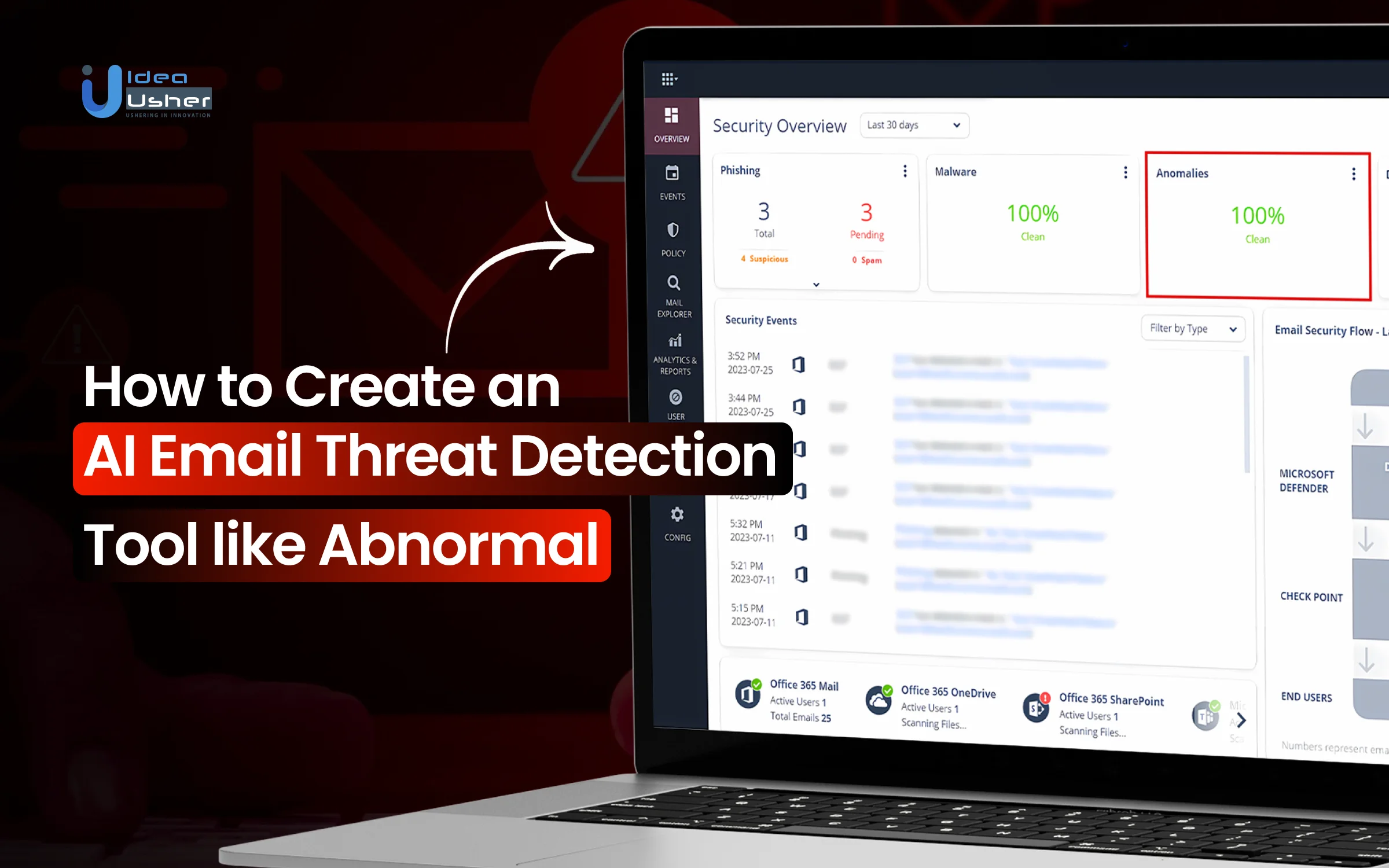
Email remains one of the most common entry points for cyberattacks, yet many threats no longer look obviously malicious. Social engineering, impersonation, and business email compromise bypass traditional filters. These risks drive organizations to adopt Abnormal-like AI email threat detection tools that analyze context, behavior, and intent rather than relying on known signatures.
AI-powered email security tools analyze normal communication patterns and flag deviations. Using machine learning, natural language processing, and behavioral analysis, they detect anomalies like unusual senders, tone shifts, or unexpected requests, helping security teams stop sophisticated email attacks early while reducing false positives.
In this blog, we’ll explore how to build an AI-driven email threat detection tool similar to Abnormal, including the core features and underlying technologies. As we have helped multiple enterprises build their AI solutions, IdeaUsher has the expertise to create a smarter, more adaptive email protection system.
What is an AI Email Threat Detection Tool, Abnormal?
Abnormal is an AI-native cloud email security platform that uses behavioral AI and contextual analysis to stop phishing, business email compromise, account takeovers, invoice fraud, and socially engineered attacks. It learns user communication patterns using identity behavior, content, metadata, and history. API-first integrations with Microsoft 365 and Google Workspace enable real-time automated detection, triage, and remediation.
This platform uses behavioral baselining and AI-driven risk scoring to detect novel attacks that bypass legacy secure email gateways. Its cloud-native, API-based architecture enables rapid deployment, real-time remediation, reduced false positives, and comprehensive protection against inbound mail, account takeover, and configuration drift risks.
- Builds per-user communication baselines analyzing relationships, patterns, and history to detect targeted or social engineering attacks missed by traditional filters.
- API-first cloud-native deployment integrates with email platforms, requires no MX changes, enabling fast rollout and continuous Microsoft 365 and Google Workspace protection.
- Automates triage and remediation of user-reported threats with conversational AI, reducing SOC workload and accelerating incident resolution.
- Ingests thousands of signals to create granular identity risk models, adapting to communication changes for context-rich anomaly detection beyond content scanning.
- AI-powered reporting workflows like the AI Security Mailbox classify and remediate threats, improving feedback loops and reducing SOC workload.
A. Business Model: How it Operates
Abnormal AI operates a cloud-native, subscription-driven cybersecurity model that delivers AI-powered email threat protection through seamless API integration and continuous behavioral analysis.
- AI-native behavioral security approach that replaces static rules with continuous learning, enabling smarter detection of social engineering, BEC and account compromise attempts.
- Cloud-delivered platform integrating directly with Microsoft 365 and Google Workspace through APIs, eliminating deployment friction and infrastructure overhead.
- Enterprise-focused solution targeting organizations that require advanced protection beyond traditional secure email gateways.
- Modular product strategy offering additional capabilities such as account takeover protection, configuration drift analysis and posture management upgrades.
- High retention model driven by automated detection, low operational burden and measurable reduction in SOC investigation time.
B. Fundings of Abnormal AI
Abnormal AI (Abnormal Security) raised venture capital to scale its AI email security platform, expand worldwide, and boost innovation. This funding timeline shows investor confidence in behavior-driven cybersecurity over traditional gateways.
1. Series A – 2019
Abnormal raised about $24 million to commercialize its behavioral AI engine and strengthen its API-based email security architecture. This round laid the groundwork for enterprise expansion and early ML model development.
2. Series B – 2020
The company secured $50 million, led by Menlo Ventures with support from Greylock Partners. Funding was used to scale data science operations, enhance anomaly detection models and expand integrations across cloud email platforms.
3. Series C – 2022
Abnormal closed a $210 million round led by Insight Partners, bringing its valuation to roughly $4 billion. This enabled rapid global expansion, investment in AI threat research and development of adjacent security products.
4. Series D – 2024
The latest round raised $250 million at a $5.1 billion valuation, led by Wellington Management. Capital is focused on advancing large-scale behavioral modeling, expanding enterprise reach and deepening the platform’s automated response ecosystem.
The Role of Behavioral AI in Modern Email Security Architecture
Behavioral AI enhances modern email security by analyzing user behavior, context, and communication patterns to detect subtle threats. Explore its role in preventing phishing, fraud, and sophisticated email attacks effectively.
1. Behavioral Baselines from Communication Patterns
Behavioral AI establishes dynamic baselines by analyzing sender relationships, message frequency, linguistic tone and interaction history. These baselines allow the system to identify deviations that traditional filters overlook, enabling early discovery of socially engineered threats and identity inconsistencies.
2. Relationship Graph Modeling for Identity
The architecture uses relationship graph modeling to understand how users and entities normally communicate. By mapping relational context across recipients, departments and domains, the system detects anomalies such as impersonation attempts, unusual authority shifts or previously unseen communication links.
3. Intent & Linguistic Signal Interpretation
Behavioral AI examines semantic cues, intent markers and syntactic patterns to classify emails beyond surface-level content. It isolates tone manipulation, urgency indicators and transactional inconsistencies that help uncover phishing attempts and business email compromise hidden behind legitimate-looking messages.
4. Multidimensional Risk Scoring
The system merges behavioral anomalies, metadata signals, identity context and communication entropy into a multidimensional risk score. This scoring engine prioritizes high-risk events, reduces false positives and brings clarity to ambiguous communication behaviors across complex email ecosystems.
5. Adaptive Baseline Recalibration for Threat Drift
Behavioral AI performs adaptive baseline recalibration, updating communication norms as users change vendors, workflows or messaging tone. This prevents model drift, enabling the system to distinguish legitimate behavioral evolution from slow-moving or intentionally low-signal social engineering attacks.
How 82.6% of Phishing Emails Using AI Proves AI Email Threat Detection Tools Are Essential?
The global AI Email Security market reached USD 5.73 billion in 2024 and is expected to grow at a CAGR of 22.4%, reaching USD 43.66 billion by 2033. This growth reflects how rapidly organizations are prioritizing AI-driven defenses against modern email threats.
Phishing attacks have become far more effective as AI now powers 82.6% of malicious emails, driving a 54% click-through rate compared to just 12% for traditional campaigns, and clearly outperforming legacy, rule-based detection techniques.
A. AI-Generated Phishing Is Bypassing Traditional Email Security
AI-generated phishing emails are driving a major shift in email security, with 87% of organizations moving away from legacy secure email gateways, highlighting why traditional tools can no longer keep pace with evolving threats.
- AI phishing has surged by 1,265% since the launch of ChatGPT, indicating exponential threat growth.
- 40% of BEC attacks are AI-generated, with average losses reaching $128,980 per successful attack.
- Traditional secure email gateways rely on static rules and signatures that cannot adapt to rapidly evolving AI-generated content.
- Modern AI email threat tools use behavioral baselining and contextual analysis to detect intent, not just known indicators.
B. Why Email Requires AI-Based Security Protection?
Email continues to be the most exploited attack surface, with phishing responsible for 75–91% of cyberattacks, making AI-driven email threat detection essential for stopping breaches at the earliest stage.
- 94% of organizations experienced phishing attacks in the past year, showing near-universal exposure.
- 44% of phishing emails originate from compromised internal accounts, bypassing authentication controls.
- 95% of security leaders report stress over email security, reflecting widespread failure of legacy defenses.
- Email gives attackers direct access to human trust, enabling impersonation and social engineering at scale.
- Stopping threats at the email layer prevents credential theft, financial fraud, and lateral movement across enterprise systems.
AI-driven phishing has fundamentally changed the email threat landscape, rendering legacy defenses ineffective against modern, adaptive attacks. As AI-generated emails dominate breach entry points, building intelligent, behavior-based email threat tools is no longer optional but essential for proactive, scalable security.
Key Differentiators That Make an AI Email Tool Stand Out in the Market
AI email security tools stand out by using advanced machine learning, behavioral analysis, and contextual intelligence to detect modern threats. Explore the key differentiators that define effective, next-generation AI email protection solutions.
1. Advanced Relational Graph Intelligence
The platform can build relational graph intelligence that maps long-term communication patterns, authority structures and cross-department relationships. This enables precise detection of identity misuse, impersonation attempts and communication anomalies often missed by content or metadata-focused filtering systems.
2. Predictive Social Engineering Signal Analysis
Instead of reacting to known attack indicators, the system identifies pre-attack behavioral signals such as tone manipulation, urgency cues, relational inconsistencies and implied intent. This predictive capability exposes early-stage manipulation long before malicious links, payloads or clear phishing markers appear.
3. Cross-Channel Threat Correlation
The tool correlates email metadata with identity logs, device posture changes, cloud application signals and collaboration tool activity. This multi-channel insight uncovers coordinated or multi-step threats hidden across systems, offering detection depth unavailable in email-only engines.
4. Dynamic Trust Scoring for Real-Time Sender
Each sender receives a dynamic trust score based on behavioral history, semantic consistency, authentication context and metadata fingerprints. This scoring framework improves accuracy in identifying synthetic identities, compromised accounts and socially engineered impersonation campaigns.
5. Explainable AI for Transparent Decision-Making
The platform integrates explainable AI reasoning that highlights the signals influencing each detection, including linguistic cues, relational anomalies and contextual risk factors. This transparency enhances analyst confidence and accelerates investigation workflows by removing black box uncertainty.
6. Adaptive Relationship Integrity Engine
The platform maintains relationship integrity models tracking identity interactions, including frequency, direction, and tone. By monitoring sudden shifts, it detects impersonation, vendor fraud, and synthetic identities more accurately than traditional filters.
Key Features of an Abnormal-like AI Email Threat Detection Tool
Abnormal-like AI email threat detection tools use behavioral analytics, machine learning, and contextual intelligence to detect phishing, BEC, and social engineering attacks. These are key features showcasing how these platforms protect organizations effectively.
1. Behavioral AI Threat Detection
The tool builds behavioral baselines for every user by analyzing communication patterns, identity relationships and message context. It identifies deviations that indicate phishing, business email compromise or social engineering attempts, catching threats that bypass traditional rule-based or signature-dependent filters.
2. API Native Cloud Integration
An API first design connects directly to cloud email providers without altering mail flow. This enables frictionless deployment, continuous data ingestion and full visibility into inbound, outbound and internal communication patterns while maintaining the performance and reliability of the existing email environment.
3. Automated Email Triage & Remediation
The platform intelligently classifies suspicious messages, evaluates user-reported threats and initiates automated remediation workflows that remove malicious emails or neutralize risky content. This reduces SOC workload while ensuring faster, more accurate responses to evolving email-based attack campaigns.
4. Account Takeover & Identity Risk Detection
By monitoring login behavior, device posture, session context and unusual access patterns, the tool detects indicators of account takeover. Identity risk scoring and contextual validation help prevent attackers from using compromised accounts to launch targeted or internal email attacks.
5. Security & Configuration Drift Monitoring
The system continuously evaluates administrative configurations, privilege assignments and exposure risks inside cloud email platforms. It identifies configuration drift, misaligned permissions and policy gaps that attackers may exploit, helping organizations maintain a strong and compliant email security posture.
6. Advanced Graymail & Noise Reduction Controls
Beyond malicious threats, the tool filters low-value but distracting messages using intelligent classification models. This improves user productivity, reduces inbox clutter and allows security teams to focus on meaningful events rather than operational noise.
7. Adaptive AI Learning for Evolving Threats
AI models refine themselves as communication patterns change and new threat techniques appear. Through continuous learning cycles, the system improves detection accuracy, reduces false positives and stays aligned with shifting attacker behavior across global email ecosystems.
8. Predictive Social Engineering Pattern Modeling
This feature uses predictive behavioral AI to detect early signs of social engineering by analyzing tone, relationships, and communication timing, anticipating attack intent and blocking high-risk emails before malicious payloads or links are introduced.
9. Cross-Channel Identity Fusion Engine
Instead of analyzing emails in isolation, the platform correlates identity signals from authentication logs, collaboration tools and cloud applications. This multi-source intelligence fusion uncovers identity inconsistencies, suspicious behavior chains and pre-attack reconnaissance attempts that traditional email-only systems cannot detect.
10. Dynamic Trust Scoring for Integrity
Every sender and internal user receives a dynamic trust score that adjusts in real time based on message credibility, historical behavior, metadata fingerprints and relational context. This enables precision-level filtering that detects impostors, synthetic identities and compromised accounts with significantly higher accuracy.
How to Create an AI Email Threat Detection Tool like Abnormal?
Building an Abnormal-like AI email threat detection tool involves combining behavioral AI, contextual analysis, and cloud-native architecture to detect advanced phishing and BEC attacks. Our developers follow a detailed process to design, test, and deploy these capabilities.
1. Consultation
We begin by understanding your email environment, identity systems and threat exposure. Our developers analyze communication patterns, compliance needs and integration requirements to design a behavior-driven security blueprint that supports accurate detection across cloud email platforms like Microsoft 365 or Google Workspace.
2. Threat Modeling & Data Strategy Planning
We map potential attack vectors such as phishing, impersonation and account takeover attempts. Our developers outline a data acquisition strategy that defines which email signals, metadata fields and behavioral indicators will feed AI models for high fidelity anomaly detection.
3. Behavioral Engine Design
We design the system architecture by outlining ingestion pipelines, relational mapping layers and behavioral analysis logic. This ensures the platform can baseline communication patterns, track identity relationships and evaluate anomalies across inbound, outbound and internal email flows with consistent accuracy.
4. AI Model Training & Development
Our developers build AI models that interpret linguistic cues, sender reputation, relationship graphs and message intent. We create training pipelines that refine prediction accuracy using historical data, behavioral samples and continuous learning methods to detect subtle, socially engineered threats.
5. Email Ingestion & Risk Scoring Buildout
We implement modules that process emails in real time, extract metadata, classify intent and generate context-aware risk scores. This includes evaluating sender identity, message structure, communication history and activity patterns to surface high-value threats early.
6. Threat Response & Automated Remediation
We design automated workflows that handle suspicious messages through intelligent remediation, such as quarantine, removal or user notification. These response actions reduce analyst workload and enable rapid containment of phishing attempts, compromised account activity or impersonation campaigns.
7. Security & Configuration Monitoring Setup
Our developers build monitoring layers that assess email security posture, privilege assignments and configuration drift. This enables continuous visibility into risky settings, misaligned permissions and exposure paths that attackers might exploit during identity or email-based intrusions.
8. Explainable AI & Trust Framework
We integrate an explainable AI layer that highlights intent cues, relational mismatches, and risk factors, clarifying why emails are flagged. This transparency builds analyst trust, improves decisions, and differentiates the platform from black-box email security systems.
9. Testing & Detection Tuning
We run extensive tests using simulated attacks, historical patterns and real communication sequences. Our developers tune false positive thresholds, refine anomaly scoring and validate end-to-end detection accuracy to ensure dependable protection across dynamic email environments.
10. Deployment & Optimization
We deploy the platform within your cloud email ecosystem, integrate dashboards and establish feedback loops. Continuous monitoring allows us to adjust behavioral baselines, refine AI scoring logic and enhance detection workflows as communication patterns evolve and new threats emerge.
Cost to Build an Abnormal-like AI Email Threat Detection Tool
The cost to build an Abnormal-like AI email threat detection tool depends on AI development, behavioral analytics, cloud infrastructure, and security testing. Here is an overview showcasing estimated investment and key cost factors.
| Development Phase | Description | Estimated Cost |
| Consultation | Defines scope, data needs and core email threat detection goals. | $4,000 – $7,000 |
| Threat Modeling & Data Strategy Planning | Maps attack vectors and builds a data ingestion strategy for AI. | $6,000 – $12,000 |
| Behavioral Engine Design | Designs pipelines and behavioral analysis logic for detection. | $13,000 – $27,000 |
| AI Model Training & Development | Builds ML models and training workflows for intent and anomaly detection. | $17,000 – $30,000 |
| Email Ingestion & Risk Scoring | Develops real-time processing, message classification and risk scoring layers. | $12,000 – $18,000 |
| Threat Response & Automated Remediation | Configures automated remediation actions for suspicious messages. | $12,000 – $18,000 |
| Security & Configuration Monitoring | Adds monitoring for misconfigurations, privilege risks and posture drift. | $10,000 – $14,000 |
| Explainable AI Layer Integration | Implements transparent AI reasoning for analyst trust and clarity. | $12,000 – $18,000 |
| Testing & Validation | Conducts scenario testing, calibrates thresholds and tunes detection accuracy. | $8,000 – $12,000 |
| Deployment & Improvement | Deploys platform, sets dashboards and enhances performance over time. | $5,500 – $10,000 |
Total Estimated Cost: $66,000 – $125,000
Note: Development costs depend on email volume, organization size, datasets, compliance, and AI complexity. Custom integrations, workflows, and optimization also affect the budget.
Consult with IdeaUsher for a personalized cost estimate and roadmap to develop a high-performance AI email threat detection tool tailored to your security goals.
Cost-Affecting Factors to Consider
Several factors influence the cost of developing an AI email threat tool, from technology choices to deployment complexity. These are some key elements showcasing their impact.
1. Scope & Complexity of AI Capabilities
Advanced detection requirements, behavioral modeling depth and multi-layer analysis significantly influence cost because they demand richer datasets, additional logic design and more extensive development cycles.
2. Quality & Volume of Email Data Available
Limited or noisy email data increases cost since developers must build data cleaning pipelines, labeling workflows and enriched baselines to support accurate AI learning and anomaly detection.
3. Integration Needs With Existing Security Ecosystem
Costs rise when connecting the tool to identity platforms, SIEM systems or workflow tools, especially if custom connectors or interoperability logic is required for seamless operation.
4. Automation Level for Threat Response
More automation, such as intelligent remediation workflows and contextual isolation logic, requires deeper engineering and testing, increasing both development time and overall project investment.
5. Compliance & Privacy Requirements
Strict regulations around message handling, data residency and privacy-preserving analysis add extra validation layers, audit controls and verification processes that expand development duration and cost.
Suggested Tech Stacks for an AI Email Threat Detection Tool
Selecting the right tech stack is essential for building an effective AI email threat detection tool. These are some suggested technologies that support accurate threat detection, scalability, and reliable email security performance.
| Category | Suggested Technologies | Purpose |
| AI & Machine Learning Frameworks | TensorFlow, PyTorch, Scikit-learn | Power behavior modeling, intent analysis and anomaly detection across email data. |
| Cloud Infrastructure & Deployment | AWS, Azure, Google Cloud | Enable scalable processing, secure storage and high availability for continuous threat analysis. |
| Natural Language Processing (NLP) | Hugging Face Transformers, spaCy | Support intent classification, linguistic pattern detection and analysis of email content signals. |
| Identity & Access Management Integration | OAuth 2.0, OpenID Connect, Keycloak | Provide secure identity context for evaluating sender legitimacy and user behavior. |
| Email Ingestion & Event Processing Layer | Kafka, Fluentd, Logstash | Handle large-scale email metadata ingestion and prepare structured streams for AI evaluation. |
| Threat Correlation & Policy Evaluation | Open Policy Agent (OPA) | Enable context-aware decision logic that merges identity, behavior and communication signals. |
| Containerization & Orchestration | Docker, Kubernetes | Support modular deployment, auto-scaling and stable operation of detection services. |
| Monitoring, Telemetry & Observability | Prometheus, Grafana, ELK Stack | Deliver real-time visibility into detection performance, anomalies and system reliability. |
Challenges & How Our Developers Will Solve Those?
Developing an AI email threat tool involves challenges like detecting sophisticated attacks, ensuring low false positives, and integrating with cloud platforms. Our developers follow proven strategies to address these challenges effectively.
1. Building Behavioral Baselines
Challenge: Communication patterns vary across teams, roles and regions, making it difficult to establish consistent behavioral baselines for accurate threat detection.
Solution: We analyze long-term communication trends, apply behavior clustering techniques and refine profiles using contextual metadata to build stable baselines that adapt naturally to organizational differences.
2. Detecting Advanced Social Engineering Attacks
Challenge: Many social engineering attacks lack malicious links or attachments, making them difficult to detect using traditional email scanning techniques.
Solution: We implement intent analysis models, relational graph scoring and linguistic pattern interpretation to reveal subtle anomalies in sender behavior, tone shifts and communication context.
3. Reducing False Positives While Maintaining Accuracy
Challenge: Overly sensitive systems generate unnecessary alerts, while overly lenient systems miss advanced threats, disrupting operational efficiency.
Solution: Our developers tune adaptive risk thresholds, integrate analyst feedback loops and apply multi-signal correlation to maintain an optimal balance between detection accuracy and alert noise.
4. Handling Encrypted & Obfuscated Email Content
Challenge: Encrypted or partially obfuscated content limits visibility and can hide attack indicators without safe handling techniques.
Solution: We design metadata inference models and behavior-driven scoring that detect suspicious patterns without decrypting sensitive content, maintaining both privacy requirements and detection quality.
5. Correlating Multi-Source Signals for Threat Detection
Challenge: Email threats often overlap with identity events, cloud activity and third-party access, making detection fragmented.
Solution: We build a cross-channel correlation layer that merges email metadata, authentication logs and historical interactions to uncover multi-step threats not visible in isolated data streams.
Revenue Model of Abnormal-like AI Email Threat Detection Tool
An Abnormal-like AI email threat detection tool generates revenue through subscription plans, tiered licensing, and enterprise services while ensuring continuous updates and support. These are some common monetization strategies to include in the solution.
1. Subscription-Based SaaS Licensing
The platform operates on recurring monthly or annual subscriptions, typically priced per user or per mailbox. This model ensures predictable revenue while giving customers continuous access to AI-driven threat detection, behavioral analysis and automated remediation capabilities.
2. Usage-Based or Consumption-Based Billing
Enterprises with large email volumes may prefer billing based on email throughput, processed events or anomaly evaluations. This aligns cost with operational scale and supports organizations handling massive telemetry and high-volume communication flows.
3. Enterprise Licensing & Long-Term Contracts
Larger companies often choose multi-year licenses that include onboarding guidance, dedicated support and customized behavioral AI tuning. These high-value contracts increase customer retention and offer predictable long-term revenue for the platform provider.
4. Professional Services & Integration Fees
Revenue is also generated through services like custom workflow design, SOC integration, environment-specific model training and advanced deployment assistance. These professional offerings increase customer success while creating a steady service-based income channel.
Conclusion
Building an email security solution of this nature requires more than detecting obvious threats. It involves understanding behavioral patterns, training models on evolving attack vectors, and aligning detection logic with real business communication flows. An Abnormal-like AI Email Threat Detection Tool succeeds when it balances accuracy, adaptability, and explainability. From data pipelines to model governance and alert workflows, every layer matters. If you are considering this path, the focus should remain on reducing false positives while strengthening real-time protection that security teams can trust and act on with confidence.
Build Your AI Email Threat Detection Tool with IdeaUsher!
At IdeaUsher, our team specializes in developing advanced AI-powered email security platforms that safeguard organizations from phishing, impersonation, business email compromise and socially engineered attacks. From behavioral baselining to dynamic risk scoring, we help you build solutions that rival industry leaders like Abnormal.
Why Partner with IdeaUsher?
- Deep Expertise in AI Security Engineering: We design intelligent email defenses powered by behavioral analytics, identity intelligence and anomaly detection.
- Custom Enterprise Solutions: Whether you need predictive threat modeling, automated remediation workflows or cross-channel correlation, we deliver platforms tailored to your security goals.
- Reliable Track Record: Our experience spans complex AI systems, cloud-native security products and high-performance enterprise applications.
- Scalable and Future-Ready: We architect solutions built for growth, ensuring your platform adapts as communication patterns and threat landscapes evolve.
Check out our portfolio to learn how our team brings complex ideas to life through high-quality, user-focused development.
Contact IdeaUsher today for a free consultation and a customized development roadmap.
Work with Ex-MAANG developers to build next-gen apps schedule your consultation now
FAQs
An AI email threat detection tool must include behavioral analysis, NLP-based email parsing, anomaly detection, user behavior baselining, and real-time alerting to accurately identify phishing, spoofing, and socially engineered attacks.
Machine learning enables continuous learning from historical and real-time email data, helping the system detect subtle patterns, impersonation attempts, and evolving attack techniques that rule-based filters often fail to catch.
Training requires access to email metadata, message content, sender behavior history, user interaction patterns, and labeled threat data to build accurate models that distinguish legitimate communication from malicious intent.
Enterprises typically deploy such tools using secure API integrations with email providers, sandboxed processing environments, strict data privacy controls, and compliance-aligned logging to ensure minimal disruption and strong security posture.