Managing identity verification and risk checks can quickly become overwhelming for growing businesses. Teams often juggle manual reviews, scattered tools, and inconsistent processes that slow onboarding and increase compliance risks. These challenges are driving companies to adopt a Persona-like identity workflow automation platform that centralizes verification, risk checks, and decisioning into one seamless automated system.
Modern identity-automation platforms show how effective the process becomes when AI, document analysis, and customizable workflows work together. They help businesses verify users faster, automate approvals, flag suspicious activity in real time, and maintain compliance without adding operational strain. This unified approach creates a smoother experience for users and gives teams greater clarity and control.
In this guide, we’ll explore how to build a Persona-like identity automation platform, the core features it should include and how this platform works. As we have helped numerous enterprises launch their AI solution in the market, IdeaUsher has the expertise to build the identity automation platform with proper development process and the required technology stack to support secure and scalable identity workflows.
What is an Identity Workflow & Automation Platform, Persona?
Persona is an identity workflow and automation platform that enables businesses to verify, manage, and understand the users and businesses they interact with. It unifies document and biometric verification, liveness checks, database and watchlist screenings, KYB, risk signals, and case management into a single identity layer, helping companies build trust and stay compliant with global KYC, AML, and regulatory requirements.
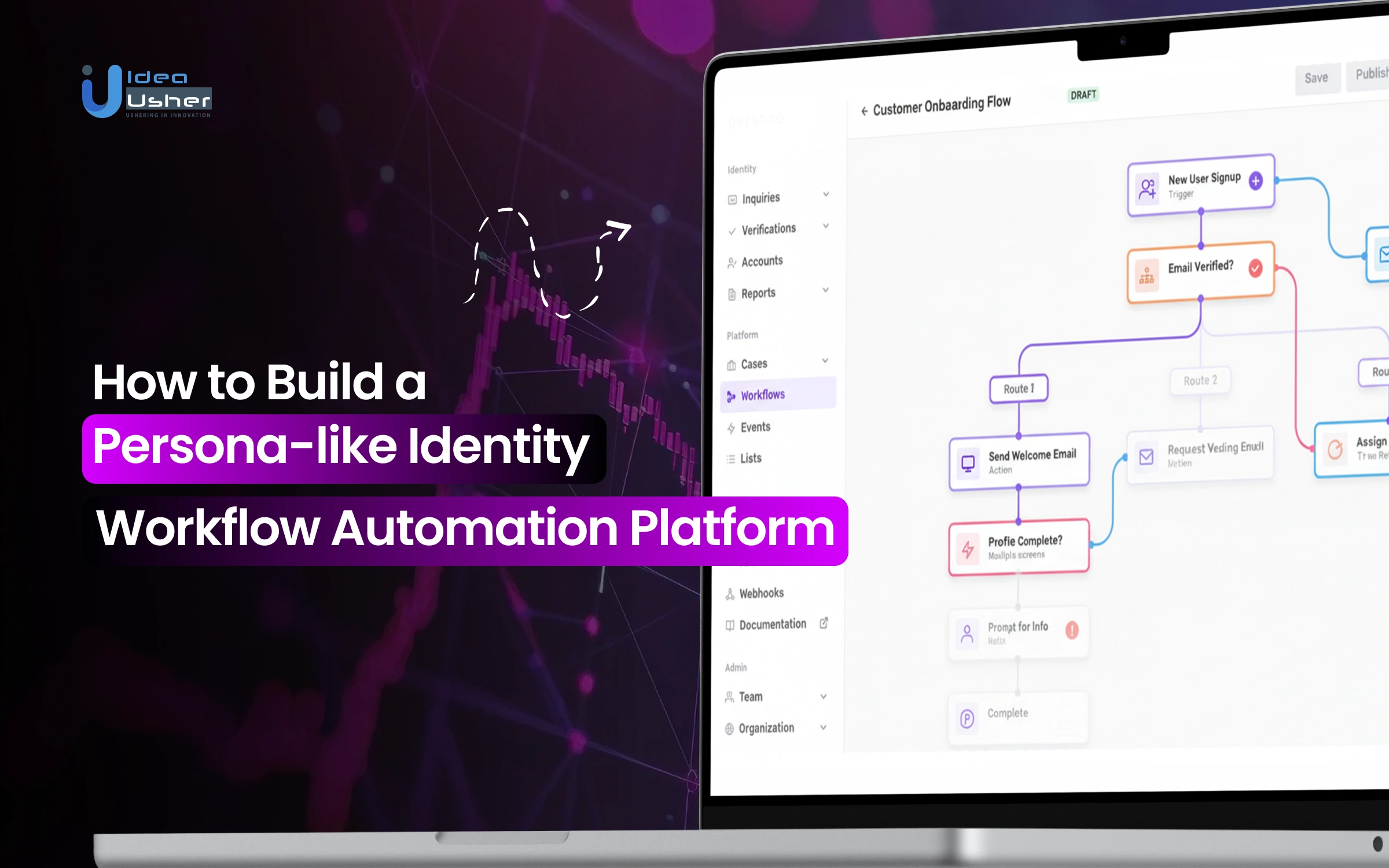
The platform’s modular architecture and workflow engine enable companies to automate identity processes throughout the customer lifecycle. Organizations can create risk-based flows, automate reviews, and integrate signals into onboarding and monitoring, all boosting efficiency, conversions, and fraud defenses.
- End-to-end identity operations, combining verification, fraud detection, risk analysis, and case management in one unified platform
- Fully configurable workflows with no-code and API-first tooling, enabling rapid iteration without engineering bottlenecks
- Dynamic, context-aware verification flows that adjust friction based on real-time risk and behavioral signals
- A unified identity graph that detects duplicates, synthetic identities, and networked fraud across users, devices, and businesses
- Global compliance coverage with built-in support for KYC, KYB, AML, sanctions screening, and age verification across regulatory regimes
A. Business Model
Persona operates as an API-first, identity-as-infrastructure platform, enabling companies to outsource verification, fraud prevention, and compliance workflows instead of building and maintaining them in-house.
- Persona offers cloud-based, API-first identity verification and management, serving businesses that need to onboard users or verify identities, including fintechs, marketplaces, gig-economy services, and companies handling KYC/KYB, age verification, compliance, and fraud prevention.
- Instead of a one-size-fits-all check, it provides a modular, customizable identity infrastructure, allowing clients to configure verification flows by use case, risk level, regulatory requirements, or fraud exposure.
- Automation and orchestration are core strengths: Persona’s workflow engine integrates identity verification, fraud & risk assessment, compliance, and lifecycle management directly into business processes, reducing manual workload and compliance overhead.
- With rising complexity from AI, bots, synthetic identities, and regulatory demands, demand for flexible “identity-as-infrastructure” solutions is growing, giving Persona broad, cross-industry and global market appeal.
B. Revenue Model
Persona uses a hybrid subscription + usage-based pricing model, allowing revenue to scale with customer growth, identity volume, and risk-management needs.
- Subscription / Tiered Pricing: Persona offers tiered plans based on size, usage, and features, such as the “Essential” plan starting at USD $250/month.
- Usage- or Volume-Based Fees: Beyond the base subscription, per-verification or per-service fees may apply when usage exceeds allocated limits.
- Customized Enterprise / Growth Plans: For large or complex clients, including multi-jurisdiction compliance, multi-product integrations, or high-volume workflows, Persona provides bespoke enterprise plans with custom pricing and premium support.
- Value from Infrastructure + Services + Support: Persona delivers full identity infrastructure including orchestration, compliance (KYC/KYB/AML), fraud detection, identity lifecycle management, and global regulatory support. This enables higher-value, long-term contracts rather than ad-hoc verification sales.
How Persona-like Identity Workflow Automation Platform Works?
A Persona-like identity workflow automation platform combines real-time verification, risk analysis, and compliance checks into one automated system. Here is a quick overview of how this API-first identity infrastructure handles end-to-end user processing.
1. User Onboarding and Data Collection
The process begins when users submit their basic information, ID documents, or biometric inputs. Behind the scenes, data normalization, OCR extraction, and signal gathering ensure the platform captures high-quality identity attributes for downstream verification and risk evaluation.
2. Document and Biometric Verification
Uploaded documents are analyzed through AI-assisted document parsing, pattern matching, and liveness assessment. Biometric inputs are compared against ID data to confirm authenticity. This stage verifies whether the user’s identity elements are genuine, consistent, and free from manipulation.
3. Risk Evaluation and Behavioral Analysis
The platform evaluates device fingerprints, geolocation, behavior patterns, and historical signals. A risk engine with anomaly analysis and adaptive scoring identifies suspicious traits such as synthetic identities, repeat fraud attempts, or unusual onboarding behavior.
4. Dynamic Workflow Routing
Based on risk level, users move through tailored verification paths. Low-risk applicants follow a streamlined flow, while high-risk users enter enhanced checks. Conditional logic and real-time decision triggers ensure friction adjusts intelligently to user behavior and trust signals.
5. Compliance Screening and Validation
The system automatically screens identities against sanctions lists, PEP databases, AML criteria, and age verification rules. Compliance engines map jurisdiction-specific requirements to ensure the user meets regulatory expectations before approval or escalation.
6. Case Review, Decisioning, and Lifecycle Management
If anomalies appear, a case is created for manual review. Investigators access organized evidence, risk insights, and AI-assisted triage suggestions. After approval or rejection, the user’s profile enters lifecycle monitoring for ongoing checks, fraud alerts, and identity health updates.
How Identity Workflow Automation Reduces 70% of the Onboarding Costs of Businesses?
The global identity verification market, valued at USD 9.87 billion in 2022, is projected to reach USD 33.93 billion by 2030, growing at a CAGR of 16.7%. This increase is driven by businesses replacing manual processes with automated solutions for cost savings and competitiveness.
An automated KYC process can reduce onboarding costs by over 70% and reduce turnaround time by as much as 90%, transforming customer acquisition from an expensive, slow bottleneck into a streamlined competitive advantage.
A. Elimination of Manual Review and Document Processing
Traditional identity verification relies on manual document review and database checks, which is labor-intensive and prone to errors. Identity workflow automation platforms use AI-powered verification to complete the process in minutes rather than days.
- Automated KYC cut onboarding costs by 60% and reduced verification time from days to under 5 minutes, showing how workflow automation removes manual handling, lowers compliance overhead, and accelerates approvals.
- Nearly 70% of financial institutions lost clients due to slow manual onboarding, highlighting how delayed verification directly erodes revenue and lifetime value.
- Over 81% of U.S. financial institutions adopted eKYC in 2024, with 64% adding biometrics, confirming automated identity workflows as the new industry standard.
- More than 45% of BFSI and e-commerce organizations adopted automated verification platforms, proving that scalable identity automation now delivers measurable value well beyond financial services.
B. Real-Time Orchestration Across Multiple Verification Sources
Identity workflow automation orchestrates verification across multiple data sources, APIs, biometric systems, and compliance databases simultaneously. This reduces verification from days to seconds, improves accuracy, and cuts false positives requiring manual checks.
- 90% of customers expect KYB platforms to deliver full fraud-detection and end-to-end orchestration, showing clear demand for automated multi-step identity workflows over manual point tools.
- Advanced biometrics cut onboarding time by 55%, driving higher conversions, lower abandonment, and smoother customer experiences.
- AI adoption in compliance jumped to 82% from 42% in one year, signaling rapid uptake of automated, decision-driven identity orchestration.
- Manual monitoring takes 328 days to detect credential breaches, while automated identity workflows flag anomalies in real time, reducing detection to minutes.
- AML compliance costs drop by 60% with smart automation, thanks to orchestrated checks and targeted escalation to analysts.
- KYC industrialization cuts onboarding time by up to 40% and reduces false positives, freeing analysts to focus on true risks.
Use Cases of Identity Workflow Automation Platform Across Industries
Identity workflow automation platforms are transforming how industries verify users, detect fraud, and manage compliance with greater speed and accuracy. Below are the top industry-specific use cases where automated identity infrastructure delivers measurable impact.
1. Fintech
Fintech platforms use automated identity workflows to verify customers, run KYC and AML checks, and evaluate fraud risk during onboarding. Adaptive risk scoring and real-time verification help maintain compliance while improving approval speed and user experience.
Real-World Example: Revolut processes over 2M monthly applications across 35+ countries, completing KYC in under 5 minutes with 85% automation, preventing $150M+ fraud annually through biometrics, AML screening, and real-time risk scoring.
2. Marketplaces
Marketplaces verify buyers, sellers, and service providers to maintain platform trust. Automated ID checks, KYB validation, and behavioral risk analysis reduce scams, prevent duplicate accounts, and ensure safe transactions for all participants.
Real-World Example: Airbnb verifies 4M+ users yearly with 99.4% fake-account detection, validating 150+ global ID types and cutting host verification time to 24 hours, reducing scams by 67% and boosting booking conversions.
3. Digital Health
Digital health platforms use identity automation to authenticate patients, verify clinicians, and protect sensitive medical data. Compliance-aligned workflows and document verification support secure telehealth sessions, prescription approvals, and patient onboarding.
Real-World Example: Teladoc automates credentialing for 93,000+ providers, cutting processing time from 120 days to under 10, performing 23 checks across 50+ databases with 99.8% compliance and continuous license-monitoring alerts.
4. Payments
Payment providers rely on identity workflows to screen users, detect transaction anomalies, and block fraudulent activity. Device intelligence and dynamic verification steps ensure safe payments while keeping friction low for legitimate customers.
Real-World Example: Stripe verifies 100,000+ merchants monthly, approves 95% low-risk cases in 10 minutes, blocks $1B+ fraud yearly, and analyzes 1,000+ risk data points per applicant while maintaining a low 3.2% false-positive rate.
5. Cryptocurrency
Crypto exchanges and Web3 platforms use automated KYC, AML screening, and sanctions checks to meet strict global regulations. Risk-adaptive verification flows help detect illicit activity and prevent identity abuse without slowing down onboarding.
Real-World Example: Coinbase serves 110M+ users, completing basic KYC in 3–5 minutes with 78% automation, screening against 500+ sanctions lists and monitoring 500M+ transactions monthly, reducing compliance costs by 60%.
6. Public Sector
Government services adopt identity automation to authenticate citizens, manage digital applications, and secure access to public benefits. Robust identity proofing and continuous verification reduce fraudulent claims and streamline service delivery.
Real-World Example: GOV.UK Verify authenticates 5M+ citizens for 23 services in 7 minutes, achieving 98.7% identity-match accuracy, preventing £140M+ fraud, and cutting verification costs by £60 per user.
8. Financial Institutions
Banks and credit unions use identity workflows for customer onboarding, loan processing, and ongoing monitoring. Automated compliance checks and fraud detection ensure regulatory adherence while accelerating account opening and approval decisions.
Real-World Example: HSBC automates onboarding in 64 markets, reducing account creation to 3 minutes, performing 45+ compliance checks, cutting verification costs by 75%, and lowering abandonment rates from 45% to 12%.
9. E-learning
E-learning platforms verify learner identities for enrollment, assessment integrity, and exam security. Document checks and biometric validation prevent impersonation and ensure credibility in remote education environments.
Real-World Example: Coursera verifies 12M+ learners, conducts 2M+ proctored exams yearly, achieves 99.1% authentication accuracy, blocks 25,000+ impersonation attempts, and completes pre-exam checks in under 3 minutes.
10. Higher Education
Universities leverage identity automation to confirm student admissions, grant campus access, and validate financial aid applications. Centralized verification workflows streamline administrative tasks and enhance institutional security.
Real-World Example: Arizona State University (ASU) processes 15,000+ international credentials yearly, reducing admission verification from 8 weeks to 14 days, detecting 1,200+ fraudulent submissions, achieving 96.5% accuracy, and saving $2.5M annually.
Key Features Required in a Persona-like Identity Workflow Automation Tool Development
Building a Persona-like identity workflow automation platform requires robust features that streamline identity verification and enhance user trust. These key features must be included to succeed in the competitive digital identity market.
1. AI-Adaptive Verification Flows
The platform enables teams to design tailored identity journeys using a visual builder powered by AI-assisted orchestration and context-aware routing. Dynamic rules adjust verification depth based on behavioral signals, user intent, and risk level, ensuring adaptable flows for diverse onboarding scenarios.
2. Global AI Document Verification Library
A robust library validates global IDs using AI-driven document classifiers, structured extraction, and security-feature inspection. The system analyzes microprint, layout consistency, and forensic visual cues to deliver highly accurate authenticity checks across international identity formats and environmental variations.
3. Biometric & AI-Enhanced Liveness Checks
The platform verifies user identity through machine-learning facial embeddings, geometric alignment, and intelligent similarity scoring. Liveness detection uses AI-based texture modeling, depth analysis, and micro-movement verification to prevent spoofing, deepfakes, and synthetic submissions with strong real-user confirmation.
4. AI-Powered Risk & Watchlist Screening
Risk screening matches users against PEP, AML, sanctions, and fraud datasets using AI-enhanced entity resolution, fuzzy matching, and pattern correlation. Integrated adverse-media signals strengthen detection of high-risk individuals and support compliant onboarding across global regulatory frameworks.
5. Automated Workflow Orchestration & Intelligent Decisioning
AI-driven automation engines run verification steps and evaluate business rules through adaptive decision models. Conditional scoring determines when to approve, reject, or escalate identities, reducing manual workloads and enabling scalable, consistent, and intelligence-led identity operations across high-volume environments.
6. AI-Assisted Case Management
A centralized dashboard supports analysts with AI-prioritized case queues, evidence correlation, and audit-ready trails. Machine-assisted insights highlight anomalies or inconsistencies, improving review accuracy and enabling faster resolution of complex verification scenarios and fraud-related investigations.
7. AI Data Enrichment
The platform enriches identity data using external registries, fraud-intelligence sources, and AI-interpreted enrichment signals. It merges supplemental attributes with verification outcomes to improve confidence scores, reduce false positives, and strengthen risk assessment across diverse identity workflows.
8. AI-Backed Phone and Email Verification
Ownership of phone numbers and email addresses is confirmed through AI-backed reputation scoring, multi-channel OTP checks, and carrier intelligence. The system analyzes disposable patterns, spoof indicators, and cross-signal anomalies to strengthen identity assurance and minimize fraudulent contact information.
9. Advanced Digital ID & NFC Verification
Support for mobile driver’s licenses and NFC-enabled IDs uses cryptographic validation, chip-data parsing, and secure-element checks. AI-driven anomaly detection identifies inconsistencies within digital identity structures, ensuring strong authenticity for next-generation identity credentials.
10. Privacy & Compliance Controls
The platform safeguards data with AI-assisted access monitoring, encrypted handling, and structured audit logs. Automated compliance checks maintain alignment with regional privacy rules, consent governance, and reporting requirements, making the system enterprise-ready for regulated industries.
How to Build a Persona-like Identity Workflow Automation Platform?
Building a Persona-like identity workflow automation platform combines identity verification, fraud detection, and compliance orchestration in a cloud-based system. This is the estimated structure our developers follow to build your scalable, API-first identity infrastructure.
1. Consultation
We begin by understanding client onboarding flows, fraud exposure, compliance duties, and identity challenges. This helps us define workflow expectations, risk thresholds, and automation needs. We also identify where AI-driven verification or risk insights can significantly enhance trust and reduce friction.
2. Requirements Analysis
Our developers analyze functional, regulatory, and operational requirements to shape identity controls and data flows. We map verification paths, risk signals, and decision points while determining where machine learning insights, behavioral patterns, or passive signals may improve fraud detection and accuracy.
3. Workflow Architecture Design
We design a modular workflow architecture that supports configurable identity steps and adaptive routing. This architecture enables dynamic flows that respond to real-time risk signals or AI-detected anomalies, ensuring friction adapts naturally to user behavior.
4. Verification Logic Design
We plan the logic that guides document checks, biometric comparisons, liveness steps, and business verifications. Our approach incorporates AI-assisted document understanding and face-matching, improving accuracy across varied ID formats and user environments.
5. Risk Engine Development
We build a configurable risk engine that evaluates device signals, behavior patterns, velocity anomalies, and identity inconsistencies. Machine learning models help surface unusual activity and refine scoring, strengthening defenses against synthetic identities and coordinated fraud.
6. Workflow Automation Layer
We create an automation layer that executes identity decisions, triggers escalations, and synchronizes results across systems. AI-supported insights assist with routing high-risk cases and automating repetitive evaluations, ensuring faster and more consistent trust decisions.
7. Case Management System Design
We design an integrated case management system aligned with the investigator’s needs. It supports audit trails, notes, and evidence review. AI-assisted triage highlights risky attributes and significant anomalies, helping teams resolve complex cases efficiently.
8. Compliance Rule Integration
We integrate configurable rules for KYC, KYB, AML, sanctions, and age verification across jurisdictions. Adaptive compliance logic ensures workflows evolve with regulatory changes, reducing ongoing maintenance for identity teams.
9. Testing & Validation
We validate workflows, rules, and verification paths through scenario simulations and edge case testing. Testing also confirms that AI-driven components remain accurate, stable, and fair, ensuring consistent automated decisions across different risk profiles.
10. Deployment & Iteration
Once deployed, we monitor performance, automation behavior, and fraud detection quality. Continuous iteration refines identity logic and AI models, keeping the platform resilient against emerging threats, behavior shifts, and compliance updates.
Cost to Build a Persona-like Identity Workflow Automation Platform
The cost to build a Persona-like identity workflow automation platform depends on features like identity verification, fraud detection, and compliance automation. Understand the key factors that influence pricing for a scalable, API-first identity workflow solution.
| Development Phase | Description | Estimated Cost |
| Consultation | Initial discovery, mapping needs, and defining core workflows and AI opportunities. | $4,000 – $8,000 |
| Workflow Architecture & Data Planning | Designing modular flows and scalable identity structures for automation. | $8,000 – $15,000 |
| Verification Logic & Document Processing Setup | Implementing ID checks, biometrics, and AI-assisted document extraction. | $16,000 – $32,000 |
| Risk Engine Development | Building rules, scoring methods, and ML-based anomaly detection. | $14,000 – $27,000 |
| Workflow Automation Layer | Creating automated routing, triggers, and real-time decisioning. | $12,000 – $16,000 |
| Case Management System | Designing tools for reviews with AI-guided triage. | $10,000 – $14,000 |
| Compliance Rule Integration | Embedding KYC, KYB, AML, and jurisdictional logic. | $5,000 – $10,000 |
| QA Testing | Ensuring workflow accuracy and AI component reliability. | $7,000 – $12,000 |
| Deployment & Optimization | Launching the platform and refining risk and automation performance. | $10,000 – $17,000 |
Total Estimated Cost: $65,000 – $126,000
Note: Development costs vary based on workflow complexity, regulatory depth, verification volume, and AI-powered fraud detection sophistication. Custom integrations and continuous optimization may also influence total investment.
Consult with IdeaUsher for a personalized cost estimate and a tailored roadmap to build a high-performing identity automation platform aligned with your security, compliance, and workflow goals.
Cost-Affecting Factors During Development
Key factors affecting the cost of a Persona-like identity workflow automation platform include features, scalability, integrations, and regulatory compliance requirements.
1. AI Complexity & Intelligence Layer
Costs rise when implementing ML-driven risk scoring, anomaly detection, or AI-assisted document understanding. Higher intelligence layers demand additional training, tuning, and validation to ensure reliable performance.
2. Compliance & Regulatory Coverage
Supporting multiple jurisdictions and industry-specific rules requires dedicated compliance logic and testing. More regions, more documentation standards, and more regulatory workflows increase development effort.
3. Workflow Customization Requirements
Extensive workflow personalization and dynamic routing logic add complexity. The more granular the decision paths and exceptions, the higher the engineering hours needed to build and test them.
4. System Integrations & Data Sources
Integrating CRMs, payment systems, risk databases, or third-party signals adds development overhead. Each custom integration point requires alignment, mapping, and additional QA cycles.
5. Security & Data Protection Measures
Implementing strong encryption, auditability, and secure data handling adds cost. Enhanced privacy safeguards and strict access controls require additional configuration and review.
Challenges & How Our Developers Will Solve Those?
Developing a Persona-like identity workflow automation platform comes with challenges around security, scalability, compliance, and fraud prevention. Here are the key hurdles and practical solutions for building a reliable, high-performance identity infrastructure.
1. Fragmented Identity Data Across Multiple Sources
Challenge: Identity signals often sit in separate systems, making it difficult to create a unified and trustworthy profile that supports accurate verification and strong fraud analysis.
Solution: We consolidate documents, biometrics, device intelligence, and risk attributes into a structured identity layer. This unified identity model strengthens verification accuracy while enabling deeper fraud insights, duplicate detection, and consistent decisioning across every workflow stage.
2. Detecting Evolving Fraud Tactics
Challenge: Fraudsters change methods frequently, introducing synthetic identities, spoof attempts, and new behavior patterns that traditional rules cannot consistently detect.
Solution: We build adaptive rule sets supported by pattern recognition and anomaly analysis. Our approach evolves with fraud trends and strengthens detection by monitoring behavioral signals, device usage, and identity inconsistencies in real time.
3. Maintaining Accuracy in Document and Biometric Verification
Challenge: Document quality, lighting conditions, image variation, and inconsistent ID formats often create errors in document checks and biometric matching.
Solution: We layer document validation, biometric comparison, and liveness signals with contextual checks. Our multi-step verification logic improves accuracy across diverse ID types while reducing false declines during identity onboarding.
4. Keeping AI Models Ethical, Fair, and Stable
Challenge: AI-driven checks risk model drift, biased outputs, or inaccurate decisions when not monitored consistently.
Solution: We evaluate model outcomes, track drift indicators, and provide transparent rules for decision-making. Our fairness checkpoints support responsible identity assessments, improving trust and compliance readiness.
5. Building Dynamic and Adaptable Workflows
Challenge: Static identity flows cannot react to changing user behavior or varying risk levels, which limits verification flexibility.
Solution: We design workflows with conditional logic and real-time triggers that adjust steps based on risk signals. Adaptive flow routing enhances accuracy while ensuring smoother user journeys for low-risk individuals.
Conclusion
Building an online identity verification platform that delivers accuracy, speed, and user trust requires a careful blend of advanced verification workflows, strong security practices, and compliance readiness. As you plan the structure of your solution, you can see how essential it is to balance automation with robust fraud prevention. An online identity verification platform becomes truly effective when it offers reliable checks, seamless onboarding, and scalable architecture that adapts to new threats. With the right approach, creating a secure and efficient verification experience becomes achievable for any growing business.
Why Choose IdeaUsher for Your Identity Workflow Automation Platform Development?
At IdeaUsher, we specialize in building secure, scalable, and fully automated identity solutions that help businesses verify users, manage risk, and streamline onboarding workflows. Our team designs platforms that reduce manual checks, improve compliance accuracy, and support global verification standards.
Why Work With Us?
- Deep Identity Automation Expertise: We build workflow engines that unify KYC data, automate decision steps, and ensure smooth identity journeys across multiple verification providers.
- Custom-built Compliance Architectures: From KYB integrations to automated document checks, we deliver tailored systems that align with your industry’s regulatory needs.
- Proven Results in Fintech: Our work on platforms like JabaPay, a fintech app requiring secure user onboarding and identity validation, reflects our experience in building reliable verification-driven products.
- Scalable Infrastructure: We create architectures that support rapid user growth while maintaining accuracy, speed, and security across identity flows.
Explore our portfolio to see how we have supported businesses from accors industries in building AI solutions.
Reach out for a consultation, and we will help you design a robust Identity Workflow Automation Platform built for precision and long-term scale.
Work with Ex-MAANG developers to build next-gen apps schedule your consultation now
FAQs
Identity workflow automation replaces manual verification tasks with rule-based processes that handle KYC checks, document reviews, and risk evaluations. It reduces onboarding delays, improves accuracy, and allows compliance teams to scale operations more efficiently without increasing workload.
Automating identity workflows cuts labor expenses by removing repetitive manual reviews. It also lowers error rates, speeds up onboarding, and reduces compliance penalties. These improvements help businesses operate more efficiently while maintaining strict verification standards.
A strong identity workflow automation system uses OCR, liveness detection, AI-driven risk scoring, API orchestration, and secure data storage. These technologies work together to create a seamless onboarding process while ensuring regulatory compliance and fast decision-making.
Dynamic rules allow teams to adjust verification logic based on risk profiles, user types, or regional regulations. This flexibility helps businesses adapt quickly, maintain compliance, and ensure consistent decisions without rebuilding their entire onboarding system.