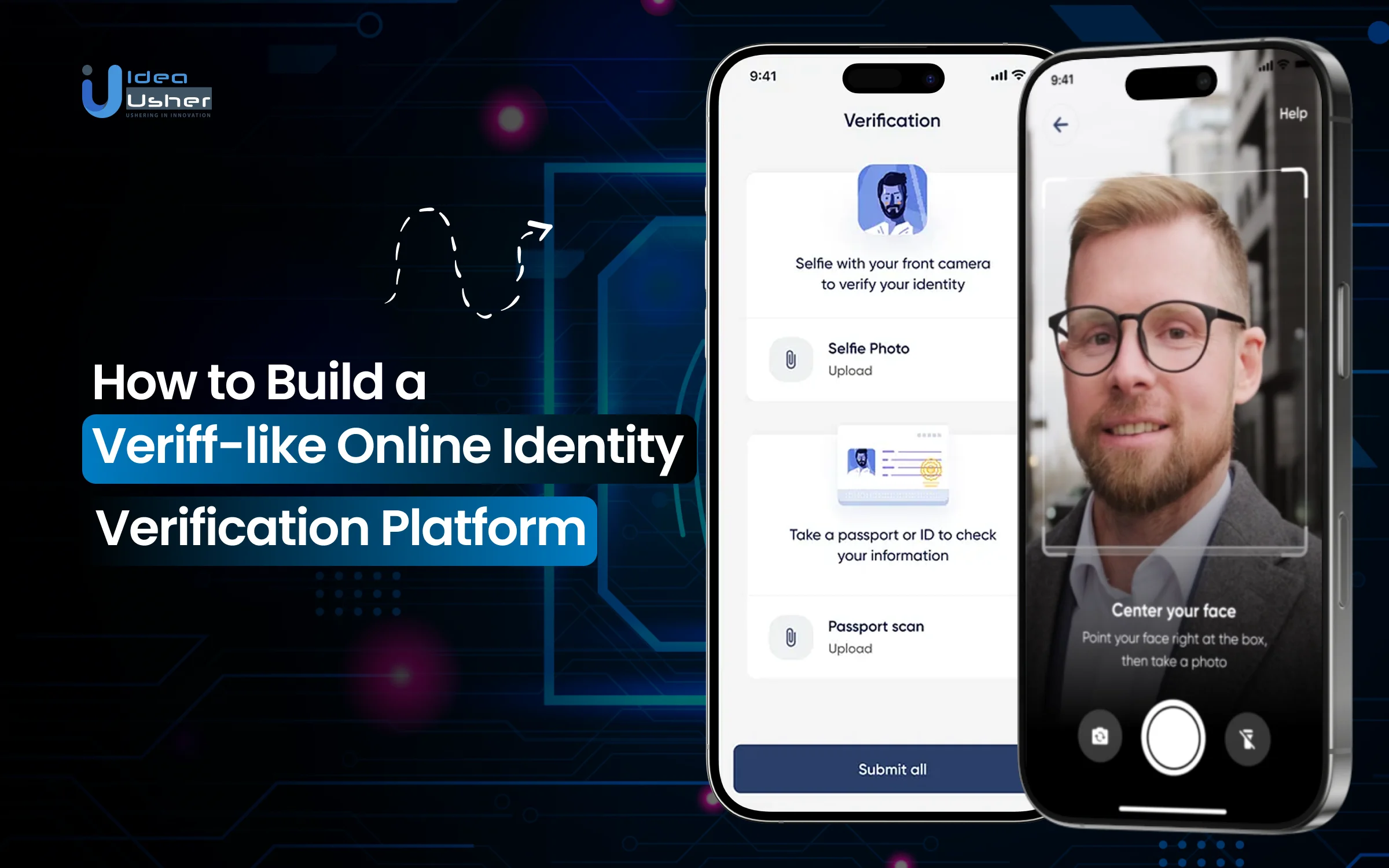
As more businesses move their services online, verifying who a user really is has become both essential and increasingly challenging. Fraud attempts are growing more sophisticated, manual checks slow down onboarding, and customers expect fast verification without compromising security. These pressures are pushing companies to adopt a modern online identity verification platform like Veriff that can confirm user identities quickly, accurately, and at scale.
These solutions demonstrate how AI, biometrics, and document analysis combine to deliver seamless verification. They automate ID checks, detect deepfakes, validate documents, and assess risk in real time, reducing operational effort and strengthening trust. For global or high-stakes businesses, this level of security and efficiency is now a competitive necessity.
In this guide, we outline how to build an identity verification platform like Veriff, covering essential technologies and features that ensure accuracy, compliance, and trust. This blog will give you a clear roadmap for developing a reliable verification solution.
What is an Online Identity Verification Platform, Veriff?
Veriff is an online identity verification platform that helps businesses confirm that their users are real people, not bots or fraudsters. It uses AI-driven ID checks, document analysis, and biometric verification to authenticate individuals quickly and securely.
This platform provides companies with a scalable, automated “trust layer” that reduces fraud, streamlines customer onboarding, and ensures compliance with global KYC/AML regulations. Its value lies in delivering high-accuracy, low-friction verification for industries like fintech, crypto, mobility, and online marketplaces—where security, user experience, and regulatory compliance directly impact revenue and risk.
- High verification accuracy driven by multi-layered AI + human review, outperforming many traditional IDV solutions.
- Global coverage, supporting thousands of ID types across 190+ countries.
- Real-time decisioning that reduces onboarding drop-off and improves conversion.
- Strong fraud detection capabilities, including behavioral signals and device analytics to catch deepfakes, synthetic IDs, and repeat bad actors.
- Enterprise-grade compliance, built for regulated industries requiring robust KYC/AML and auditability.
- Scalable architecture, capable of handling high-volume onboarding spikes with consistent quality.
A. Business Model
Veriff operates as a B2B identity-verification infrastructure provider that businesses integrate directly into their onboarding and compliance workflows.
- Veriff offers identity verification services including online checks, document and biometric verification, fraud detection, and KYC/AML compliance via APIs/SDKs to businesses.
- The service is globally oriented: it supports thousands of government IDs from 230+ countries/territories & multiple languages, enabling clients to onboard users worldwide.
- It offers flexible verification “flows”: fully automated (AI-only) for standard/low-risk use cases, or “hybrid” (AI + human / manual review + enhanced fraud detection) for higher-risk or regulated industries.
- It aims to reduce friction (fast verification, good user experience) while enabling clients to comply with regulatory and fraud-prevention requirements.
B. Revenue Model
Veriff uses a usage-based / subscription + usage pricing model, with tiers meant to serve different customer segments (from small businesses to large enterprises).
- Self-serve/SaaS-style plans: For smaller clients or those wanting quicker setup, Veriff offers plans where clients pay per verification + a monthly minimum commitment.
- The “Essential” plan starts at US $0.80 per verification with a US $49/month minimum.
- The “Plus” plan charges about US $1.39 per verification (with a higher monthly minimum) and offers hybrid verification (AI + human + additional fraud tools).
- The “Premium” plan (for heavier regulatory/fraud needs) has higher per-verification cost (≈ US $1.89) and higher commitment/minimums.
- Enterprise/custom plans: For large clients or those needing heavy customization, Veriff offers enterprise-level contracts: custom workflows, SLA, dedicated support, and advanced fraud detection.
- Add-on services / extra costs: For example, extracting more data fields from ID beyond the included limits may add per-verification charges.
- By combining subscription minimums + pay-per-use + volume-based/enterprise pricing, Veriff aligns pricing with customer size, use frequency, and risk / compliance needs.
How a Veriff-like Identity Verification System Works
A Veriff-like identity verification system works by securely capturing user data, validating documents, and confirming identity through automated checks and biometric verification.
1. User Onboarding & Environment Setup
The user starts verification through a secure session link. The system initializes a session token, collects device metadata, and configures a controlled verification environment using context-aware capture settings for mobile or web platforms.
2. Document Capture & Intelligent Preprocessing
The user submits an ID, and the platform performs image normalization, glare removal, and document-edge detection. These preprocessing steps ensure optimal image quality so downstream verification modules receive clean, structured visual data for accurate document analysis.
3. Document Authentication & Data Extraction
The system validates the ID using OCR pipelines, MRZ checks, and template-based forensics. It extracts personal details, detects tampering, and verifies embedded security elements through pattern consistency analysis and metadata comparison.
4. Biometric & Liveness Verification
The user captures a selfie, processed through landmark mapping and quality scoring. Liveness detection runs anti-spoofing classifiers that analyze depth cues, texture changes, and micro-movements to confirm real-user presence before biometric matching.
5. Identity Matching, Screening & Risk Evaluation
The system generates facial embeddings from the selfie and ID photo to calculate a similarity score. It performs AML, sanctions, and PEP checks, while a dynamic risk engine evaluates device signals, behavior patterns, and session anomalies.
6. Final Decision, Audit Log & Dashboard Review
All verification results are aggregated into a single decision output. The platform generates an audit-ready report, updates case status, and presents insights in the admin dashboard for monitoring, manual review, and compliance tracking.
How an Online Identity Verification Platform Achieves a 90% Cost Reduction in Digital Onboarding?
The global identity verification market was valued at USD 9.87 billion in 2022 and is projected to reach USD 33.93 billion by 2030, growing at 16.7% CAGR from 2023 to 2030. This 243% growth is mainly driven by enterprises aiming to cut costs, reduce processing times, and minimize customer friction of manual verification.
McKinsey research demonstrates that the potential cost reduction in onboarding costs by using digital ID-enabled processes is 90%, transforming customer acquisition from a cost center into a competitive advantage.
A. Elimination of Manual Verification Processes
Traditional identity verification is slow and costly, relying on manual review, in-person meetings, physical documents, and human agents. Online platforms speed this up using AI, biometric authentication, and database checks.
- Biometric adoption reached 79% in U.S. enterprises, tripling since 2019 and confirming that automated verification is now a trusted, scalable standard.
- Onboarding costs drop by 50% with automation, as Face SDK and Document Reader SDK integrations remove manual checks, reduce staffing needs, and speed up approvals.
- 81% of consumers trust biometric verification, allowing businesses to replace manual, costly processes without compromising user confidence.
- Cloud-based deployment holds 65.8% market share, driven by scalable, pay-as-you-grow models that eliminate heavy infrastructure and IT expenses.
B. Real-Time Verification Eliminates Processing Delays
Beyond labor savings, slow onboarding incurs costs like customer abandonment, delayed revenue, competitive disadvantages, and compliance risks. Online platforms deliver instant or near-instant results, reducing processes from days or weeks to minutes.
- A study by Forrester Consulting sees 195% ROI within three years, as advanced IDV platforms quickly recover their investment and operate as true profit-protecting assets.
- According to Gartner, 500 million users will adopt digital identity wallets by 2026, enabling reusable verified credentials and lowering repeated onboarding burdens.
- 36% of customers abandon onboarding due to slow verification, causing wasted acquisition costs and lost lifetime value to faster competitors.
- Mobile banking touchpoints grew 72%, now reaching 150 interactions per user annually, increasing the need for instant, automated verification without delays.
- 40% of enterprises use cloud biometric authentication, simplifying verification across platforms and reducing the cost of managing separate systems.
Industry Use Cases of Online Identity Verification Platform
As digital interactions grow, online identity verification has become essential across sectors. Explore the key industry use cases driving security, trust, and seamless customer experiences.
| Industry | Use Case | Why Verification Matters |
| Fintech & Banking | KYC onboarding and AML screening | Prevents account fraud, supports regulatory compliance, and ensures only legitimate users access financial services. |
| Crypto & Web3 | Wallet creation and exchange registration | Helps platforms comply with evolving crypto KYC rules, reduces fraud, and blocks illicit or anonymous manipulation. |
| Ecommerce & Marketplaces | Seller and high-risk buyer verification | Protects against counterfeit sellers, reduces chargeback fraud, and builds trusted marketplace experiences for users. |
| Gig Economy & Workforce Platforms | Driver and worker identity validation | Ensures worker legitimacy, prevents account sharing, and increases platform safety and accountability. |
| Healthcare | Patient onboarding and access control | Verifies patient identities, protects sensitive health records, and prevents unauthorized access to medical platforms. |
| Travel & Hospitality | Contactless guest check-in and passport validation | Speeds up onboarding, supports border-compliant document checks, and enhances secure digital travel experiences. |
| Real Estate & Rentals | Tenant background and identity validation | Helps property managers verify real applicants, reduce fraud, and ensure safer long-term rental transactions. |
| Education & EdTech | Student ID verification and exam proctoring | Confirms student legitimacy, prevents cheating, and maintains academic integrity in remote learning environments. |
Key Features Required in a Veriff-like Identity Verification Platform Development
Developing a Veriff-like identity verification platform requires a strong set of core features that ensure security, compliance, and seamless user onboarding. Below are the essential capabilities your platform must include to compete effectively in the digital identity market.
1. AI-powered Document Verification
The engine validates passports, national IDs, and licenses using OCR pipelines, document forensics, and template-based pattern recognition. It examines microprint integrity, MRZ consistency, hologram behavior, and metadata correlation to confirm authenticity across a wide range of global ID formats.
2. Facial Biometric Matching
Biometric matching uses deep-learning neural embeddings to compare a selfie with the document portrait. It evaluates facial vectors, encoding distance, and texture fidelity to deliver high-confidence identity matching while minimizing false positives through robust similarity scoring.
3. Liveness Detection
Liveness detection verifies physical presence by analyzing motion vectors, depth cues, challenge–response patterns, and anti-spoofing classifiers. It identifies replay attacks, masks, and synthetic media by monitoring temporal consistency and micro-movement signatures in real time.
4. Video Verification
Video verification enables trained agents to validate identities through secure, streaming sessions. It provides real-time document inspection, behavioral analysis, and cross-checking of dynamic cues, offering an added assurance layer for high-risk or regulated verification scenarios.
5. Age Estimation
Age estimation uses facial analytics, probabilistic modeling, and AI-driven morphology assessment to determine user age. It blends date-of-birth extraction, demographic pattern recognition, and optional registry lookups to support compliant onboarding for age-restricted digital services.
6. AML/PEP Screening
The screening module checks users against AML, sanctions, and PEP datasets using entity resolution, fuzzy matching, and risk-based KYC screening logic. It flags potential matches, automates compliance workflows, and supports audit-ready reporting for financial and regulatory oversight.
7. Multi-Document Type Support
The platform supports thousands of global document types using document classifiers, region-specific templates, and adaptive parsing models. It handles passports, driver’s licenses, national IDs, and residence permits across jurisdictions with consistent accuracy and localized pattern detection.
8. Fraud Prevention & Risk Scoring
Fraud controls combine device fingerprinting, IP reputation checks, behavioral biometrics, and anomaly-detection models. A configurable engine generates a dynamic risk score using weighted attributes, helping businesses detect synthetic identities, repeat fraud attempts, and suspicious cross-device patterns.
9. Admin Dashboard & Analytics
The dashboard centralizes verification management with real-time analytics, audit logs, and automated case prioritization. It provides operational metrics, throughput monitoring, and performance intelligence so teams can optimize review workflows and maintain consistent verification quality.
How to Build a Veriff-like Online Identity Verification Platform
Building a Veriff-like online identity verification platform involves combining secure verification technologies with smooth, user-friendly workflows. Below is a concise guide to help you develop a scalable, compliant, and competitive IDV solution from the ground up.
1. Consultation
We begin by understanding the client’s compliance needs, risk appetite, and onboarding workflows. Our team analyzes user journeys, target markets, verification volumes, and regulatory obligations to define a clear identity-verification strategy and ensure the platform aligns with business and security goals.
2. User Flow & Verification Journey Design
We design intuitive verification journeys that reduce friction and support high completion rates. This involves crafting step-by-step flows for document capture, biometric checks, and liveness tasks while maintaining secure interaction patterns and minimizing drop-offs across devices.
3. Architecture Planning
We define an extensible system architecture that separates identity processing, verification logic, and compliance modules. This ensures the platform can handle increasing volumes, support multi-region expansion, and maintain high availability across verification operations.
4. Document Verification Module Development
We build the core document-verification engine by implementing structured pipelines for document capture, security checks, data extraction, and authenticity validation. Our goal is to ensure consistent accuracy across global ID formats and support evolving document standards.
5. Biometric & Liveness Module Development
We develop facial-matching and liveness modules by integrating biometric comparison logic, motion analysis, and anti-spoofing techniques. Each component is calibrated to deliver high-confidence identity validation with minimal user effort and strong resistance against spoofing attempts.
6. Risk & Fraud Analysis Engine Development
We implement risk scoring with configurable rules, behavioral signals, and metadata inspection. The system correlates device patterns, geo-signals, and user behavior to identify anomalies and generate a dynamic risk profile for each verification attempt.
7. Compliance & Screening Integration
We integrate screening logic for KYC, AML, and PEP checks and map the workflows to regulatory requirements. Our developers ensure seamless identity resolution, audit logs, and compliance-ready verification outputs for businesses operating in regulated sectors.
8. Admin Dashboard & Analytics Setup
We build a centralized dashboard that provides real-time monitoring, case management, and operational insights. It includes verification summaries, risk indicators, and performance analytics to help teams make informed decisions and refine onboarding flows.
9. Quality Assurance & Security Validation
We run extensive QA cycles that include edge-case testing, spoofing scenario validation, and stress testing of verification pipelines. Every step is reviewed to ensure data integrity, reliable decision-making, and robust protection of sensitive identity information.
10. Deployment & Optimization
We deploy the platform in a secure environment with full monitoring, logging, and incident-response mechanisms. After launch, we continuously optimize verification accuracy, reduce friction, and refine risk strategies using ongoing performance data.
Cost to Build a Veriff-like Identity Verification Platform
The cost to develop a Veriff-style identity verification solution depends on features, compliance needs, and integration complexity. Explore the major cost drivers to plan your investment effectively.
| Development Phase | Description | Estimated Cost |
| Consultation & Planning | Defines project goals, compliance needs, and verification strategy through structured discovery. | $4,000 – $7,000 |
| User Flow & Verification Journey Design | Creates frictionless verification paths for document capture, biometrics, and secure interactions. | $5,000 – $8,000 |
| Architecture Planning | Outlines a scalable identity framework with modular, high-availability components. | $6,000 – $10,000 |
| Document Verification Module Development | Builds ID validation pipelines with OCR extraction, security checks, and global document handling. | $14,000 – $30,000 |
| Biometric & Liveness Module Development | Develops face-matching and liveness detection with anti-spoofing and real-user presence checks. | $13,000 – $27,000 |
| Risk & Fraud Analysis Engine Development | Implements risk scoring, device analysis, and behavioral anomaly detection. | $12,000 – $25,000 |
| Compliance & Screening Integration | Integrates AML, PEP, and sanctions screening with audit-ready workflows. | $6,000 – $12,000 |
| Admin Dashboard & Analytics Development | Creates a centralized dashboard with verification insights and operational metrics. | $7,000 – $13,000 |
| QA Testing | Conducts security testing, spoofing checks, and accuracy validation across identity flows. | $5,000 – $9,000 |
| Launch & Maintenance | Provides ongoing optimization for fraud patterns, compliance updates, and performance tuning. | $7,000 – $17,000 |
Total Estimated Cost: $64,000 – $125,000
Note: Actual costs vary by project scope, verification complexity, regulations, and biometric or fraud-detection sophistication. Customization and ongoing optimization also impact the budget.
Consult with IdeaUsher for a personalized cost estimate and a tailored roadmap to build a high-performing identity verification platform aligned with your business and compliance goals.
Cost Affecting Factors to Consider During Development
The development cost of a Veriff-style identity verification platform depends on key factors such as features, integrations, and regulatory requirements.
1. Project Scope and Feature Complexity
Broader feature sets such as document analysis, biometrics, and liveness detection increase development effort because each verification capability requires specialized logic, extensive testing, and well-structured identity workflows.
2. Global Document Coverage
Supporting passports, IDs, and licenses across regions demands template mapping, localized validation rules, and adaptable OCR logic, which increases engineering time and dataset preparation needs.
3. Biometric and Liveness Requirements
Building accurate facial matching with quality scoring and anti-spoofing checks requires advanced algorithms and dedicated calibration, which elevates both development complexity and implementation cost.
4. Compliance and Regulatory Alignment
Integrating AML, PEP, and KYC workflows, while ensuring data privacy compliance, adds cost due to required rule mapping, audit logs, and secure identity-handling standards.
5. Integration Requirements
Connecting with CRMs, databases, and third-party services demands custom integration flows, additional testing cycles, and alignment with existing operational systems.
Challenges & How to Overcome Those?
Developing a Veriff-like identity verification platform presents technical, compliance, and user-experience challenges. Here’s a brief overview of common hurdles and solutions to help you build a secure, scalable, and conversion-friendly KYC system.
1. Ensuring High-Accuracy Document Recognition
Challenge: Global IDs differ widely in structure, security elements, and print quality, which makes consistent document authenticity checks difficult across diverse lighting and capture conditions.
Solution: We strengthen recognition by calibrating adaptive OCR models, refining template classification, and expanding real-world datasets. Our developers apply targeted document forensics to detect microprint, MRZ integrity, and layout anomalies for reliable global verification.
2. Achieving Reliable Biometric Matching
Challenge: Facial images captured in low light or inconsistent angles can reduce the accuracy of biometric comparison, increasing both false positives and false negatives.
Solution: We improve matching by enforcing guided selfie capture, applying landmark calibration, and using optimized embedding models. Our process includes face-quality scoring and controlled comparison logic to keep biometric decisions stable across unpredictable environments.
3. Preventing Spoofing and Deepfake Attempts
Challenge:
Modern spoofing attacks use masks, printed photos, and deepfake videos that can bypass weak liveness checks and traditional visual validation.
Solution: We strengthen protection using multi-layered anti-spoofing classifiers that read depth cues, temporal consistency, and skin texture signals. Our team trains detection models on diverse spoof datasets to reliably identify synthetic or staged media.
4. Maintaining Real-Time Risk Assessment
Challenge: High traffic makes it challenging to compute risk scores quickly while analyzing device signals, behavior anomalies, and metadata patterns in real time.
Solution: We streamline scoring through lightweight rule evaluation, optimized session analysis, and cached low-risk outcomes. Our risk engine correlates device fingerprints and geo-signals within milliseconds to maintain responsive verification during peak load.
5. Protecting Sensitive Identity Data
Challenge: Handling biometric and government ID information increases the risk of exposure, making data security a critical challenge during verification and storage.
Solution: We apply encrypted transmission, strict access controls, and tamper-resistant storage. Our team performs continuous security audits, intrusion monitoring, and threat detection to keep sensitive identity data protected throughout every stage of verification.
Conclusion
Building a Veriff-like online identity verification platform that delivers accuracy, speed, and user trust requires a careful blend of advanced verification workflows, strong security practices, and compliance readiness. As you plan the structure of your solution, you can see how essential it is to balance automation with robust fraud prevention. An online identity verification platform becomes truly effective when it offers reliable checks, seamless onboarding, and scalable architecture that adapts to new threats. With the right approach, creating a secure and efficient verification experience becomes achievable for any growing business.
Why Choose IdeaUsher for Your Online Identity Verification Platform?
At IdeaUsher, we specialize in building robust identity verification systems that combine AI-powered document scanning, facial recognition, and secure authentication to deliver strong KYC compliance and frictionless user onboarding.
Why Work with Us?
- Expert Identity Verification Knowledge: We implement advanced OCR, biometric, and real-time authentication technologies for accurate user verification.
- Custom Compliance Solutions: We tailor verification flows, data handling, and audit trails to match your regulatory and business requirements.
- Secure & Scalable Architecture: Our platforms are built to handle high user volume, encrypted storage, and scalable verification throughput.
- User Experience Focus: We balance strong security with seamless UX to maintain high conversion and user satisfaction.
Explore our portfolio to see how we helped companies deploy secure identity verification systems.
Contact us to build your own compliant and user-friendly online identity verification platform.
Work with Ex-MAANG developers to build next-gen apps schedule your consultation now
FAQs
An online identity verification platform allows businesses to confirm user identities digitally. It combines document scanning, biometric checks, and real-time authentication to prevent fraud, ensure compliance, and streamline user onboarding securely and efficiently.
A Veriff-like platform should include AI-based document verification, facial recognition, liveness detection, multi-device support, and secure data storage. These features enhance accuracy, reduce identity fraud, and maintain a seamless user experience.
Verification platforms help companies comply with KYC and AML regulations by securely validating users’ identities. They create audit trails and ensure that only verified individuals access services, reducing regulatory risk and operational exposure.
Technologies like AI, machine learning, optical character recognition, biometric authentication, and secure cloud storage form the backbone of online identity verification platforms, enabling fast, accurate, and tamper-proof identity validation.