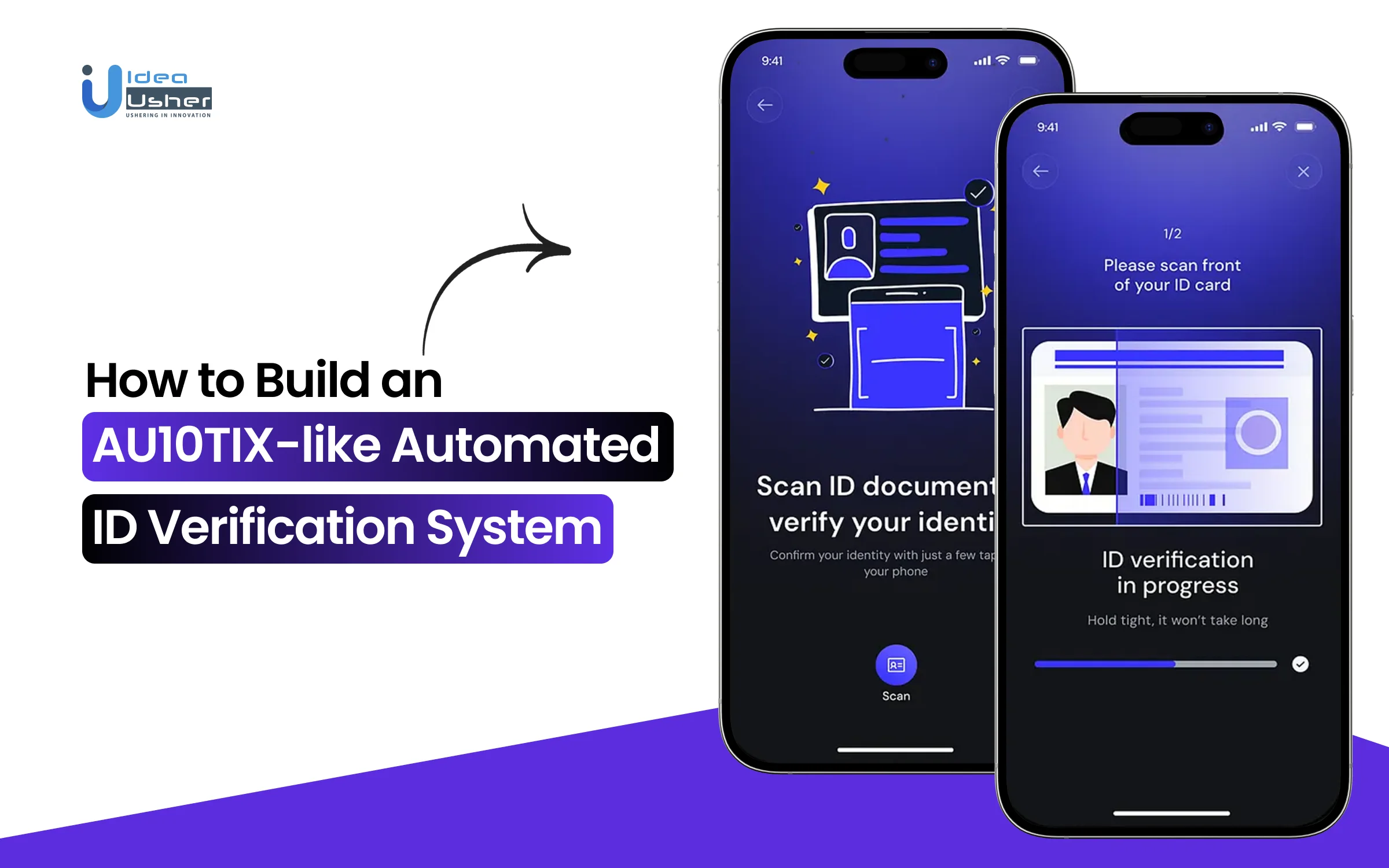
Every digital product starts with a moment of trust when a user shares their identity and expects the verification to happen quickly and quietly in the background. For businesses, that moment carries real pressure because compliance and fraud risks sit behind every submitted document. Automated verification systems like AU10TIX help close that gap with automated document detection and passive liveness checks that don’t slow users down.
The platform also adds cross-document fraud analysis and global ID coverage, enabling reliable verification at scale. Behind that experience are OCR engines and biometric matching models built to detect spoofing attempts and synthetic identities.
We’ve built several identity verification and compliance automation platforms over the years that use computer vision pipelines and biometric authentication frameworks. With that experience, we’re writing this blog to help you understand what it takes to build an AU10TIX-like automated ID verification system. Let’s begin.
Key Market Takeaways for Automated ID Verification Systems
According to GrandViewResearch, the identity verification industry is expanding rapidly as more everyday transactions move online and security risks grow. Industry estimates show the market was worth close to USD 10 billion in 2022, and analysts expect it to reach almost USD 34 billion by 2030. That level of growth underscores the importance of secure digital onboarding across sectors such as banking, fintech, government services, and any platform handling sensitive information.
Source: GrandViewResearch
Automated identity verification is gaining momentum because it solves a problem businesses can no longer ignore: verifying users quickly without sacrificing accuracy. Instead of relying on slow and error-prone manual checks, modern systems use biometric matching, document scanning, liveness detection, and risk scoring to stop fake identities, deepfakes, and other emerging fraud tactics. Customers benefit too, since faster verification means fewer abandoned sign-ups and a smoother digital experience.
Companies such as Jumio and Onfido demonstrate how automated ID verification is being applied in real-world onboarding. Jumio’s platform combines identity checks with compliance screening, enabling organizations to verify users in seconds rather than hours.
Onfido takes a similar approach, offering document and biometric verification to support global onboarding across many regulatory environments. Both represent a growing trend: identity verification is no longer just a security step, but a core part of customer trust and digital transformation.
What is the AU10TIX Platform?
AU10TIX is an identity verification and authentication platform built to provide fast, forensic-grade user verification at scale. The company traces its roots to border control and aviation security technologies, which gives its approach a level of rigor not typically found in commercial verification tools.
Today, AU10TIX is used across sectors like fintech, payments, mobility services, e-commerce, gaming, and other industries where verifying individuals quickly and accurately is essential.
Instead of relying on slow manual checks, AU10TIX uses AI-driven automation to validate identity documents, match faces, confirm liveness, and detect fraud patterns.
Here are some of its standout features,
Lightning-Fast Automated Identity Verification
AU10TIX verifies identity documents and selfies in seconds, providing users with an immediate approval or denial result. This near-instant experience prevents hesitation, reduces drop-off, and helps businesses onboard more users successfully without creating delays or confusion.
Intelligent Capture Guidance
As users take photos, the system gives real-time feedback to fix common issues such as glare, blur, poor framing, or low light. This guidance ensures better input quality the first time, reducing failed submissions, repeat attempts, and the need for manual support.
Passive Liveness Detection
Users simply look at the camera naturally without blinking, requests, head movements, or staged actions. This frictionless process feels intuitive and respectful, which improves completion rates and accessibility for users of all ages and comfort levels.
Automatic Global Document Recognition
The platform recognizes and processes government IDs, passports, and licenses from many countries without requiring manual selection. This makes onboarding seamless for international users and removes complexity for global businesses scaling into new markets.
Clear Results with Helpful Explanations
Instead of ambiguous rejection messages, users receive clear context and guidance, such as retaking a photo or using the original document. This transparency reduces frustration, builds trust, and empowers users to complete verification independently.
How Does the AU10TIX Platform Work?
AU10TIX takes an ID and a selfie, runs automated image-quality checks, and optimizes processing so the input is clean and ready. Then its AI engines could validate the document structure, perform forensic fraud checks, and extract data with OCR while a biometric model matches the face and confirms liveness silently.
Step 1: Guided Document Capture
The user is asked to verify their identity through your app or website. They take a picture of an official ID and then a short selfie. The on-screen guidance feels similar to using a modern camera app, offering gentle prompts if something needs adjusting.
What the system does behind the scenes:
- Instant quality review: The platform immediately checks the document image for glare, blur, cropping, focus, and clarity. If the photo is not usable, the system provides tailored instructions so the user can fix it without guessing.
- Automatic optimization: The image is straightened, cropped, enhanced, and prepared for analysis so the next steps run cleanly.
This alone saves enormous time by preventing failed uploads and manual re-checks.
Step 2: Forensic Document Authentication
Once a clean scan is confirmed, AU10TIX runs a multi-layer inspection that happens extremely fast but mirrors expert-level document examination.
Layer 1: Detecting the document type
The platform matches the layout, fonts, and structure against thousands of known ID formats, determining what the document is and where it comes from.
Layer 2: Authenticity and tamper analysis
This is where the forensic technology comes into play. The platform checks for:
- altered or missing holograms
- inconsistent fonts or layouts
- pixel-level manipulation
- reprinted surfaces or texture mismatches
More than one hundred tests are carried out automatically to detect counterfeit documents, edited digital images, or physically altered IDs.
Layer 3: Extracting and validating data
OCR technology reads printed and encoded fields such as names, dates, and document numbers. The extracted data is then validated logically and format-wise, reducing errors and catching discrepancies.
Step 3: Face Verification and Liveness Detection
While the document is being analyzed, the selfie is processed in parallel.
- Facial comparison: The system converts both the selfie and the document portrait into secure facial signatures and compares them for similarity.
- Passive liveness: Without asking the user to move or perform gestures, the platform determines whether a real live person is in front of the camera. Texture, depth cues, lighting patterns, and natural micro-movement help detect printed photos, videos, deepfakes, or masks.
This step confirms the person submitting the ID is the rightful owner and physically present.
Step 4: Decision Logic and Risk Intelligence
At this point, everything AU10TIX has learned is brought together.
The platform:
- checks user information against watchlists, sanction lists, and PEP databases
- evaluates fraud signals using a shared global intelligence network
- applies rules or triggers additional steps based on risk level
For example, a clean, low-risk result may be approved instantly. Anything suspicious may trigger an extra layer of review or be rejected.
Step 5: Final Decision and Output
Within about five to eight seconds, the user and your system both receive the outcome.
- If approved: The user continues onboarding or completes their action with no interruption.
- If not approved: The business receives detailed reasoning and visual evidence so compliance teams can review or escalate.
The user may also receive tips on how to retry if the failure was caused by image quality rather than fraud.
What is the Business Model of the AU10TIX Platform?
AU10TIX operates as an identity verification and fraud-prevention platform built around advanced AI and automation. Its core purpose is to help organizations verify individuals and businesses quickly, accurately, and in compliance with regulatory frameworks such as KYC, KYB, and AML requirements.
Revenue Model
The company generates revenue primarily through SaaS-based pricing structures. Customers typically pay either:
- Subscription fees, depending on usage tier and feature access
- Per-transaction or per-verification pricing linked to API calls
- Enterprise contracts that include volume rates, compliance features, and advanced add-ons
Higher-value offerings include risk scoring, AML screening, workflow automation, and compliance case management dashboards. For large organizations conducting continuous monitoring or complex onboarding flows, AU10TIX offers premium modules to enhance fraud resilience and process efficiency.
Growth, Market Performance, and Impact
AU10TIX has demonstrated strong commercial traction and measurable impact in fraud mitigation. In 2024 alone, the platform reported preventing approximately $7.5 billion in fraud attempts, bringing cumulative protection to $24 billion since 2021.
Revenue growth has followed a similar upward trend, with external reporting indicating the company approached around $70 million in annual revenue by 2021.
Beyond financial performance, the platform also delivers tangible business outcomes. Organizations using AU10TIX frequently report higher customer approval and onboarding rates, in some cases improving conversion by up to 25 percentage points.
Funding and Valuation
AU10TIX has secured roughly $80 million in total funding, raised over two primary investment rounds. The most recent growth financing—$20 million—closed in November 2019. During this period, the company’s estimated valuation was recorded at around $260 million.
The platform attracted backing from prominent investors, including Oak HC/FT Partners and TPG, who invested to support AU10TIX’s global expansion, product innovation, and scaling of its AI-driven technology.
How to Build an AU10TIX-like Automated ID Verification System?
Building an AU10TIX-like system starts with a strong document analysis engine that can detect tampering and extract identity data with high accuracy. You would then add biometric verification and liveness detection so the platform can confirm the real user behind the document with minimal friction. We have built systems like this for clients, and we know the exact technical path to make it work.
Step 1 – Document Intelligence
We start by creating a document verification foundation that supports passports, national IDs, and driver’s licenses from multiple countries. Our team acquires compliant datasets, trains OCR and forensic models, and builds a dynamic template engine to handle global document patterns.
Step 2 – Biometric Security
Next, we integrate biometric identity proofing aligned with global privacy and compliance frameworks. Facial data is converted into encrypted vector signatures and secured with cryptographic salting to prevent reverse engineering attempts.
Step 3 – Fraud Monitoring
Once identity and document proofing is stable, we layer in intelligence-driven fraud detection. Device fingerprinting, behavioral analytics, and graph-based identity mapping help identify repeat offenders across channels.
Step 4 – Risk Orchestration
To ensure efficiency at scale, we introduce adaptive risk scoring paired with configurable policy automation. The system evaluates biometric confidence, document authenticity, fraud indicators, and jurisdictional rules to determine the appropriate verification pathway.
Step 5 – Deepfake Defense
Modern fraud requires proactive security, so we deploy deepfake detection, spoof resistance models, and passive liveness checks. A controlled threat simulation environment helps test and validate defensive capabilities.
Step 6 – Enterprise Delivery
Finally, we package the platform for real use. We build secure APIs, management dashboards, billing components for consumption-based pricing, and a customizable white-label portal for enterprise onboarding and compliance operations.
Challenges of an AU10TIX-like Automated ID Verification System
Building a high-accuracy identity verification platform isn’t just another software project. It’s a complex mix of compliance engineering, machine learning, fraud forensics, and global scalability. After implementing these systems for multiple enterprise clients, we’ve identified the most common pitfalls teams run into and how to prevent them.
1. Global Privacy & Biometric Regulations
Compliance is not universal. GDPR (EU), CCPA (California), PDPA (Singapore), and BIPA (Illinois) all define strict limitations on biometric data usage, including how data is collected, processed, stored, and deleted. A system acceptable in one jurisdiction may violate regulations in another.
Our Approach: Compliance Built Into the Architecture
Instead of treating compliance as an afterthought, we design systems where regulatory alignment is part of the core framework. Key elements include:
- Geo-aware data routing to ensure biometric and PII data never leave approved regions.
- Consent enforcement frameworks that track permissions with full auditability.
- Automated lifecycle management that purges or anonymizes data based on local retention requirements.
This approach turns legal complexity into a configurable rule set rather than a blocker to progress.
2. Keeping Pace With Deepfakes
Fraud is constantly evolving. Attackers now use generative AI to create synthetic identities, manipulate live video, and inject spoofed facial images into verification flows. A static model quickly becomes ineffective.
Our Approach: Evolving AI Defense Systems
We implement a continuous learning strategy that includes:
- Adversarial training loops where one model generates attacks and another learns to detect them.
- Closed-loop retraining so every fraud attempt informs future improvements.
- Multimodal signal analysis combining visual data with device metadata, liveness signals, and behavioral biometrics.
This ensures the system evolves alongside threat tactics instead of reacting after damage is done.
3. Cost of Large-Scale ML Processing
Identity verification at scale can be expensive. Running high-resolution image analysis and video liveness checks requires significant GPU capacity. Without smart orchestration, costs escalate quickly.
Our Approach: Cost-Aware ML Deployment
We reduce operational overhead while maintaining accuracy using:
- Progressive inference paths where lightweight models handle straightforward cases, and advanced analysis is reserved for edge cases.
- Auto-scaling GPU infrastructure so resources expand during peak usage and pause when idle.
- Model optimization through quantization and pruning to reduce computational load.
The result is enterprise-level performance with predictable cost efficiency.
4. Consortium-Level Fraud Intelligence
Platforms like AU10TIX benefit from fraud data across multiple industries. A new or isolated system only sees its own traffic, which limits its ability to detect repeat fraud attempts.
Our Approach: Data Intelligence Ecosystem Design
We accelerate threat detection accuracy by enabling:
- Privacy-safe consortium sharing through hashing, tokenization, and differential privacy.
- Integration with existing fraud intelligence networks to enhance scoring.
- Contribution frameworks that allow anonymous sharing of verified fraud signals.
This shifts the system from operating alone to participating in a global defense network.
How Much Revenue Can an Automated ID Verification System Generate?
Identity verification platforms typically monetize across multiple pricing layers rather than relying on a single model. Most market players combine usage-based billing with subscription pricing to maximize recurring revenue and capture growth from transaction volume.
1. Transaction-Based Pricing
This model is common among platforms serving fintech, e-commerce, gig onboarding, marketplace trust systems, and gaming.
Typical pricing ranges:
| Verification Type | Typical Market Price |
| Basic ID scan | $0.75 – $1.50 |
| ID plus biometric selfie match | $1.50 – $2.50 |
| Full verification with biometrics, watchlist screening, AML checks | $2.50 – $5.00+ |
Example Revenue Scenario:
- Monthly verification volume: 2,000,000
- Average price per verification: $1.50
- Monthly revenue: $3,000,000
- Annual revenue: $36,000,000
This level of throughput is realistic once the platform secures several high-volume fintech clients or one major enterprise rollout.
Justification: Onfido, prior to its acquisition, reported processing hundreds of millions of verifications. A volume of 2 million monthly transactions is conservative for a platform serving several mid-sized fintechs or one large enterprise.
2. SaaS Subscription Revenue
This pricing style is oriented toward enterprise adoption, predictable billing, custom compliance features, dedicated support, analytics dashboards, and configurable risk rules.
Typical pricing tiers:
| Tier | Monthly Cost Range | Ideal Customer Profile |
| Starter | $5,000 – $15,000 | Early-stage fintech platforms |
| Growth | $20,000 – $50,000 | Mid-sized companies |
| Enterprise | $75,000 – $250,000+ | Banks, government, telecom, large brands |
Example Subscription Revenue Scenario:
Assume the platform signs 100 enterprise customers.
- 30 customers at $35,000/month = $1,050,000/month
- 70 customers at $120,000/month = $8,400,000/month
Total annual subscription revenue: $113,400,000
Enterprise contracts in this sector often exceed six figures per year and some can reach multi-million-dollar terms.
Justification: Trulioo, a major player, serves thousands of enterprises globally. An average enterprise contract in this space often exceeds $100,000 annually, with large financial institutions paying millions.
Integrated Model & Real-World Benchmark
Successful platforms like AU10TIX and Jumio employ a hybrid model: a base SaaS fee plus overage charges per transaction. This provides stable recurring revenue while capturing upside from client growth.
Public Company Benchmark:
While most IDV leaders are private, we can look at NICE Actimize (a broader fraud/AML platform with strong IDV components). Its financials reveal:
- Annual Revenue: ~$700+ million
- Growth Rate: ~10-12% annually
- High Gross Margins: ~70-75% (indicative of the software-centric model’s profitability)
For a pure-play IDV provider, gross margins typically range from 65-80%, as the core cost is cloud infrastructure and AI R&D, not raw materials.
Five-Year Revenue Projection for a Strong Execution Path
Here is a phased revenue model for a well-executed IDV platform:
| Year | Phase | Expected Annual Revenue | Notes |
| Year 1 | Validation and pilot clients | $2M – $5M | Limited volume but early strategic wins |
| Year 2 | Market scaling | $10M – $20M | Around 1 million transactions per month |
| Year 3 | Enterprise penetration | $40M – $60M | Multi-region compliance rollout |
| Year 4 | Expansion and product diversification | $80M – $120M | Add KYB, monitoring, fraud scoring |
| Year 5 | Maturity and exit readiness | $150M – $250M+ | Attractive for acquisition or IPO |
Valuation Outlook
If the platform reaches $150M in recurring revenue by year five and maintains growth above 30 percent annually, common SaaS valuation benchmarks of 8x to 12x ARR suggest a potential market valuation of: $1.2 billion to $3.0 billion
This projection aligns with valuation patterns seen in companies such as Socure and other identity security platforms during later scaling stages.
Key Factors That Influence Revenue Potential
- Accuracy and speed of identity verification
- Regulatory readiness across jurisdictions
- Ability to detect deepfakes and biometric spoofing
- Customer retention and expansion potential
- Integration ecosystem and developer experience
Platforms that demonstrate superior fraud detection and compliance outcomes can command premium pricing, often 30 percent to 50 percent higher than basic verification tools.
How Automated ID Verification Systems Control Identity Fraud Rising 12% Per Year?
Identity fraud has been climbing fast; since 2020, it has grown by about 12% each year, meaning the threat today is roughly 76% larger than it was 5 years ago. That pace is beyond the capacity of manual verification, so automated systems use biometric matching and real-time risk scoring to detect manipulation before an account is created.
Modern identity verification platforms used in banking, fintech onboarding, government portals, healthcare access, and digital account creation apply a layered security model. The goal is simple: if fraud evolves quickly, defenses must evolve faster.
Layer 1: Stopping Fraud at the Entry Point
The most effective intervention happens immediately during account creation or access requests.
Forensic Document Analysis
High-resolution scanning breaks down an uploaded ID into thousands of micro-validation points. Systems check pixel noise patterns, holograms, microtext, font consistency, and optical protection elements that are often invisible to human reviewers. While identity fraud increases at 12% annually, machine-learning models supporting forensic document checks improve 20 to 30% each year due to continuous dataset expansion.
Instant Risk Scoring
Every verification attempt receives a risk score within seconds using document authenticity, device fingerprinting, biometric confidence, and anomaly signals. Suspicious verification attempts can be suspended or declined automatically without human review.
Layer 2: Biometrics and Behavioral Intelligence
As fraud evolves from Photoshop edits to deepfakes and synthetic identities, advanced verification systems rely on biological authentication and user behavior signals.
Passive Liveness Detection
Instead of prompting users to blink or turn their heads, passive verification measures micro-movements, 3D facial structure, depth mapping, and blood-flow patterns during a selfie. When paired with biometric matching, passive liveness reduces account takeover success rates by up to 89%.
Behavioral Biometrics
Automation, scripts, and fraud rings often leave behavioral fingerprints. Systems evaluate typing cadence, swipe motion, device handling, latency patterns, and timing irregularities. Behavioral intelligence can flag around 34% of fraud attempts that document scanning alone would miss.
Layer 3: Shared Intelligence & Pattern Recognition
This layer creates collective security through shared data intelligence.
If a fraudulent identity, forged document, or suspicious device is flagged in one institution, the anonymized signature becomes part of a shared fraud intelligence network. When the same fraud attempt appears elsewhere, the system can detect and block it quickly.
Machine-learning models evaluate millions of verification attempts to detect pattern shifts far earlier than human analysts. If fraudsters suddenly pivot to a different document type or geographic region, automated systems can update risk logic within hours.
How Automation Exceeds a 12% Annual Increase in Fraud Attempts
Speed Comparison:
- Manual verification: typically 15 to 45 minutes
- Basic automation: 30 to 120 seconds
- Advanced AI identity verification: 5 to 8 seconds
Cost and Scalability
Human verification costs increase proportionally with fraud volume. Automated identity verification has a minimal marginal cost per additional check, which means cost efficiency improves as user volume grows.
Learning and Adaptation
Modern platforms learn continuously. Every verification attempt, whether legitimate or fraudulent, strengthens the model. Many systems retrain weekly or even daily to detect new attacks quickly.
Defense Performance Against Major Fraud Types
| Fraud Type | Method | Effectiveness |
| Synthetic identities | Cross-database validation and identity correlation | 67 to 82% reduction in success rate |
| Deepfakes and AI-generated submissions | Neural spoof detection and frame-level video analysis | ≈94% current detection accuracy, improving monthly |
| Account takeover | Continuous authentication and device intelligence | Blocks up to 96% of takeover attempts |
Tools & APIs for an AU10TIX-like Automated ID Verification System
Building an automated identity verification platform with the capabilities of AU10TIX requires far more than OCR tools and biometric libraries. It demands a coordinated tech ecosystem where machine learning, security, infrastructure, and compliance operate as one. The stack below represents the core building blocks used in real production-grade identity verification systems.
1. AI and Machine Learning Stack
The heart of any advanced verification engine is machine learning. This layer performs document classification, detects manipulation, and validates biometric identity. It must operate at high throughput while maintaining forensic-grade accuracy.
Key Components
- TensorFlow and PyTorch: Used to build and train deep learning models for document fraud detection, facial matching, and pattern classification. PyTorch offers agility during model development, while TensorFlow provides maturity and reliability when deploying at scale.
- OpenCV: Handles low-level processing before images reach neural networks. It manages noise reduction, alignment, glare removal, template matching, and text region isolation. Clean image preprocessing directly impacts model accuracy.
- NVIDIA GPU Acceleration and CUDA: Real-time model inference demands parallel processing. GPU-powered compute environments are essential for scaling facial recognition, hologram detection, and passive liveness checks without sacrificing user experience.
2. Biometric and Image Processing Layer
This layer converts raw media into verified, structured identity features. It must remain resilient against spoofing and low-quality capture environments.
Face Embedding Systems (FaceNet-Style Encoders)
Faces are converted into numerical vectors rather than compared as images. This enables precise matching for 1:1 and 1:N searches across large identity datasets.
MediaPipe Framework
Useful for lightweight, on-device analysis such as face landmark detection, pose estimation, or pre-screening before advanced server-side checks. It improves speed and reduces unnecessary processing load.
Custom Passive Liveness Detection Models
Generic liveness tools are no longer sufficient due to deepfakes and highly realistic spoof attempts. Effective systems train their own models using real and adversarial data to detect biological signals such as blinking patterns, subtle muscle tension, or natural motion variability.
3. Fraud Intelligence, Analytics, and Observability
Verifying identity once is not enough. Modern fraud is network-driven, adaptive, and coordinated. This layer turns millions of identity events into actionable intelligence.
Key Components
| Tool / Technology | Primary Role | Purpose in an Automated ID Verification System |
| Apache Kafka | Event Streaming Backbone | Streams verification attempts, model outputs, and fraud signals in real time. Supports instant scoring, anomaly detection, and integration with downstream systems. |
| Graph Databases (Neo4j or TigerGraph) | Fraud Pattern Detection | Uncovers hidden links between accounts by analyzing relationships such as shared device fingerprints, reused images, repeated geolocations, or behavioral similarities. |
| Elasticsearch | Search and Investigation Engine | Enables fast querying across large identity datasets, logs, metadata, and processed artifacts. Used for fraud analysis, audits, and compliance investigations. |
4. Cloud Infrastructure and Security Controls
Identity documents, biometrics, and compliance metadata must remain secure at every stage. This infrastructure layer focuses on privacy, redundancy, and operational reliability.
| Item | Role | Purpose |
| AWS / GCP / Azure | Cloud Infrastructure | Supports regional deployments to meet residency laws and latency needs. GPU instances power high-intensity model inference. |
| HSMs | Secure Key Storage | Protects encryption keys and sensitive identity data using hardware-level security, even in failure scenarios. |
| Zero-Trust Model | Security Framework | Requires authentication and authorization for every request. Reduces attack risk and blocks lateral movement. |
5. Compliance and AML Integration Layer
Even the most advanced verification system must meet regulatory standards. Automated screening with providers such as World-Check, Dow Jones, Refinitiv, or ComplyAdvantage helps flag sanctions, PEPs, and adverse media, ensuring each onboarding flow complies with KYC and AML requirements at scale.
Conclusion
AU10TIX-like systems have become digital trust engines rather than optional add-ons, and enterprises that build them gain new revenue streams, stronger compliance positioning, and a measurable defense against fraud. With the right development partner, you could move faster, scale globally, and maintain enterprise-level security without wasting cycles on guesswork or rework, and that’s where IdeaUsher genuinely helps by guiding both the strategy and the execution so the platform becomes a long-term competitive advantage.
Looking to Develop an AU10TIX-like Automated ID Verification System?
IdeaUsher could help you build an AU10TIX-style ID verification system by combining OCR, biometric authentication, and secure backend automation. Their team might guide you through integrations, compliance, and scalable architecture so the system actually works in real environments.
With over 500,000 hours of coding experience and a team of ex-MAANG/FAANG developers, we architect systems that are:
- Forensic-grade — layered fraud detection, not just OCR
- Frictionless — passive liveness & sub-8-second verification
- Globally compliant — dynamic workflows for KYC/AML across borders
Work with Ex-MAANG developers to build next-gen apps schedule your consultation now
FAQs
A1: Building a system at that level usually takes eight to fourteen months because you need strong document analysis, biometric verification, workflow automation, and global compliance alignment, and if you aim for advanced risk scoring or real-time fraud detection, the timeline may extend slightly.
A2: Yes, and many companies do it successfully by charging per verification or offering subscription-based compliance plans, and once the platform stabilizes with automation and scalable infrastructure, you can add premium modules like AML screening or fraud scoring to increase revenue predictably.
A3: Suppose you’re running high-volume onboarding and want long-term product leverage. In that case, building becomes more valuable because you gain full control over pricing, compliance logic, and roadmap, and you can strategically turn the platform into an asset that boosts valuation rather than a recurring cost.
A4: Yes, the architecture is industry agnostic as long as you design flexible rule engines, configurable verification steps, and adaptable compliance paths, and this lets the platform handle fast-moving sectors like crypto or fintech while still supporting stable onboarding use cases in gaming and marketplaces.