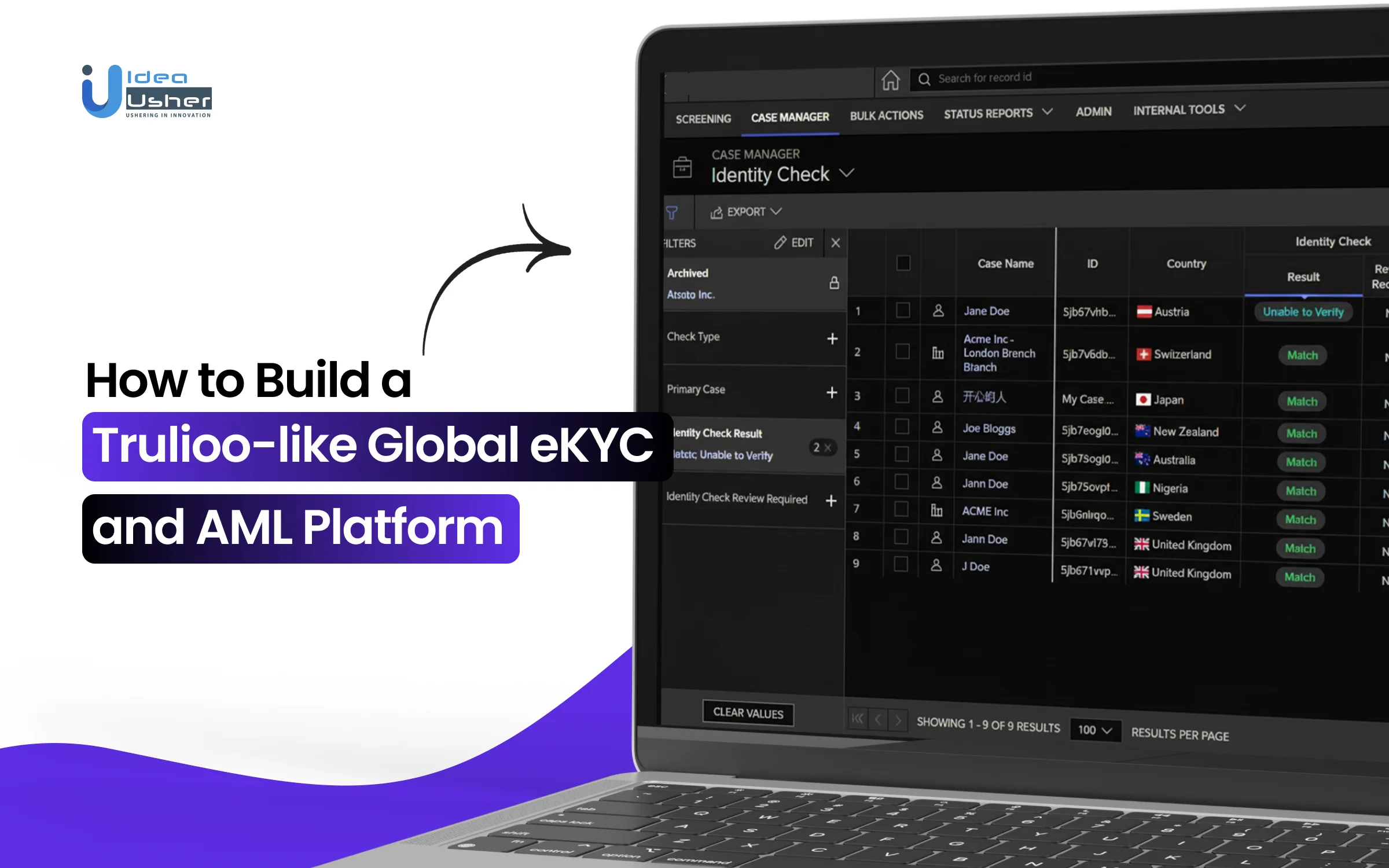
Trust is becoming the baseline of the digital world, and most businesses now meet users without ever seeing them face to face. That convenience now feels normal, but it also creates gaps where fraud and compliance failures can quietly grow. This is why many companies now rely on global eKYC and AML platforms like Trulioo that offer identity proofing, document validation, and sanctions screening.
These systems verify users in real time and still keep onboarding smooth enough to reduce drop-offs. Biometrics, liveness checks, and automated KYB must work together behind the scenes and adapt to regional rules.
Over the years, we’ve built several global verification ecosystems that use technologies like identity intelligence frameworks and fraud intelligence models. As IdeaUsher has this expertise, we’re sharing this blog to discuss the steps to build a global eKYC and AML platform like Trulioo. Let’s start!
Key Market Takeaways for Global eKYC and AML Platforms
According to MordorIntelligence, the KYC market is valued at USD 6.73 billion in 2025 and is forecast to reach USD 14.39 billion by 2030, advancing at a 16.42% CAGR. This expansion reflects surging demand for automated verification amid regulatory penalties, remote onboarding surges, and AI advancements reducing false positives by up to 90%. Global eKYC and AML platforms are surging in popularity as fintechs, banks, and non-financial sectors adopt cloud-native solutions for real-time compliance, driven by digital transaction booms and threats like deepfakes.
Source: MordorIntelligence
Jumio leads as a major example with its AI-powered KYX Platform, offering configurable workflows, risk scoring, and analytics for identity verification, eKYC, and AML screening tailored to sectors like finance and gaming.
Onfido provides another powerhouse solution, featuring biometric verification, document checks, perpetual KYC, and AML tools, including PEP, sanctions, and adverse media screening across 195 countries. Both platforms enable 94% automated decisions, slashing manual reviews and boosting onboarding efficiency.
A key partnership sees Complytek and Advapay collaborating to deliver scalable core banking with advanced AML compliance for fintechs, enhancing audit readiness and machine learning-driven transaction monitoring. These alliances highlight the shift toward integrated ecosystems that streamline global workflows and cut compliance costs.
What is the Trulioo Platform?
Trulioo is a global identity verification solution designed to help organizations verify both individuals and businesses through one unified API and contract. Instead of relying on multiple tools or vendors, Trulioo brings KYC, KYB, and AML capabilities together in one place. The platform supports verification in 195+ countries, tapping into hundreds of trusted data sources and thousands of recognized document formats to ensure broad and reliable coverage.
While the platform works behind the scenes to complete compliance checks, Trulioo focuses heavily on making the verification experience smooth, intuitive, and secure for end users.
Here are some of the standout features:
AI-Optimized Document Capture
Instead of requiring users to adjust angles or lighting manually, Trulioo’s document capture experience is guided by AI. The system automatically detects when the ID image is clear, well framed, and readable, helping reduce errors, resubmissions, and user frustration.
Biometric Selfie Verification
To confirm the person behind the identity document is genuinely who they claim to be, users take a selfie that’s analyzed using biometric technology. The system performs passive liveness detection (meaning no exaggerated head movements or prompts) and compares the selfie against the submitted ID. The feature supports 40+ languages and is built to operate quickly without compromising compliance or accuracy.
Recognition for Returning Users
If someone has been verified before, the platform can recognize the face from previous verification attempts. This allows frequent or returning users to move through the process faster while also helping businesses identify repeat fraud attempts.
Customizable Interface Through SDKs
Businesses can tailor the look and feel of the verification flow so it aligns with their brand. This includes localized instructions, on-screen coaching, and automatic document scan triggers to help guide users step-by-step.
Instant and Transparent Results
Once the verification checks are complete, results are displayed immediately in a clear dashboard format. Scores, reasoning, match strength, and even fuzzy-matching logic help reviewers understand outcomes without ambiguity.
How Does the Trulioo Platform Work?
The Trulioo platform works by taking your verification request and routing it through the best available identity sources using a decision engine that evaluates region, document type, and risk level. It then analyzes data, documents, and biometrics in a structured workflow that could adapt based on confidence scores and regulatory rules.
Core Architecture
Developers interact with one unified API endpoint. Behind that interface is a decision engine responsible for evaluating the request and choosing the best verification route.
When a verification request is submitted, the platform:
- Collects input data such as personal details, submitted images, and metadata
- Evaluates context, including user location, regulatory expectations, and identity method availability
- Routes the request to the most suitable identity sources using machine learning logic
- Normalizes results from multiple systems into a consistent structure
- Returns a clear verification result with scoring, indicators, and reasoning
What appears to be a single request and response may actually involve dozens or hundreds of micro-decisions happening within milliseconds.
Person Verification
Trulioo uses a step-up strategy for verifying individuals. The platform begins with the least intrusive method and escalates only if needed to maintain conversion and compliance.
1. Data Source Matching (Fastest Path)
In regions with strong digital identity coverage, the system checks official and commercial records such as:
- Credit bureaus
- Government databases
- Telecom and utility records (when permitted)
Example:
A user in Germany enters their details. Trulioo checks SCHUFA, government records, and telecom databases.
If confidence is high, verification completes in under three seconds with no further action required.
2. Document Authentication (Fallback or Enhancement)
If the first layer cannot confidently confirm identity, Trulioo automatically shifts to document analysis.
The uploaded ID is examined for:
- Authenticity using hologram detection, MRZ validation, and format checks
- Tampering such as generative edits, overlays, or pixel inconsistencies
- Structured data extraction using OCR and format-aware parsing
The platform supports thousands of document types across 195 countries and continuously updates to respond to new fraud patterns.
3. Biometric Verification and Liveness (Highest Assurance)
For high-risk scenarios or regulatory requirements, the biometric layer is activated.
This includes:
- Passive liveness detection without forced gestures
- Facial matching between the selfie and document photo
- Repeat fraud detection using stored biometric reference matching (Known Faces capability)
This step verifies that the person submitting the ID is the real holder and not a deepfake, impersonator, or synthetic identity.
Business Verification
Trulioo’s business verification capabilities extend beyond confirming a company’s legal status. The platform analyzes ownership and risk at multiple levels.
The workflow includes:
- Verification of business existence through registries and government data
- Automatic beneficial ownership discovery across jurisdictions
- Screening for sanctions, politically exposed person status, and adverse media
- Ongoing monitoring when regulations require continual oversight
What is the Business Model of the Trulioo Platform?
Trulioo operates as a global platform for digital identity verification. It enables organizations to verify individuals and businesses for KYC, KYB, and AML compliance. Through a single API, customers can access verification capabilities across 195 countries, supported by hundreds of trusted data sources and multilingual support.
How the Platform Makes Money
Trulioo uses a hybrid SaaS and usage-based pricing model. Customers typically pay a platform access or subscription fee and then additional charges based on the volume and category of verification activity. Pricing varies depending on factors such as:
- Verification type (individual, business, document, AML screening, etc.)
- Geographic region and regulatory requirements
- Depth or tier of data requested
- Monthly or annual onboarding volume
This model allows revenue to scale naturally alongside fast-growing industries, including fintech, crypto, e-commerce, and digital payments.
Marketplace Model
A core component is GlobalGateway, the marketplace that aggregates data from hundreds of public and commercial data partners. Trulioo generates revenue from organizations consuming verification services and, in some cases, from participating data providers.
This approach removes the operational and regulatory burden for customers who would otherwise need to negotiate and maintain direct relationships with each source.
Additional Revenue Streams
Beyond subscription and verification-based fees, Trulioo generates additional value through:
- Data-as-a-Service enrichments and advanced identity insights
- Professional services and compliance advisory support
- Custom enterprise integrations
Growth and Market Performance
Trulioo continues to experience strong traction across regulated digital sectors. Recent highlights include:
- Over 60% year-over-year revenue growth in the APAC region, driven by rising usage from fintech and digital marketplace clients
- Significant adoption of KYB verification services in the United States
- Expanded verification volume across payments, crypto platforms, and global digital marketplaces
Customers report measurable outcomes, including faster onboarding cycles, reduced fraud risk, and meaningful revenue gains through higher verification-match success rates.
Funding and Valuation
Trulioo has secured more than $400 million in venture and growth capital from institutional and strategic investors. Funding rounds progressed from early angel and seed financing to later large-scale growth rounds backed by global financial institutions and long-term technology investors.
The most recent top-tier investments support marketplace expansion and global scaling efforts, placing the company at an estimated valuation of approximately $1.8 billion.
Customer Base and Market Focus
The platform serves highly regulated and high-volume onboarding sectors such as:
- Digital banking and neobanking
- Domestic and cross-border payments
- Online marketplaces and gig-economy platforms
- Cryptocurrency and digital asset providers
Notable customers include Nium, EQ Bank, Airwallex, Metal Pay, and additional large-scale identity-sensitive platforms.
How to Develop a Trulioo-like Global eKYC & AML Platform?
To build a Trulioo-like global eKYC and AML platform, you’d first connect identity data providers across regions and normalize their outputs into one consistent schema that machines can verify. Then you’d add AI verification logic so the system can dynamically choose the right method based on risk and regulation.
We’ve created solutions like this before for different industries, and this is how we typically execute them.
Step 1: Global Data Layer
We begin by integrating identity sources such as government registries, credit bureaus, banking networks, and telecom datasets. A geo-aware routing engine determines the most appropriate provider for each region, and a consent management layer ensures privacy, lawful access, and fully traceable authorization.
Step 2: Normalized Identity Schema
Next, we design a unified identity schema that standardizes all provider outputs into a consistent format. This includes multilingual field support, country-specific address validation, and normalized JSON responses so downstream systems can consume identity data without adapting to regional differences.
Step 3: AI Verification Orchestration
We then build an AI-driven orchestration engine that selects verification methods based on accuracy, compliance rules, provider cost, and risk level. Cascading logic enables automated fallback to secondary checks when needed, ensuring reliability and cost efficiency without manual oversight.
Step 4: Biometric & Fraud Layer
At this stage, we integrate biometric verification, document authentication, and fraud detection models. Liveness detection, deepfake prevention, synthetic identity evaluation, and continuous scoring help prevent identity theft, impersonation, and emerging digital fraud attempts.
Step 5: Continuous Monitoring
For business compliance, we deploy continuous KYB and UBO monitoring with ownership graph mapping. Sanctions lists, PEP monitoring, and adverse media feeds are streamed into automated AML triggers to keep organizations compliant as regulatory or profile risk changes occur over time.
Step 6: Compliance Workflow Studio
Finally, we provide a no-code workflow builder that allows compliance teams to customize verification logic without engineering involvement. Audit trails, jurisdiction-based rule templates, and configurable decision paths make ongoing compliance updates faster and easier.
What is the Revenue Potential of a Global eKYC and AML Platform?
The identity verification and compliance space is expanding fast because regulation and digital onboarding are no longer optional. eKYC and AML tools are now treated as core infrastructure across banking, fintech, crypto and other regulated digital industries. As fraud rises and governments enforce stricter rules, businesses must adopt verification systems that can operate globally, scale efficiently, and support remote user onboarding.
Once integrated through API or workflow orchestration, these platforms benefit from:
- Long-term recurring revenue cycles
- High switching costs
- Compound transaction growth tied to customer volumes
- Regulatory pressure is creating non-discretionary demand
- Ongoing monitoring requirements extending the lifetime customer value
This combination creates infrastructure-grade economics, comparable to payments, cybersecurity, or credit bureau networks.
Growth Forces Fueling Expansion
| Driver | Numeric Impact |
| Regulatory enforcement increased across the G20 since 2020 | ~300% growth |
| Global digital banking penetration | 72% of financial interactions |
| Regulatory enforcement increased across G20 since 2020 | $2.2T underlying asset ecosystem |
| Projected cost of online fraud in 2024 | $48B |
| Verification demand growth in frontier economies | 200–400% YoY |
Additional macro factors:
- Increasing cross-border labor mobility
- High-risk industries are being forced into KYC frameworks
- Government adoption of digital identity and e-ID mandates
- Mergers between financial infrastructure and identity systems
A global compliance platform typically generates revenue across four monetization pillars. Each contributes differently to gross margin, scalability, and valuation multiple.
1. Identity Verification Transactions
This revenue stream scales with onboarding volume because each verification triggers a billable event. Pricing usually falls between $1.50 and $3.50, depending on the verification depth and regulatory standards. Costs may vary based on geography and the method used, whether it is biometric scanning, document validation, or device-level checks.
Scenario example:
- 1,000,000 verifications/month
- Unit economics: $2.50 average price
- Monthly revenue: $2,500,000
- Annualized: $30,000,000
Cost structure includes:
| Cost Component | Margin Impact |
| Data sources (government, MNO, credit bureaus) | High variance |
| Cloud compute and OCR/ML processing | Declines with scale |
| Fraud and decisioning analytics | High fixed value, low marginal cost |
At scale, transaction margins typically stabilize between 30 and 55 percent, depending on data sourcing agreements.
Real-World Benchmark: Sumsub processed 100M+ verifications in 2022, suggesting ~$200-300M in annual transaction revenue.
2. Subscription and Platform ARR
SaaS subscription revenue is valuable because it brings predictability and strong retention. Pricing often depends on how much compliance coverage a client needs and how many API calls they expect to run. It may also shift based on whether the platform supports multiple jurisdictions and the level of workflow automation required.
Portfolio example:
| Client Tier | Count | Annual Fee per Client | Total |
| Tier 1 (banks, regulated financial institutions) | 10 | $480,000 | $4,800,000 |
| Tier 2 (fintech, digital banks, large PSPs) | 50 | $180,000 | $9,000,000 |
| SMEs and SaaS-integrated platforms | 200 | $60,000 | $12,000,000 |
Annual Recurring Revenue Total: $25,800,000
Retention rates for enterprise buyers frequently exceed 90 percent, with contract terms averaging 2–4 years. Switching costs remain high due to regulatory audit trails.
Real-World Benchmark: Alloy’s pricing suggests similar enterprise ARR models with $25M+ ARR from subscription fees
3. Value-Added and Compliance Lifecycle Services
These modules provide the highest margin contribution due to low incremental cost.
Revenue examples:
| Service | Volume | Price | Annual Value |
| KYB / UBO legal entity checks | 100,000 | $100 avg | $10M |
| Continuous AML and sanctions monitoring | 500,000 profiles | $3.50/month | $21M annually |
| Manual review / case escalations | 50,000 | $20 | $1M |
| Compliance advisory | Variable | $300–$500/hr | $1M–$5M potential |
Estimated annual value: $32M
Gross margins often range 70–85 percent.
4. Data, Intelligence, and Risk Scoring Products
Once a platform has verified millions of identities, anonymized intelligence becomes a sellable asset particularly for:
- Banks
- Fraud analytics firms
- Regulators
- Risk engines and cyber defense systems
This category is projected to contribute 10–15 percent of total revenue by maturity with margins exceeding 90 percent due to negligible marginal delivery cost.
Market Dynamics and Competitive Structure
The eKYC and AML ecosystem is shifting from fragmented adoption to consolidation as regulatory regulation intensifies and enterprises standardize vendor reliance. Competition is increasingly shaped by accuracy performance, geographic compliance coverage, and platform extensibility rather than standalone feature capabilities.
Market consolidation is ongoing.
| Tier | Market Share Control |
| Top 5 global providers | ~45% |
| Next 10–15 regional or specialized platforms | ~30% |
| Long tail (100+ niche solutions) | ~25% |
Winning the space requires:
- High verification accuracy
- Multi-jurisdiction regulatory mapping
- Continuous onboarding and monitoring capabilities
- Integration into core financial workflows
- Strong customer lifetime value and CAC recovery within 12 months or less
Global eKYC Demand Surges as Financial Access Reaches 79 Percent
According to recent reports, 79 percent of adults worldwide now hold a financial account through a bank, mobile wallet, or digital payment service. That level of access signals a shift where identity verification technology could become the next foundation of global finance.
If billions are transacting digitally, then scalable eKYC and AML platforms will likely be the systems that keep the ecosystem compliant, secure, and truly interoperable.
Four Structural Demand Waves
1. Digital Banking and Neobanks
Digital-first financial institutions have opened over 300 million accounts in the past three years. Each account requires digitally verifiable trust layers such as:
- Identity verification
- Sanctions and PEP screening
- Continuous AML monitoring
- Global compliance reporting
Without automation, the cost and operational burden of manual verification become unsustainable.
2. Embedded Finance
Companies outside traditional financial services are now offering banking, lending, payroll, and insurance functions. This includes platforms such as Uber, Shopify, Grab, Mercado Libre, and Temu. Each participating company becomes a financial actor responsible for onboarding, monitoring, and securing identities.
As embedded finance adoption accelerates, identity verification becomes mandatory infrastructure rather than a niche capability.
3. Digital Assets and Crypto Integration
Traditional banks, payment processors, and asset managers are now integrating crypto products. This transition introduces requirements such as chain-of-custody tracking, transaction provenance, virtual asset identity verification, and blockchain compliance analytics. Regulatory bodies worldwide now expect the same AML standards applied to fiat markets to apply in digital asset markets.
4. Cross-Border E-Commerce and Payments
Global e-commerce is expanding at 25 percent year over year, accelerating demand for:
- Know Your Business onboarding
- Cross-border identity verification
- Fraud-resistant checkout
- Real-time sanctions compliance
International commerce now depends on digital trust more than physical presence.
The Structural Verification Gap
Even with rising access, current systems are not equipped to handle the volume, diversity, and regulatory complexity.
| Breakdown Point | Current Reality | Strategic Need |
| Documentation | Over 4,000 global ID formats | A unified global identity data standard |
| Regulation | More than 200 AML regimes | Adaptive rule engines with continuous updates |
| User Experience | 60-second abandonment threshold | Instant, low-friction verification |
| Demographics | Low formal documentation in emerging markets | Biometrics, alternative data, and digital ID |
Traditional verification tools were designed for national banking, not global interoperability. The result is costly inefficiency:
- Up to 20 percent of valid applicants fail onboarding
- Each manual review costs $15 to $25
- Financial institutions face $42 billion in fraud losses annually
- Regulatory bodies issued more than $10 billion in AML violations last year
Trust gaps are now measurable financial risks.
Why the Market Is Ripe
A combination of technology readiness and regulatory alignment is reshaping the verification landscape.
Technology tailwinds:
- Machine learning and computer vision now achieve 99.5 percent accuracy
- 5G enables global real-time verification
- Cloud orchestration reduces verification cost to less than one cent
- More than 3,000 verified open banking APIs support third-party authentication
- Self-sovereign identity models are maturing
Policy and regulatory momentum:
- FATF guidance is followed by more than 200 jurisdictions
- Digital ID rollouts are underway in 160+ countries
- Continuous verification is replacing periodic review
- The Financial Action Task Force Travel Rule applies to transactions above $250
Regulation and technology are converging, creating a clear path to standardization.
Common Challenges for a Trulioo-like Global eKYC and AML Platform
After working with dozens of fintech startups, regional banks, digital lenders, and global marketplaces, one truth keeps repeating: everyone assumes identity verification is just about calling a few APIs. Then reality hits.
Building eKYC and AML at a global scale isn’t a feature. It is a moving target shaped by fragmented regulations, inconsistent data, and increasingly sophisticated fraud tactics. Over the years, we’ve seen the same stumbling blocks derail teams, so we built solutions that eliminate those failure points.
1. Wildly Inconsistent Global Identity Data
Identity data formats around the world rarely align in structure or semantics. A German record may use Vorname and Nachname. A Brazilian form may provide Primeiro Nome and Sobrenome. Japanese addresses may exclude postal codes entirely. Philippine IDs follow conventions that do not correlate to U.S. driver’s license formats.
Attempting to force all of this into a single rigid database model quickly creates silent breakage, compliance gaps, and false negatives.
How we solved it: Universal Identity Mapping
Instead of forcing global data into one fixed schema, we developed a process that:
- Detects the country and document type automatically
- Applies rules tailored to each jurisdiction
- Normalizes everything into a universal JSON model
- Stores both normalized and raw formats for transparency and auditability
Outcome: A single predictable response format regardless of where the user is located, without sacrificing regulatory traceability or original record fidelity.
2. Country by Country Regulatory Chaos
Regulations shift based on geography and license type, so what works in one region might fail in another. FinCEN demands specific crypto reporting, the FCA enforces stricter controls for e-money use, and MAS pushes enhanced screening for high-risk and PEP checks.
Teams often believe a static playbook will scale, but gaps usually surface during audits or when entering a new market.
How we solved it: A Jurisdiction Aware Workflow Engine
Our system enables compliance teams to adjust requirements without engineering involvement. It includes:
- A no-code visual rules builder
- Automatic enforcement of requirements based on jurisdiction and license class
- Real-time regulatory updates through monitored integrations
- Fully tracked and immutable decision histories
2. Fraud Is Becoming More Sophisticated
Fraud attempts now involve deepfake onboarding, synthetic identities built with fragments of real data, bot-driven multi-platform attacks, and identity manipulation at scale. Systems that rely on only one method of verification allow high-risk users to slip through.
How we solved it: Multi-layer Fraud Fusion
Instead of running checks independently, the platform correlates signals across:
- Document analysis with tampering and forgery detection
- Biometrics using 3D liveness and injection-attack defense
- Behavior and device intelligence, including velocity and pattern analytics
- Shared intelligence that identifies repeated or coordinated fraud attempts
4. KYB and Beneficial Ownership
Corporate structures are often layered and intentionally complex. A company may be incorporated in Delaware, owned by a Luxembourg holding entity, operating through a Singapore subsidiary, and represented by nominee directors in Hong Kong.
Finding the true Ultimate Beneficial Owner is often an investigative process rather than a single query.
How we solved it: Graph-Based Ownership Intelligence
The platform uses:
- A Neo4j graph model to represent legal and ownership relationships
- Automated registry retrieval across more than 100 jurisdictions
- AI extraction from official filings and scanned documentation
- Ongoing monitoring to detect ownership or directorship changes.
Tools & APIs for a Trulioo-like Global eKYC and AML Platform
Building a global identity verification platform is not just a coding exercise. It requires solving complex compliance, data trust, and real-time orchestration challenges across many legal jurisdictions. A platform operating at Trulioo-scale needs an engineered stack built for security, performance, reliability, and regulatory flexibility.
Below is a practical breakdown of the required system components.
1. Backend, Architecture, and Communication
Core Backend Languages
Different services may require different technologies depending on workflow and performance demands:
- Go for low-latency fraud scoring, biometric match pipelines, and high-performance workloads
- Java (Spring Boot) for compliance engines, rule-based processing, and long-term maintainability
- Python (FastAPI or Django) for machine learning services and experimentation
- Node.js for public API gateway layers and rapid user-facing iteration
Architecture Model
A microservices architecture is essential. Identity verification involves independent processes such as OCR, sanctions screening, biometric validation and fraud scoring. Each must scale independently and evolve without platform-wide deployments.
Message and Event Layer
Verification flows work best in an asynchronous, event-driven environment:
- Apache Kafka
- RabbitMQ
- AWS EventBridge
Example processing chain:
User submits document -> OCR service triggered -> registry lookup -> AML check -> decision engine.
2. Identity and Verification Data Layer
A global identity product must integrate multiple identity registry types and verification pathways.
Data Source Integrations
Government ID systems such as Aadhaar, eIDAS, DigiD and MyInfo SG provide verified identity data directly from national registries. Credit bureaus like Equifax, Experian and TransUnion add identity scoring in supported regions. Where these are unavailable, telecom and utility records offer alternative verification signals such as phone ownership or residential proof.
Document Authentication Components
Identity documents can be captured and validated using SDKs like Onfido or Jumio. OCR tools such as ABBYY, Google Vision or PyTesseract extract text from IDs and supporting documents. PDF and XML parsing enables the platform to read business filings, statements and regulatory paperwork.
Biometrics and Liveness
Face recognition engines like AWS Rekognition, Azure Face API or DeepFace match the user to their document photo. Liveness detection from providers such as FaceTec or IDmelon prevents spoofing and deepfake attempts. Optional voice biometrics can add an additional verification layer for call-based workflows.
3. Data Infrastructure and Machine Learning
Database Strategy
A single database type will not handle every data shape or regulatory need. Typical storage layers include:
| Type | Purpose | Example |
| Relational | Transaction history, audit logs, verification status | PostgreSQL |
| NoSQL | OCR payloads, metadata, session logs | MongoDB or DynamoDB |
| Graph | UBO mapping, AML network clustering | Neo4j or Amazon Neptune |
ML Lifecycle and Infrastructure
- Data stack: Pandas, NumPy and scikit-learn
- Deep learning: TensorFlow or PyTorch
- Model lifecycle: MLflow or Kubeflow
- Feature store: Feast or Tecton
Models typically cover document forgery detection, anomaly scoring, sanctions matching, similarity matching (BERT or Levenshtein), behavioral analysis, and risk prediction.
4. Security, Privacy, and Regulatory Compliance
Security is mandatory and must be part of the design from day one.
Data Protection
TLS 1.3 protects data in transit, and AES-256-GCM secures it at rest. Tokenization and field-level controls limit exposure of sensitive fields. HSMs like AWS CloudHSM or Azure HSM manage cryptographic keys in a secure, isolated environment.
Platform Security Controls
Zero-trust networking ensures every request is verified. mTLS secures service-to-service communication. API gateways such as Kong or Apigee provide throttling, authentication, and abuse protection. Secrets are stored and managed securely using Vault or AWS Secrets Manager.
Compliance and Reporting
Immutable audit logs ensure records cannot be altered. Consent platforms like OneTrust help manage privacy and user rights. Automated reporting supports SAR, CTR, and FATF obligations without manual effort.
5. Client SDKs, Device Capture, and Frontend Layer
Mobile verification should feel fast and effortless while still being secure. Cross-platform frameworks like React Native or Flutter help unify the experience, and native Kotlin or Swift SDKs improve camera capture and face matching.
A browser flow can work too when supported by Web Components or React, along with direct cloud uploads, WebAssembly checks, and basic document cleanup like auto crop and MRZ reading.
Workflows, Automation, and Observability
Workflow Coordination
- Temporal or Cadence for complex verification flows, human review steps and retry orchestration
- Prefect or Apache Airflow for scheduled compliance jobs such as sanctions list updates
Monitoring and System Observability
- Jaeger or Zipkin for distributed tracing
- Prometheus with Grafana visualization for performance metrics
- ELK stack for log aggregation and auditable access by compliance teams
Conclusion
Global eKYC and AML systems are no longer optional, they are core infrastructure, because the organizations that control identity verification also control compliance outcomes, fraud defense, and even how fast they can onboard customers. Trulioo already proved the model scales, and IdeaUsher pushes it further by letting enterprises build and customize their own verification ecosystems instead of relying on rigid vendor limitations, so they can adapt faster, reduce risk, and unlock new revenue powered by trusted digital identity.
Looking to Develop a Trulioo-like Global eKYC and AML Platform?
IdeaUsher could help you build a Trulioo-style global eKYC and AML platform by designing secure identity verification workflows, integrating advanced AI-powered fraud detection, and setting up compliant data standards with global regulators.
With over 500,000 hours of coding experience and a team led by ex-MAANG/FAANG developers, we engineer secure, scalable, and intelligent identity verification platforms, just like Trulioo, designed to:
- Orchestrate 400+ global data sources into one seamless API
- Auto-adapt workflows across 195+ countries with no-code logic
- Detect fraud in real-time using biometrics & AI-powered monitoring
- Simplify KYB/UBO verification with continuous risk intelligence
Work with Ex-MAANG developers to build next-gen apps schedule your consultation now
FAQs
A1: Building something similar usually happens in phases. An MVP with basic identity checks, document OCR, and a simple compliance workflow might take three to six months if the team already understands the tech. Scaling it into a global, enterprise level platform with fraud scoring, uptime guarantees, and large integration coverage could take one to two years because regulations, infrastructure, and data networks evolve.
A2: Yes, and many companies eventually do it once the system becomes stable and audit ready. Monetization often happens through SaaS access or through per verification billing tied to usage volume. Some teams also license KYB and AML data access separately, especially when they integrate multiple international registries.
A3: Fintech and crypto gain the most because they onboard high risk users across multiple regions and must meet strict regulations. Payments, forex, and online marketplaces also benefit since automated compliance reduces manual review work and speeds up onboarding. Any industry moving regulated financial value eventually needs a scalable verification workflow.
A4: They can be highly secure when they follow zero trust principles, encrypted storage, and strict access controls. Most teams add continuous audit logs, hardware backed key storage, and isolated compute so sensitive data stays contained. With proper patching and monitoring a self-hosted system may offer more control than a third party provider since the organisation manages the entire risk surface.