Capital markets were never slow because systems were outdated. They slowed down because coordination depended on too many manual approvals. Each transfer required trust across multiple intermediaries. As these inefficiencies mounted, security token platforms began to gain attention as a more structured alternative to traditional systems.
Blockchain mattered here because it could be programmed to enforce identity checks and role-based permissions. Transfer rules and jurisdiction controls could live directly inside the asset. Settlement could then happen predictably with governance and compliance enforced by design.
We’ve built many security token solutions powered by permissioned blockchain protocols and compliance automation. Drawing on years of expertise, we’re sharing this blog to outline the steps to develop a security token platform like Polymesh.
Key Market Takeaways for Security Token Platforms
Source: Fortune Business Insights
Security token platforms are gaining traction because they solve long-standing inefficiencies in traditional finance. They enable fractional ownership of assets, such as equity and real estate, provide near-continuous liquidity, and embed regulatory controls directly into smart contracts via standards such as ERC-3643.
Among leading platforms, Securitize and Tokeny stand out for institutional adoption. Securitize operates as an SEC-registered provider and is expanding toward a regulated tokenized stock exchange on Avalanche, planned for 2026, with EU regulatory alignment.
Tokeny, now part of Apex Group, focuses on modular, institution-grade tokenization and multi-chain deployment, supported by partnerships such as its collaboration with Security Token Network to streamline end-to-end STO issuance and governance.
What is the Polymesh Platform?
Polymesh is a purpose-built blockchain platform designed specifically for security tokens. It embeds identity verification, compliance rules, and role-based permissions directly at the protocol level so issuers and regulators do not rely on off-chain enforcement. This design enables assets such as equities, debt, and funds to be issued, traded, and settled on-chain, with built-in governance, jurisdiction controls, and regulatory alignment from day one.
Why Is Polymesh Different from Ethereum-Based Tokenization?
Polymesh differs because it is built specifically for regulated assets, whereas Ethereum is a general-purpose chain. Compliance and identity checks are enforced at the protocol level, preventing transfers from bypassing rules and significantly reducing institutional risk. If you are building security tokens, you can rely on predictable settlement and governance from day one.
1. Regulated Asset Focused Layer 1
This is the foundational difference. Ethereum was created as a general-purpose world computer. Polymesh was engineered as a financial jurisdiction, a sovereign digital environment with legal and regulatory requirements baked directly into its core protocol.
- Ethereum Approach: Let us create tokens on our existing computer.
- Polymesh Approach: Let us build a new computer specifically for regulated securities.
This architectural decision means every component of Polymesh, from consensus to transaction processing, prioritizes what financial institutions need, certainty, compliance, and institutional-grade security.
2. Protocol Level Compliance
Here is where the real shift happens. On Ethereum, compliance checks happen in smart contracts, code that can have bugs, be upgraded, or even bypassed. On Polymesh, compliance is embedded directly in the blockchain runtime.
What This Means in Practice
- Identity verification, such as KYC and AML, is mandatory for participation
- Transfer restrictions like geographic limits and investor accreditation are automatically enforced by the network
- Corporate actions such as dividends and voting are native functions, not add-ons
- There is no compliance bypass because the blockchain itself rejects non-compliant transactions
3. No Smart Contract Only Enforcement
This is one of the most important distinctions for risk-conscious institutions. On Ethereum, the entire compliance framework depends on the quality of smart contract code and the effectiveness of audits.
The Smart Contract Risk Reality
- A single bug in a Solidity contract can bypass compliance logic
- Upgradable contracts introduce governance and centralization risks
- Auditing complex financial logic is expensive and never perfect
- Even with strong contracts, the underlying chain remains anonymous and probabilistic
Polymesh Institutional Grade Solution
- No Single Point of Failure: Compliance is enforced across the validator set, not by one contract
- Mathematically Enforced Rules: Logic is implemented in the blockchain core using a Rust-based runtime
- Inherent Identity Layer: Every transaction is tied to a verified identity with no anonymous actors
- Deterministic Finality: Once a transaction settles, it is final with no chain reorganizations and clear legal certainty
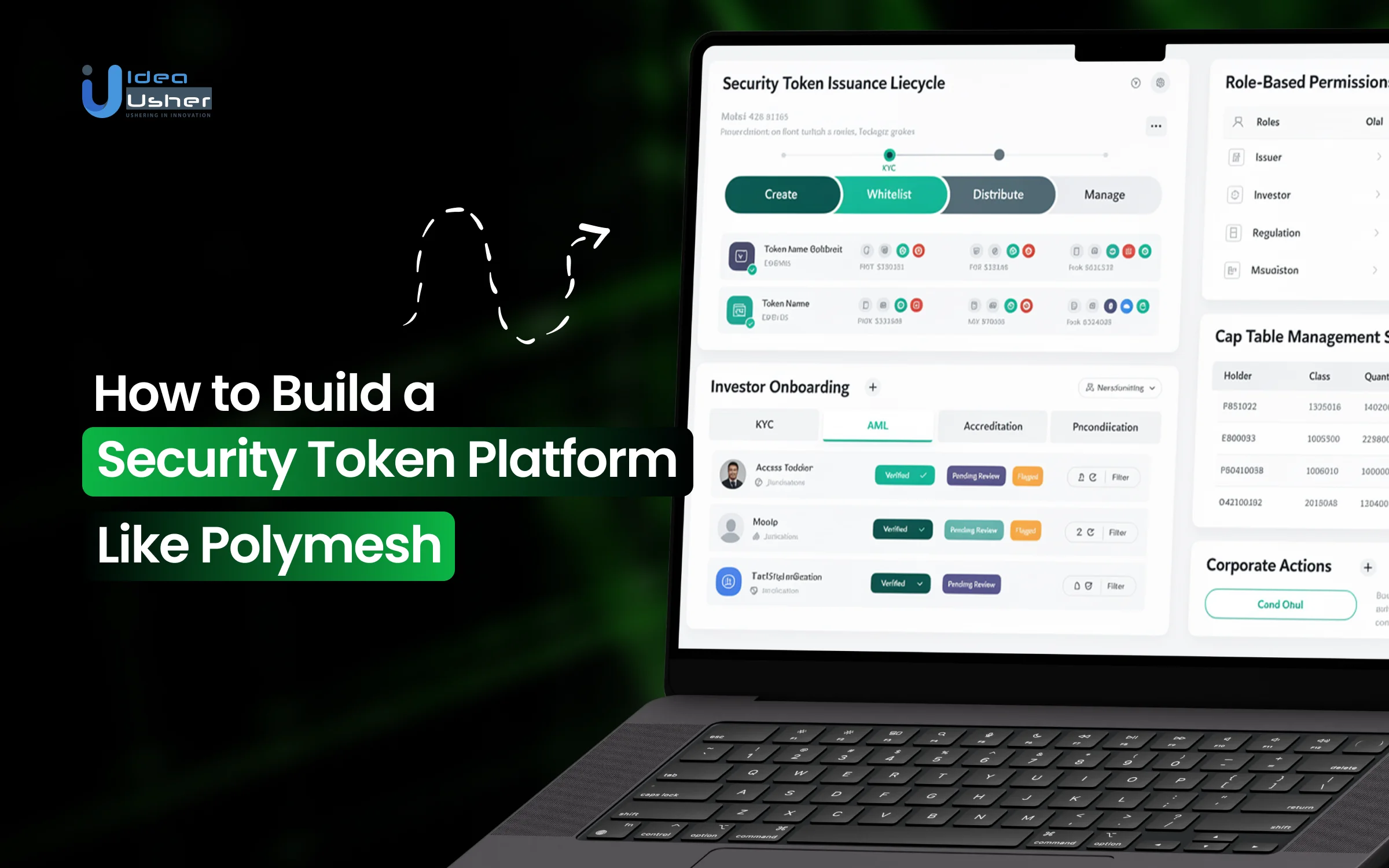
How Does the Polymesh Security Token Platform Work?
The Polymesh Platform works by making identity a prerequisite for any transaction, so every participant can act as a known, verified entity on-chain. Compliance rules can reside at the protocol level, so transfers should execute only when regulatory conditions are met and the transfer is secure.
1. The Foundation
On public blockchains, you start with a wallet. On Polymesh, you start with an identity.
Step 1: Becoming a Known Entity
Every participant, issuer, investor, or delegate must undergo verification by a Trust Anchor, a regulated third party such as a broker-dealer or law firm. This creates a decentralized identity, or DID, anchored in real-world credentials.
Step 2: The Identity Centric Ledger
Transactions are not just signed by a private key. They are authorized by a verified identity. This solves the anonymous counterparty problem that has hindered institutional blockchain adoption for years.
The Result: A permissioned network where every action is traceable to a legally accountable entity. This is not just a feature. It is the bedrock.
2. The Rulebook
Traditional platforms enforce rules through smart contracts, which are code that can have bugs. Polymesh enforces them at the protocol level.
How It Works:
- An issuer defines compliance rules using intuitive logic, such as requiring only accredited investors in the EU and the US or limiting the number of holders to 499.
- These rules are set directly into the asset’s on-chain compliance pallet, which is a core module of the blockchain.
- When a transfer is initiated, the protocol checks the rules before the transaction is even included in a block. If the recipient lacks the required credentials, the network rejects the transfer.
The Result: Automated and unbreakable compliance. Issuers gain real-time control without manual checks, and regulators gain assurance that the rules are enforced by the infrastructure itself.
3. The Privacy Layer
Public ledgers expose sensitive trading data. Polymesh uses Confidential Assets to balance privacy with transparency.
The P-DART Protocol:
| View Type | What Is Visible |
| Public View | Observers can see that a transaction occurred between two verified identities, but the asset type and transaction amount remain hidden. |
| Counterparty View | Participants in the transaction can view the full details relevant to their role. |
| Regulator View | Authorized auditors and compliance officers can use special decryption keys to access transaction details for regulatory oversight. |
The Result: Institutions can trade with operational privacy while maintaining the audit trail required for financial regulation. This balance was previously impossible on blockchain.
4. The Lifecycle Engine
Tokenization is not just about creating tokens. It is about managing them over years. Polymesh has this built in.
Automated Corporate Actions:
- Dividends: The protocol automatically calculates entitlements based on a snapshot date and distributes payments to thousands of verified holders.
- Voting: Shareholder votes are weighted by verified holdings and executed on chain with immutable records.
- Cap Table Management: The ownership ledger remains accurate and up-to-date, eliminating the need for manual reconciliation.
5. The Settlement System
Financial settlement requires certainty. Polymesh uses the GRANDPA and BABE consensus mechanism to provide deterministic finality.
The Process:
A valid transaction is proposed; once validated, it can be finalized instantly on-chain. The settlement cannot be reversed or altered, which means execution should remain legally and technically final. This enables settlement at T+0 and significantly reduces counterparty risk in high-value financial transactions.
The POLYX Token: Fueling the Ecosystem
The native POLYX token is designed for utility within a regulated environment rather than speculation.
- Staking: Token holders stake POLYX to secure the network using Nominated Proof of Stake.
- Governance: Stakeholders vote on protocol upgrades, enabling stable and fork less evolution.
- Fees: POLYX is used to pay for transaction fees, asset creation, and compliance rule updates.
What is the Business Model of the Polymesh Security Token Platform?
Polymesh is a permissioned Layer-1 blockchain designed for security tokens and real-world assets. It focuses on governance identity, compliance, confidentiality, and settlement. Its business model centers on enabling regulated asset tokenization through the POLYX utility token, with fees and staking supporting long-term sustainability.
Transaction and protocol fees
Paid in POLYX for on-chain actions such as transfers, ticker reservations, and native protocol functions. Fees scale with transaction size and complexity and are partially governed by the Polymesh Governing Council.
Staking rewards distribution
New POLYX is minted daily, with inflation capped at 14 percent annually until the total supply reaches 1B, then limited to 140M per year. Rewards are distributed to node operators and stakers, with a target staking ratio of 70%.
Ecosystem incentives
Companies and developers earn POLYX through integrations, tokenization services and ecosystem grants. Support includes a 10M USD Ecosystem Development Fund and a 50M POLYX Grants Program.
Funding History
The platform received a major grant on Feb 1 2022, raising 115M USD from undisclosed investors. This single round accounts for the entire funding raised to date and supported the early development of the network, founded in 2021 in Zug, Switzerland.
In addition to core funding, a 10M USD Ecosystem Development Fund was launched in 2022. This fund is dedicated to supporting builders’ integrations and long-term protocol growth across the ecosystem.
How to Build a Security Token Platform Like Polymesh?
To build a security token platform like Polymesh, you should start by designing compliance and identity at the protocol level rather than adding them later. The system must automatically enforce transfer rules, investor eligibility, and settlement logic to ensure every transaction is predictable and legally compliant.
We have built multiple security token platforms similar to Polymarket, and this is the approach we follow.
1. Regulatory Mapping
We start by analyzing applicable securities regulations and translating them into system-level constraints. This ensures transfer rules, investor eligibility, and reporting obligations are enforced by the protocol itself rather than through manual oversight.
2. Identity Layer Design
We implement a protocol-level identity system that integrates DID frameworks with KYC and AML providers. Each on-chain account is mapped to a verified real-world entity, enabling compliance decisions to be made automatically during transactions.
3. Compliance Rules Engine
We build a native rules engine that evaluates transfers in real time based on jurisdiction, identity attributes, and issuer-defined policies. This approach avoids fragmented contract logic and allows compliance parameters to evolve without redeployments.
4. Confidential Transactions
We integrate privacy-preserving transaction models using zero-knowledge proofs. Sensitive data remains confidential, while the protocol continues to demonstrate regulatory compliance and supports selective disclosure to auditors and regulators.
5. Deterministic Settlement
We design settlement infrastructure with finality guarantees and no-fork governance. This ensures ownership transfers are irreversible, legally reliable, and aligned with institutional settlement expectations.
6. Asset Lifecycle Automation
We automate dividends, governance voting, and ownership tracking through on-chain workflows. Cap tables and historical records are continuously updated, giving issuers a clear, auditable view of the asset lifecycle.
What Happens if a Participant Fails Compliance After Already Holding Assets?
If a participant fails to comply after holding assets, the platform will typically freeze transfers immediately to protect regulatory integrity. The investor may still retain economic rights, but they cannot trade until re-verification is completed.
If compliance is not restored within the allowed window, the system can automatically enforce a controlled exit in accordance with the legally agreed terms.
Triggers for Post-Issuance Compliance Failure
A participant can become non-compliant in several key ways.
- KYC or AML expiry or rejection: Identity verification from providers such as Onfido or Jumio may expire or be rejected during periodic re-screening due to new sanctions or risk flags.
- Loss of accreditation status: An accredited investor in the United States may no longer meet income or net worth thresholds after a financial event.
- Jurisdictional reclassification: An investor may relocate to a jurisdiction where holding that specific security token is no longer permitted.
Security token platforms are designed to handle these scenarios automatically and usually escalate enforcement in clearly defined stages.
1. Immediate Transfer Freeze The Soft Lock
The moment a compliance failure is detected by the identity oracle or registry, the participant’s status is updated on-chain.
Action: A smart contract that implements standards such as ERC-3643 imposes a transfer freeze on all tokens held by that wallet address. The investor continues to legally own the asset and retains economic rights such as dividend entitlement, but cannot sell, transfer, or pledge the tokens.
Real World Mechanism
This is enforced by the token’s canTransfer function returning false for any transaction originating from the non-compliant wallet. Platforms such as Tokeny and Securitize embed this logic directly into their base token contracts.
User Experience: The investor logs into the dashboard and sees a clear notification stating that re-verification is required and trading is temporarily disabled.
For example, in Securitize, DS Protocol tokens embed compliance logic at the contract level. If an investor’s KYC credential expires within the connected identity registry, the smart contract automatically restricts transfers.
Dividend distribution remains unaffected, but any transfer attempt is reverted, effectively placing the tokens in a compliance lock until verification is restored.
2. The Grace Period and Remediation Path
Regulatory frameworks require that investors be given a lawful opportunity to resolve compliance issues.
Action: The platform notifies the investor and, typically, the issuer or administrator, and initiates a predefined grace period, such as 30 to 90 days.
Process: If the investor completes re-verification or restores accreditation within the allowed window, the on-chain credential is renewed, and the transfer restriction is automatically lifted by the smart contract.
3. Forced Exit or Cooling Off Sale
If remediation fails within the grace period, the platform must enforce an outcome that preserves the legality of the offering.
Action: The smart contract enables a mandatory redemption or forced sale mechanism, governed by a multi-signature wallet controlled by the issuer, the compliance officer, and the licensed transfer agent.
The Forced Sale Process
- The administrator triggers a forceSell function targeting the non-compliant wallet and the affected tokens.
- The tokens are transferred into a controlled escrow contract.
- The platform matches the tokens with a compliant buyer at market price or a predefined fair value based on NAV or appraisal.
- An atomic transaction completes where tokens move to the new buyer and proceeds in stablecoins are sent to the original investor after applying any contractual fees or penalties.
Legal Foundation
This mechanism is explicitly defined in the STO purchase agreement and the SPV or issuer operating agreement. The investor is not experiencing asset seizure but the execution of a pre-agreed contractual obligation.
4. Administrative Burn and Re-Issue
This stage addresses situations such as permanent non-compliance or provable loss of wallet access.
Action: After legal verification, such as court orders, notarized declarations, or estate documentation, the administrator executes a burnAndReissue function using a recovery multi-signature process.
Process
The stranded tokens are permanently burned and an equivalent number of new tokens are minted to a newly verified wallet. Total supply and cap table integrity remain unchanged, ensuring legal ownership continuity.
For example, Polymath’s Token Studio supports a recovery module within its ST 20 security token standard. When private keys are irrecoverably lost, a predefined group of administrators must jointly authorize the recovery transaction.
Tokens are burned and reissued without introducing unilateral control, preserving institutional-grade governance and auditability.
How Security Token Platforms Ensure Legal Enforceability in Court?
A security token platform keeps assets enforceable by tying each token to legal rights inside a regulated entity that courts already recognize. The on-chain ledger may be contractually defined as the official record of ownership, while administrators may lawfully act on court orders when required.
1. The Legal Wrapper
This is the non-negotiable legal core. The real-world asset is transferred into a bankruptcy-remote legal entity, such as an LLC, LP, or trust.
How it creates enforceability.
The SPV’s Operating Agreement or equivalent charter is the supreme governing document. It is explicitly amended to state that:
- Ownership of the SPV is represented by digital tokens on a specified blockchain.
- The on-chain ledger maintained by the smart contract is recognized as the official register of beneficial ownership.
- Token holders are granted shareholder or member rights as outlined in the agreement, including voting and profit distribution.
Court admissible evidence.
In a dispute, the plaintiff presents the court-verified Operating Agreement alongside a forensically extracted snapshot of the blockchain ledger proving token ownership at a specific block height. This directly links the defendant’s digital wallet to their legal rights in the SPV.
2. Golden Record Synchronization
A platform must have a clear process for resolving discrepancies between the blockchain ledger and the legal registry.
The enforceability mechanism.
The legal documents authorize a licensed administrator, often a regulated transfer agent, to reconcile records. This is executed through a governed smart contract function such as reconcileCapTable.
Example process.
If a court orders an ownership transfer due to divorce, inheritance, or judgment, the administrator, upon receiving the sealed court order, uses a multi-signature wallet to execute a forcedTransfer or burnAndReissue function.
This action updates the blockchain to reflect the legal reality, and the court order itself provides the audit trail. Platforms like Polymath and Securitize build these administrator controls into their core protocol.
3. Smart Contracts as Executable Legal Code
Smart contracts are not just software. They are the technical embodiment of the legal agreement’s covenants.
How it holds up in court.
A well-drafted smart contract’s code for dividend distribution, for example, can be presented as digital evidence of the issuer’s binding promise.
- If the code executes as written, it demonstrates fulfillment of the contract.
- If it fails due to a bug, the code, its audit reports, and the associated legal offering memorandum constitute evidence of a breach of contract or negligence claim.
Integration with oracles.
To ensure enforceability in real-world settings, such as distributing 80% of audited net profits, platforms integrate legal oracle services.
These are trusted, regulated entities, such as audit firms, that cryptographically sign data before it is submitted on-chain to trigger contracts. This creates a verifiable link between audited financial statements and on-chain actions.
4. Identity Linkage
A wallet address must be inextricably linked to a verified legal identity for any judgment to have meaning.
The KYC and AML anchor
Every investor’s wallet is tied to their legally verified identity through mandatory onboarding. This KYC data is stored off-chain by a licensed provider but is referenced on-chain via a verifiable credential.
Court order enforcement
If a court needs to freeze or seize assets, it does not order the seizure of tokens from a wallet address. It issues an order to the licensed platform administrator to freeze the assets of a named legal person.
The administrator, bound by law to comply, then uses the governed smart contract’s privileges to freeze the tokens in the wallet associated with that verified identity.
This mirrors how a judge orders a traditional broker to freeze a stock account.
5. Audit Trails and Cryptographic Proof
The blockchain provides an immutable, time-stamped record that is stronger than traditional databases in court.
Admissible evidence
Every transfer, vote, and dividend payment is permanently recorded. A platform can provide cryptographic proof of ownership history using Merkle proofs that are nearly impossible to falsify. This serves as powerful evidence in disputes over ownership history, transaction timing, or participation in corporate actions.
Example
In a dispute between two parties claiming ownership of tokens, a forensic blockchain analysis can irrefutably trace the chain of custody from issuance to the current holder, as validated by the network’s consensus.
Conclusion
Security token platforms like Polymesh show where compliant digital finance is heading. For enterprises, this is not about launching another chain but about building regulated financial systems institutions can realistically trust. With the right architecture and a compliance-first approach, a business can steadily unlock new asset classes, revenue models, and access to global markets with far less friction.
Looking to Develop a Security Token Platform like Polymesh?
IdeaUsher helps you build a security token platform like Polymesh with compliance engineered at the core. Our team can design protocol-level identity controls, asset logic, and settlement flows to ensure the system behaves predictably under regulatory requirements.
With over 500,000 hours of coding experience and a team of ex-MAANG and FAANG developers, we build purpose-driven financial infrastructure that goes beyond general-purpose blockchains.
- Identity is built-in, not bolted on — every participant is verified, eliminating anonymous counterparty risk
- Compliance is protocol-level — rules execute automatically, reducing legal exposure and audit complexity
- Trades stay private yet remain fully auditable by regulators via zero-knowledge technology
- Settlement is legally final — no rollbacks, no forks, just T+0 certainty
Work with Ex-MAANG developers to build next-gen apps schedule your consultation now
FAQs
A1: Platforms like Polymesh embed identity and compliance directly into the protocol itself. This means rules are enforced by the network rather than added later through contracts. It can make compliance more predictable and harder to bypass.
A2: This type of platform typically suits startups that plan to operate in regulated markets. It may suit teams with strong enterprise backing or long-term infrastructure goals. Smaller experiments could feel constrained by the upfront compliance effort.
A3: Development often takes between six and twelve months, depending on the scope. Regulatory coverage integrations and security reviews usually drive the timeline. A phased rollout may help validate the platform earlier.
A4: These platforms are designed to be asset-agnostic at the core. They can support equities, debt, real estate funds, and structured products through standardized token models. This flexibility helps institutions scale across markets.