- Groups related issues (e.g., all functions missing access control).
- Suppresses false positives, improving efficiency by learning patterns from previous audits.
4. Learning and Adapting to New Threats
AuditAgent is designed to learn and adapt over time, using data to keep up with evolving threats:
Continuous Learning Loop: The bot ingests new data from:
- Past audits from Nethermind’s internal database.
- Exploit reports from platforms like Immunefi and Rekt.News.
- Bug bounty submissions from sites like HackerOne.
Retraining Models: The bot’s AI models are updated weekly to incorporate new attack patterns and improve detection capabilities.
Anomaly Detection for Zero-Days: AuditAgent establishes a baseline of “normal” code patterns by analyzing over 10,000 verified contracts. This helps it spot zero-day exploits by flagging code that deviates from this baseline.
5. MAS Attacker Models for Multi-Step Exploits
Traditional audit tools typically focus on single-contract vulnerabilities, but they fail to detect multi-step, cross-contract exploits. AuditAgent overcomes this limitation with Multi-Agent Systems (MAS) simulations, which model both malicious and benign agents interacting within the contract environment.
Why Single-Agent Analysis Fails: Single-agent analysis doesn’t account for complex attack paths, such as:
- Cross-contract exploits: A flash loan followed by price manipulation and fund draining.
- Time-dependent attacks: Like governance proposal frontrunning or other attacks dependent on market timing.
MAS Simulation
AuditAgent models various agents within the system, including malicious agents like arbitrage bots or governance attackers, benign agents such as normal users and protocol keepers, and environmental factors like market conditions and gas fees to simulate realistic attack scenarios.
Example Attack Scenario: The bot might simulate a scenario where:
- Agent A takes a flash loan.
- Agent B manipulates an oracle price.
- Agent C exploits the price discrepancy to drain funds.
AuditAgent would reconstruct this attack path and issue a warning, for example: “Possible flash loan exploit vector in executeTrade().”
Benefits of Building a Blockchain Audit Bot for Businesses
Building a CI-based blockchain audit bot cuts down on manual audit costs and speeds up fixing issues. It helps prevent security breaches, protecting your reputation and keeping users confident. Plus, it ensures you’re meeting regulatory requirements, which makes your project more attractive to investors.
Technical Advantages:
- Early-Stage Vulnerability Detection: By catching flaws during development, a CI-based audit bot reduces the attack surface and prevents risks like reentrancy or oracle manipulation from reaching production, ensuring real-time security as code is written.
- Faster Remediation Cycles: Developers get immediate feedback with vulnerability alerts and AI-powered fix suggestions, minimizing debugging time and eliminating delays typically caused by manual audits.
- Customizable Rule Sets for Your Protocol Logic: The bot can be tailored to detect specific risks for your protocol, such as flash loan attacks for DeFi or proposal hijacking in governance systems, adding custom checks for business-specific needs.
Business Advantages:
- Reduce Cost of Third-Party Audits Over Time: CI-based bots can cut down audit costs by over 70%, handling routine checks while leaving expensive manual audits to focus on complex protocol logic.
- Mitigate Brand & Reputation Risk from Exploits: By preventing hacks and exploits, these bots help protect your project’s reputation, making your security measures publicly verifiable, which builds trust with users.
- Maintain Compliance Posture for Partners & Investors: Automated audits ensure ongoing compliance with regulatory frameworks like MiCA (EU) and SEC (US), making the project more appealing to institutional partners.
- Enable Secure Feature Deployment Velocity: With automated security checks, teams can deploy features quickly without waiting for time-consuming audit results, supporting agile development and rapid iteration.
How to Build a Blockchain Audit Bot Like AuditAgent?
We understand the critical importance of blockchain security. That’s why we developed a custom CI-based blockchain audit bot, similar to AuditAgent, to streamline security checks for our clients. Our solution automates vulnerability detection in real-time, helping teams catch issues early and ensure secure deployments. Here’s how we build and integrate the bot for our clients.
1. Design the Audit Bot Architecture
We begin by designing a bot architecture that fits seamlessly into your CI/CD pipeline. The bot is set up with a trigger mechanism that activates the audit process and a reporting layer that keeps your team updated on any findings. We work with you to determine whether the bot should run on the dev, testnet, or mainnet, ensuring that security checks are both efficient and secure.
2. Set Up CI/CD Integration
The next step is integrating the bot into your CI/CD workflow using platforms like GitHub Actions, GitLab CI, or Jenkins. We configure the bot to automatically trigger security scans on every commit, push, or pull request, catching vulnerabilities before they reach production and ensuring real-time security during development.
3. Integrating Analysis Tools
We integrate both static and dynamic analysis tools into the process. Tools like Slither are used for static checks, while Mythril or Manticore are added for symbolic analysis to detect potential vulnerabilities at runtime. Additionally, Echidna is used for fuzzing to uncover unexpected behaviors by testing the system with random inputs.
4. Embed AI/ML Models
To enhance vulnerability detection, we embed AI and machine learning models into the bot. Using pre-trained LLMs, the bot can better understand the context of the code and flag vulnerabilities based on the intent. We also set up anomaly detection pipelines to monitor for unusual code patterns, while NLP or graph-based models provide actionable, structured insights for your team.
5. Add Formal Verification (Optional)
For critical components, such as financial logic, vaults, or governance systems, we add formal verification. Using tools like Certora or SMT solvers, we ensure that the code is mathematically proven to be correct and free from logical flaws, making sure high-stakes components are secure and reliable.
6. Set Up Alerts, Dashboards & Reporting
Finally, we configure alerts to notify your team in real-time via Slack or JIRA. Detailed reports in CSV or JSON format are generated, and we set up custom dashboards to help you visualize trends in vulnerabilities over time, making it easy for your team to prioritize fixes and track security progress.
Challenges & Solutions in Building a Blockchain Audit Bot
After working with numerous clients, we know exactly what challenges can arise when building a CI-based blockchain audit bot, and we’ve developed strategies to handle them effectively. Here’s a breakdown of the most common hurdles and how we tackle them:
1. False Positives & Alert Fatigue
Security tools tend to generate a lot of alerts, and when developers are bombarded with warnings, it’s easy to miss critical vulnerabilities. This “alert fatigue” can make teams ignore important issues. Over time, it can lead to developers trusting the system less.
How We Handle It:
- Precision Tuning: We fine-tune detection rules to fit your specific code and protocol, ensuring only relevant alerts show up.
- Risk-Based Filtering: We set up tiered severity systems so only the most critical vulnerabilities stop deployment, reducing the noise.
- Context-Aware AI: We integrate machine learning models that understand your code’s intent, helping the bot distinguish between real threats and harmless patterns.
2. Performance Bottlenecks
Comprehensive security scans can slow down the CI/CD pipeline, especially when you need quick deployments. This can be a real pain in fast-paced environments, where every second counts.
How We Handle It:
- Targeted Scanning: Instead of scanning the whole codebase, we focus on modified files, making the process quicker without sacrificing thoroughness.
- Intelligent Scheduling: We schedule resource-intensive scans for off-peak hours so that the pipeline isn’t slowed down during peak times.
- Distributed Processing: We break down the analysis tasks and distribute them across multiple machines, allowing parallel execution and speeding up the process.
3. Integration Complexity
Adding security tools to an already-established CI/CD pipeline can get complicated, and it may disrupt your existing workflow. This can slow down development and increase the chance of mistakes in production.
How We Handle It:
- Phased Rollout: We start by implementing basic vulnerability checks and then gradually introduce more advanced features, ensuring smooth integration with minimal disruption.
- Preconfigured Templates: To make the setup easier, we use integration blueprints from industry-standard solutions, which speeds up the process.
- Decoupled Architecture: We make sure security checks run in parallel with other tasks, rather than holding up the entire pipeline, so things continue moving smoothly.
4. Training Data Limitations
AI-powered detection depends on having quality exploit data, and many organizations don’t have enough internal data to train models effectively. This lack of data can limit the bot’s ability to spot new or complex vulnerabilities.
How We Handle It:
- Open Security Databases: We pull from publicly available vulnerability registries and incident reports to train the models and ensure they’re as accurate as possible.
- Controlled Simulation: We generate synthetic attack scenarios to increase the amount of training data, allowing the bot to recognize a wider range of threats.
- Collaborative Learning: We participate in security networks that share anonymized findings, so we can learn from the broader community and improve detection.
Tools & Frameworks for Building a Blockchain Audit Bot
To build a reliable and efficient CI-based blockchain audit bot, we leverage a range of powerful tools, APIs, and frameworks. Here’s a breakdown of the essential components we use:
1. Static & Dynamic Analysis Tools
Core Security Scanners
- Slither: A Python-based static analyzer for Solidity that identifies common vulnerabilities like reentrancy and access control issues. It requires minimal configuration and is a fast way to spot issues early.
- Mythril: A symbolic execution engine designed to explore all possible execution paths in the code, finding edge-case vulnerabilities that traditional tools might miss.
- Echidna: A property-based fuzzer that generates random inputs to test contract invariants and identify potential failure conditions, ensuring that contracts handle unexpected scenarios properly.
- Manticore: An advanced symbolic executor for deeper contract analysis. It’s particularly useful for finding vulnerabilities in multi-transaction attack vectors that other tools might overlook.
2. AI/ML & NLP Components
Intelligent Analysis Layer
- OpenAI/Anthropic APIs: These AI models enable contextual understanding of the code. They help assess business logic risks and detect issues beyond simple pattern matching, improving the bot’s detection capabilities.
- Graph Neural Networks (GNNs): By mapping the contract’s call graph, GNNs help identify dangerous interactions between functions, offering a deeper level of analysis to pinpoint vulnerabilities that arise from complex contract interactions.
- Transformer Models: These models process natural language, allowing the bot to analyze comments and documentation to ensure that the code implementation matches the intended specifications.
3. CI/CD Integration Frameworks
Pipeline Automation
- GitHub Actions: A lightweight, YAML-based CI/CD workflow tool that integrates well with Ethereum projects, offering seamless native code scanning and automation.
- GitLab CI/CD: A robust platform with built-in security dashboards and compliance reporting, providing a more comprehensive pipeline support for blockchain projects.
- Jenkins Pipelines: A flexible tool using Groovy scripting, ideal for complex enterprise environments requiring custom workflows and integrations for blockchain auditing.
4. Formal Verification Systems
Mathematical Proof Tools
- Certora Prover: An industry-standard formal verification tool that helps prove the correctness of protocol invariants and security properties, providing mathematical guarantees for smart contract security.
- Scribble: An annotation-based system that converts developer assertions into machine-checkable proofs, ensuring that the protocol behaves as intended under all circumstances.
5. Monitoring & Reporting Stack
Operational Visibility
- Tenderly: A real-time transaction simulation and alerting platform for deployed contracts. It provides instant feedback on the behavior of contracts in production, helping detect issues quickly.
- Etherscan APIs: These APIs integrate on-chain data with static analysis findings, allowing you to correlate what the code says it should do with what it’s actually doing on the blockchain.
Notification Gateways
- Discord/Slack/JIRA Connectors: Pre-built connectors route alerts to the appropriate teams, ensuring real-time communication about vulnerabilities and security issues as they arise.
Use Case: Custom Audit Bot for a DeFi Lending Platform
One of our clients, a rapidly growing DeFi lending protocol, came to us with a critical challenge: their manual audit process was slowing down feature releases, with security reviews taking weeks. Post-deployment bugs were also becoming an issue, as exploitable flaws slipped through pre-launch checks. To top it off, investors demanded stronger security, seeking continuous and verifiable protection for their platform.
What We Delivered
We provided a complete CI audit solution tailored to the needs of the DeFi lending platform, including:
- Custom rule sets to address lending-specific risks (e.g., interest rate exploits).
- LLM-powered analysis to detect novel attack patterns beyond traditional static checks.
- Ongoing tuning based on emerging threat intelligence to keep the bot ahead of new vulnerabilities.
Implementation Steps
GitHub Actions Integration
We configured automated scans to trigger on every pull request and main branch merge, ensuring continuous security checks throughout the development cycle. Failure gates were set up to block deployments containing critical vulnerabilities, such as reentrancy or oracle manipulation, preventing insecure code from reaching production.
Multi-Layered Security Analysis
We implemented a multi-layered security approach. Slither performed static analysis to quickly identify common Solidity vulnerabilities, while Mythril used symbolic execution to uncover edge-case attack vectors.
Additionally, AI Anomaly Detection flagged unusual patterns in the lending logic, helping us identify potential vulnerabilities in the mathematical models that could pose risks.
Real-Time Monitoring & Dashboards
We set up real-time tracking of vulnerabilities, with the bot catching 12 critical issues within the first three months. Auto-generated reports were automatically sent to security teams and auditors, allowing for seamless and efficient vulnerability management and timely action.
Outcome
| Outcome | Result |
| Reduction in Post-Deployment Bugs | 40% decrease, improving platform stability after launch. |
| Lower Audit Costs | 30% reduction by automating routine checks, allowing focus on complex issues. |
| Higher Investor Confidence | Continuous, provable security processes, assuring stakeholders of ongoing protection. |
This custom audit bot not only improved the security and efficiency of the platform but also provided the client with a powerful tool to scale their DeFi business confidently.
Conclusion
As we move into 2025, traditional static tools alone won’t cut it. CI-based audit bots powered by AI and simulation models are setting the new standard for smart contract security. Building an in-house solution offers more control, tailored customization, and deeper protection for platform owners and DeFi enterprises. At Idea Usher, we specialize in creating custom audit pipelines, integrating tools like Slither and AI, and offering enterprise-grade CI solutions.
Looking to Develop a CI-Based Blockchain Audit Bot Like AuditAgent?
Automating the audit process with a CI-based blockchain audit bot is the most effective way to ensure your code is secure before deployment. At IdeaUsher, we specialize in helping blockchain projects automate their security processes with CI-based audit bots that:
- Scan every code change in real-time
- Catch vulnerabilities before deployment
- Slash audit costs by 30-50%
Why Choose Us?
- 500,000+ hours of coding expertise – Our team of ex-MAANG/FAANG engineers brings specialized skills in blockchain security and AI automation.
- Custom-built for your stack – Whether you’re using EVM, Solana, Cosmos, or other chains, we tailor the solution to fit your needs.
- Proven results – Our clients have reduced exploits by over 40% with our automated security solutions.
Check out our latest projects to see how we’ve helped DeFi protocols, NFT platforms, and L2 solutions secure their code at scale.
Let us help you build a robust, scalable security framework!
Work with Ex-MAANG developers to build next-gen apps schedule your consultation now
FAQs
A1: Manual audits are a one-time process, meaning vulnerabilities can be missed between audits. A CI-based audit bot, on the other hand, continuously scans the code in real-time as it evolves, catching issues early and reducing security risks throughout development.
A2: No, CI-based bots cannot fully replace human auditors. While they automate repetitive tasks and catch common flaws, human auditors are essential for analyzing complex logic and assessing the broader implications of vulnerabilities that a bot might miss.
A3: A basic CI-based audit bot can typically be set up in 2–4 weeks using tools like GitHub Actions and Slither. However, integrating advanced AI features or custom rules may require additional time to fine-tune and implement effectively.
A4: No, AI is not strictly necessary, but it significantly enhances the audit bot’s capabilities. AI helps with prioritizing risks, understanding code context, and detecting complex or novel vulnerabilities that may otherwise go unnoticed.