As smart contracts become more widely used, and technologies like DeFi and DAOs continue to grow, blockchain security is becoming absolutely critical. With the rise of cross-chain interactions and the increasing complexity of these systems, vulnerabilities are a bigger concern than ever. In 2025, ensuring the safety of these ecosystems is essential—not just for the platforms themselves but for everyone who relies on them. If we want to maintain trust and stability in the decentralized world, security has to be a top priority.
That’s why more companies are turning to blockchain threat detection systems like Forta. These systems provide real-time monitoring, helping to catch issues before they escalate and securing platforms as they evolve
As blockchain technology grows in complexity, so does the need for intelligent, decentralized threat detection. Having worked on building custom, real-time monitoring solutions that leverage smart contract analysis and cross-chain threat detection, IdeaUsher understands how vital it is to stay ahead of evolving blockchain vulnerabilities. The purpose behind writing this blog is to guide you through the essentials of building your own robust system like Forta to protect your platform from emerging threats.
Key Market Takeaways for Blockchain Threat Detection Systems
According to DataHorizzonResearch, the blockchain security market has grown rapidly, reaching USD 5.7 billion in 2023 and is expected to grow to USD 28.6 billion by 2033. This growth is driven by the increasing use of blockchain in industries like finance, healthcare, and supply chain. As more decentralized applications (dApps) and digital assets emerge, there is a rising need for strong security measures to protect against evolving cyber threats, especially with increasing regulatory scrutiny.
Source: DataHorizzonResearch
Blockchain Threat Detection Systems are now vital to securing decentralized networks. These systems are designed to address a wide range of threats, including smart contract exploits and phishing attacks. By using real-time analytics, machine learning, and collaboration between detection models, they provide proactive defense, ensuring low false positives while improving integration with decentralized finance protocols to enhance security across blockchain platforms.
Systems like Chainalysis Hexagate, Forta, Harpie, and Phalcon are leading the way in blockchain security. Chainalysis Hexagate focuses on early detection of malicious activities, while Forta leverages machine learning for customized threat alerts. Harpie works as an on-chain firewall, protecting wallets from real-time hacks, and Phalcon stands out for its low false-positive rate, having successfully prevented significant asset losses from attacks.
What Is a Blockchain Threat Detection System?
A blockchain threat detection system is a security framework designed to monitor, identify, and prevent malicious activities across decentralized networks in real time. These systems are specifically built to address blockchain’s unique risks, such as exploits in smart contracts, flash loan attacks, front-running, governance manipulation, and fraud.
How Does It Work?
- Continuous Surveillance: The system scans transactions, smart contract interactions, and on-chain events in real time to identify suspicious activities.
- Threat Identification: It flags unusual patterns, such as sudden large withdrawals or abnormal token movements, which could signal a potential attack or exploit.
- Automated Alerts & Responses: The system sends notifications or initiates defensive actions, such as pausing contracts or blocking certain activities, to minimize the impact of detected threats.
Overview of Forta’s Blockchain Threat Detection
Forta is one of the leading decentralized threat detection networks designed to secure Web3 applications. It operates on a community-driven model, empowering independent node operators worldwide to monitor blockchain transactions and share insights.
Detection Bots
Forta uses open-source scripts, written in JavaScript or Python, to monitor blockchain transactions. These detection bots are designed to spot suspicious activities, such as flash loan attacks or reentrancy exploits, by analyzing patterns in transactions and contract interactions..
Scan Nodes
Forta’s scan nodes are operated by independent participants across the globe. These nodes process real-time blockchain data from major chains like Ethereum and Solana. This decentralized approach ensures that blockchain activity is monitored continuously, with no single point of failure, offering a more resilient and scalable way to track suspicious behavior.
Decentralized Alerting
When a detection bot flags an anomaly, the alert is sent to a shared network, ensuring there’s no central failure point. Users receive notifications through channels like Slack, Discord, or via API integrations.
No Central Authority
Forta is a fully decentralized network, powered by independent node operators and incentivized with $FORT tokens. Honest operators are rewarded, while malicious behavior is penalized through slashing. This structure ensures the network remains secure, transparent, and free from central control.
Key Advantages Over Traditional Systems
- Faster Adaptation: Community developers rapidly update bots to address new threats.
- Censorship-Resistant: Detection rules are not controlled by any central authority, ensuring neutrality.
- Lower Costs: Crowdsourcing intelligence allows for a more cost-effective system.
Types of Blockchain Threat Detection
| Detection Type | What It Does | Use Case |
| Rule-Based Detection | Uses predefined rules to flag suspicious activities (e.g., flagging transactions over a set threshold). | Catching known attack signatures. |
| Heuristic & Behavior-Based Detection | Analyzes transaction patterns, like rapid token swaps or unusually high gas fees, to detect abnormal activities. | Identifying front-running bots or wash trading. |
| AI & Machine Learning-Based Detection | Uses advanced algorithms like Graph Neural Networks (GNNs) to predict and detect attacks based on historical data and patterns. | Detecting multi-stage exploits, where a hacker tests smaller attacks before a large-scale theft. |
| Simulation & Anomaly Detection | Replays transactions in a simulated environment to check for vulnerabilities and exploits. | Preventing price oracle manipulation before it happens. |
Why Businesses Are Investing in Blockchain Threat Detection?
Businesses are investing in blockchain threat detection systems like Forta because they need to stay ahead of fast-evolving security threats. With billions lost to hacks, real-time protection is a must for maintaining trust and compliance. Plus, automated systems offer scalability and efficiency that manual monitoring just can’t match.
Rising Number of Hacks and Financial Losses
With over $3 billion lost to DeFi hacks in 2024 alone, businesses can no longer afford to be reactive. Real-time monitoring is essential to prevent significant financial losses before they occur. For example, the $197 million hack of Euler Finance could have been avoided with continuous threat detection and immediate alerts.
Compliance and Governance Requirements
Regulations such as MiCA (EU) mandate proactive security measures for blockchain networks. Blockchain threat detection systems help businesses ensure they are meeting these regulatory standards by maintaining audit trails and providing real-time insights into suspicious activities.
Customer Trust and Platform Reliability
Hacks and security breaches often lead to users abandoning platforms, as seen with Mt. Gox and Poly Network. Implementing real-time protection through blockchain threat detection strengthens platform security, improves reliability, and boosts customer retention by ensuring a safer environment.
Need for Proactive vs. Reactive Security
Traditional security approaches, like audits or bug bounty programs, are often too slow to address fast-evolving blockchain threats. Forta’s proactive system helps prevent attacks before they are executed, providing more effective and timely protection against emerging vulnerabilities.
Benefits of a Forta-like Threat Detection System for Businesses
A Forta-like threat detection system offers real-time alerts to stop attacks before they happen, keeping your assets safe. It’s decentralized, so there’s no single point of failure, and the community constantly updates it to stay ahead of new threats. Plus, it builds trust with users and regulators, ensuring your platform stays secure and compliant.
Technical Advantages
- Real-Time Threat Alerts: Forta detects malicious transactions instantly, stopping them before they can cause harm. It monitors every block for anomalies like flash loan attacks or reentrancy exploits. For example, Forta prevented a $3M exploit attempt on a DeFi protocol by automatically pausing the system to protect funds.
- Decentralized, Censorship-Resistant Intelligence: Forta’s decentralized network means there’s no single point of failure. With thousands of independent operators contributing, no entity controls the threat data. This approach is especially important in DeFi, where avoiding censorship and malicious shutdowns is crucial for maintaining security.
- Low False Positives via Simulation & ML Models: By using transaction simulation and machine learning, Forta ensures more accurate threat detection with fewer false positives. Its AI-powered system has a false positive rate of just 5-10%, far lower than the 30%+ rate of traditional systems, leading to more reliable security alerts.
- Continuous Learning Through Community Contributions: Forta thrives on contributions from a global community of developers. This open-source model helps the platform stay updated and adaptive to new attack vectors, providing faster responses to emerging threats compared to centralized systems.
Business Advantages
- Reduced Loss from Hacks & Scams: Forta helps prevent significant financial losses by detecting and stopping hacks before they can take effect. For instance, it blocked a $15M oracle manipulation attack in 2024. Real-time security also results in lower insurance premiums for businesses using it.
- Greater Investor & User Confidence: Investors and users are more likely to trust platforms with live exploit prevention. A study found that 72% of DeFi users check for Forta integration before interacting with a platform, making real-time security a key factor in their decisions.
- Regulatory Alignment (SEC, GDPR, MiCA): Forta helps businesses stay compliant with regulations like SEC, GDPR, and MiCA by providing proactive security and maintaining detailed audit logs. These logs are essential for legal compliance and can be used for insurance purposes.
- Competitive Edge in Web3 Security Infrastructure: Platforms using Forta gain a competitive advantage in the market. Well-known platforms like Aave and Compound leverage Forta as a selling point, attracting both users and developers who value secure blockchain systems.
How Forta Achieves Decentralized Security Intelligence?
Forta secures blockchain networks by using independent bots run by global operators, so there’s no central authority controlling the process. Transactions are cross-checked and validated by peers, ensuring accuracy and preventing fraud. With a reputation system and real-time threat-blocking, Forta stays ahead of evolving attacks, powered by the community.
1. Coordination Without a Central Authority
Forta operates without relying on a single central authority, utilizing three main strategies to ensure security:
- Independent Detection Bots: Global node operators run custom bots that autonomously scan transactions, preventing bottlenecks and centralization.
- Decentralized Aggregation Protocol: Forta’s peer-to-peer system allows nodes to validate findings before broadcasting them, ensuring accurate data.
- Reputation & Staking-Based Quality Control: Node operators stake $FORT tokens, earning rewards for high-performing bots and penalties for underperforming ones, ensuring reliability.
By decentralizing security intelligence, Forta prevents censorship and ensures continued network operation even if some nodes fail or act maliciously.
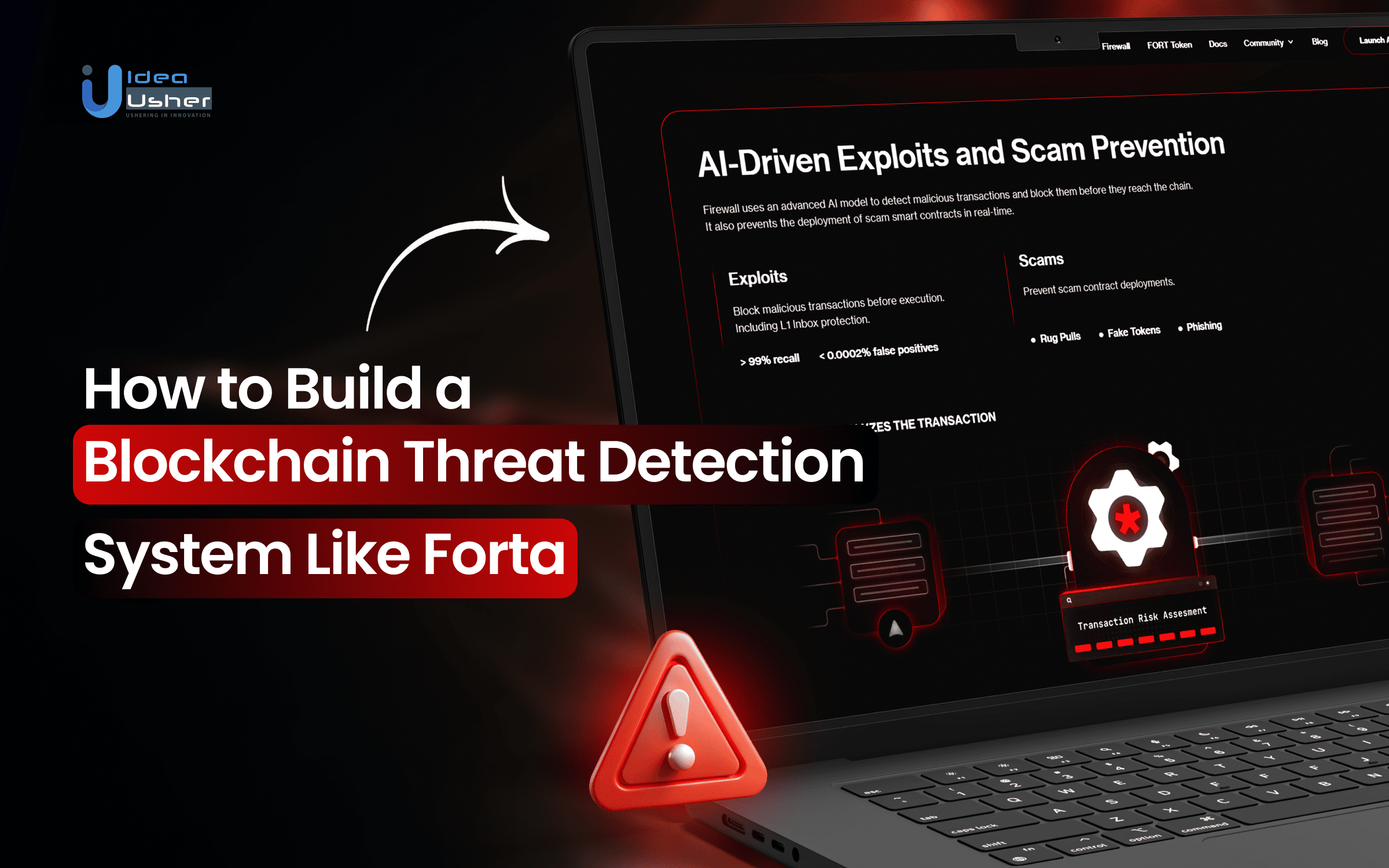
2. Forta Firewall & Transaction Prevention
Forta doesn’t just detect threats, it actively blocks them in real time using advanced techniques:
- Simulated Execution: Suspicious transactions are run through a virtual environment before they can impact the blockchain. If an exploit is identified, the transaction is flagged or auto-reverted to prevent harm.
- Validation Networks: Multiple nodes resimulate high-risk transactions to minimize false positives. Only threats confirmed by a consensus of nodes lead to defensive actions.
Example: If a flash loan attack is detected on a lending protocol, Forta can interrupt the transaction in real time, preventing funds from being drained.
3. AI & Graph Neural Networks
Forta goes beyond traditional rule-checking by incorporating AI and advanced machine learning models to detect and analyze threats:
- Cross-Chain Pattern Recognition: Graph neural networks analyze transaction patterns across different blockchains to detect complex attack chains, such as funds being moved through multiple protocols to obscure theft.
- Temporal Analysis: This method identifies slow-building attacks, such as governance attacks where malicious voting accumulates over time.
Unlike signature-based systems that rely on known patterns, Forta’s AI can detect novel attack techniques by identifying abnormal behaviors, even if they’ve never been seen before.
4. Incentive Design via $FORT Token
Forta’s cryptoeconomics ensure network integrity and encourage participants to act in the network’s best interest:
| Mechanism | Description |
| Bot Staking | Developers stake $FORT tokens to deploy bots. Malicious bots risk losing their stake. |
| Slashing | Bots that send false alerts or perform poorly lose a portion of their staked tokens. |
| Reward Curve | Bots that identify critical or unique threats early are rewarded with higher tokens. |
This incentivizes all participants to help maintain the security of the network, aligning their interests with the integrity of the system.
5. Community-Driven Bot Development
Forta’s open-source model encourages rapid adaptation and continuous improvement in detecting emerging threats:
- Public Bot Library: Anyone can contribute detection logic, enabling the network to quickly respond to new vulnerabilities. For example, after the first attempt to exploit a Balancer-style pool, a new bot was deployed just hours later to address the attack.
- Crowdsourced Improvements: The global developer community constantly refines detection bots to handle evolving attack vectors.
- Enterprise-Grade Customization: Large protocols can modify bots for their unique needs while still contributing their improvements back to the ecosystem.
This open-source, collaborative approach enables Forta to adapt to new threats 10 to 100 times faster than traditional security firms.
How to Build a Forta-like Blockchain Threat Detection System?
We understand the risks that come with decentralized applications and smart contracts. To help protect your blockchain ecosystem, we offer a robust Threat Detection System that works much like Forta. Our system is designed to monitor, detect, and alert you to potential security issues, keeping your blockchain environment secure and responsive.
1. Detection Goals & Supported Chains
We start by understanding the specific threats you want to protect against—whether it’s rug pulls, flash loan attacks, or governance exploits. We also work with you to identify which blockchains and contract types (ERC-20, ERC-721, etc.) need to be monitored, ensuring that the detection system is tailored to your needs.
2. Decentralized Event Listener Layer
Our next step is setting up a decentralized event listener. This tool monitors blockchain activities in real-time, ensuring that we detect suspicious transactions as they happen. We can integrate existing tools like Forta Scanner or build a custom event ingestion engine to support high-throughput and low-latency parsing, making sure your system is always up-to-date.
3. Modular Detection Bots
We then create detection bots focused on specific threats. These bots are programmed using Python or JavaScript, depending on your preferences. Each bot is designed to spot anomalies such as unusual trades or suspicious smart contract interactions. With pattern recognition and AI techniques, we ensure the bots can detect even the most advanced attacks.
4. Simulation & AI Layers
To increase detection accuracy, we incorporate AI layers, such as Graph Neural Networks. These AI models simulate the impact of transactions before they’re executed, helping to identify potential issues and reduce false positives. This step adds an extra layer of safety, allowing us to test transactions in a simulated environment before they hit the main blockchain.
5. Incentivize & Decentralize Bot Operations
Our system encourages active participation from the community. We use token-based rewards and staking to incentivize bot operators. To keep the network secure, we implement slashing mechanisms for those who abuse the system or submit false data, ensuring that the detection system remains trustworthy.
6. Alert Management & Firewall Integration
Finally, we set up real-time alerts to notify you whenever a threat is detected. Whether through webhooks, dashboards, or platforms like Discord, we make sure you’re always informed. We also offer optional on-chain firewalls or pause mechanisms to give you the ability to take immediate action and protect your assets.
Challenges in Building a Blockchain Threat Detection System
After working with numerous clients to build and deploy blockchain threat detection systems, we’ve faced several common challenges. Through experience, we’ve developed effective strategies to tackle these issues. Here’s a look at the most frequent challenges and how we ensure they are managed for optimal performance.
Challenge 1: Maintaining Low False Positives
Excessive false alerts can overwhelm security teams, leading to alert fatigue and reduced trust in the system. Rule-based systems are prone to flagging legitimate transactions as suspicious, often causing unnecessary panic. This results in wasted resources and potential oversight of real threats.
Our Solution:
We take a multi-layered approach to reduce false positives:
- Transaction Simulation – We replay suspicious transactions in a sandboxed environment before flagging them.
- Machine Learning (GNNs) – By using behavioral analysis, we identify true anomalies instead of relying on rigid rules.
- Heuristic Filters – Alerts are cross-checked with historical false positives to fine-tune the system’s accuracy.
Challenge 2: Coordinating Decentralized Nodes
In a decentralized system, it can be challenging to ensure that nodes stay honest and provide reliable threat intelligence. Malicious or lazy nodes could compromise the accuracy of the data, leading to flawed conclusions about network health. Additionally, ensuring fairness and preventing manipulation across the network can be difficult.
Our Solution:
We apply cryptoeconomic governance to encourage honest node behavior:
- Staking & Slashing – Node operators stake tokens, and those who act maliciously are penalized.
- Uptime Scoring – Nodes with over 99% availability receive better rewards, ensuring constant reliability.
- Transparent Reputation Metrics – We provide public dashboards that track node performance, ensuring accountability.
Challenge 3: Bot Quality & Redundancy
Poorly coded bots can miss critical threats or generate unnecessary noise, making it harder to distinguish between real risks and false alarms. A single bot dominating the detection process can create a single point of failure, which weakens the reliability of the system. This can lead to missed attacks or slow response times.
Our Solution:
We ensure robust bot quality and redundancy through:
- Open-Source Audits – Security experts review bot logic before deployment to ensure quality and security.
- Redundancy Scoring – Multiple bots must agree before an alert is triggered, reducing the chance of false positives or missed threats.
- Bug Bounties – We incentivize the community of developers to identify and fix flaws in detection models, keeping the system self-improving.
Tools & APIs or Building a Forta-Like Threat Detection System
To create a robust decentralized blockchain threat detection system, you need the right set of tools for real-time monitoring, AI-powered analysis, and automated responses. Here’s the complete toolkit we use at IdeaUsher to ensure enterprise-grade deployments:
1. Detection Infrastructure
Forta SDK
The Forta SDK is a core framework for building and deploying detection bots. It includes pre-built templates for common threats like flash loans and reentrancy attacks, and easily integrates with EVM-compatible chains for seamless monitoring and security.
Node.js / Python Runtime
Detection bots are commonly written in JavaScript (Node.js) or Python because of their flexibility and strong community support. Key libraries like web3.js and ethers.js are used for Ethereum-based chains, while solana-web3.js is used for Solana, providing the necessary tools to interact with the respective blockchain networks.
Forta Network Scanner
The Forta Network Scanner aggregates alerts from decentralized nodes, helping to consolidate threat data for analysis. As an alternative, a custom scanner can be built using P2P protocols like libp2p, allowing for greater flexibility and customization to meet specific requirements.
2. Blockchain Indexing & Data APIs
Alchemy / Infura / QuickNode
Tools like Alchemy, Infura, and QuickNode allow you to fetch real-time blockchain data, including transactions and logs, which are crucial for accurate threat detection. For optimal performance, we recommend using webhook-based alerts for low-latency monitoring, ensuring that you receive immediate notifications of potential threats as they happen.
The Graph (Subgraph Queries)
The Graph is ideal for indexing historical attack patterns, allowing you to query data like “all flash loans over $1M last month.” This helps identify recurring exploit trends or risky behaviors, providing valuable insights for proactive threat detection and security planning.
3. Simulation & AI Tools
| Tool | How It Works | Critical For |
| Tenderly / Anvil | Replay suspicious transactions in a sandboxed environment to check for vulnerabilities. | Reducing false positives by simulating real-world conditions before acting. |
| PyTorch / TensorFlow | GNNs (Graph Neural Networks): Detect anomalies in transaction flows, like abnormal token movements.LSTMs: Predict time-based attacks, such as slow rug pulls. | Training AI models with past DeFi hacks (e.g., Eul |
4. Notification & Integration Systems
Discord / Slack / Webhook APIs
Discord, Slack, and Webhook APIs enable your system to send real-time alerts to security teams, ensuring they can react swiftly to potential threats. For enterprise use, critical threats can be escalated via SMS, email, or PagerDuty, ensuring the right team receives immediate notifications and can respond quickly.
5. Cryptoeconomic Layer (For Decentralized Security)
Ethereum Smart Contracts (Staking/Slashing)
Ethereum Smart Contracts for staking and slashing are used to maintain decentralized security. By rewarding honest node operators and penalizing malicious ones, these contracts help ensure the integrity of the network, fostering trust and reliability within the system.
Chainlink Oracles (Data Validation)
Chainlink Oracles are used to verify off-chain threat intelligence, such as IP blacklists or external data feeds. This ensures the integrity and accuracy of the information fed into your system, helping to protect against external threats and vulnerabilities.
Use Case: Threat Detection for a DeFi Lending Protocol
One of our clients, a leading DeFi lending platform with over $50M in total value locked, approached us with critical security challenges.
They were concerned about vulnerabilities to flash loan attacks and oracle manipulation, lacked sufficient monitoring for complex, multi-stage exploits, and faced increasing regulatory pressure after high-profile breaches in the DeFi space. Our team was tasked with addressing these issues to enhance their security and mitigate risks.
Our Custom Security Solution
We designed and implemented an advanced threat detection system, modeled after Forta’s decentralized approach, to address these issues and safeguard the platform.
1. Specialized Threat Detection Bots
Flash Loan Defense System
Our Flash Loan Defense System monitors borrowing patterns, identifies rapid collateral swaps, and flags suspicious liquidity movements. These key indicators help spot flash loan attacks early, allowing us to prevent malicious activity before it impacts the platform.
Oracle Integrity Monitor
The Oracle Integrity Monitor continuously cross-validates price feeds in real-time, checking for inconsistencies across different sources. This ensures that the platform’s pricing remains accurate and protected from oracle manipulation, safeguarding users from incorrect liquidations or exploits.
2. Advanced Transaction Analysis
We use pre-execution simulations to test high-risk transactions before they’re finalized. The dynamic threat scoring system evaluates transaction risks based on several factors, while the tiered response protocol ensures that actions are tailored to the severity of each potential threat, making sure we respond quickly and appropriately.
3. Decentralized Alert Network
Our decentralized alert network automatically triggers emergency protocols when critical threats are detected, ensuring fast, coordinated responses. Multisig governance integration adds a layer of security for key decisions, while real-time security dashboards allow the team to monitor and react to threats immediately.
4. Sustainable Community Ecosystem
We’ve built a developer bounty program to encourage ongoing improvements to our detection models, rewarding the community for their contributions. Performance-based rewards keep node operators motivated to perform at their best, while open-source contributions foster collaboration and ensure the system is always improving.
Measurable Security Improvements
Within just 90 days of implementation, the results were clear:
| Result | Outcome |
| Potential Losses Prevented | $15M+ in potential losses from intercepted attacks |
| False Positives Reduction | 72% reduction compared to previous systems |
| System Uptime | 99.9% uptime across monitoring nodes |
| Industry Recognition | Recognized as security leaders in DeFi lending |
Conclusion
As Web3 continues to evolve, decentralized threat detection systems, like Forta, are becoming vital for maintaining security. With the integration of AI, community-driven insights, cryptoeconomics, and real-time simulations, these systems offer unparalleled flexibility and rapid response times. At IdeaUsher, we specialize in creating custom Forta-like solutions tailored to your platform’s unique needs, strengthening security and building trust within your ecosystem.
Looking to Build a Blockchain Threat Detection System Like Forta?
Your blockchain platform deserves the best in security. With Forta-level protection, we offer real-time threat detection, AI-powered analysis, and decentralized defense mechanisms. At IdeaUsher, we specialize in building custom threat detection systems that:
- Block attacks before execution with simulated transactions
- Minimize false positives using advanced machine learning techniques
- Scale securely with decentralized node networks
- Ensure compliance while maintaining censorship resistance
Why Choose Us?
- 500,000+ hours of coding expertise – Our experienced ex-FAANG/MAANG engineers bring enterprise-grade security to your platform
- Proven track record – Check out our latest blockchain security projects and success stories
- End-to-end development – We handle everything from threat modeling to AI bot deployment
Don’t wait for an exploit to occur. Let’s build your Forta-like shield today!
Work with Ex-MAANG developers to build next-gen apps schedule your consultation now
FAQs
A1: Forta stands apart by being decentralized, open-source, and real-time. Unlike traditional security scanners that rely on centralized systems, Forta leverages thousands of bots working in tandem and continuously improving through incentives, providing a more dynamic and resilient approach to blockchain security.
A2: Yes, systems like Forta are designed to support multiple blockchains, including Ethereum, Polygon, BNB Chain, Arbitrum, and others. This cross-chain compatibility allows for unified threat detection across a variety of decentralized platforms.
A3: Not necessarily. While basic detection bots can be built using simple rule-based logic, more advanced bots benefit from integrating machine learning or AI techniques. This helps detect more complex patterns and enhances the overall accuracy and efficiency of the system.
A4: Staking ensures that bot developers have a vested interest in maintaining high-quality contributions. By staking tokens, they are financially incentivized to ensure their bots perform well. If their bots misbehave or provide inaccurate results, they face slashing, which helps keep the system trustworthy and reliable.