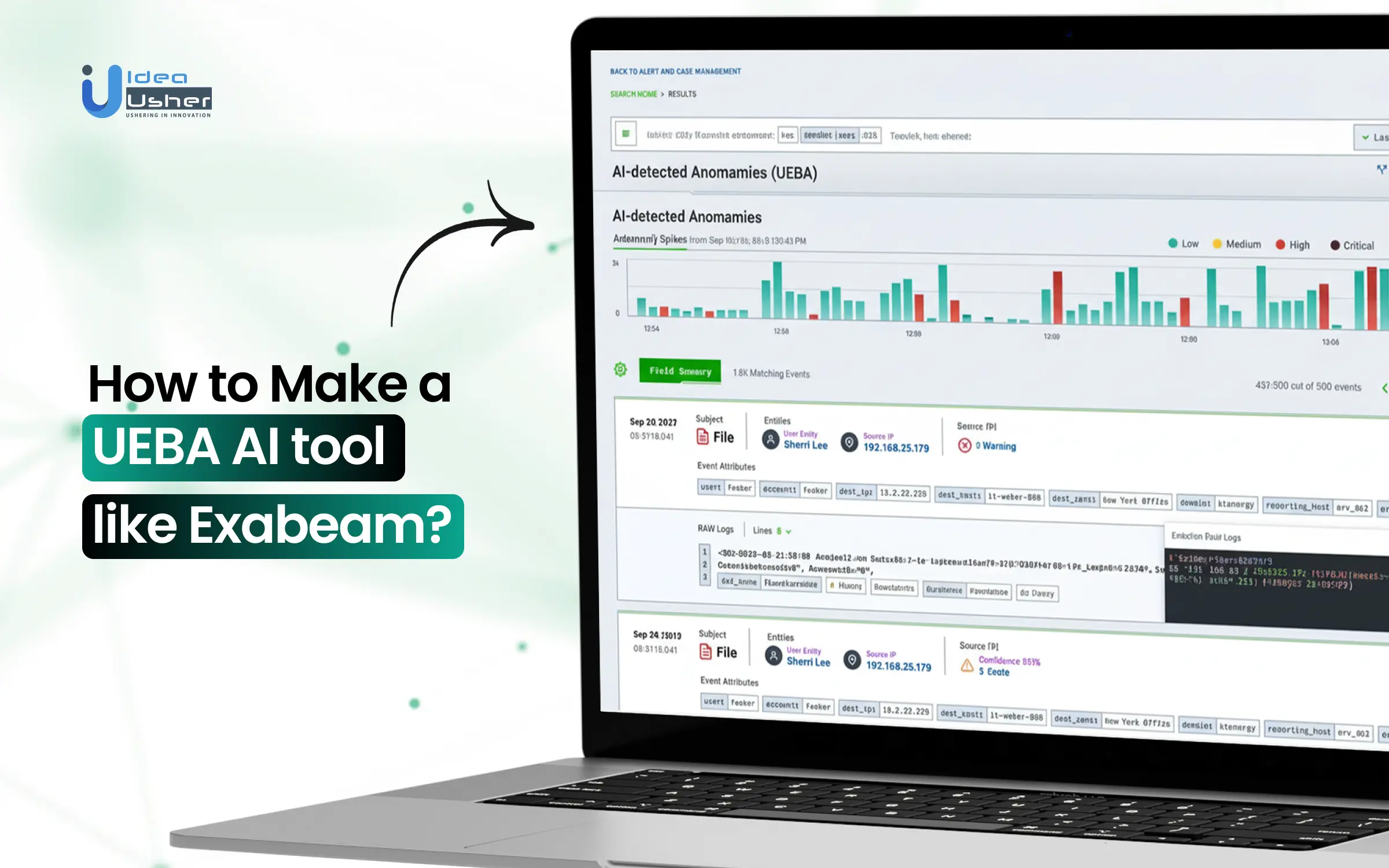
Security teams today face nonstop streams of authentication events, access attempts, and system actions that never truly pause. Somewhere inside that volume, early indicators of compromise may quietly exist. Analysts can identify the risk but must continually decide which behavior matters. This is why UEBA AI tools are becoming essential in modern security stacks.
Platforms like Exabeam have shown that modeling normal behavior, building session-based timelines, and dynamically scoring risk can significantly sharpen detection. A well-built UEBA system should gradually learn patterns that correlate activity across users and devices and clearly explain why something is risky.
Over the past decade, we’ve developed several UEBA-driven security analytics solutions, powered by behavioral machine learning and entity graph analytics. Thanks to this expertise, we’re sharing this blog to discuss the steps to make a UEBA tool like Exabeam. Let’s start!
Key Market Takeaways for UEBA AI tools
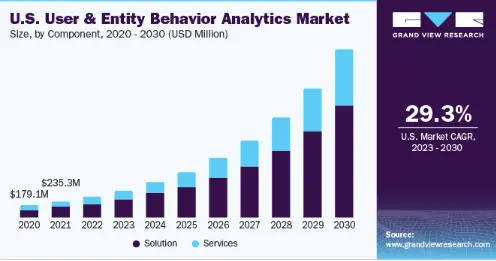
Source: GrandViewResearch
UEBA AI tools are surging in popularity as organizations combat sophisticated insider threats, lateral movement, and AI-enhanced attacks, with machine learning enabling real-time behavioral baselining that outperforms traditional rules-based systems.
Adoption accelerates in cloud-heavy environments such as BFSI and IT, where regulations such as GDPR increase the need for proactive monitoring, while integrations with SIEM platforms reduce alert fatigue by up to 90%.
Exabeam leads with its New-Scale Security Operations Platform, deploying over 750 behavioral models and Smart Timelines™ for automated anomaly prioritization and MITRE ATT&CK-aligned threat hunting across hybrid clouds.
Securonix excels with cloud-native UEBA in its Unified Defense SIEM, leveraging peer group analysis and prebuilt threat chains to reduce false positives and detect low-and-slow attacks.

What is the Exabeam Platform?
The Exabeam Platform is a cloud-native security operations platform built to help security teams detect, investigate, and respond to threats faster and more effectively. It brings together core security capabilities, including SIEM, user and entity behavior analytics, log management, and automation, into a single system.
By applying AI and machine learning, Exabeam helps organizations identify insider threats, external attacks, and risky behavior while also supporting compliance and large-scale security operations.
Here are some of its standout features,
1. Threat Center
The Threat Center serves as a unified workspace where security teams can manage all aspects of threat detection, investigation, and response. It offers a real-time view of security incidents, allowing analysts to quickly assess, prioritize, and address emerging threats from a single dashboard.
2. Search
Exabeam’s Search function enables users to run fast, scalable queries across large data volumes. With natural language processing, analysts can quickly search petabytes of security data, simplifying event lookups and accelerating investigations.
3. Dashboards
The Dashboards feature offers customizable visualizations of security data, alerts, and metrics. Analysts can monitor trends and track the health of their security environment with intuitive charts, helping them stay on top of potential threats and critical incidents.
4. Automation Management
With Automation Management, users can create no-code playbooks that streamline and automate incident response. This feature reduces manual workloads, ensures consistent actions, and speeds up resolution times, allowing security teams to respond to threats more efficiently.
5. Log Stream
Log Stream provides a centralized console for managing log data and parsers in real time. It allows teams to ingest, monitor, and enrich logs seamlessly across on-prem, cloud, and SaaS sources, supported by over 9,500 pre-built parsers, ensuring high-quality data for threat detection.
6. Outcomes Navigator
The Outcomes Navigator provides actionable recommendations to improve threat-detection coverage. It helps security teams focus on the most valuable use cases, prioritize their efforts, and optimize their security strategies to improve outcomes and mitigate risk.
7. Collectors
Exabeam’s Collectors simplify the process of gathering and onboarding logs from diverse data sources. Whether it’s on-premises, in the cloud, or from SaaS applications, Collectors ensure seamless log integration and real-time data flow into the platform, making it easier for analysts to monitor and respond to security events.
How Does the Exabeam Platform Work?
Exabeam works by first normalizing data from over 900 sources into a standardized model. It then uses machine learning to detect anomalies based on user behavior and context. Finally, Exabeam automates responses by using AI agents to investigate, advise, and take action on potential threats.
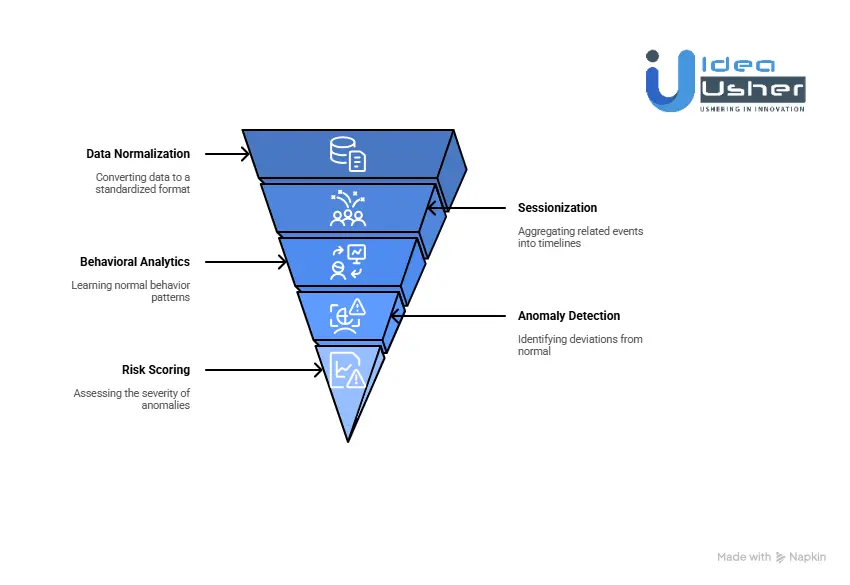
Layer 1: Data Normalization & Sessionization
The first challenge in cybersecurity is dealing with the massive volume of data from various sources. Exabeam tackles this by normalizing and organizing security data.
Universal Translation
Exabeam ingests logs from over 900 sources (e.g., firewalls, endpoints, cloud services) and uses parsers to convert them into Exabeam’s Common Information Model (CIM). This process ensures that all security data, regardless of origin, is presented in a standardized format.
Entity-Centric Organization
Instead of sorting security events by time, Exabeam organizes them around entities like users, hosts, applications, and IP addresses. Each entity has its own dynamic, real-time profile that is continuously updated as more data is ingested. This structure enables more insightful, entity-based analysis.
Smart Sessionization: Exabeam’s patented sessionization engine aggregates related events into a continuous timeline. For example:
- 9:00 AM: User “jsmith” authenticates from New York.
- 9:05 AM: “jsmith” accesses the financial database.
- 9:15 AM: “jsmith” downloads 2GB of sensitive files.
- 9:30 AM: Connection to an unusual external IP.
Traditional SIEMs would treat each of these as separate alerts, creating noise. Exabeam, however, consolidates these activities into a single chronological event, “Potential Data Exfiltration by jsmith,” providing clearer insights.
Layer 2: Behavioral Analytics & Risk Scoring
Once the data is cleaned and organized, Exabeam applies advanced machine learning to understand what “normal” behavior looks like.
Dual Baselining:
- Personal Baseline: The system learns each user’s typical behavior—such as login times, applications accessed, and data volumes. It uses this baseline to identify deviations.
- Peer Group Baseline: Exabeam compares each user to similar colleagues, looking at factors like role, department, and access levels, to detect anomalies in a broader context.
Anomaly Detection Engine
Exabeam uses a combination of machine learning algorithms to detect abnormal behavior, including:
- Isolation Forests: Identify statistical outliers that deviate significantly from normal patterns.
- Clustering Algorithms: Group similar users to compare their behaviors and detect anomalous activity.
- Sequence Analysis: Detect unusual behavior patterns that occur over time, such as an unexpected sequence of actions by a user.
Context-Aware Risk Scoring
Not all anomalies are inherently threats. Exabeam’s risk engine provides additional context to assess the severity of detected anomalies:
- Is the user an executive with broader access?
- Are they accessing high-value or sensitive assets?
- Does the behavior align with known attack patterns (e.g., MITRE ATT&CK)?
In this context, Exabeam generates a dynamic risk score (0-100) that updates as more data is added. This ensures that security teams focus on the most critical alerts, helping to prevent alert fatigue.
Layer 3: Agentic AI & Automated Response
What sets Exabeam apart from traditional SIEM solutions is its ability to take proactive, intelligent action rather than just presenting data.
Exabeam Nova AI Agents
| Agent | What It Does |
| Investigation Agent | Automatically correlates risks to build full incident cases, generates clear reports, and suggests next steps to reduce manual investigation time. |
| Advisor Agent | Reviews the organization’s security posture against industry benchmarks and recommends targeted improvements. |
| Search Agent | Enables natural language searches across security data, such as finding high-risk users who accessed sensitive data within a specific timeframe. |
| Response Agent | Executes approved automated actions through API integrations, such as containing threats or restricting user access without manual effort. |
What is the Business Model of the Exabeam Platform?
Exabeam follows a subscription-based SaaS model, where clients pay annually for access to its cloud-native or self-hosted platforms, such as the New-Scale Fusion SIEM. Unlike competitors such as Splunk, Exabeam’s pricing model is user-centric (per employee) rather thanbased on data volume. This approach enhances pricing predictability for customers.
Exabeam primarily targets mid- to large enterprises, with a focus on cybersecurity organizations. It has a significant concentration in the United States (82.61%), with a growing presence in the UK (7.53%) and Canada (4.18%).
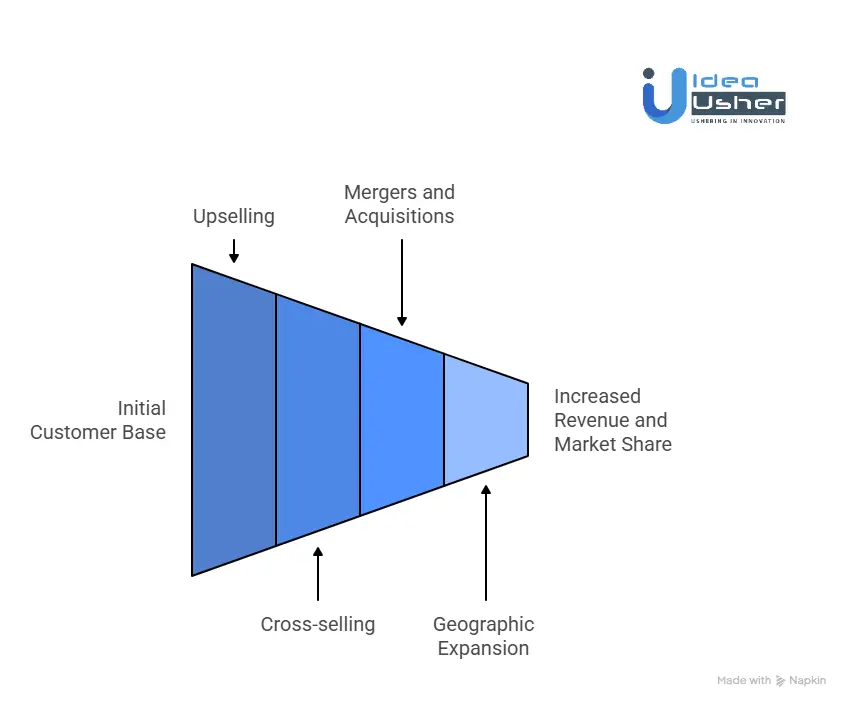
Revenue Streams
The company generates most of its revenue from annual subscriptions, which offer an “all-you-can-eat” model. This model is based on a fixed price for specific data ingestion volumes. For example, an offering such as SIEM-10000-GB-1-YR costs around $3.66 million, while Fusion-2500-GB-1-YR is priced at $1.39 million.
In addition to subscription revenue, Exabeam also earns revenue from partner programs (focused on training), professional services, and renewals. These are designed to enhance its recurring Annual Recurring Revenue (ARR). For instance, the company’s estimated ARR is about $100 million.
Growth Strategy
Exabeam is actively pursuing a growth strategy that includes:
- Upselling existing clients on additional modules.
- Cross-selling other security products.
- Mergers and Acquisitions (M&A), such as the acquisition of LogRhythm in 2024, and Cyberlytic.
- Geographic expansion, exemplified by the opening of an office in Riyadh in November 2024 to cater to the iMETA (Middle East, Turkey, and Africa) region.
The company operates within the $18.12 billion SIEM market as of 2023, positioning itself as a market leader. After the merger with LogRhythm in 2024, Exabeam is focusing on scaling its operations.
Financial Performance
Exabeam has achieved a $2.4 billion valuation, reflecting its growing role in the cybersecurity market, which is experiencing strong demand. The company’s recurring revenue model provides stability and drives profitability through ongoing customer expansion and operational efficiencies.
Funding History
Exabeam has raised a total of over $500 million across seven funding rounds:
- Series A: $10 million in June 2014, with investors like Shlomo Kramer, Norwest, and Aspect Ventures.
- Series B: $25 million in September 2015.
- Series C: $30 million in February 2017.
- Series D: $50 million in August 2018, led by Lightspeed Venture Partners.
- Series E: $75 million in May 2019.
- Series F: $200 million in June 2021.
Exabeam remains a private company and has not yet gone public via an Initial Public Offering. Its investors include a mix of venture capital and private equity firms, as well as strategic investors such as Cisco Investments.

How to Build a UEBA AI Tool Like Exabeam?
To build a UEBA AI tool like Exabeam, it’s crucial to create a stateful identity model that links users, hosts, and service accounts over time. Logs from various sources should then be normalized into a consistent format to support accurate analysis. We have built UEBA AI platforms inspired by Exabeam, and this is how we do it.
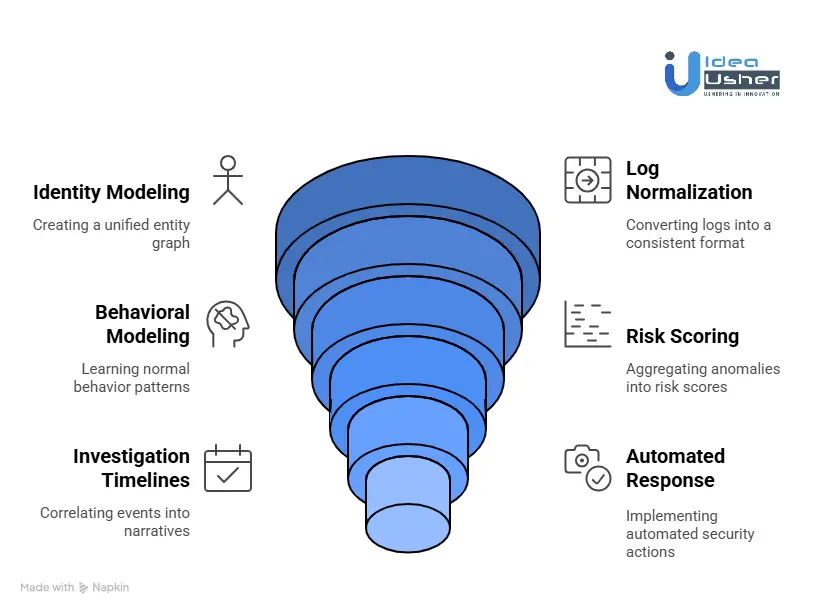
1. Identity and Entity Model
We begin by modeling users, hosts, IP addresses, service accounts, and cloud entities as persistent identities within a unified entity graph. This stateful approach allows us to track behavior over time and across systems, ensuring that activity is analyzed in full context rather than as isolated events.
2. Log Normalization Layer
We build a common information model that normalizes and abstracts logs from thousands of data sources into consistent security semantics. This layer ensures that analytics, detections, and models operate reliably across source formats and environments.
3. Behavioral and Peer Modeling
We develop machine learning models that learn normal behavior patterns over time, across roles, and within peer groups. These baselines continuously adapt, allowing the system to identify meaningful deviations while minimizing false positives.
4. Risk Scoring Engine
We engineer a risk-scoring engine that aggregates anomalies through statistical normalization and business-context weighting. This approach transforms low-level detections into prioritized risk scores that reflect real-world impact.
5. Investigation Timelines
We design investigation timelines that automatically correlate related events into clear, human-readable narratives. This helps SOC analysts quickly understand attack progression and intent without manual log correlation.
6. Automated Response
We integrate automated response and SOAR workflows to enable actions such as account lockouts, session termination, and case creation. This ensures faster containment while maintaining visibility, auditability, and operational alignment.
What is the Growth Potential of a UEBA AI tool?
UEBA, or User and Entity Behavior Analytics, is a high-growth, premium segment within the cybersecurity market, driven by rising breach costs, cloud adoption, and demand for advanced threat detection. Its revenue potential is significant but depends heavily on product positioning, target customers, and the chosen business model.
Revenue Models and Pricing Structures
UEBA platforms employ several revenue models, each with different financial implications:
- Subscription/SaaS Model (Most Common): Annual recurring revenue (ARR) based on data volume, users, or endpoints
- Perpetual License + Maintenance: Traditional enterprise software model with 20-25% annual maintenance fees
- Consumption-Based Pricing: Pay-as-you-go based on actual usage metrics
- Tiered Feature Packages: Different capability levels at different price points
Typical Pricing Ranges:
- Mid-Market (500-2,500 employees): $50,000 – $200,000 annually
- Enterprise (2,500+ employees): $200,000 – $1,000,000+ annually
- Government/Large Financial: $1 million – $5 million+ annually
Real-World Revenue Benchmarks from Established Players
Let’s examine publicly available data and industry estimates:
Exabeam: As a private company, Exabeam doesn’t disclose exact figures, but industry analysts estimate their annual revenue at $150-200 million (pre-merger with LogRhythm). With over 500 enterprise customers, this translates to an average contract value of approximately $300,000-400,000.
Splunk Enterprise Security: As part of Splunk’s $3.65 billion revenue (FY2023), their security segment represents approximately $1.2 billion. While not exclusively UEBA, this includes their UBA capabilities and provides scale context.
Microsoft Sentinel: As part of Microsoft’s broader security business (which grew 33% to $20 billion+ annually), Sentinel’s rapid adoption suggests significant revenue contribution, though exact UEBA-specific figures aren’t broken out.
Market Penetration and Saturation Analysis
Despite rapid growth, UEBA remains underpenetrated. Current adoption rates are approximately:
- Fortune 500: 45-50% penetration
- Enterprise (1000+ employees): 25-30% penetration
- Mid-market (500-1000 employees): 10-15% penetration
- SMB market: <5% penetration
This leaves enormous headroom for growth, particularly in mid-market and specialized verticals. The SMB segment alone represents 3+ million potential customers who will increasingly need UEBA capabilities as they adopt cloud infrastructure and face sophisticated threats.
Vertical-Specific Growth Opportunities:
- Financial Services: Regulatory pressure driving 40%+ adoption rates
- Healthcare: HIPAA compliance and ransomware protection creating 35% growth
- Manufacturing: IoT/OT security convergence with IT UEBA (50% growth potential)
- Government: Zero Trust mandates requiring behavioral analytics (45% growth)

Why 73 % of Global Firms now Use AI in Cybersecurity Defenses?
According to reports, about 73% of global firms now use AI in their cybersecurity defenses. This shift is driven by the growing complexity of cyber threats and the need for faster, more efficient responses. AI helps organizations handle the overwhelming volume of alerts and evolving attacks that human teams might struggle to keep up with.
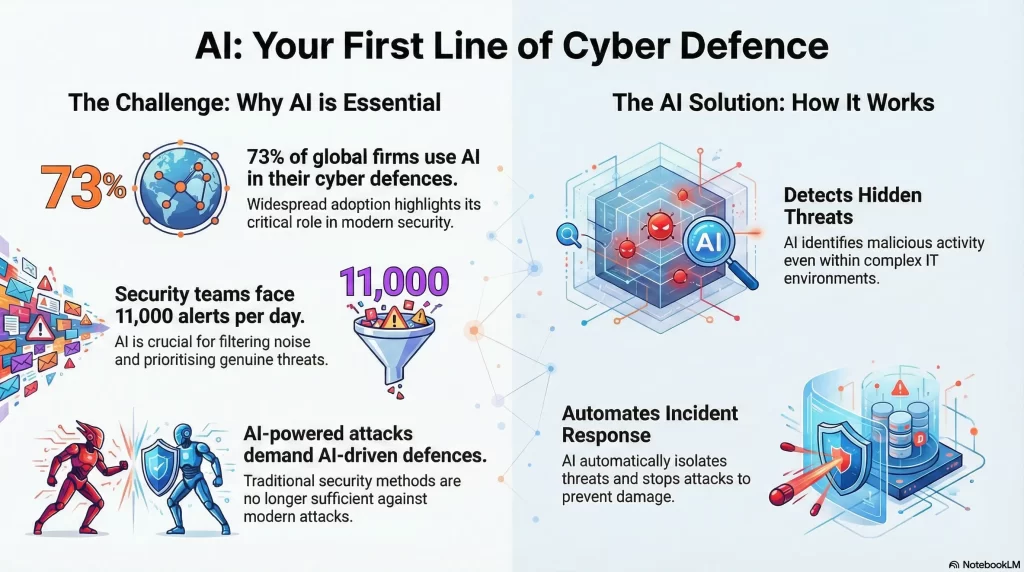
The Perfect Storm Driving AI Adoption
1. The Human Scalability Challenge
Security Operations Centers are caught in a difficult position. While the number of cyber threats continues to rise, the number of skilled security professionals remains dangerously low.
Here is the current reality:
- On average, organizations receive more than 11,000 security alerts per day.
- Only about 19% of these alerts are actual threats.
- More than half of all alerts go uninvestigated due to resource constraints.
- The global cybersecurity talent shortage continues, with 3.5 million unfilled security roles.
AI is not designed to replace human analysts. Instead, it strengthens their effectiveness. By automating time-consuming tasks such as filtering false alarms, correlating related incidents, and prioritizing critical threats, AI allows cybersecurity professionals to focus on high-impact investigations and strategic defense.
2. The Increasing Complexity of Cyberattacks
Cybercriminals are no longer relying on traditional techniques. Many now leverage AI to make attacks faster, more targeted, and harder to detect.
The modern attack landscape includes:
- AI-generated phishing campaigns with highly convincing language and context.
- Adaptive malware capable of learning how to evade detection.
- Automated vulnerability discovery powered by machine learning.
- Synthetic identity attacks that bypass conventional authentication controls.
Maria Chen, CISO of a major financial institution, explains the shift clearly.
“The gap between manual defense and automated offense was becoming unsustainable. To defend against AI-driven attacks, we had to adopt AI-driven defenses.”
3. The Data Overload Dilemma
Enterprise environments are more complex than ever, creating major visibility challenges that traditional security tools cannot handle.
Today’s data reality includes:
- Most organizations rely on multiple cloud providers, increasing security complexity.
- Remote and hybrid workforces access systems from countless devices and locations.
- More than 15 billion IoT devices are connected globally.
- Security log volumes now reach petabyte scale in large enterprises.
Rule-based security systems were designed for simpler, perimeter-focused networks. They struggle in modern distributed environments. AI excels by analyzing massive, diverse datasets and identifying subtle patterns that humans and static rules cannot detect at scale.
How AI Actually Works in Modern Cybersecurity?
Tier 1: Automated Triage and Prioritization
At this level, AI focuses on noise reduction. It reviews alerts, assigns risk scores, and queues the most important incidents for human review.
For example, an AI system may analyze 10,000 daily alerts and identify the 200 that truly require investigation. The result is a dramatic reduction in alert fatigue and significantly faster response times.
Tier 2: Behavioral Analytics and Threat Hunting
Here, AI establishes normal behavior patterns across users, devices, and systems. It then looks for deviations that suggest compromise.
A common example is User and Entity Behavior Analytics. These systems can detect stolen credentials by spotting unusual access patterns that traditional tools miss. Organizations using this approach often reduce attacker dwell time from several months to just a few weeks.
Tier 3: Predictive and Autonomous Response
At the most advanced level, AI does not just detect threats. It acts on them.
These systems can anticipate likely attack paths and automatically isolate infected endpoints before damage spreads. In ransomware scenarios, this can stop execution entirely and prevent millions of dollars in losses.
Conclusion
UEBA platforms like Exabeam clearly point to where enterprise threat detection is heading. They can shift security teams away from noisy alerts and toward context-driven risk decisions that evolve steadily over time. For platform owners, this approach should become a core part of modern security architecture, and it may also unlock a strong SaaS business model. Building such a system can demand disciplined data engineering and mature behavioral analytics that operate efficiently at scale.
Looking to Develop a UEBA AI tool like Exabeam?
IdeaUsher can help you build a UEBA AI tool like Exabeam by leveraging advanced machine learning techniques to detect and respond to anomalies in user behavior. They can design a scalable system that integrates seamlessly with your existing infrastructure.
Why Partner with Us?
- 500,000+ hours of coding expertise — powered by former MAANG/FAANG developers who specialize in scalable, AI-first architectures.
- From sessionization to agentic AI — we build systems that don’t just detect anomalies, but autonomously investigate and explain them.
- Tailored to your SOC’s needs — whether you’re enhancing an existing SIEM or building a next-gen TDIR platform from scratch.
We turn complex challenges into clean, actionable intelligence, so your SOC can focus on what matters: stopping breaches, not searching logs.
Work with Ex-MAANG developers to build next-gen apps schedule your consultation now
FAQs
A1: To develop a UEBA tool like Exabeam, you should start with a clear data strategy and a scalable backend. The platform must ingest logs and identity data in near-real time. You will need machine learning models that can learn behavior gradually and adapt continuously. This system should also integrate seamlessly with SIEM and SOAR tools to enable security teams to respond efficiently.
A2: The key features of a UEBA tool usually focus on behavioral baselining and anomaly detection, while maintaining strong context awareness. It should correlate user actions and device context across the environment. Risk scoring must update dynamically as behavior changes over time. Clear investigation workflows should be in place to enable analysts to act with confidence.
A3: UEBA tools can make money through a SaaS subscription model that scales with data volume or user growth. Some vendors may offer tiered analytics features for larger enterprises. Managed detection services can also be added for recurring revenue. Over time, the platform could support premium integrations and advanced threat modules.
A4: The cost of developing a UEBA tool can vary widely based on scope and scale, but technical depth matters. A basic platform may require significant investment in data pipelines and model training. Ongoing costs will include cloud infrastructure and continuous tuning. With careful planning, organizations can gradually control costs while improving detection accuracy.