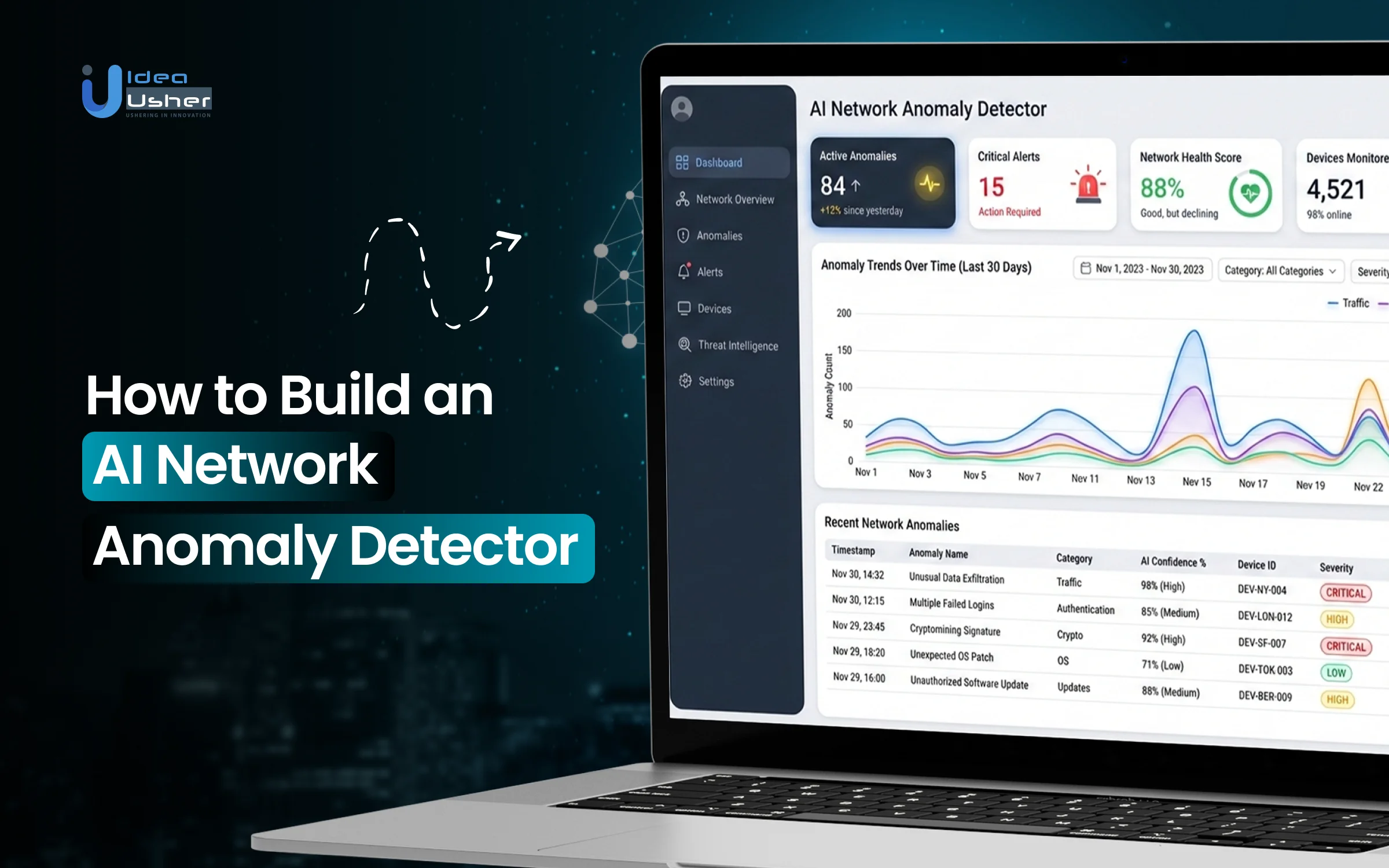
Modern networks generate massive traffic, making it difficult to distinguish normal activity from anomalies. Hidden intrusions, unusual spikes, and slow-moving attacks often go unnoticed, especially in distributed, complex infrastructures. That is why many organizations increasingly rely on an AI network anomaly detection tool to continuously monitor behavior, identify risks in real time, and prevent minor issues from escalating into serious security incidents.
AI-driven anomaly detection shifts network security from static rules to adaptive intelligence. By learning normal traffic patterns, user behavior, and system interactions, these systems can identify subtle deviations that traditional tools often miss. Using machine learning, real-time analytics, and automated alerts, they help security teams respond faster while reducing noise from false positives.
In this blog, we’ll break down how AI network anomaly detectors work, the key components needed to build one, and the technologies that power intelligent network monitoring. This guide will give you a clear roadmap for building a scalable, effective anomaly detection system.

What is an AI Network Anomaly Detection Tool?
An AI Network Anomaly Detection Tool is a security platform that uses machine learning, behavioral baselining and real-time telemetry analysis to identify unusual or high-risk activity across a network. Instead of relying on fixed rules, it continuously learns normal patterns and detects deviations that may indicate threats such as intrusions, data misuse, compromised accounts or abnormal traffic flows.
It represents a scalable, high-value cybersecurity solution built for cloud era networks, enabling organizations to automate threat detection, strengthen visibility and reduce response time with far lower operational overhead than traditional monitoring systems.
- Hidden pattern extraction through temporal sequence modeling, allowing the system to detect multi-step attack behaviors that unfold slowly over long time windows.
- Risk amplification logic that combines weak, low-confidence signals into meaningful threat indicators when correlated across users, workloads and network layers.
- Contextual metadata fingerprinting that builds identity signatures for devices and workloads, enabling detection of impersonation or subtle behavioral mismatches.
- Adaptive sensitivity tuning algorithms that automatically recalibrate thresholds in noisy or high-traffic environments to maintain stable, accurate detection levels.
Why Traditional Network Monitoring Fails in Modern Distributed Environments?
Traditional network monitoring relies on static rules and perimeter-based visibility, which struggle in cloud and remote environments. Modern distributed infrastructures require continuous, behavior-driven monitoring to detect evolving threats effectively.

1. Limited Visibility Across Cloud & Hybrid Traffic
Traditional monitoring tools, designed for centralized networks, struggle to monitor cloud workloads, remote endpoints, and east-west traffic. Lack of continuous telemetry creates blind spots, hindering detection of distributed threats or anomalies at scale.
2. Reliance on Static Rules & Signatures
Legacy systems rely on predefined rules or threat signatures, which can’t recognize evolving patterns, subtle deviations, or unknown attacks. As environments change, rule sets quickly become outdated, leading to missed threats and increased manual tuning.
3. Inability to Handle Real-Time Data Volumes
Modern environments generate extensive telemetry from applications, identity systems, and microservices. Traditional tools process logs in batches without real-time correlation, causing delays. This latency impairs early detection of suspicious activity or attacks.
4. Lack of Contextual Understanding
Legacy monitoring detects isolated events and can’t combine signals from identity, device, application activity, or encrypted traffic. Without context-aware interpretation, it struggles to distinguish harmless anomalies from security threats in distributed systems.
5. Poor Detection of Internal Lateral Movement
Traditional perimeter-focused systems rarely inspect internal communication deeply, allowing attackers to move laterally in microservices or cloud workloads without detection. Missing behavioral shifts prolong dwell times and increase breach impact.
How 94.3% Detection Accuracy Shows AI Network Anomaly Detection Is Essential?
The global anomaly detection market was valued at USD 4.33B in 2022 and is projected to reach USD 14.59B by 2030, growing at 16.5% CAGR. This growth is driven by technology, with machine learning systems showing that AI platforms deliver near-perfect threat detection and reduce false positives and missed threats common in traditional systems.
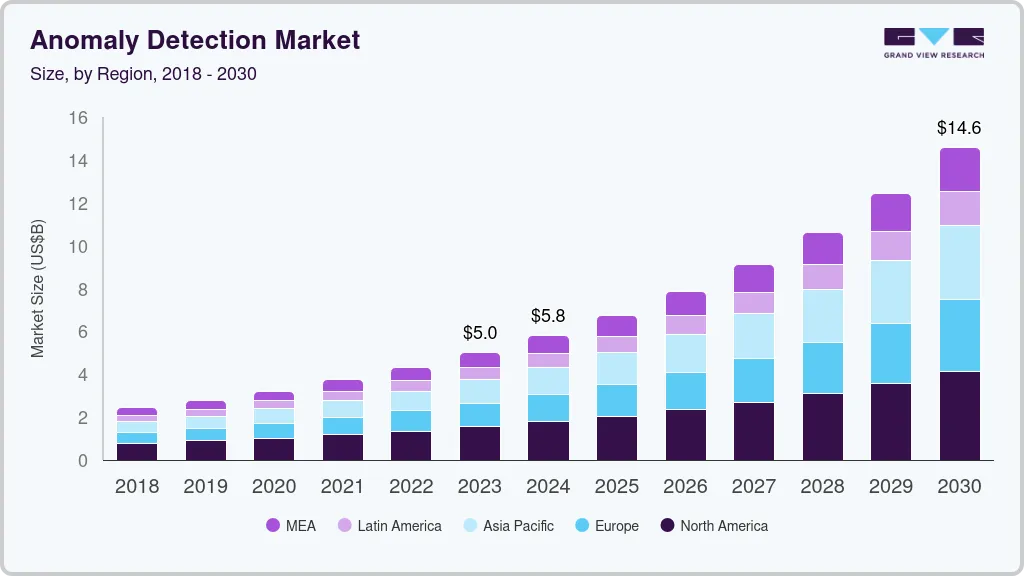
A machine learning system for network anomaly detection achieved 94.3% accuracy using Random Forest models. Combining unsupervised temporal pattern recognition with supervised anomaly classification, it validates AI anomaly detection as enterprise-ready.
A. AI Anomaly Detection Adoption and Market Growth
AI anomaly detection adoption is accelerating as enterprises seek better visibility, faster threat detection, and scalable security solutions to protect complex, distributed networks amid growing cyber risks.
- In 2025, 67% of enterprises used generative AI for cybersecurity, driving a 42% surge in demand for real-time monitoring and AI-enhanced anomaly detection.
- According to Blumira’s recent case study, advanced AI delivers 70% higher detection than traditional systems.
- 35% of large enterprises projected to adopt AI anomaly detection by 2025 leaves 65% untapped, representing tens of billions in potential ARR. Global network security spending totals $72.6B, making even modest market penetration highly lucrative.
- Google demonstrates 90% faster threat response with 20% more threats blocked at massive scale, validating AI anomaly detection in high-demand environments and easing enterprise adoption for risk-averse buyers.
B. How AI Enhances SOC Performance and Reduces Costs?
AI enhances SOC performance by automating threat detection, reducing alert fatigue, and accelerating response times, enabling security teams to operate more efficiently while lowering operational costs across enterprise environments.
- Red Canary’s AI agents reduce investigation times by 90%, with cases cutting response from 3 weeks to 19 minutes (99.9% improvement).
- Gartner projects 30-40% MTTR reduction, 20-25% fewer false positives, 25-50% higher analyst throughput, and 15-30% SOC cost savings.
- AI-driven anomaly detection reduces investigation time by 90%, allowing SOC teams to handle 10x more alerts without expanding headcount, improving threat detection efficiency and operational economics.
- McKinsey data shows 65% of cybersecurity budgets go to third-party vendors ($130B of $200B total), confirming that enterprises overwhelmingly prefer buying platforms over building AI in-house.

How AI Shifts Network Security From Reactive to Predictive?
AI transforms network security by analyzing behavior, detecting anomalies early, and predicting threats before impact. This shift enables proactive defense, faster response, and stronger protection across modern, distributed enterprise networks.
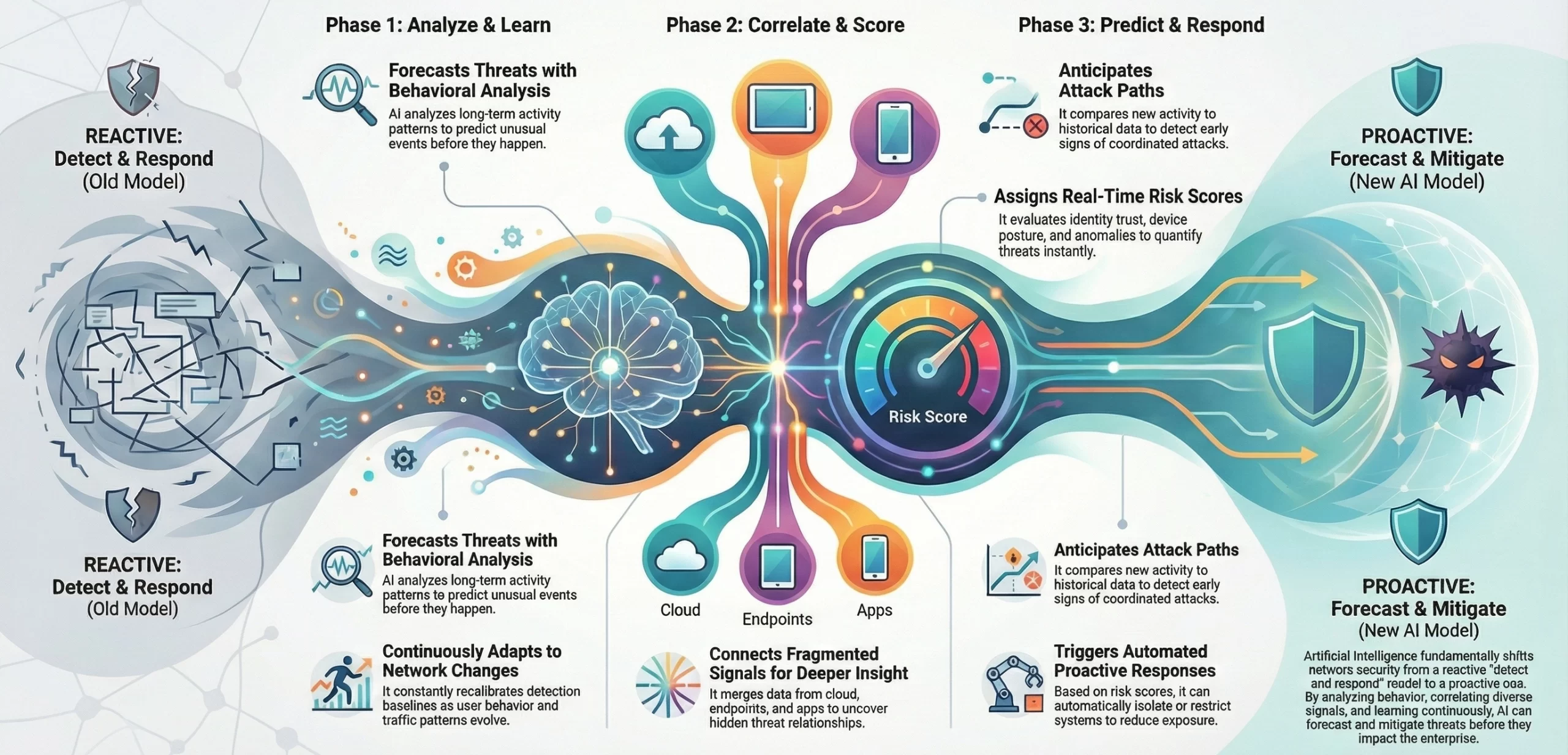
1. Early Detection Through Behavioral Forecasting
AI analyzes long-term activity patterns, traffic rhythms and identity behavior to forecast unusual events before they materialize. By applying behavioral prediction models, the system identifies early deviations that traditional tools miss, enabling teams to mitigate threats before they escalate.
2. Multi-Source Signals for Deeper Insight
Modern environments generate fragmented signals across cloud, identity, applications and endpoints. AI merges these streams using correlation intelligence, uncovering hidden relationships between events. This broader context transforms detection accuracy and shifts security from isolated alerts to anticipatory threat awareness.
3. Continuous Learning From Network Behavior
As user behavior, workloads and traffic patterns change, AI adapts by recalibrating detection baselines. Through continuous learning cycles, the system refines risk evaluation and maintains reliability, ensuring predictive detection even in highly dynamic environments with shifting operational norms.
4. Automated Risk Scoring & Response
AI assigns real-time risk scores based on identity trust, device posture, traffic context, and anomalies. When risks increase, it can trigger responses like isolation or restriction, reducing exposure and enhancing proactive security.
5. Threat Anticipation Through Pattern Analysis
AI studies long-term shifts in network behavior, comparing new activity to historical baselines to predict attack paths. It analyzes pattern evolution to detect early signs of coordinated threats, enabling organizations to act before malicious activity escalates.
Key Features of an AI Network Anomaly Detection Tool
An AI network anomaly detection tool continuously monitors network behavior, identifies unusual activity, and prioritizes threats in real time. These key features enhance visibility, reduce false positives, and strengthen enterprise cybersecurity defenses.

1. Advanced Behavioral Baseline Modeling
The tool learns normal activity patterns using behavioral baselining and statistical profiling. It continuously refines these models to detect subtle deviations that traditional systems miss. This helps identify early indicators of misuse, compromised accounts or unusual operational behavior across distributed environments.
2. Context-Aware Risk Scoring
Every event is evaluated with context-driven risk scoring that considers identity factors, device posture, data sensitivity and historical patterns. This layered context allows the tool to distinguish legitimate anomalies from harmful ones, reducing alert fatigue and improving the accuracy of detection outcomes.
3. Real-Time Data Stream Analysis
The system processes logs, telemetry and network signals in real time using streaming analytics. Inline pattern interpretation helps the tool react immediately to suspicious activities, enabling faster containment responses and early detection of abnormal spikes or unauthorized access attempts.
4. Adaptive Detection Algorithms
The tool uses adaptive AI algorithms that evolve with system behavior and emerging threats. As environments change, models recalibrate themselves to maintain precision. This ensures long-term detection reliability in dynamic settings with shifting user behaviors or application usage trends.
5. Multi-Source Signal Correlation
It aggregates signals from identity systems, cloud services, endpoint activity and network traffic, then applies correlation logic to identify cross-channel anomalies. This multi-perspective insight uncovers complex threat patterns that remain hidden when data sources are analyzed in isolation.
7. Automated Threat Response Triggers
When risk crosses defined thresholds, the tool activates automated response actions such as session isolation, access restriction or policy adjustments. These rapid controls prevent escalation, reduce exposure windows and support continuous security without relying solely on manual intervention.
8. Explainable Detection Insights
The system provides explainable insights that clarify why an anomaly was flagged. It highlights key influencing signals, model reasoning and contextual evidence, enabling analysts to make informed decisions quickly and build trust in the AI driven detection process.
9. Predictive Threat Anticipation Modeling
This feature uses predictive AI forecasting to identify threats before they fully emerge by analyzing long-term behavioral shifts and environmental signals. It highlights potential compromise paths and risk buildup patterns, enabling teams to take early preventive actions rather than reacting after anomalies occur.
10. Cross Domain Intelligence Fusion Engine
The tool merges signals from cloud workloads, API ecosystems, identity systems and microservices architectures through an AI fusion engine. By correlating these diverse sources, it detects multi-stage attack patterns that typically evade isolated monitoring tools, giving enterprises deeper situational awareness.
11. Dynamic Sensitivity Calibration
The system automatically fine-tunes detection sensitivity using adaptive calibration algorithms that monitor false positives, user friction levels and operational noise. This dynamic adjustment keeps detection accuracy high in constantly changing environments while ensuring alerts remain meaningful and contextually aligned with real risks.

How to Build an AI Network Anomaly Detector Tool?
Building an AI network anomaly detection tool requires collecting and analyzing network data, training models, and continuously monitoring traffic. Our developers follow a structured process to create robust, scalable enterprise cybersecurity solutions.
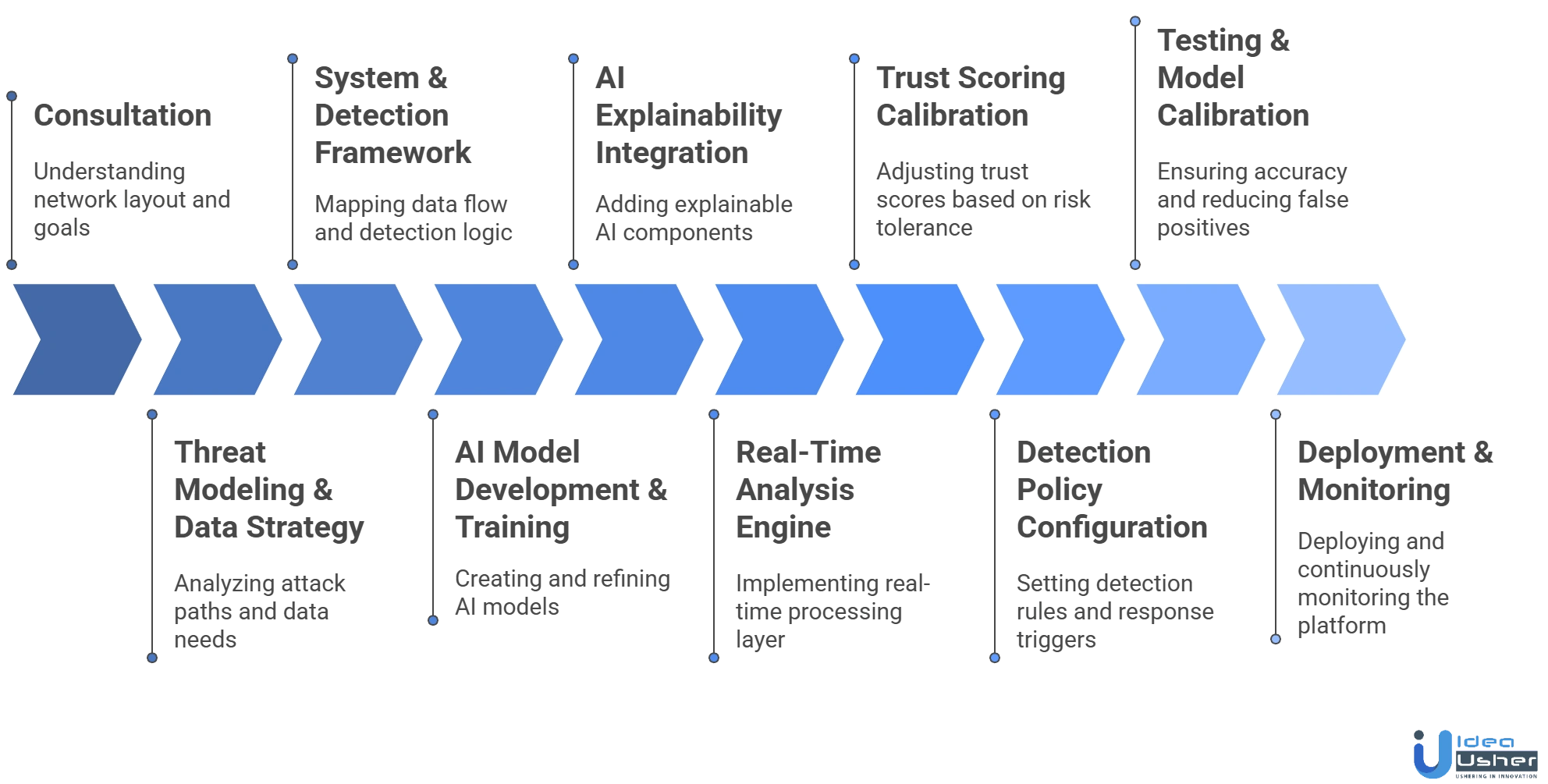
1. Consultation
We begin by understanding your network layout, data flows and detection goals. Our developers identify critical telemetry sources, compliance priorities and visibility gaps to design a tailored blueprint for an AI-driven anomaly detection system aligned with your operational structure.
2. Threat Modeling & Data Strategy Planning
We analyze potential attack paths, blind spots and misuse scenarios to understand what behaviors must be monitored. Our developers then design a data acquisition strategy, selecting which signals, logs and traffic patterns will feed the AI models for accurate anomaly detection.
3. System & Detection Framework Design
We outline how data moves through the platform, mapping ingestion pipelines, correlation layers and detection logic. The architecture supports behavioral baselining, context enrichment and structured scoring so anomalies can be identified with precision across dynamic and distributed network environments.
4. AI Model Development & Training
Our developers create AI models that interpret traffic patterns, event sequences and contextual signals. We build training pipelines that refine detection accuracy over iterations using curated datasets, adaptive learning methods and risk indicators derived from normal and abnormal network behaviors.
5. AI Explainability and Model Transparency Integration
To build trust, especially in regulated industries, we add explainable AI components that show why an anomaly was flagged, highlighting the signals and reasoning behind model decisions. This ensures analysts can understand and validate AI-driven detection outcomes.
6. Real-Time Analysis Engine Development
We implement a processing layer that handles continuous telemetry, normalizes signals and prepares them for interpretation. This enables real-time anomaly detection, allowing the engine to identify sudden deviations, suspicious flows or unauthorized activity without slowing down network performance.
7. Trust Scoring Calibration
We create dynamic trust scoring frameworks that adjust based on organization size, sensitivity zones and behavioral baselines. This allows the detection engine to align more naturally with each client’s unique operational risk tolerance.
8. Detection Policy Configuration
We configure detection rules, context-aware scoring thresholds and automated response triggers. These controls allow the platform to differentiate benign fluctuations from genuine threats and enforce protective actions such as session containment or activity blocking when high-risk behavior emerges.
9. Testing & Model Calibration
Our developers conduct extensive testing using simulated attack patterns, historical datasets and controlled environment traffic. We calibrate detection sensitivity, reduce false positives and validate model reasoning to ensure the system performs accurately under various operational loads and behavioral variations.
10. Deployment & Monitoring
We deploy the platform with real time monitoring dashboards and feedback loops that support ongoing tuning. Our developers refine model behavior, adjust scoring logic and enhance detection workflows to ensure the tool evolves alongside emerging network patterns and advanced threat techniques.
Cost to Build an AI Network Anomaly Detection Tool
The cost to build an AI network anomaly detection tool depends on data collection, model training, infrastructure, and ongoing maintenance. Accurate budgeting ensures efficient deployment and effective enterprise cybersecurity protection.
| Development Phase | Description | Estimated Cost |
| Consultation | Defines scope and identifies key network visibility and anomaly detection needs. | $4,000 – $7,000 |
| Threat Modeling & Data Strategy | Maps attack paths and designs a data acquisition strategy for AI learning. | $10,000 – $16,000 |
| Detection Framework Design | Creates pipelines, correlation layers and baseline modeling structure for detection. | $14,000 – $22,000 |
| AI Model Training & Development | Builds anomaly models, training workflows and behavior interpretation logic. | $16,000 – $30,000 |
| Real Time Processing & Analysis Engine | Develops continuous telemetry ingestion and real-time detection layers. | $14,000 – $27,000 |
| Security Policies & Automated Response Setup | Configures context-aware thresholds and automated isolation triggers. | $12,000 – $18,000 |
| Testing & Validation | Tests detection accuracy and tunes false positive balance and model sensitivity. | $7,000 – $14,000 |
| Deployment & Monitoring | Deploys platform, sets dashboards and ongoing calibration loops for stability. | $8,000 – $18,000 |
Total Estimated Cost: $65,000 – $124,000
Note: Final cost depends on network size, AI complexity, compliance, data access, security tool integration, explainable AI, drift detection, and multi-source correlation, which all influence the budget.
Consult with IdeaUsher to get a precise cost estimate and a customized development roadmap for building a high-performing, enterprise-grade AI anomaly detection solution tailored to your business environment.
Cost-Affecting Factors to Consider
Several key factors, including data complexity, model selection, infrastructure, and maintenance, influence the overall cost of developing an AI network anomaly detection tool.
1. Scope & Complexity of Detection Capabilities
Broader requirements such as multi-layer anomaly detection, behavioral modeling and advanced risk scoring increase development cost since they require deeper design planning, extensive data coverage and more refined detection logic.
2. Quality & Availability of Network Data
High-quality datasets reduce training effort, while fragmented or limited data sources increase cost. Additional work is needed to build cleaning pipelines, labeling workflows and baseline models to support accurate AI detection.
3. Integration With Existing Security Systems
Connecting the tool to identity systems, SIEM platforms and traffic sources can raise cost depending on compatibility. Complex environments often require custom adapters and mapping logic to maintain reliable interoperability.
4. Level of Automation & Response Capabilities
Costs rise as the system moves beyond detection into automated isolation or dynamic policy adjustments. Building automated response triggers and adaptive rules involves additional design and testing work.
5. Compliance & Governance Requirements
Industries with strict regulations may need deeper auditing, encrypted telemetry handling and governance controls, which influence total development time and validation cycles.
6. Scalability & Performance Expectations
Supporting continuous inspection for large or distributed networks requires strong architecture planning. Designing high-throughput pipelines and scalable components increases engineering effort and overall budget.
Suggested Tech Stacks for AI Network Anomaly Detection Tool Development
Selecting the right technology stack is critical for building an AI network anomaly detection tool. A well-designed stack supports scalable data processing, accurate machine learning models, and reliable real-time threat detection.
| Category | Suggested Technologies | Purpose |
| AI & ML Frameworks | TensorFlow, PyTorch, Scikit-learn | Power behavior modeling, anomaly detection algorithms and continuous learning capabilities. |
| Cloud Infrastructure & Distributed | AWS, Azure, Google Cloud | Provide scalable compute, low-latency processing and global availability for detection pipelines. |
| Identity & Access Management | OAuth 2.0, OpenID Connect, Keycloak | Ensure secure identity validation and accurate context for behavior analysis. |
| Network Telemetry & Ingestion Layer | Kafka, Fluentd, Logstash | Handle high-volume event ingestion and structured processing of network signals. |
| Correlation & Policy Evaluation Engine | Open Policy Agent (OPA) | Enable context-aware decision-making across identity, behavior and traffic events. |
| Containerization & Orchestration | Docker, Kubernetes | Support modular deployment, auto scaling and stable operation of detection components. |
| Monitoring, Telemetry & Observability | Prometheus, Grafana, ELK Stack | Deliver real-time visibility, anomaly insights and performance monitoring across pipelines. |
Challenges & How Our Developers Will Solve Them?
Developing AI network anomaly detection tools presents challenges such as data quality, model accuracy, and scalability. Our developers address these issues with robust design, advanced algorithms, and enterprise-ready solutions.

1. Data Quality Issues in Network Telemetry
Challenge: Incomplete, noisy or inconsistent telemetry reduces AI accuracy and limits the system’s ability to build reliable behavioral baselines across large network environments.
Solution: We create data refinement pipelines, normalize logs, filter noise and design structured ingestion flows that improve baseline formation, enabling the model to learn clean and consistent behavior patterns.
2. Detecting Sophisticated Low & Slow Threats
Challenge: Slow-moving attacks generate minimal signals and often bypass traditional rules, making it difficult to identify long-term anomalies hidden within normal traffic patterns.
Solution: Our developers apply behavioral baselining, sequence pattern analysis and long window correlation to identify subtle deviations, allowing early detection of threats designed to evade short interval monitoring.
3. Balancing False Positives & Detection Sensitivity
Challenge: Overly sensitive detection triggers unnecessary alerts, while low sensitivity leaves critical anomalies undetected, disrupting operational reliability.
Solution: We calibrate adaptive detection thresholds, embed analyst feedback loops and refine scoring models, creating a balanced system that minimizes noise while maintaining strong awareness of meaningful network abnormalities.
4. Ensuring Real-Time Detection
Challenge: Continuous analysis of high-volume telemetry streams can slow performance and impact user experience if processing layers are not optimized.
Solution: We build streamlined processing pipelines, optimize event correlations and apply selective prioritization so real-time detection occurs at scale without affecting network stability or user responsiveness.
5. Adapting to Evolving Network Behavior
Challenge: Network environments change, causing model drift that reduces detection precision and triggers outdated interpretations of new traffic patterns.
Solution: Our developers implement drift detection logic, continuous retraining workflows and automated model updates, ensuring the system evolves with environment changes and maintains long-term detection accuracy.

Revenue Models of an AI Network Anomaly Detection Tool
AI network anomaly detection tools can generate revenue through subscription plans, licensing, and managed services. Choosing the right monetization model ensures predictable income while supporting scalable, enterprise-grade cybersecurity solutions.
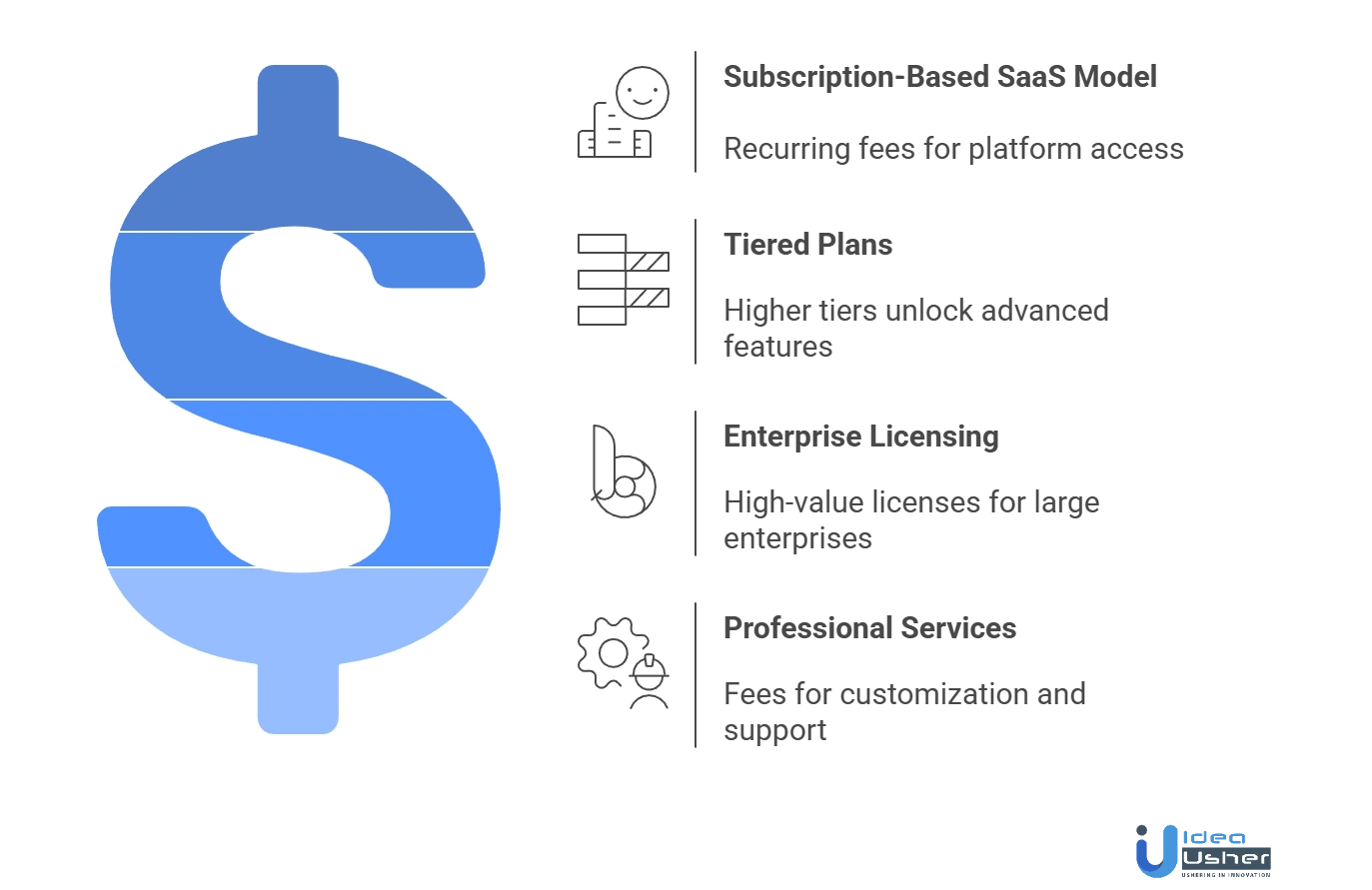
1. Subscription-Based SaaS Model
This model charges recurring monthly or annual fees for access to the platform. Pricing scales with user count, monitored assets or network size. It provides predictable revenue while delivering continuous updates, AI enhancements and real-time anomaly detection capabilities to customers.
2. Tiered Plans With Feature-Based Upgrades
Companies adopt a layered pricing model where higher tiers unlock advanced capabilities such as AI-driven risk correlation, encrypted traffic insights, automated response actions and deeper analytics. This structure encourages gradual customer expansion as security maturity increases and operational needs grow.
3. Enterprise Licensing & Dedicated Deployments
Large enterprises may require private deployments, advanced AI governance, custom integrations and compliance adaptations. This creates opportunities for high value licenses, dedicated support plans and premium features tailored to regulated industries or mission-critical environments.
4. Professional Services & Customization Fees
Revenue can also come from onboarding assistance, integration support, model training, system tuning and building custom detection policies. These services help clients maximize value from the tool while generating consistent service-based income for the provider.
Leading AI Network Anomaly Detection Platforms
AI-powered network anomaly detection platforms use machine learning and behavioral analytics to identify unusual network activity and security threats in real time. Below are leading real-world platforms applying AI across modern enterprise and cloud networks.
1. Vectra AI
Vectra AI is an AI-powered Network Detection and Response (NDR) platform using machine learning and behavioral analytics to detect network anomalies, attacker behaviors, and advanced threats like lateral movement, C2 traffic, and data exfiltration across cloud, hybrid, and enterprise networks. Its AI-driven risk scoring and MITRE ATT&CK alignment help teams prioritize alerts.
2. Darktrace

Darktrace Network is an AI-based anomaly detection platform using unsupervised machine learning to establish real-time baselines of normal behavior. It detects abnormal traffic, insider threats, and zero-day attacks without predefined rules, continuously adapting as network conditions and behaviors evolve.
3. Seceon
Seceon is an AI-driven network anomaly detection platform that applies machine learning to traffic, logs, and telemetry data to identify hidden threats. It correlates anomalies with user and entity activity, improving detection accuracy, reducing false positives, and integrating with SIEM and XDR workflows.
4. Selector
Selector is an AI-powered network observability and anomaly detection platform that uses machine learning to analyze traffic patterns, performance metrics, and infrastructure behavior. It detects abnormal activity in real time, accelerates root-cause analysis, and bridges network performance monitoring with AI-driven anomaly detection.
5. CrunchMetrics
CrunchMetrics is an AI-based anomaly detection platform that uses machine learning to identify abnormal patterns in large-scale time-series and network data. It learns historical behavior automatically, enabling real-time detection of anomalies affecting performance, reliability, and security in high-volume environments.
Conclusion
An AI network anomaly detector tool enables organizations to proactively identify unusual patterns and potential threats within their networks, ensuring continuous security monitoring. By leveraging intelligent algorithms, this tool enhances visibility, reduces response times, and prevents data breaches before they escalate. Implementing such a platform allows businesses to maintain operational continuity, safeguard sensitive information, and optimize network performance. Combining automation with advanced analytics ensures that anomalies are detected accurately and efficiently, supporting informed decision-making while strengthening the overall cybersecurity posture of the organization.
Build an AI Network Anomaly Detection Tool With IdeaUsher!
Building an AI network anomaly detector goes beyond basic monitoring. It demands intelligent traffic analysis, real-time alerting, and systems that scale across complex network environments. IdeaUsher helps businesses engineer AI-powered security platforms that detect threats before they escalate.
Why Work With Us?
- Advanced Anomaly Detection Design: We develop AI models trained to identify unusual traffic patterns, lateral movement, and hidden network threats.
- Real-Time Data Processing: Our solutions are built for high-volume data ingestion with low-latency detection and response.
- Scalable Security Infrastructure: We architect platforms that integrate smoothly with cloud, hybrid, and enterprise network environments.
- Strong Platform Engineering Track Record: Our portfolio showcases successful delivery of AI-led and security-focused platforms.
Review our portfolio to see how we’ve helped companies launch reliable, high-performance AI solutions.
Contact us to explore how we can help you build and launch an AI network anomaly detection solution tailored to your market needs.
Work with Ex-MAANG developers to build next-gen apps schedule your consultation now
FAQs
Essential features include real-time traffic monitoring, anomaly detection algorithms, alert notifications, historical pattern analysis, and reporting dashboards. These functionalities ensure accurate identification and timely resolution of network anomalies.
Effective AI anomaly detection requires large volumes of historical and real-time network traffic data. Diverse datasets improve accuracy, reduce false positives, and help models learn normal behavior patterns before identifying suspicious anomalies reliably.
False positives are reduced through continuous model training, adaptive thresholds, contextual analysis, and feedback loops. Combining supervised and unsupervised learning improves precision while ensuring security teams are alerted only to actionable threats.
Yes, with cloud-native architecture and distributed processing, the system can scale across large enterprise networks. Scalable data pipelines and optimized models allow real-time analysis without performance degradation as traffic volumes increase.