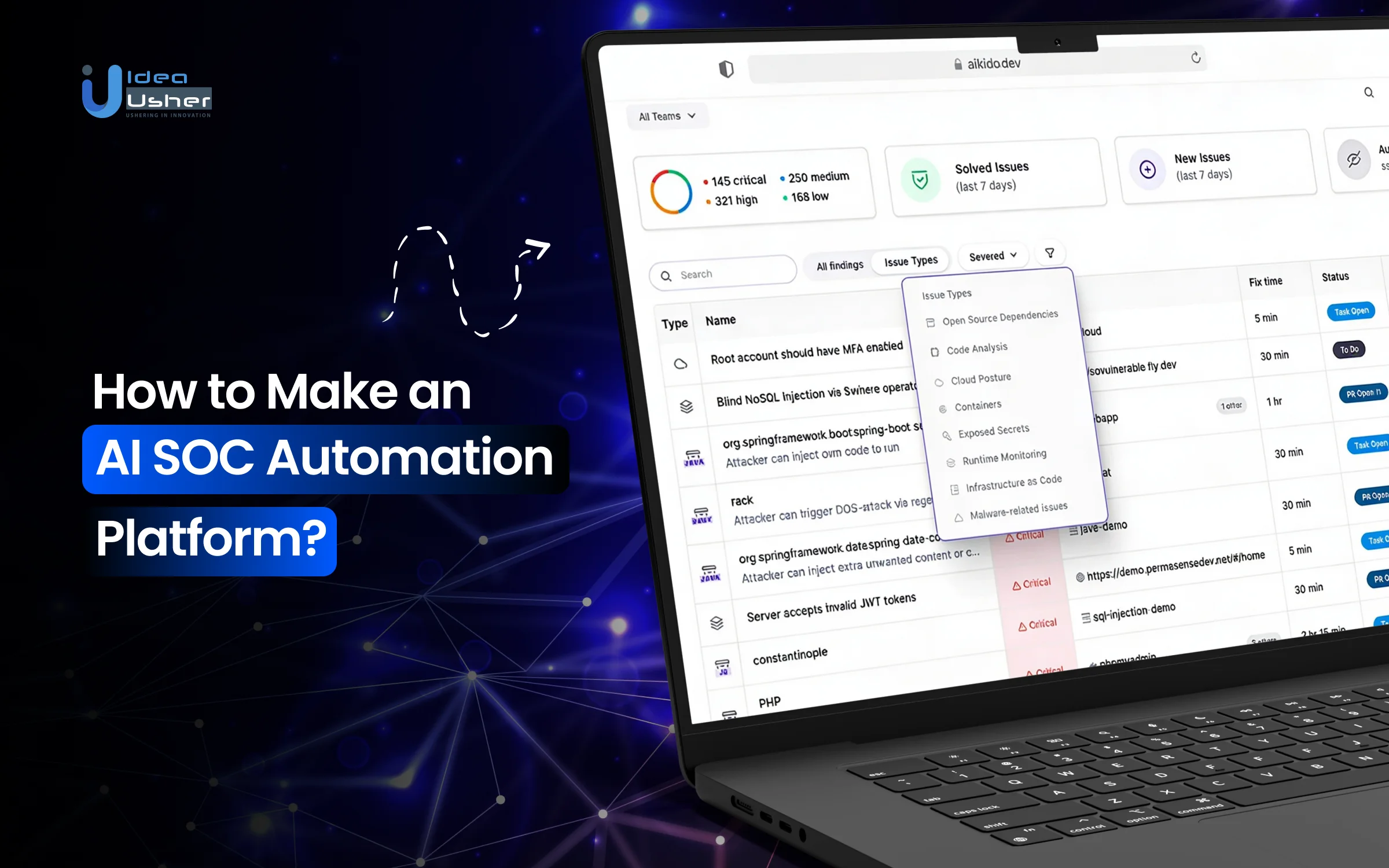
Most security teams spend their days chasing alerts and know the queue will never end. Each notification may demand action, and every pause could increase exposure, which slowly drains focus. Over time, this pressure often leads to alert fatigue and missed threats, as analysts are forced to react rather than investigate. That’s why many teams have started relying on AI-driven SOC automation platforms.
These platforms may correlate events, enrich telemetry, and apply real-time risk scoring and root-cause analysis. Machine learning models surface real risk, while anomaly detection and threat intelligence fusion reduce noise. With automated playbooks handling containment, response teams can finally work deliberately on threats that matter.
Over the years, we’ve built multiple SOC automation solutions using graph-based behavioral analytics and machine learning to handle real-world security complexity. As we have this expertise, we’re writing this blog to discuss the steps to develop an AI SOC automation platform. Let’s start!
Key Market Takeaways for AI SOC Automation Platforms
According to Verified Market Reports, the AI SOC market was valued at USD 25.5 billion in 2024 and is expected to reach USD 90.0 billion by 2033, growing at a CAGR of 15.5% from 2026 to 2033. This growth reflects rising demand for automated security operations as threat volumes and complexity increase.
Source: Verified Market Reports
AI SOC automation platforms combine SIEM, XDR, and SOAR with machine learning and agentic AI to automate threat triage and response. Microsoft Sentinel is a leading example, offering a cloud-native, AI-ready SIEM that uses automated rules and playbooks to standardize investigations and accelerate remediation.
Newer vendors such as Radiant Security are taking this further by designing adaptive platforms that can automatically handle most threats, repositioning analysts as overseers of AI-driven workflows.
Partnerships are speeding adoption by embedding AI SOC automation into managed services. A notable example is DXC Technology’s partnership with 7AI, which pairs DXC’s MSSP and integration expertise with 7AI’s autonomous detection and response engine. This model enables enterprises to access a largely automated SOC-as-a-service, reducing operational complexity while maximizing the value of their fast-growing AI investments.
What Is an AI SOC Automation Platform?
An AI SOC Automation Platform is an advanced security operations system designed to automate many of the tasks performed in a modern SOC. It combines artificial intelligence, machine learning, and automated orchestration to detect threats, investigate incidents, and respond in real time.
Unlike traditional security tools that depend heavily on analysts to interpret alerts and decide next steps, an AI SOC Automation Platform works alongside the security team as a force multiplier. It automates repetitive, time-consuming tasks while enabling analysts to focus on high-impact, complex threats that require human judgment.
Some of its core components are,
- AI-Driven Detection: Uses machine learning and behavioral analytics to identify suspicious activity and subtle anomalies that often bypass signature-based and rule-driven systems.
- Autonomous Investigation: Employs AI agents that replicate how human analysts think by gathering context, correlating events, validating risk, and determining whether an alert represents real malicious activity.
- Intelligent Response: Executes automated containment and remediation actions based on situational awareness, severity, and business impact, rather than relying on rigid, one-size-fits-all rules.
- Continuous Learning: Improves accuracy over time by learning from analyst feedback, incident outcomes, and evolving threat intelligence, making each response cycle smarter than the last.
How AI SOC Automation Differs from Traditional Security Tools?
| Security Tool | Primary Function | Key Limitation / Advantage | Simple Analogy |
| SIEM | Collects and correlates security logs | Requires manual investigation and response | Records everything, but needs someone to watch |
| SOAR | Automates response using predefined rules | Rigid playbooks that lack adaptability | A robot that only follows instructions |
| XDR | Correlates threats across multiple domains | Still depends on human decision-making | Puzzle pieces without an assembler |
| AI SOC Automation Platform | Detects, investigates, and responds autonomously | Learns, adapts, and acts with context | Expert analysts working nonstop |
Types of AI SOC Automation Platforms
AI SOC automation platforms generally fall into a few types based on how much responsibility they take from analysts. Some may assist with detection and alert prioritization; others may investigate incidents independently; and the most advanced may respond automatically using context from across the environment.
1. SOAR Platforms
SOAR tools automate incident response by orchestrating actions across security tools using predefined playbooks. They reduce manual effort by automatically containing threats, enriching alerts, and enforcing consistent response procedures at scale.
Example: Palo Alto Networks Cortex XSOAR.
2. AI-Driven Alert Triage & Noise Reduction
These platforms use machine learning to reduce alert fatigue by deduplicating, clustering, and prioritizing alerts. They help analysts focus on high-risk incidents by filtering out false positives and low-value events.
Example: Exabeam.
3. Autonomous SOC / AI SOC Analysts
Autonomous SOC platforms use generative AI to investigate alerts, correlate context, and make decisions similar to a Tier-1 analyst. They can close benign cases, document findings, and escalate only confirmed threats.
Example: Microsoft Copilot for Security.
4. AI-Enhanced SIEM Platforms
AI-powered SIEMs centralize log data and apply behavioral analytics to detect threats. By using UEBA and anomaly detection, they identify suspicious activity that traditional rule-based systems may miss.
Example: Microsoft Sentinel.
5. Threat Intelligence Automation Platforms
These platforms automate the ingestion and analysis of threat intelligence feeds, enriching alerts with external context. AI helps score indicators and prioritize threats based on relevance and confidence.
Example: Recorded Future.
6. AI-Powered Detection & Response
EDR and XDR platforms use AI to detect malicious behavior across endpoints, networks, and cloud environments. They enable rapid, often automated, threat containment through behavioral analysis.
Example: CrowdStrike Falcon.
7. Case Management & SOC Productivity AI
SOC productivity platforms use AI to streamline case handling by summarizing incidents, suggesting next steps, and generating reports. They improve analyst efficiency and support compliance and performance tracking.
Example: ServiceNow Security Operations (SecOps).
How Does an AI SOC Automation Platform Work?
An AI SOC automation platform continuously monitors security data and intelligently connects related events. It can analyze behavior in real time and may determine the severity of a threat without waiting for human input. It can then respond automatically while learning from each incident to improve future decisions.
Layer 1: The Perception Layer
This layer transforms raw security data into actionable insights.
Security data is ingested from dozens of sources, including SIEM logs, endpoint telemetry, cloud services, network devices, and identity platforms. As data arrives, it is processed in real time through parsing, tagging, and enrichment with threat intelligence.
A normalization engine converts all incoming data into a common format using standardized schemas such as OCSF. This ensures that events from different tools can be understood and correlated together.
Example flow:
A suspicious login from Russia appears in identity logs. At the same time, unusual PowerShell activity is detected on a server. Threat intelligence links the IP address to a known threat group. These signals are normalized and combined into a single potential credential compromise event.
Layer 2: The Reasoning Layer
This layer replaces manual analysis with artificial intelligence.
Instead of relying on one large model, the platform uses multiple specialized AI agents that work together, each with a clear responsibility.
- The Triage Agent evaluates alerts and determines urgency and credibility
- The Investigation Agent reconstructs the attack path and scope
- The Containment Agent executes defensive actions
- The Enrichment Agent gathers external and internal context
- The Orchestrator Agent coordinates the overall workflow
These agents do not rely on rigid rules. They pursue objectives such as containing ransomware or confirming data exfiltration. Each agent can use tools such as APIs, search queries, and analytical models. They share findings in a common workspace, similar to how human analysts collaborate.
Real-world scenario:
An alert fires, and the triage agent classifies it as high-risk phishing. The orchestrator assigns investigation tasks. The system identifies multiple affected users, quarantines malicious emails, updates blocklists with new indicators, and documents each action with a clear explanation for analyst review.
Layer 3: The Action Layer
This is where decisions turn into responses. The orchestration engine builds response workflows dynamically based on context. Low-risk actions are executed automatically, while high-impact actions require explicit human approval.
The platform can issue commands across multiple security tools simultaneously, enabling rapid, coordinated responses.
Human interaction remains central. Analysts can use natural language queries to explore activity, view visual attack timelines, and approve or reverse actions with full context.
How to Build an AI SOC Automation Platform?
To build an AI SOC automation platform, you should first unify security data into a single incident view that machines can reason over. You must then deploy agentic AI that can triage, investigate, and respond while explaining each decision clearly. We have successfully developed AI SOC automation platforms for diverse clients; here is how we approach this work.
1. SOC Architecture
We define AI agent roles for triage, investigation, and response with clear decision boundaries. Orchestration flows are designed to enable agents to collaborate and escalate as needed. We choose centralized or distributed agent models based on scale and risk requirements.
2. Security Data Fabric
We integrate SIEM, EDR, NDR, IAM, cloud, and SaaS telemetry into a unified data layer. Alerts, users, assets, and activities are normalized into consistent entities. This creates a shared incident and threat graph for AI-driven correlation.
3. AI Decision Layer
We implement specialized AI agents to handle alert triage, investigations, and response actions. Agents use goal-driven reasoning to adapt to new contexts. Decisions are continuously re-evaluated based on confidence and impact.
4. Explainability and Control
We build explainable AI pipelines that show why actions were taken. Real-time decision narratives help analysts trust automation. Audit logging is added to support compliance and forensic review.
5. Learning Loops
We capture analyst feedback from daily SOC operations. Models are retrained safely to improve accuracy and behavior over time. MLOps pipelines manage versioning and controlled deployment.
6. Human Oversight
We define approval thresholds for sensitive actions. Analysts can pause, resume, or override automation at any point. Rollback mechanisms ensure operational safety in high-risk scenarios.
Most Successful Business Models for AI SOC Automation Platform
AI-driven SOC automation platforms are monetized in several proven ways, shaped by how security teams buy, deploy, and measure value. Across the market, four business models consistently outperform others in adoption, revenue growth, and customer retention.
1. Consumption-Based SaaS Model
The most common and widely accepted model for cloud-native security platforms is usage-based pricing. Customers pay based on how much of the platform they actually consume, typically measured by data volume or asset count.
How It Works in Practice
Pricing is usually anchored to measurable units such as:
- Log data ingested per day (GB)
- Endpoints or identities protected
Microsoft Sentinel is a leading example. Its pricing is based on log ingestion volume, with publicly listed Pay-As-You-Go rates starting around $2.46 per GB for log analytics.
CrowdStrike Falcon follows a different consumption metric, charging on a per-endpoint, per-year basis. While exact enterprise pricing varies by contract, advanced endpoint and XDR offerings commonly fall in the $100 to $200+ per endpoint annually range.
Why This Model Works
For customers, the appeal is flexibility. They can start small, run pilots, and scale usage as their environment grows, all while keeping spend aligned with operational reality. Finance teams typically range from $100 to $200+ per endpoint annually, providing a predictable OpEx structure.
For vendors, this model naturally expands revenue as customers generate more data, add endpoints, or onboard new business units. Once integrated into daily SOC operations, platforms priced this way become difficult to remove, driving long-term recurring revenue.
2. Enterprise Tiered Subscription Model
In this model, the platform is sold through clearly defined tiers, often labeled Standard, Pro, and Enterprise, with each tier unlocking progressively more advanced capabilities.
How It Works in the Market
Base tiers typically provide core detection and alerting, while higher tiers introduce:
- Advanced AI-driven analytics
- Automated investigation and response
- Premium support and stricter SLAs
Splunk and Palo Alto Networks’ Cortex XSOAR illustrate this approach well. Splunk’s Enterprise Security offering bundles SIEM, analytics, and automation into a premium package.
For large organizations, list pricing for these enterprise-grade security suites can reach tens of thousands of dollars per month, with AI and SOAR functionality acting as major value drivers at the top tier.
3. AI Analyst Force Multiplier Model
This is a value-based pricing strategy that reframes the platform not as a tool, but as a digital analyst that absorbs human workload.
How It Works Conceptually
Rather than charging per log or endpoint, pricing is justified by labor reduction and productivity gains. Vendors position their platforms to automate a large share of Tier-1 and Tier-2 SOC tasks, including triage, investigation, and enrichment.
Companies like Prophet Security and Radiant Security exemplify this approach. While they do not publish price lists, their sales motion centers on ROI.
The math is compelling:
- A fully loaded SOC analyst in the U.S. typically costs $100,000 to $150,000+ per year
- If an AI platform automates 70–80% of Tier-1 work, a subscription priced at $50,000 to $80,000 annually can allow one analyst to manage several times the workload they previously handled
4. Integrated Ecosystem and Platform Model
In this model, AI SOC automation is not sold as a standalone offering. Instead, it is embedded as a premium capability within a broader security ecosystem, such as an XDR or full security suite.
How It Works at Scale
CrowdStrike and SentinelOne are the clearest examples. CrowdStrike’s Charlotte AI and SentinelOne’s Purple AI function as intelligent layers across their Falcon and Singularity platforms. Customers adopt AI features as part of a broader endpoint, identity, and threat intelligence stack.
CrowdStrike’s financial performance highlights the strength of this model. In fiscal year 2024, the company reported $3.06 billion in total revenue, with a significant share coming from customers adopting multiple Falcon modules, including managed and AI-driven services such as Falcon Complete.
How AI SOC Can Address the Ransomware Attacks that Grew by 34%?
Ransomware attacks on critical industries increased by 34 percent year over year in 2025, and that should concern you if your SOC still relies on manual response. An AI SOC can continuously monitor behavior patterns and may detect ransomware indicators earlier than any analyst, while automatically containing threats before encryption spreads. It can also intelligently learn from each incident, so your defenses gradually become stronger and more precise over time.
1. Proactive Threat Hunting & Exposure Control
Ransomware rarely starts with encryption. Attackers typically spend weeks inside an environment, mapping assets and quietly escalating privileges.
Behavior-Driven Exposure Detection
Instead of relying on signatures, an AI SOC continuously builds a behavioral baseline across users, endpoints, applications, and data flows. It flags subtle precursors to ransomware, such as abnormal file access by a legitimate account, unusual credential usage, or silent data staging to external cloud storage.
Contextual Threat Prediction
AI-driven intelligence engines do not just ingest threat feeds. By correlating emerging ransomware tactics with your organization’s asset inventory, identity posture, and known vulnerabilities, the SOC can surface which systems are most likely to be targeted next.
2. Initial Breach and Lateral Movement
Once attackers gain access, speed becomes the deciding factor.
Autonomous Alert Investigation
When suspicious activity appears, such as shadow copy deletion, credential dumping tools, or abnormal PowerShell execution, an autonomous investigation process begins immediately. The system enriches the signal with identity context, process lineage, endpoint telemetry, and network connections.
Attack Chain Correlation
Traditional SOC tools generate fragmented alerts. A phishing email, a risky login from an unfamiliar region, and a malicious script execution are no longer separate events. They are recognized as a single, unfolding ransomware campaign.
3. Coordinated, Automated Response
When ransomware starts encrypting files, delays are catastrophic.
Multi-Layer Containment in Seconds
Once policy thresholds are met, automated containment executes simultaneously across the security stack. Infected endpoints are isolated, malicious domains are blocked at the network layer, compromised identities are disabled, and high-value file shares are locked down.
Human-in-the-Loop for High-Risk Decisions
For actions with operational consequences such as shutting down a production system or an OT environment, the platform pauses and presents analysts with clear, evidence-backed recommendations.
4. Recovery That Strengthens Future Defense
An AI SOC does not stop working once the threat is contained.
Automated Forensics and Compliance Reporting
Post-incident evidence collection happens automatically. File changes, process execution paths, registry modifications, and timestamps are preserved and compiled into audit-ready reports.
Continuous Learning and Adaptation
Every incident becomes training data. Analyst feedback and response outcomes are fed back into detection and orchestration models. Over time, the system adapts faster than attackers can evolve.
Key Challenges to Make an AI SOC Automation Platform
Building an AI-powered SOC automation platform is not about clever models or shiny tooling. It is about surviving real-world conditions like noisy data, skeptical analysts, brittle integrations, and production systems that fail at the worst possible moment.
After designing and deploying these platforms for multiple security teams, we consistently see the same challenges appear. More importantly, we have learned what actually works to overcome them.
1. Data Noise and False Positives
The moment you connect an AI SOC platform to multiple data sources, noise levels increase dramatically. Logs, alerts, and detections accumulate faster than any model can process them. Traditional rules fire constantly, while early ML models, often trained on imbalanced or generic data, start flagging harmless behavior as malicious.
Instead of helping analysts, the system simply shifts alert fatigue from humans to automation.
How We Solve It
We do not start with AI-driven detection. We start by cleaning the signal.
- Layered Triage by Design: Simple, fast filters go first. Known-bad indicators, allowlists, and basic statistical baselines remove a large portion of noise before AI ever gets involved.
- Context-Based Scoring: The AI never evaluates a single log in isolation. Related signals, such as process execution, network behavior, and identity context, are grouped into an incident candidate with a single unified risk score. This alone can reduce alert volume by 60-80%.
- Feedback Loops That Actually Matter: Every confirmed false positive feeds back into the system. Thresholds, features, and weights are adjusted based on how your environment behaves rather than a generic dataset.
2. Automation vs. Human Trust
Security teams do not trust black boxes, and for good reason. Fully automated containment can create serious business risk, while requiring human approval for every minor step defeats the purpose of automation altogether.
The tension is not whether humans should be involved. It is where.
How We Solve It
We design for human-on-the-loop control rather than blind automation.
Risk-Banded Automation Policies
Actions are clearly separated by risk. Low-risk actions are fully automated, such as enrichment, tagging, and grouping. Medium risk actions require one-click approval, such as host isolation or IP blocking. High-risk actions are manual only, including account removal and organization-wide changes.
Explainability as a Requirement
Every automated action produces a short, plain-language incident narrative explaining what happened, why the system acted, and what evidence it used. Analysts can override any decision, and that override immediately influences future behavior.
Shadow Mode Before Go-Live
The platform runs in parallel for weeks before taking action. It makes decisions without enforcing them, allowing teams to build confidence and tune thresholds safely.
3. Scaling AI Reliably
Models that perform well on paper often fail under real-world pressure. They slow down during alert spikes, break when dependencies fail, and struggle to explain decisions when questioned.
Scaling AI is not just about accuracy. It is about resilience.
How We Solve It
We treat AI decision-making as a distributed, fault-tolerant system.
Specialized AI Agents
Instead of one monolithic brain, we deploy focused agents for triage, enrichment, and containment. Each runs independently so the system continues operating even if one component fails.
Graceful Degradation
Every workflow has a fallback. If a model times out, rules take over. If a data source is unavailable, the cached context is used. The system never stops working simply because intelligence is temporarily unavailable.
Performance Over Perfection
We evaluate models on latency and throughput, not just accuracy. In production, a decision made in 200 milliseconds at 95 percent accuracy is more valuable than one made in two seconds at 97 percent accuracy.
Tools & APIs to Make an AI SOC Automation Platform
Building an AI-driven SOC isn’t about stacking popular tools or chasing the latest frameworks. It’s about designing a system that can reason over data, retain context, and act with intent. The strongest platforms feel less like dashboards and more like investigative partners.
1. The Intelligence Layer
This is where detection moves beyond rules and signatures into real understanding.
- PyTorch and TensorFlow form the backbone. PyTorch dominates research and experimentation because it’s flexible and fast to iterate on, while TensorFlow earns its place in production environments where stability and deployment tooling matter.
- Transformer models (via Hugging Face) are essential for understanding language, not conversation. Fine-tuned models allow the platform to extract attacker behavior, tools, and intent from unstructured security text.
- Scikit-learn remains indispensable. Classic machine learning techniques often outperform deep learning on structured security data like authentication logs and network telemetry.
Key insight: Strong SOC platforms don’t rely on a single model type. They combine transformers for language, graph-based models for relationships, and traditional ML for behavioral anomalies.
2. The Memory Layer
Security isn’t about individual alerts; it’s about how events connect over time.
Elasticsearch or OpenSearch provides fast search and recall. This layer stores logs, alerts, and events so the platform can respond quickly to questions. OpenSearch offers tighter ML integration out of the box, while Elasticsearch benefits from a larger ecosystem of plugins and extensions.
Graph databases like Neo4j are where things change fundamentally. Attacks are relational by nature: users, devices, IPs, processes, credentials. Graphs allow the platform to trace attack paths, correlate weak signals, and surface connections that would never appear in flat tables.
Kafka and event streaming act as the nervous system. Telemetry flows continuously through the platform, enabling detections and responses to occur in near-real time. Just as importantly, streaming protects the system during spikes so data isn’t lost when attacks get noisy.
Key insight: Mature platforms treat the graph as the source of truth for entities and relationships. Logs feed the graph, but investigations query relationships—not raw events.
3. The Action Layer
Detection without response is just reporting.
| Integration Type | Examples | What It Provides |
| Endpoint Security | CrowdStrike, SentinelOne | Host telemetry and direct response actions (isolation, process kill) |
| Identity & Access | Okta, Azure AD | User login, privilege, and behavior context |
| Cloud & Container Security | AWS, Azure, GCP | Audit logs and visibility into cloud and container activity |
Key insight: Integrations must be two-way. Pulling data is only half the job; the platform must also consistently push actions back into tools through a common abstraction layer.
4. The Control Layer
This is what separates demos from production systems.
- Workflow engines like Airflow and Temporal handle coordination. Airflow excels at scheduled jobs, while Temporal supports long-running, stateful investigations.
- Kubernetes underpins scalability and resilience. AI agents can scale independently during alert surges and contract when demand drops.
- MLflow manages the model lifecycle. It tracks deployed models, performance metrics, and training data for auditability.
Top 5 AI SOC Automation Platforms in the USA
We spent time delving into the SOC automation space and carefully reviewed how modern platforms perform in real-world security environments. What stood out was how these solutions can intelligently triage alerts and autonomously investigate threats while still allowing analysts to stay in control.
1. ReliaQuest GreyMatte
ReliaQuest GreyMatter is a US-based AI-powered SOC platform that uses automation and agentic AI to detect, investigate, and respond to threats across hybrid environments. It focuses on reducing alert fatigue by correlating data from multiple security tools and automating response actions for enterprise SOC teams.
2. Microsoft Sentinel
Microsoft Sentinel is a cloud-native SIEM and SOAR platform enhanced with AI and machine learning to automate threat detection and response. Widely adopted in the USA, it integrates tightly with the Microsoft security ecosystem and uses automation playbooks to streamline SOC workflows at scale.
3. Torq (HyperSOC)
Torq (HyperSOC) is a no-code security automation and orchestration platform that enables SOCs to scale incident response. It focuses on fast, AI-assisted workflow execution to eliminate manual tasks and speed up security operations.
4. Dropzone AI
Dropzone AI is an AI-first SOC automation platform that acts as a virtual security analyst. It autonomously investigates alerts from SIEM and EDR tools, provides clear conclusions, and escalates only high-confidence threats, significantly reducing analyst workload.
5. Radiant Security
Radiant Security is an agentic AI SOC platform that automates alert triage, investigation, and response using autonomous decision-making. It focuses on eliminating false positives and accelerating response times, making it well-suited for modern, AI-driven SOC operations in the US market.
Conclusion
AI SOC automation platforms can reshape security operations in a very practical way, and they should feel less experimental and more engineered for scale. When autonomous reasoning operates within a unified context and produces explainable decisions, teams will operate faster and more securely with human oversight in the loop. If you choose the right architecture and partner, this platform will steadily turn security from a cost center into something that supports growth.
Looking to Develop an AI SOC Automation Platform?
IdeaUsher can help you design an AI-driven SOC automation platform that connects SIEM, SOAR, and telemetry at scale. We will pragmatically map use cases, build ML-assisted detection, and orchestrate response playbooks that run quickly and securely.
Our team, powered by 500,000+ hours of coding experience and led by ex-MAANG/FAANG developers, specializes in crafting intelligent, AI-driven SOC platforms that:
- Replace rigid playbooks with Agentic AI that dynamically investigates threats
- Unify siloed data into a context-aware intelligence fabric
- Build trust with Explainable AI that logs every decision
- Learn continuously with Human-on-the-Loop feedback systems
See our latest projects and start your AI SOC transformation with us today.
Work with Ex-MAANG developers to build next-gen apps schedule your consultation now
FAQs
A1: You can start by defining clear SOC workflows and threat models to automate first. The platform should gradually combine data ingestion, reasoning engines, and response logic with strong human review. If you build on modular architecture, the system will scale efficiently over time.
A2: The cost will depend on data sources, model complexity, and integration depth. You should expect a higher upfront investment, but it may clearly reduce long-term operational spend. With careful planning, the return can steadily justify the build.
A3: The platform continuously ingests security signals and reasons over them in near-real time. It can correlate alerts, explain decisions, and trigger responses in accordance with defined policies. Human analysts will usually supervise and intervene when risk thresholds are crossed.
A4: Development time can vary based on scope and maturity goals. A focused version may be delivered in a few months, while enterprise-scale systems will take longer. If priorities remain clear, progress should continue to be consistent.