Industrial environments were never designed with today’s cyber threats in mind, yet factories, power plants, and critical infrastructure are now more connected than ever. Legacy systems, aging equipment, and limited visibility make it difficult to spot risks before they disrupt operations or compromise safety. This growing exposure is why many organizations are exploring a Nozomi-like OT security AI detection tool that can continuously monitor operational technology environments without interfering with real-time processes.
AI-driven OT security platforms focus on understanding how industrial systems normally behave and detecting deviations early. By analyzing network traffic, device communications, and operational patterns, these tools can identify anomalies that signal potential faults, misconfigurations, or cyber intrusions. Machine learning helps reduce noise, adapt to complex environments, and give security teams actionable insights while keeping operations running smoothly.
In this blog, we’ll break down how to build an AI-powered OT security tool similar to Nozomi, covering the core features and underlying technologies. This guide will give you a clear roadmap for creating a scalable and reliable OT security platform.

What is an OT Security AI Detection Tool, Nozomi?
Nozomi (by Nozomi Networks) is an AI-driven OT and IoT cybersecurity platform providing real-time visibility, anomaly detection, threat identification, and risk prioritization. It unifies asset discovery, continuous monitoring, and AI analysis, helping organizations detect vulnerabilities and respond with actionable intelligence without disrupting industrial or critical infrastructure operations.
This platform is for environments prioritizing safety, uptime, and reliability, where traditional security tools fall short. It uses AI and machine learning to learn normal traffic and device behaviors, quickly spotting deviations that may signal cyberattacks, misconfigurations, or anomalies.
- Deep Packet Inspection across 250+ industrial protocols enables granular analysis of OT and IoT traffic, empowering richer behavioral modeling and anomaly detection.
- Adaptive AI learning enriched by continuous asset intelligence reduces false alerts by distinguishing benign operational changes from real threats in dynamic industrial environments.
- Native AI-trained query assistant can interpret and explain complex OT/IoT risk questions in plain language using environment-specific models, accelerating insights and remediation planning.
- Continuous passive network monitoring with automated vulnerability assessment surfaces hidden device risks and misconfigurations while preserving OT process integrity.
A. Business Model: How It Operates
Nozomi Networks uses a hybrid software-plus-services model for industrial and critical infrastructure needing continuous visibility, threat detection, and resilience. It offers OT cybersecurity software, cloud services, and expert support for distributed networks.
- OT and IoT Security Platform Licensing: Provides access to a unified platform for real-time visibility, threat detection, asset intelligence and operational monitoring across industrial networks.
- Cloud and On-Premise Deployment Flexibility: Customers can deploy the platform in the cloud, on-premises or through hybrid models to match operational and regulatory requirements.
- Sensor and Edge Appliance Ecosystem: Offers hardware and virtual sensors that collect industrial telemetry and feed it into centralized analytics platforms.
- Advanced Analytics and AI Add-Ons: Includes optional modules for AI insights, behavioral modeling, predictive analytics and automated risk interpretation.
- Threat Intelligence Subscriptions: Delivers continuous updates on OT/IoT vulnerabilities, attacker tactics and industry-specific threat activity.
B. Fundings of Nozomi Networks
Nozomi Networks has raised significant venture capital over multiple rounds to build and scale its OT and IoT security platform, attracting strategic and institutional investors from across the technology and industrial sectors.
a. Key Funding Rounds:
- Series A (~2016): Nozomi Networks raised about $7.5 million in its Series A round led by GGV Capital and Lux Capital to support early growth and market expansion.
- Series C (2018): The company raised $30 million, bringing total funding to around $53.8 million at the time and fueling global expansion and R&D.
- Series D (2021): Nozomi announced a $100 million pre-IPO investment led by Triangle Peak Partners with participation by Honeywell Ventures, Porsche Ventures, In-Q-Tel, Keysight Technologies and others.
- Series E (2024): The company secured another $100 million in funding from strategic investors including Mitsubishi Electric and Schneider Electric to accelerate product innovation and global go-to-market expansion.
b. Acquisition (2025)
In September 2025, Mitsubishi Electric announced an agreement to acquire Nozomi Networks in a deal valued at approximately $1 billion, reflecting the company’s strong position and investor confidence in OT security.
Why Traditional IT Security Models Fail in OT Environments?
Traditional IT security models often fall short in OT environments due to unique operational constraints, legacy systems, and real-time requirements. Understanding these gaps is key to safeguarding industrial and critical infrastructure.
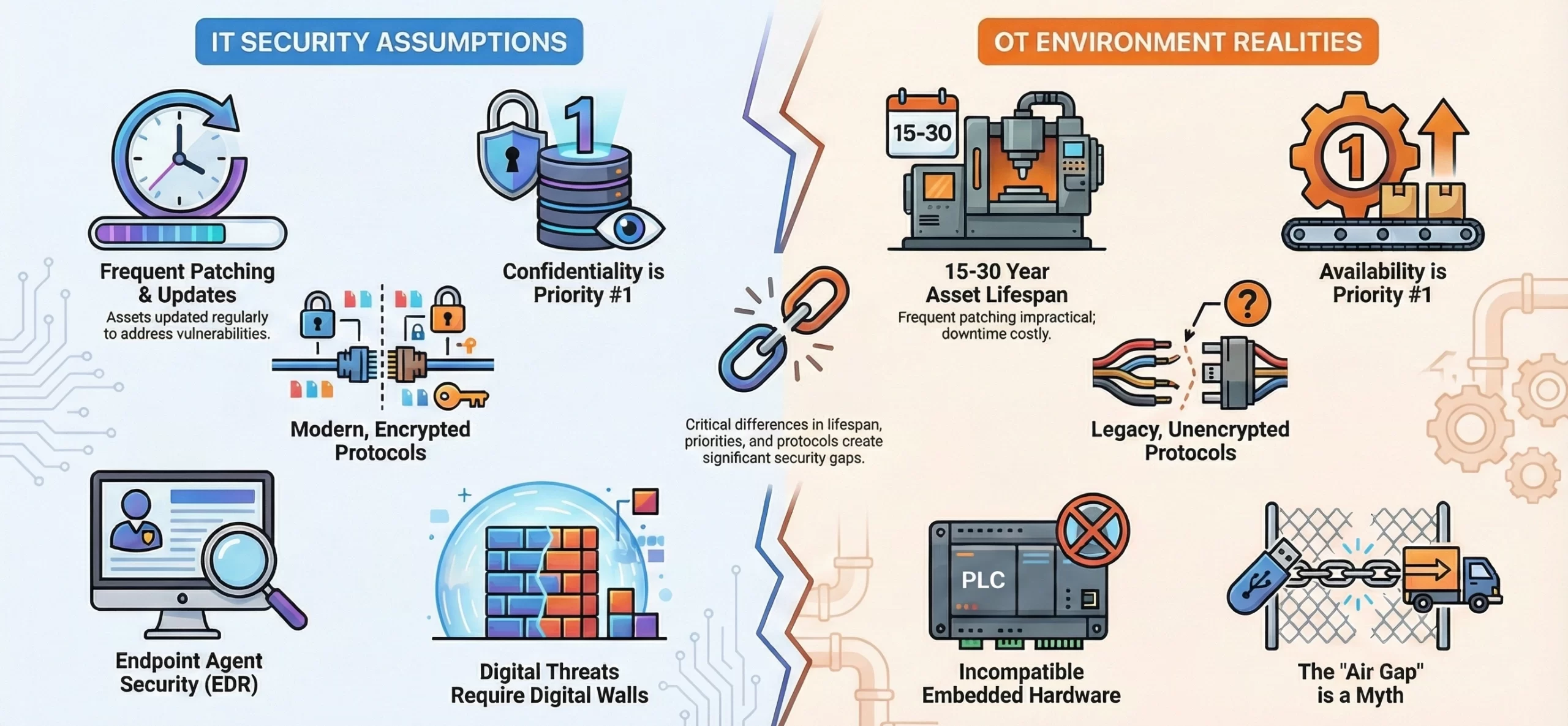
1. Legacy Protocols & Deterministic Communication
OT networks rely on legacy protocols like Modbus, DNP3, and PROFINET that lack encryption. Traditional IT inspection introduces latency that disrupts deterministic control loops, risking process instability, safety system faults, and real-time operational failures.
2. Asset Longevity vs. Patch Management
OT assets operate for 15 to 30 years, making frequent patching impractical. IT security remediation cycles conflict with availability requirements, where downtime costs facilities up to $260,000 per hour and introduces operational and safety risks.
3. Availability First Security Model in OT Systems
OT security prioritizes availability and integrity over confidentiality. IT zero trust segmentation and continuous authentication add latency and interrupt persistent device communications required between field assets and control systems for stable operations.
4. Air Gap Assumptions vs. IT OT Convergence
Air gap models no longer apply as IIoT, remote access, and ERP integration drive IT OT convergence. Threats like Triton and Industroyer exploit supply chains, removable media, and jump hosts to breach isolated environments.
5. Endpoint Security Limits in Industrial Hardware
EDR tools require resources unavailable on PLCs and embedded controllers. Installing agents violates IEC 61508 certifications, while deterministic behaviors trigger false positives, making endpoint-based security incompatible with safety-critical OT systems.

Why 70–80% of OT Assets Require OT-Native AI Security Detection?
The global operational technology security market was valued at USD 27.03 billion in 2025 and is projected to reach USD 122.22 billion by 2034, growing at a CAGR of 18.25% from 2025 to 2034. This sustained growth reflects increasing reliance on industrial automation and rising exposure to cyber-physical risk.
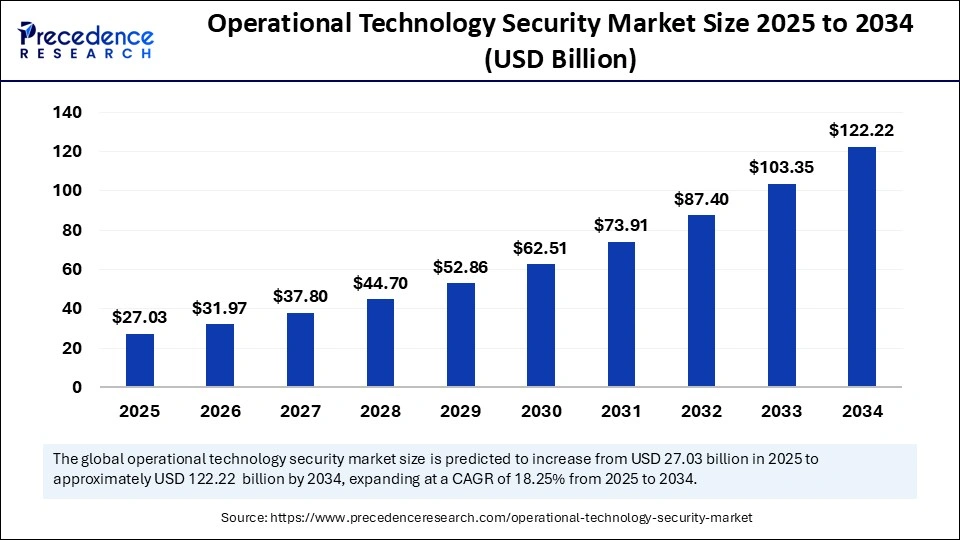
One of the strongest drivers behind this growth is that 70–80% of OT and ICS assets run on non-traditional operating systems, according to SANS. These systems fundamentally change how security detection must be designed, deployed, and operated in industrial environments.
A. Non-Traditional OT Assets Break IT-Centric Security Assumptions
According to the SANS 2024 ICS/OT Cybersecurity Report, 64% of organizations lack adequate OT network monitoring, largely because traditional IT security tools cannot operate effectively in industrial environments.
- Most OT assets cannot support endpoint agents due to proprietary firmware and real-time constraints
- 64% of organizations lack proper network visibility, leaving gaps for undetected threats
- Industrial ransomware attacks increased 87% in 2024, showing that OT assets are high-value targets for cybercriminals
- Legacy industrial protocols lack authentication, confusing IT detection models
- OT-native AI uses passive traffic analysis to restore visibility without disrupting operations
B. OT-Native AI Detection Aligns with Operational and Safety Requirements
SANS reports that 21.5% of OT organizations experience at least one security incident annually, highlighting the need for detection approaches aligned with operational priorities rather than IT-centric controls.
- OT security prioritizes availability and process integrity over confidentiality
- Even brief outages can cost $250,000 to millions per hour, depending on industry and process criticality
- 49% of manufacturing leaders plan to deploy AI/ML for cybersecurity within 12 months, signaling immediate adoption readiness
- Safety-certified systems cannot be modified without extensive revalidation
- OT-native detection correlates cyber events with physical process risk, not IT severity, reducing operational disruptions
The high prevalence of non-traditional OT assets, combined with rising cyber threats and operational risks, makes OT-native AI security detection essential. Purpose-built platforms provide visibility, real-time threat detection, and process-aware protection, ensuring industrial operations remain secure, reliable, and resilient.
Key Features of Nozomi-like OT Security AI Detection Tool
A Nozomi-like OT Security AI Detection Tool combines real-time asset visibility, protocol-aware monitoring, and intelligent threat detection to protect industrial networks. These features collectively support secure, reliable, and resilient OT operations.

1. Real-Time OT & IoT Asset Visibility
The platform continuously discovers OT and IoT devices through passive monitoring and selective active probes. It builds high-resolution asset inventories, identifies communication protocols and reveals device roles, giving security teams deep situational awareness across industrial networks.
2. AI-Powered Anomaly & Threat Detection
The system applies adaptive AI models that baseline operational behavior, inspect industrial protocol traffic and identify deviations in process values or communication flows. This enables real-time detection of both cybersecurity threats and subtle operational anomalies affecting reliability or safety.
3. Vulnerability Assessment & Risk Prioritization
A Nozomi-like tool automatically identifies device vulnerabilities and exposure paths using signature intelligence and configuration analysis. It prioritizes remediation based on operational impact, asset criticality and real-world behavior, helping teams focus on risks that matter most in industrial environments.
4. Threat Intelligence & Alert Correlation
The platform enriches alerts with global OT and IoT threat intelligence, known attacker tactics and protocol insights. Correlation logic groups related events to reduce noise, elevating high-priority incidents that require immediate investigation and response.
5. Centralized Visibility & Management
The OT security AI solution provides unified dashboards that consolidate cross-site OT telemetry, security posture insights and asset inventories. This central management capability simplifies monitoring for distributed facilities and streamlines policy control and configuration oversight across all industrial assets.
6. Endpoint & Wireless Coverage
Beyond network visibility, the platform extends protection with lightweight endpoint sensors that capture host-level behavior, wireless activity and asset posture. This coverage reduces blind spots and reveals threats that bypass network-only monitoring approaches in OT environments.
7. Interactive Network Visualization
The system generates live topology maps that show real communication flows, protocol usage and trust boundaries across industrial zones. These visualizations accelerate investigations by highlighting abnormal traffic paths or unexpected device relationships within OT networks.
8. AI Trained Environment Specific Insights
The OT security AI detection tool can embed environment-trained AI models that interpret telemetry patterns and answer security questions with context-aware reasoning. This capability supports faster decisions, clearer risk explanations and more precise operational guidance for industrial security teams.
9. Autonomous Protocol Behavior Normalization Engine
This engine employs AI to learn normal command structures, timing patterns and payload signatures in industrial protocols automatically, without manual rules. It detects malformed, out-of-sequence, or impersonated commands used by attackers to manipulate controllers or disrupt processes.
10. AI-Based Supply Chain Device Trust Scoring
The platform assigns dynamic trust scores to OT and IoT devices by analyzing firmware, lineage, vulnerabilities, and behavior. This detects compromised, counterfeit, or tampered devices, enhancing supply chain security beyond traditional asset discovery.

How to Create an OT Security AI Detection Tool like Nozomi?
Creating a Nozomi-like OT Security AI Detection Tool requires aligning industrial expertise, data-driven intelligence, and secure system design. Our developers follow a structured development approach that helps ensure accuracy, reliability, and operational trust across OT environments.
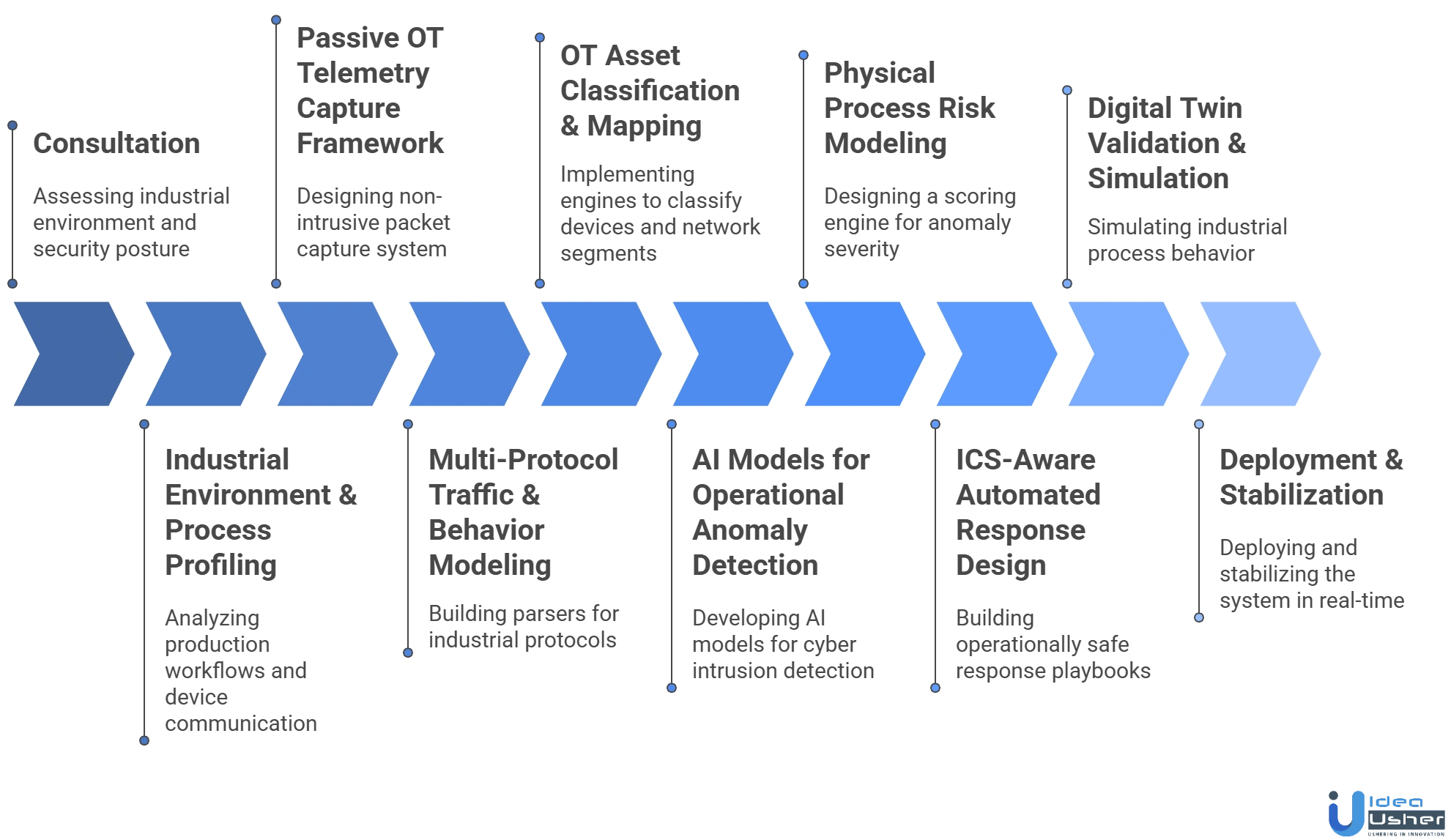
1. Consultation
We begin by assessing the client’s industrial environment, reviewing control systems, existing ICS security posture and operational constraints. Our developers study process flows, protocol usage and plant-level dependencies to design a platform aligned with operational safety and real-time monitoring needs.
2. Industrial Environment & Process Profiling
We analyze production workflows, control loop structures and device communication patterns to understand how machines, sensors and controllers interact. This lets us model process dynamics so detection logic reflects real operational behavior instead of generic IT traffic assumptions.
3. Passive OT Telemetry Capture Framework
Our developers architect a passive monitoring system that reads industrial traffic without interfering with processes. We design non-intrusive packet capture, protocol-aware parsing and timing preservation to safely observe PLC, HMI and sensor activity in real-time.
4. Multi-Protocol Traffic & Behavior Modeling
We build parsers for industrial protocols like Modbus, DNP3, IEC 104 and proprietary ICS languages. The system learns command structures, register patterns and payload signatures to detect unsafe write attempts, malformed commands or control logic manipulation.
5. OT Asset Classification & Mapping
We implement engines that classify field devices, controllers, safety systems and network segments. The platform creates a communication behavior graph that models trust boundaries, zone interactions and expected device relationships across the industrial network.
6. AI Models for Operational Anomaly Detection
We develop AI models trained on control loop signals, sensor trends and command timing to detect deviations indicating cyber intrusions or equipment issues. These models uncover abnormal process shifts, unauthorized setpoint changes or irregular actuator behavior.
7. Physical Process Risk Modeling
We design a scoring engine that weighs anomaly severity based on process importance, device criticality and potential operational disruption. This OT-specific context ensures alerts reflect real physical risk, not just network irregularity.
8. ICS-Aware Automated Response Design
Unlike IT security, OT response must avoid production disruption. We build operationally safe playbooks that isolate malicious traffic, block harmful commands or alert operators while preserving control loop stability and safety constraints.
9. Digital Twin Validation & Simulation
We simulate industrial process behavior using digital twins or environment replicas to test model accuracy. This helps validate false-positive reduction, control-loop sensitivity and anomaly thresholds before deployment in live industrial settings.
10. OT Deployment & Baseline Stabilization
We deploy passively, monitor real operational cycles and gradually stabilize behavioral baselines as the system learns normal ICS activity. Our developers fine-tune process deviation thresholds to prevent false alerts during production shifts or maintenance cycles.
Cost to Build a Nozomi-like OT Security AI Detection Tool
The cost to build a Nozomi-like OT Security AI Detection Tool depends on features, data complexity, and deployment scale. Understanding key cost drivers helps businesses plan development budgets with clarity and confidence.
| Development Phase | Description | Estimated Cost |
| Consultation | Defines industrial scope and process-aware security requirements. | $5,000 – $8,000 |
| Workflow & Threat Modeling | Maps operational flows and OT-specific threat paths. | $6,000 – $12,000 |
| Passive Telemetry Architecture | Builds safe non-intrusive data capture pipelines. | $13,000 – $22,000 |
| Multi-Protocol Behavior Modeling | Develops interpreters and behavioral protocol logic. | $17,000 – $30,000 |
| OT Asset & Communication Graph | Creates device classifications and trust graphs. | $10,000 – $17,000 |
| AI Models for Process Integrity & Anomaly Detection | Trains AI for control deviation and ICS anomaly detection. | $15,000 – $28,000 |
| OT Risk & Contextual Correlation Engine | Builds impact-based scoring logic for physical systems. | $11,000 – $19,000 |
| Safe Response Workflow Design | Designs ICS-aware containment actions. | $8,000 – $12,000 |
| Digital Twin Simulation & Testing | Validates performance using process simulation environments. | $9,500 – $15,500 |
| Deployment & Baseline Stabilization | Ensures accurate behavior baselining and tuning. | $11,500 – $16,000 |
Total Estimated Cost: $67,000- $128,000
Note: Actual costs vary with protocols, plant complexity, asset diversity, safety, and integration. Deep protocol coverage, digital twins, or multi-site setups may need extra investment.
Consult with IdeaUsher for a personalized cost estimate and roadmap to develop an OT Security AI platform tailored to your industrial environment and resilience goals.

Cost-Affecting Factors to Consider
Several technical, operational, and compliance factors influence the overall cost of developing a Nozomi-like OT Security AI Detection Tool, shaping scope, complexity, and long-term scalability.
1. Complexity of Industrial Protocol Coverage
Supporting diverse OT protocols requires specialized parsers and behavioral models. Costs rise when environments include proprietary or legacy protocols with limited documentation and non-standard communication patterns.
2. Scale & Diversity of OT Assets
Larger plants with varied PLCs, RTUs, sensors and IoT devices require extensive asset classification logic, increasing development time and validation demands across different device types.
3. Passive, Non-Disruptive Monitoring
OT systems require non-intrusive telemetry capture to avoid production impact. Engineering safe monitoring frameworks increases both design complexity and implementation cost.
4. Process Integrity & Control Loop Analysis
Analyzing operational signals such as setpoints, actuator behavior and control timing adds cost because the AI must interpret physical process behavior, not just network patterns.
5. Operational Safety for Automated Response
Developing safe containment playbooks that avoid disrupting production requires ICS-aware logic, rigorous testing and coordination with operations teams, which increases development investment.
6. Digital Twin or Simulation-Based Validation
If the project requires validating detection using process simulations or digital twins, costs rise due to modeling complexity and additional scenario testing.
Suggested Tech Stacks for OT Security AI Detection Tool Development
Selecting the right tech stack is essential for building a reliable OT Security AI Detection Tool that supports real-time monitoring and analytics. A well-chosen stack ensures performance, scalability, and long-term maintainability.
| Category | Suggested Technologies | Purpose |
| AI & ML Frameworks | TensorFlow, PyTorch, Scikit-learn | Support behavioral modeling, anomaly detection, and protocol-level intelligence across OT data. |
| OT Protocol Parsing | Custom parsers, Scapy, Wireshark libraries | Decode OT protocols and enable passive traffic monitoring without disrupting operations. |
| Data Streaming & Ingestion | Apache Kafka, Apache Flink, MQTT | Process high-volume OT telemetry in real time and correlate events across devices. |
| Data Storage & Analytics | InfluxDB, TimescaleDB, Elasticsearch | Store sensor, process, and network data for analysis and historical visibility. |
| Dashboards & Visualization | Grafana, Kibana | Present asset insights, network views, and anomaly trends for operators. |
| Asset Integration | CMDB connectors, REST APIs | Enrich asset inventories and link OT devices with enterprise systems. |
| Container & Orchestration | Docker, Kubernetes | Enable scalable, resilient deployment across distributed industrial environments. |
| Alerting & Response | SOAR tools, custom rule engines | Deliver contextual alerts and structured incident response workflows. |
| Simulation & Digital Twin | Unity Simulation, MATLAB Simulink | Test detection logic and validate models using simulated industrial processes. |
Challenges & How Our Developers Will Solve Those?
Building an OT Security AI Detection Tool involves technical, operational, and compliance challenges across industrial environments. Our developers address these issues through structured design, domain expertise, and proven security practices.
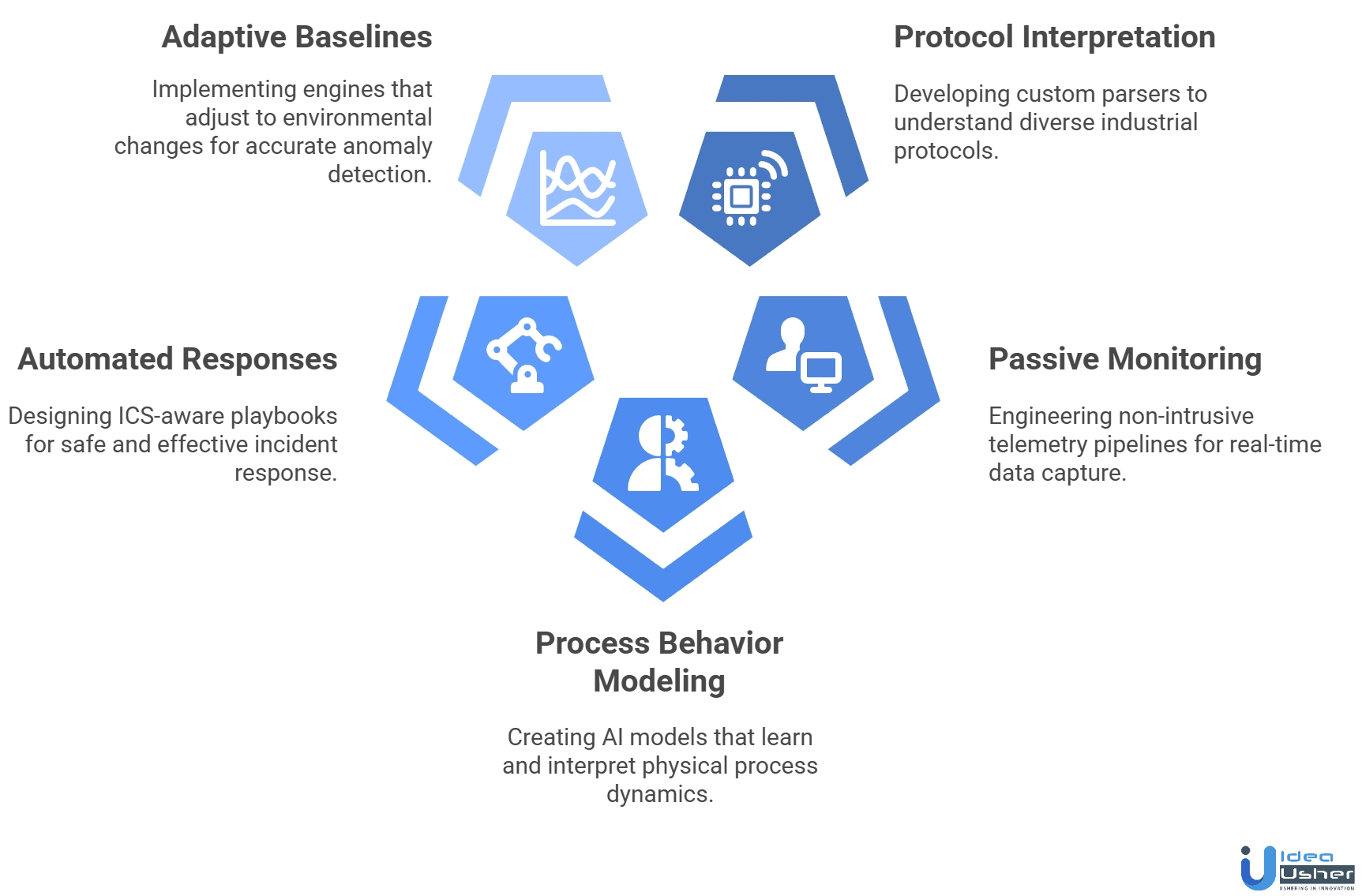
1. Interpreting Industrial Protocols Accurately
Challenge: Many OT environments use undocumented or vendor-specific protocols, making behavioral interpretation extremely difficult for AI models.
Solution: We design custom protocol parsers and train behavioral models on captured field traffic. Our developers build adaptive interpreters that learn command structures, timing patterns and payload semantics directly from real OT communications.
2. Passive Monitoring Without Disruption
Challenge: OT systems cannot tolerate scanning, probing or heavy processing that risks downtime or latency.
Solution: We engineer non-intrusive telemetry pipelines that capture packets passively and preserve timing fidelity. Our approach safeguards PLC cycles and control-loop stability while still delivering high-resolution monitoring.
3. Modeling Physical Process Behavior
Challenge: OT security requires understanding setpoints, actuator behavior and control-loop cycles, which traditional AI models struggle to interpret.
Solution: We develop process-aware AI models that learn sensor trends, command-response patterns and operational baselines. This enables detection of cyber-induced process deviations and subtle shifts in physical system integrity.
4. Safe Automated Operational Responses
Challenge: Incorrect containment in OT can halt production or damage equipment, creating significant safety and financial risks.
Solution: We design ICS-aware response playbooks that restrict malicious commands, isolate compromised devices and escalate alerts while maintaining operational continuity. Each action is validated against process safety constraints.
5. Reliable Anomaly Baselines in Noisy Environments
Challenge: Industrial environments change during maintenance, shift transitions and seasonal cycles, creating variability that complicates learning.
Solution: We implement adaptive baseline engines that re-learn behavior across operational cycles, filtering maintenance-related noise and adjusting thresholds to minimize false positives during normal plant variability.
Conclusion
Building an OT security platform requires more than algorithms and data pipelines. It demands a clear understanding of industrial processes, safety priorities, and the realities of legacy environments. When you design a Nozomi-like OT Security AI Detection Tool, success comes from combining accurate asset visibility, contextual threat detection, and explainable insights operators can trust. Thoughtful architecture, high-quality telemetry, and continuous model refinement help ensure resilience. The goal is not automation alone, but confidence for teams responsible for protecting critical operations. This perspective helps align technology decisions with real operational outcomes.
Why Choose IdeaUsher to Build an OT Security AI Detection Tool?
At IdeaUsher, we specialize in designing and developing advanced OT security AI solutions tailored for industrial environments. From manufacturing and energy to utilities and critical infrastructure, we help businesses build intelligent platforms that provide deep asset visibility, threat detection, and operational trust.
Why Partner With Us?
- OT and Industrial Security Expertise: Our team understands industrial protocols, legacy systems, and safety-critical operations.
- AI Driven Security Architecture: We build AI models focused on anomaly detection, behavioral analysis, and actionable risk insights.
- End-to-End Product Development: From strategy and data architecture to deployment and scaling, we support the entire product lifecycle.
- Market Ready Solutions: We help you design platforms that meet compliance, performance, and buyer expectations in the OT security market.
Explore our portfolio to see how we deliver a range of AI solutions for enterprises across industries.
Connect with our experts to discuss how we can help you bring your OT security AI product to market with confidence.
Work with Ex-MAANG developers to build next-gen apps schedule your consultation now
FAQs
To build an OT Security AI Detection Tool like Nozomi, you need real-time asset discovery, protocol-aware traffic analysis, anomaly detection, risk scoring, and incident contextualization. These features help industrial teams detect threats without disrupting operational continuity.
AI models for OT security must be trained using passive network data, industrial protocols, and historical operational behavior. Labeling normal versus abnormal patterns is critical, as OT environments prioritize stability, safety, and low tolerance for false positives.
Launching an OT security AI product involves handling legacy systems, limited data access, strict uptime requirements, and long sales cycles. Gaining trust from industrial operators and proving reliability in real-world environments is often the biggest hurdle.
Differentiation comes from accurate detection, clear risk explanations, easy deployment, and seamless integration with existing OT and SOC tools. Buyers value solutions that reduce alert fatigue while providing actionable insights aligned with industrial operations.