Today, fraud networks are evolving faster than traditional verification systems, and compliance tools are struggling to keep pace. Long manual checks are slowing down onboarding, and users rarely tolerate delays. That’s why the popularity of biometric identity verification systems like Jumio is increasing rapidly.
With AI-powered facial recognition, liveness detection, and hardware-level signals, platforms can verify users almost instantly. Automated document scanning and global eKYC flows are helping platforms stay compliant without incurring significant operational overhead.
Over the years, we’ve built multiple biometric identity and compliance-driven platforms powered by AI-driven computer vision and decentralized digital identity frameworks. Using that expertise, we’re sharing this blog to walk you through the process of building a biometric identity verification system similar to Jumio. Let’s begin.
Key Market Takeaways for Biometric Identity Verification Systems
According to FortuneBusinessInsights, the demand for biometric identity verification has surged as organizations look for stronger ways to confirm who’s really behind a digital interaction. The global market was worth about $33 billion in 2023, and forecasts suggest it could climb to more than $113 billion by 2032, showing how quickly the technology is becoming standard infrastructure. Much of that momentum is coming from the Asia-Pacific region, where large-scale digital identity programs and mobile-first services already account for more than half of global revenue.
Source: FortuneBusinessInsights
The shift isn’t theoretical; millions of people interact with these systems every day. ID.me, for example, now supports over 100 million verified users, helping government agencies and major brands authenticate individuals using face recognition and secure document checks.
Another platform, iDenfy, blends facial matching, liveness detection, and automated ID scanning so banks, fintechs, and online marketplaces can meet regulatory checks without slowing down customer onboarding.
Partnerships are also shaping the market by making biometric verification easier to integrate into existing identity frameworks. One recent example is the collaboration between Incode and Descope, which enables developers to add biometric checks directly into login, sign-up, and risk-based step-up authentication flows.
What is the Jumio Platform?
Jumio is a complete identity verification and compliance platform designed to help organizations verify individuals, detect fraud, and meet global regulatory requirements. The system combines biometric authentication, machine learning, document analysis, and AML screening into a single workflow. Businesses use it to onboard customers, assess risk in real time, and monitor identity activity throughout the customer lifecycle.
A key component of the platform is the Jumio Identity Graph, a fraud-intelligence system trained on tens of millions of identity records. It allows the platform to recognize suspicious behavior patterns, repeated fraud attempts, and identity mismatches.
Jumio is designed to streamline identity verification while minimizing friction. Some core capabilities include:
1. Document Capture and Verification
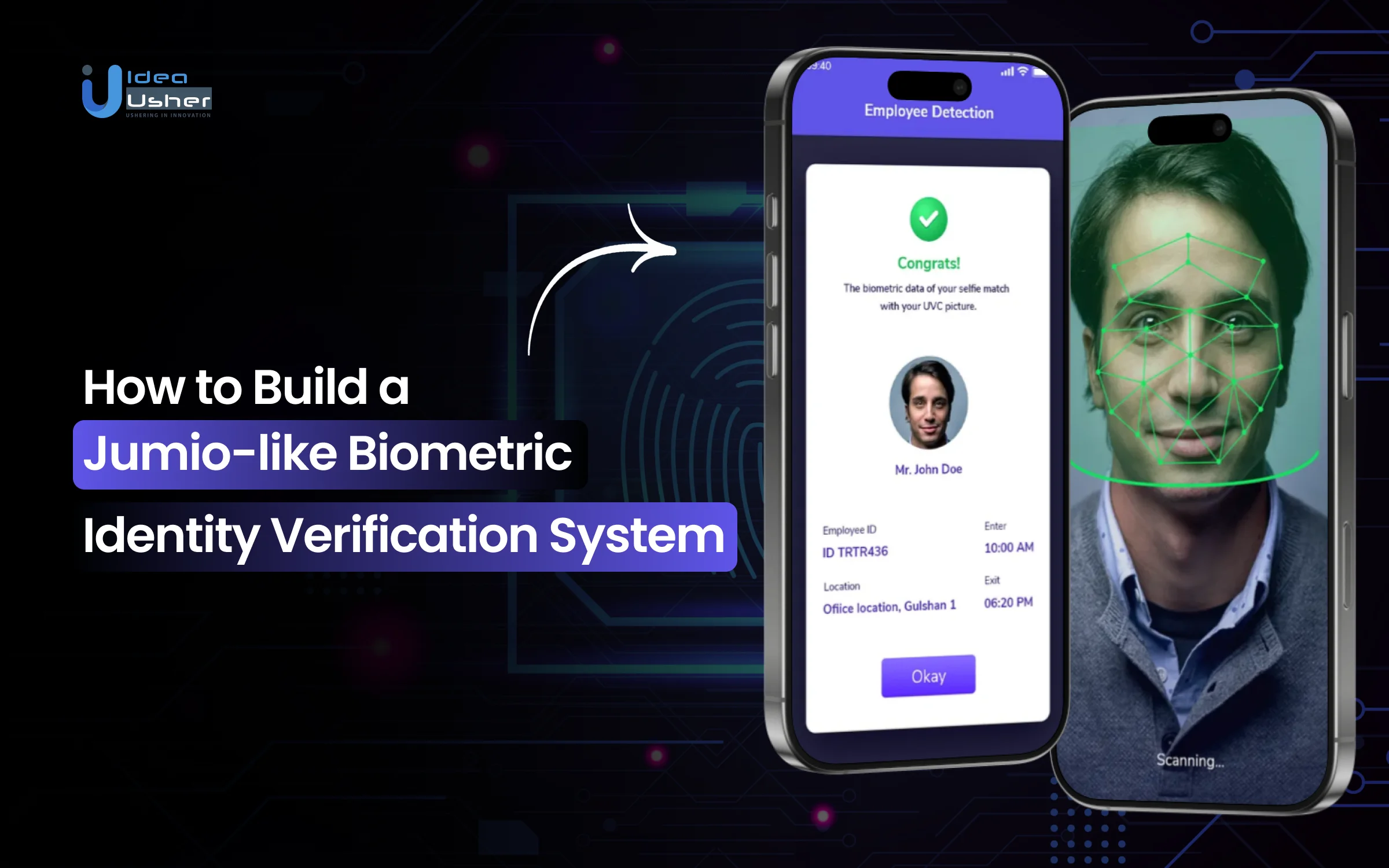
Users can submit identity documents such as passports or driver’s licenses using a smartphone camera or webcam. The system automatically checks document security details, including holographic elements, fonts, layout consistency, and signs of manipulation or tampering.
2. Biometric Verification and Liveness Checks
A selfie is used to confirm that the person submitting the ID is the same individual pictured on the document. Jumio applies liveness detection to prevent spoofing, deepfake attacks, masks, and static image submission. Additional signals, such as age estimation and detection of multiple faces, contribute to fraud scoring.
3. Guided Retakes and Error-Proofing
If an image is blurry, poorly lit, or partially cropped, users receive feedback and can retake the photo instead of abandoning the process. This reduces friction and increases conversion rates, especially in mobile onboarding flows.
4. Fast Re-Verification with Selfie.DONE
Returning or previously verified users can authenticate with a selfie rather than repeating the full document scan process. The identity match is handled through the Identity Graph and stored reference data, helping repeat customers move through the process quickly.
5. Active Liveness Prompts
In higher-risk scenarios, the platform may require dynamic user actions such as head movement or blinking to confirm real-time presence and prevent synthetic or deepfake impersonation.
6. QR Code Capture
Some identity documents can be verified by scanning embedded QR codes, providing instant validation and reducing manual review. This method removes the need to analyze complex document layouts or security features, since the encoded data can be checked directly against trusted sources.
7. Cross-Device Support
Users can begin the process on one device and complete authentication on another. For example, someone may start on a desktop computer, then complete biometric verification on a mobile phone for better camera performance.
How Does the Jumio Platform Work?
The Jumio platform captures a user’s ID and biometric data through adaptive SDKs and device-aware prompts. It processes that data with AI and liveness analysis so it can detect manipulation, verify documents, and match the real person to the credential. Then the system evaluates risk signals using its identity intelligence network and returns an approval or challenge decision in real time.
Layer 1: User Experience and Capture
Everything starts with the interaction between the user and the verification flow. Jumio’s mobile and web SDKs adapt to the user’s device and environment to make the process quicker and reduce friction.
Key elements include:
Device-aware guidance
The system adjusts camera instructions and prompts depending on whether the user is on a mobile device, desktop webcam, or lower-resolution hardware.
Adaptive workflows
If early signals suggest increased risk, such as VPN usage, mismatched region, or untrusted device, the platform can escalate to additional verification steps without forcing the user to restart.
Real-time capture validation
If an ID photo has glare, the selfie is cropped incorrectly, or the image is out of focus, the user is prompted to correct it before the submission goes forward.
Advanced capture capabilities
When supported, NFC chips inside passports or national IDs are scanned for encrypted identity data. In some flows, the system captures short video clips rather than static photos to help analyze natural movement for liveness checks.
Layer 2: AI Analysis and Identity Extraction
Once data is submitted, a deeper analysis pipeline begins. This includes document analysis, text extraction, biometric matching, and environmental risk signals.
Document Intelligence
- The system first identifies the type of document and its issuing country, then routes it to the correct validation model.
- Security elements such as holograms, fonts, and layout formatting are compared against reference templates.
- OCR goes beyond reading text. It understands structure and meaning, distinguishing expiration dates, birth dates, and other relevant fields even across different writing systems and formats.
- For digital IDs and chip-enabled documents, the platform verifies digital signatures and cryptographic security features.
Biometric Matching and Liveness
- Jumio checks whether the face in the selfie belongs to a live person and not a photo or deepfake.
- Liveness checks may be passive or active depending on risk. Passive checks look for natural motion and texture signals. If needed, the platform can require actions like blinking or turning the head.
- A 3D facial map is generated to make matching more resilient to lighting, camera differences, or age variation between the ID photo and real-time capture.
Risk Signal Aggregation
At the same time, the system analyzes technical and behavioral signals such as:
- IP reputation and geolocation
- VPN or proxy usage
- Device fingerprint and system integrity
- Unusual retry, upload, or input patterns
These signals feed the next layer of evaluation.
Layer 3: Identity Intelligence and Decisioning
This layer is powered by the Jumio Identity Graph, a privacy-preserving network of hashed identity signals derived from millions of past verification events.
Instead of storing sensitive information in plain text, the system converts identity data into secure hashed tokens. These tokens become nodes in a graph database that reveal patterns such as:
- Repeat attempts using the same identity across unrelated organizations
- Synthetic identity construction using partial real data
- Coordinated fraud attacks across multiple accounts
As verification signals are processed, the platform produces a composite risk score that reflects the integrity of the document, the biometric match, the environmental context, and identity graph insights.
Decision and Orchestration
Based on the combined score and the rules defined by each business, outcomes may include:
- Immediate approval
- Step-up authentication, such as video verification
- Terminal rejection with fraud flagging
- Escalation to a manual review queue
The platform continues learning from reviewer decisions and evolving attack patterns. This feedback loop helps the system strengthen accuracy and reduce false positives over time.
What is the Business Model of the Jumio Platform?
Jumio’s customer base is primarily enterprise-level organizations in finance, online gaming, payments, travel, and telecommunications, where user trust, fraud prevention, and regulatory compliance are critical to onboarding.
Platform & Delivery
The company delivers its technology through a cloud-based software platform that customers integrate via API. Jumio positions this offering as “Trusted Identity as a Service,” meaning customers outsource identity verification workflows rather than building them internally.
The platform’s core value focuses on:
- Faster and secure onboarding
- Meeting and maintaining compliance standards (KYC, AML, PSD2, etc.)
- Fraud detection through biometric matching, liveness testing, and its expanding Identity Graph of verified identities
Revenue Streams
Jumio generates revenue through a mix of SaaS licensing and usage-based pricing:
- Subscription Licensing: Customers pay recurring fees for platform access, system updates, support, and continuous compliance assurance.
- Transaction-Based Pricing: Organizations are charged per identity check. Pricing varies based on verification volume, complexity, and security levels.
- Premium Feature Tiers: Advanced biometric checks, upgraded liveness features, and enhanced fraud prevention tools are priced as add-ons.
- AML and Compliance Products: Following the acquisitions of Beam Solutions and 4Stop, Jumio expanded into transaction monitoring and data orchestration. These services now support tens of millions of AML events each month.
Market Performance and Growth Indicators
Jumio has demonstrated strong commercial growth. The company surpassed $200 million in identity proofing bookings during a recent quarter, making it one of the first companies in the category to reach that scale.
- Revenue grew at triple-digit rates in 2021, driven by AML offerings and regional growth in APAC and LATAM. Customers using the platform have reported reductions in fraud of up to 60 percent.
- Current market estimates place annual revenue at roughly $260 million or more, with an approximate 2–3 percent share of a global identity verification market valued at around $15 billion and forecasted to grow substantially over the next decade.
Funding and Strategic Expansion
Jumio has raised over $205 million since its founding. Early rounds included seed and Series A contributions from fintech-focused investors, including Eduardo Saverin, followed by venture funding in 2016 to support expansion. In 2021, the company secured $150 million from Great Hill Partners, representing one of the largest private equity investments recorded in the digital identity sector.
Acquisitions such as Beam Solutions in 2020 and 4Stop in 2021 expanded Jumio’s AML analytics and orchestration capabilities. Partnerships, including the 2024 alliance with LatticeFlow, have strengthened the accuracy and reliability of Jumio’s AI-based verification systems.
How to Build a Jumio-like Biometric Identity Verification System?
To build a Jumio-like biometric verification system, you need a strong pipeline that captures and analyzes identity documents and face data in real time. The platform should use liveness detection and machine learning to verify that the user is a real person and that the document has not been tampered with. We’ve done this at scale for different markets, and this is the method we trust.
1. Biometric & Document Capture
We begin by integrating a high-fidelity camera SDK and optimizing capture quality using multi-frame processing, motion correction, and adaptive lighting. The experience guides users through capturing facial biometrics and identity documents while maintaining consistent verification standards.
2. Liveness & Anti-Spoofing
We implement passive liveness AI to confirm a real human is present without requiring active gestures. Additional layers, such as active illumination detection and SDK-level spoof prevention, protect against replay attacks, masks, printed photos, and device injection attempts.
3. Document Intelligence
We create a document intelligence layer capable of supporting passports, national IDs, and licenses globally. OCR, layout detection, forgery analysis, and optional NFC eID chip reading ensure authenticity checks and accurate data extraction across multiple document types and regions.
4. Fraud Intelligence Layer
After verification, identity signals are connected to a fraud intelligence model. Using tokenized biometrics and a graph database, the system identifies repeated attempts, synthetic identities, device-linked fraud, and emerging risk patterns across participating platforms.
5. Secure Biometric Vault
A secure identity vault is deployed to store biometric templates. This includes biometric hashing, hardware-backed encryption, access limitation, retention governance, and auditable logs to ensure privacy compliance and long-term trust.
6. AI Risk Decisioning
We finalize the system by implementing a decision engine that merges biometric confidence scores, document authenticity, behavioral metadata, and risk signals. Low-risk users pass instantly, while higher-risk attempts trigger enhanced KYC steps, AML screening, or manual review.
Most Popular Business Models for Biometric Identity Verification Systems
Biometric identity verification platforms usually rely on three main business models, and each one serves a different operational need. Some charge per verification so cost scales with usage, others use predictable annual licensing with feature tiers, and a growing group uses revenue sharing, where pricing aligns with performance and fraud reduction outcomes
1. Transaction-Based Model
The transaction-based model charges clients on a per verification basis, typically ranging from $0.50 to $5.00 depending on verification complexity, biometric modality (such as face, fingerprint, or liveness detection), compliance requirements, and verification volume.
This model is the most common among API-first platforms serving high-growth digital sectors, including fintech, crypto, gig-economy platforms, and e-commerce.
Market Dynamics and Real-World Performance
Jumio, one of the leading providers, processes more than 1 million identity checks daily.
Their pricing model demonstrates clear volume economics:
| Volume Tier | Price Per Verification |
| 1,000–10,000/month | $3.50–$4.50 |
| 10,001–100,000/month | $2.50–$3.50 |
| 100,000+/month (Enterprise) | $0.75–$2.50 |
Incode follows a similar framework but positions itself as a premium platform, charging $4–$8 per verification. With enterprise clients including Telefonica, BBVA, and Citibanamex, the company reached a valuation of $1.25 billion, with estimated annual revenue exceeding $120 million.
Best-Fit Use Cases
This model is ideal for:
- Startups and small or medium businesses with flexible budgeting
- Industries with seasonal verification volume
- Companies experimenting with new geographic or regulatory markets
2. Platform or Enterprise Subscription Model
Enterprise clients and government agencies often prefer annual subscription or tiered licensing contracts, ranging from $15,000 to more than $500,000 per year. Pricing depends on compliance complexity, integration with legacy systems, verification volume guarantees, and advanced support obligations.
This model dominates in:
- Banking and financial institutions
- Healthcare and insurance
- Government identity and national ID programs
- Security and workforce identity governance
Industry Benchmarks and Revenue Impact
IDEMIA, one of the largest identity technology providers, generates more than $3 billion per year through identity solutions. Government identity programs frequently exceed $50 million per contract, while enterprise identity subscriptions often range from $250,000 to multiple millions.
3. Revenue Sharing or Partnership Model
The revenue sharing model reduces or eliminates upfront fees and instead ties pricing to business outcomes, such as:
- Verified transactions
- Approval conversions
- Reduction in fraud
- Successful financial onboarding
This model is rapidly gaining traction in lending, fintech, insurance, and crypto platforms where each verified identity directly enables revenue.
Real-World Adoption Example
Ping Identity has demonstrated measurable value using this structure. In one engagement, improved verification workflows increased loan approvals by 22%, and Ping received a percentage of the incremental revenue created. These agreements often include:
- 1%–5% of transaction value
- $0.10–$0.50 per verified user
- Shared value from quantified fraud reduction
Biometric Identity Verification Can Protect 13 Million Identity Theft Victims
Biometric identity verification can give people a stronger way to prove who they are in a digital environment, where stolen passwords and forged documents are common. According to reports, in 2019, more than 13 million adults in the U.S. were victims of identity fraud using non-biometric methods, underscoring how outdated traditional verification methods have become.
With biometrics, the system verifies the real user in real time, making it far harder for criminals to reuse stolen data or impersonate someone.
Why Traditional Identity Verification Keeps Failing
Think about the way identities are still verified today. A mix of login credentials, static personal data, and documents someone can copy or steal.
Where the breakdown happens:
- Passwords are everywhere, and they leak constantly. In 2019 alone, data breaches exposed more than 3.8 billion records.
- Security questions are predictable. Mother’s maiden name, first school, first pet. All of that can be found online or purchased.
- Document checks rely on surface-level validation. A high-quality fake ID can pass a visual scan or even fool inexperienced staff.
- Identity checks are reactive, not preventive. Systems often detect fraud after accounts are opened or money is moved.
For victims, recovery is not a quick phone call:
- More than 200 hours on average are spent resolving the damage
- More than $1,000 in out-of-pocket costs, even after reimbursements
- Roughly 65 percent report significant emotional distress
Traditional systems are clearly struggling to keep people safe.
How Biometrics Change the Landscape
Biometric identity verification isn’t just a better version of authentication. It represents a shift in how identity is proven and protected.
Instead of asking users to prove who they are, biometrics verify who they are physically and behaviorally.
1. Biological Identity Compared to Borrowed Information
A Social Security number can be stolen. A fingerprint cannot.
A fraudster might know your birthday or your address. They cannot replicate your heartbeat pattern, iris structure, vocal signature, or 3D facial geometry.
Example scenario:
Sarah’s healthcare provider experiences a data breach, and her Social Security number ends up for sale online. A criminal attempts to open credit cards in her name.
- A traditional system would likely approve the application.
- A biometric-enabled system would require a live facial scan that matches Sarah’s real stored biometric record. The impersonation attempt fails instantly.
2. A Defense Strategy That Works in Layers
Instead of relying on a single point of failure like a password, biometric systems combine multiple verification signals.
| Attack Type | Old System Result | Biometric Defense |
| Stolen ID cards | Accepted as proof | Requires live verification with liveness detection |
| Hacked personal data | Enables account takeover | Biometric match required to proceed |
| Synthetic identities | Often slip through | 3D mapping and behavioral profiles expose mismatches |
| Remote account takeover | Simple with stolen credentials | Device, biometric, and behavioral signals stop access |
This layered approach prevents the most common and costly attack paths.
3. Protection That Continues After Login
Biometrics do not stop working once an identity has been verified. They continue protecting the account.
Examples include:
- Step-up authentication for risky transactions
- Behavioral biometrics based on typing rhythm, swipe patterns, or device grip
- Contextual intelligence that evaluates device history and location patterns in real time
Biometric verification becomes a living identity profile that grows stronger and more accurate as it learns.
Challenges for a Jumio-like Biometric Identity Verification System
After deploying biometric verification systems across fintech, crypto, healthcare, and mobility sectors, one thing has become clear: choosing the right technology is only half the battle. The real challenge begins in production, where real fraud, scaling demands, and strict regulations test the system beyond what prototypes reveal. Below are the three biggest challenges teams face and how to overcome them
1. Deepfakes & AI-Driven Identity Fraud
Fraud tactics have evolved, and attackers now use deepfake video streams, realistic masks, and AI-generated voices instead of simple replays or printed photos.
These tools were once rare, yet now anyone can access them with little effort. One crypto exchange we supported was losing over $500K each month because basic liveness checks simply could not detect these advanced spoofing attempts.
Our Solution: Adaptive Multi-Layer Liveness Detection
We prevent these attacks using a layered model:
- Passive Liveness: Detects biological cues like subtle muscle movement and eye reflection patterns without user actions.
- Active Challenge-Response: Random prompts such as “turn slightly left” block pre-recorded or auto-generated footage.
- Active Illumination: The device screen projects randomized color patterns while analyzing true skin reflection. Masks, prints, and synthetic renderings cannot mimic natural subsurface scattering.
- Environmental Fingerprinting: Device sensor data helps detect video injection or hardware spoofing attempts.
2. Biometric Privacy and Compliance
Biometric data is permanent, and if it is compromised, there is no way to replace it. Regulations like GDPR, CCPA, and India’s DPDPA make the rules around storage, consent, and data residency very strict. Many teams pass security testing yet still fail compliance because they store raw images, skip deletion workflows or keep data outside required regions.
A European bank we assisted avoided a €2M GDPR fine after discovering its vendor stored full facial images with no compliant deletion process.
Our Solution: Privacy-By-Design Architecture
We address compliance and security simultaneously:
- On-Device Processing: Face templates are created locally. Raw images are never uploaded.
- Irreversible Hashing: Templates cannot be reconstructed into facial images.
- Region-Bound Storage: Data stays where law requires. EU stays in EU, India stays in India, and so on.
- Automated Compliance Systems: Built-in audit trails, deletion flows, consent logs, and privacy-safe analytics ensure continuous regulatory alignment.
3. Global Document Coverage vs Accuracy
Identity documents are not consistent across regions, and every country uses different fonts, holograms, security layers and chip formats. A system that works perfectly in one market might fail the moment it is exposed to a new document type. In one global rollout we reviewed more than 3200 variations across just 47 countries, which clearly shows how complex global coverage can become.
Our Solution: Tiered Global Verification Framework
We combine multiple verification techniques:
- Regional OCR Models: Trained specifically on local scripts like Arabic, Hindi, Cyrillic, and Latin variations.
- Security Feature Reference Libraries: Thousands of hologram signatures, microprint rules, and UV identifiers maintain accuracy.
- NFC Chip Verification: For e-passports and smart IDs, secure NFC data validation and PKI checks provide the highest certainty.
- Fallback Methods: When a chip fails or is unreadable, the system switches to visual checks, database cross-referencing, and region-specific manual review.
Tools & APIs for a Jumio-like Biometric Identity Verification System
Building a modern biometric identity verification system isn’t just about stitching together a few AI models. It requires a carefully orchestrated ecosystem of machine learning, security architecture, and scalable infrastructure. Below is a practical breakdown of the core building blocks that power enterprise-grade verification systems used in fintech, travel, healthcare, and government onboarding.
1. AI and Machine Learning Foundation
This is the core intelligence layer responsible for understanding faces, analyzing documents, and making verification decisions.
TensorFlow and PyTorch
PyTorch is great for fast experimentation, face matching prototypes, and testing new spoof-resistance methods. TensorFlow and TensorFlow Lite are better suited for stable, production deployments on mobile and edge devices. Many teams build models in PyTorch and deploy them with TensorFlow for a balance of speed and reliability.
OpenCV
OpenCV is used for key preprocessing tasks like face detection, alignment, denoising, and correcting document perspective. It also supports fast frame-by-frame image handling, making it essential for real-time selfie capture workflows.
ONNX Runtime
ONNX Runtime enables models trained in frameworks like PyTorch to run efficiently across different platforms, including mobile apps, browsers, and IoT hardware. It helps maintain consistent performance without retraining models for each environment.
2. Biometric Processing and Document Intelligence
Turning raw images into trustworthy identity signals requires specialized subsystems beyond typical machine learning.
Custom Face Recognition Models
Open-source face recognition tools work for prototypes, but enterprise-grade systems rely on custom-trained models built for high accuracy in 3D facial mapping, consistent landmark tracking across lighting and pose changes, cross-age and cross-ethnicity reliability, and strong resistance to spoofing attempts like deepfakes, printed photos, or masks.
Advanced OCR and Document Forensics
Basic OCR solutions like Tesseract are not sufficient for large-scale identity workflows. High-performance systems require models trained on diverse ID formats, capable of detecting holograms, watermarks, and UV elements, supporting multiple languages, including non-Latin scripts, and performing signature comparison when required.
Forgery Detection
Forgery detection models analyze subtle digital clues such as compression anomalies, lighting inconsistencies, deepfake or synthetic media artifacts, and evidence of screen recording or photo-of-photo captures, enabling reliable detection of manipulated or fraudulent content.
3. Backend Architecture and Infrastructure
A verification platform must handle unpredictable workloads, ranging from small onboarding pipelines to large-scale real-time global traffic.
Backend Stack
A typical backend stack uses Python frameworks like FastAPI or Flask for machine learning services, while Node.js handles live video streams, WebSockets, and real-time user interactions. These components are usually structured as microservices to allow independent scaling and modular development.
Containerization and Orchestration
Docker provides consistent and reproducible runtime environments, while Kubernetes manages automatic scaling, workload distribution, and reliability during traffic spikes. Service mesh tools like Istio or Linkerd add secure communication, observability, and policy control between microservices.
Cloud Platforms
Modern identity systems often operate across multiple regions and clouds to meet compliance, reliability, and latency requirements. Managed services like AWS SageMaker or Google Vertex AI support machine learning operations, while edge compute nodes enable faster on-device decision-making, and redundant deployments ensure business continuity.
4. Security, Governance, and Compliance
Since biometric and identity data are extremely sensitive, compliance is equally important as accuracy.
Security, Governance, and Compliance
Because biometric and identity data is highly sensitive, security controls and compliance standards are as critical as system accuracy. Strong governance ensures that collection, processing, storage, and access remain tightly controlled, auditable, and legally compliant.
Hardware Security Modules
HSMs protect and manage encryption keys in a secure, tamper-resistant environment, ensuring that biometric templates and other sensitive data are never exposed in raw or unencrypted form at any point in the system.
End-to-End Encryption
Stored data is typically encrypted using AES-256, while all communication is secured using TLS 1.3 or newer, with emerging research exploring homomorphic encryption to enable future privacy-preserving biometric matching.
5. Intelligence Layer, Risk Scoring and Fraud Networks
Modern verification does not end with a single decision. It improves with accumulated knowledge.
Graph Databases
Graph databases like Neo4j or Amazon Neptune help uncover coordinated fraud patterns by mapping relationships among identity clusters, device fingerprints, reused documents, and biometrics, as well as unusual behavioral signals that may indicate organized attacks.
Identity Resolution Engine
An identity resolution layer anonymizes user identifiers using irreversible hashing and links signals across repeated verification attempts, enabling continuity in risk evaluation without exposing raw personal data.
Risk Signal Aggregation
A risk aggregation system combines multiple intelligence sources such as email, phone, and IP reputation scoring, blockchain analytics for crypto compliance, custom business rules, and machine learning models to generate dynamic risk assessments.
Conclusion
Building a Jumio-style biometric identity verification system is more than a feature upgrade; it is a long-term strategic move for platforms that need secure growth and global compliance. With deepfake attacks increasing and regulatory pressure rising, biometric verification is becoming a core requirement rather than an optional layer.
When companies design the right AI infrastructure, integrate an adaptive fraud intelligence engine, and apply strong biometric security principles, verification can evolve into a scalable product and even a revenue stream. IdeaUsher can help teams build this system in a way that feels practical, technically sound, and ready for real-world expansion.
Looking to Develop a Jumio-like Biometric Identity Verification System?
IdeaUsher can help you build a Jumio-like biometric identity verification system by combining secure APIs with AI-powered facial matching and document scanning. Their team would guide you through compliance, liveness detection, and backend automation to ensure the system works reliably in real-world conditions.
With over 500,000 hours of coding experience and a team of ex-MAANG/FAANG developers, we architect enterprise-grade identity platforms that deliver:
- Deepfake-resistant liveness detection using advanced photonic analysis
- Cross-platform fraud intelligence via secure identity graph architecture
- Global document coverage with automated template adaptation
- Zero-friction UX through reusable identity frameworks
- Real-time risk orchestration with dynamic decision engines
Work with Ex-MAANG developers to build next-gen apps schedule your consultation now
FAQs
A1: A system like Jumio usually takes 6 to 12 months because you must build fingerprint or face-matching models, integrate liveness detection, and test across many ID formats. You could shorten the timeline with ready AI components; however, accuracy, compliance, and security tuning almost always take time.
A2: It can be compliant globally if you follow frameworks like GDPR, SOC 2, ISO 27001, and regional data protection rules. You might also need to adjust storage policies, encryption methods, and consent flows depending on the jurisdiction, as each region treats biometric data differently.
A3: Yes, and many companies do it by charging per verification or offering subscription tiers. Businesses will pay because it is usually cheaper and faster to integrate a reliable verification API than to build and maintain their own machine learning, fraud prevention, and regulatory controls.
A4: It is highly secure because the system stores encrypted biometric templates instead of raw media. Matching happens against mathematical patterns, and with access control, hashing, and audit trails in place, the risk of compromise is much lower than with passwords or static personal data.