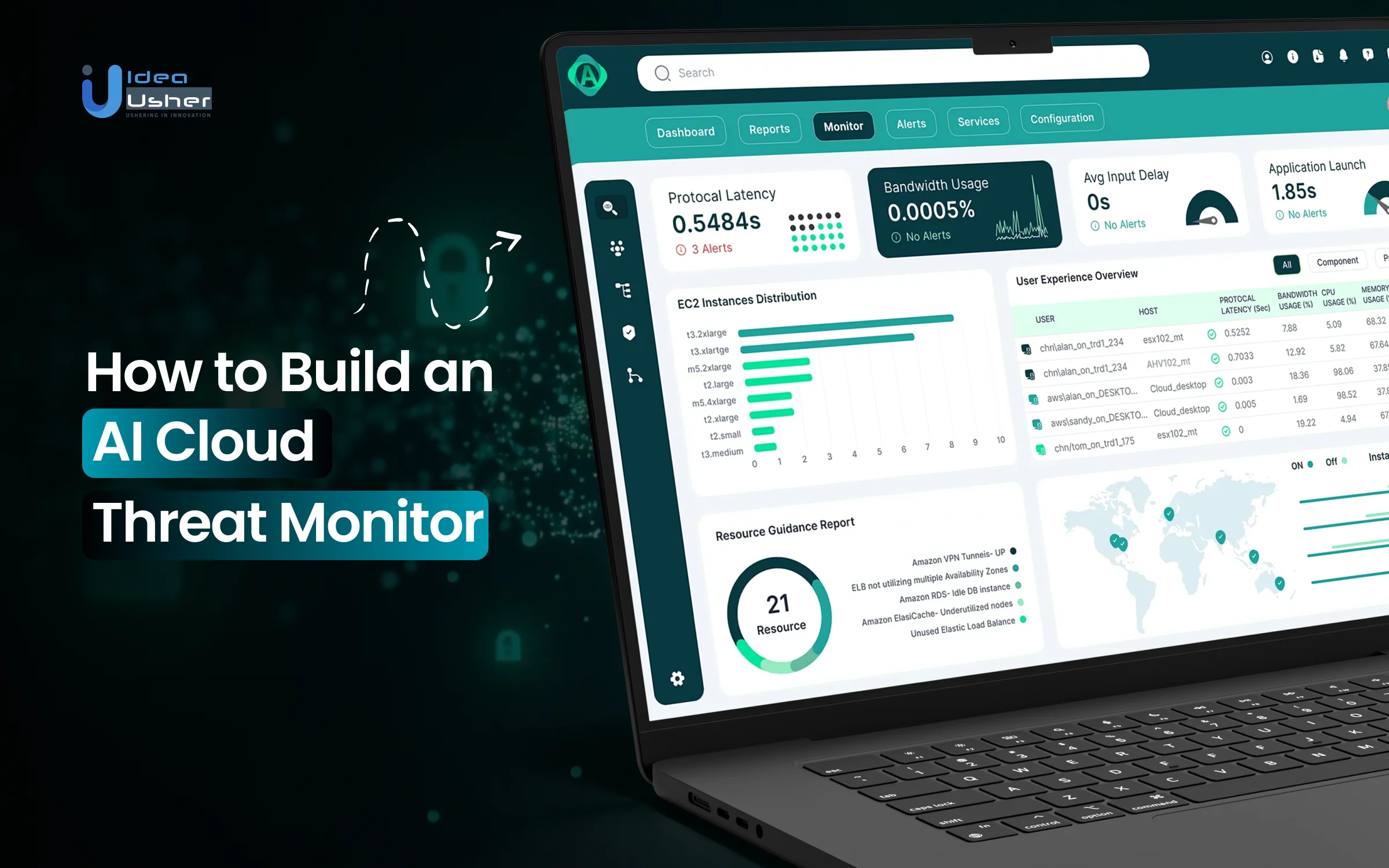
As more businesses move their infrastructure to the cloud, keeping track of security risks becomes increasingly complex. Misconfigurations, unusual access patterns, and silent intrusions can easily slip through traditional monitoring tools, especially in fast-changing cloud environments. These challenges are driving organizations to adopt an AI cloud threat monitor tool that can continuously watch for anomalies and detect threats in real time.
AI-powered cloud security solutions bring together behavioral analysis, machine learning, and real-time visibility to protect modern cloud systems. By learning normal usage patterns across workloads, users, and services, these platforms can flag suspicious behavior early and help teams respond before issues escalate. This approach shifts cloud security from reactive alerts to proactive risk prevention.
In this blog, we’ll walk through how to build an AI cloud threat monitoring platform, the core features it should include, and the technology needed to support scalable and secure cloud protection. This guide will help you understand the full roadmap to create an intelligent cloud threat monitoring solution.

What is an AI Cloud Threat Monitoring Tool?
An AI Cloud Threat Monitoring Tool leverages self-learning AI, behavioral analytics, real-time anomaly detection, machine-speed threat scoring, and context-aware correlation to monitor cloud workloads, identities, and data flows. It detects deviations across multi-cloud environments, identifying zero-day threats, insider activity, and misconfigurations while enabling autonomous AI-driven investigation and risk mitigation.
This platform is favored as enterprises adopt complex cloud environments where traditional tools fall short. AI monitoring provides faster threat detection, fewer false positives, and adaptive protection, reducing operational workload, uncovering unknown threats, and delivering scalable, automated, cloud-native security intelligence.
- Continuous audit and misconfiguration monitoring helps catch security gaps that human reviews often miss by automating checks across dynamic cloud resources.
- These tools significantly reduce alert fatigue by filtering false positives, allowing security teams to focus on high-risk incidents.
- AI cloud monitoring can prioritize risk based on exploitability and impact, improving decision-making under pressure.
- Integrated threat context enhances detection intelligence by correlating suspicious cloud activity with global attack insights.
- Some platforms adapt models continuously to reflect runtime changes in workloads and permissions for better real-time defense.
Why Traditional Cloud Security Tools Cannot Handle Modern Threats?
Traditional cloud security tools rely on static rules and signatures, making them ineffective against dynamic cloud environments, identity-based attacks, and evolving threats that require real-time behavioral analysis.
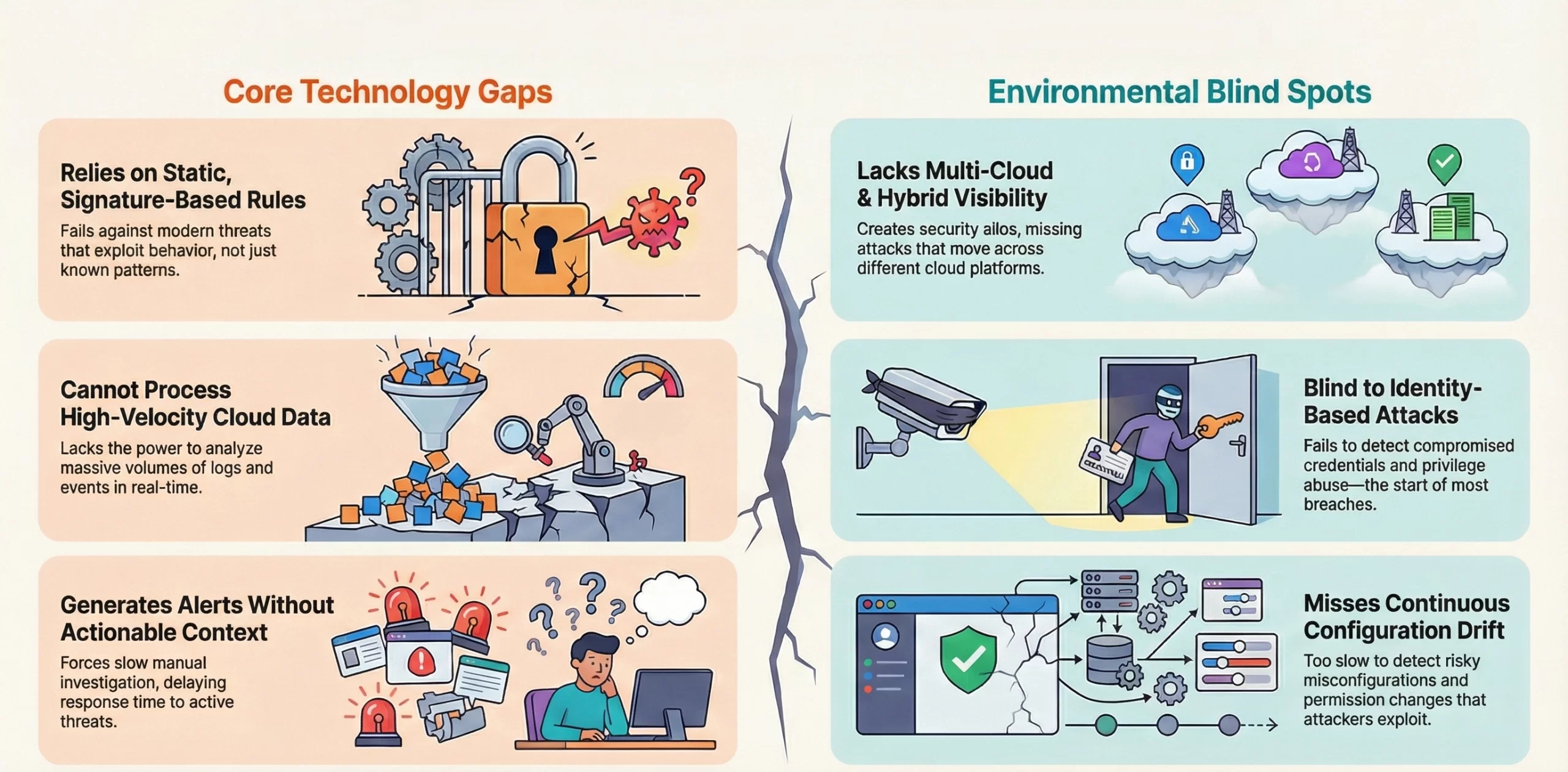
1. Static Rules vs. Behavioral Understanding
Legacy cloud security tools rely on static signatures and policies, which can’t keep up with dynamic cloud environments. Modern threats exploit behavioral deviations, identity misuse, and API manipulation, bypassing predefined patterns and remaining undetected.
2. No Multi-Cloud & Distributed Architecture Visibility
Traditional tools suited on-prem or single-cloud setups. Now, enterprises use AWS, Azure, Google Cloud, and hybrid environments, leading to fragmented visibility. Without cross-cloud data, legacy tools miss multi-step attacks moving between accounts, regions, or services.
3. Miss Identity-Centric Attacks
Most cloud breaches start with compromised credentials, privilege abuse, or permission drift. Traditional tools can’t model identity relationships or detect subtle interaction anomalies, leaving organizations vulnerable to stealthy access threats.
4. Cannot Process High-Velocity Telemetry in Real-Time
Cloud workloads generate massive volumes of API events, logs, authentication attempts and configuration changes. Traditional tools lack the performance and intelligence to analyze this telemetry at cloud speed, creating blind spots where attackers operate unnoticed.
5. Miss Misconfigurations & Continuous Drift
Cloud environments constantly change as teams deploy workloads, modify IAM roles, and update settings. Traditional tools are slow to adapt, missing misconfigurations and permission shifts that attackers exploit to escalate privileges or bypass controls.
6. Detection Without Intelligent, Context-Aware Response
Traditional tools generate alerts but lack AI-driven context, forcing manual investigation of anomalies, delaying response and increasing breach impact. Modern threats need autonomous or assisted action that legacy systems can’t provide.
How an AI Cloud Threat Monitoring Tool Works?
An AI cloud threat monitoring tool analyzes cloud activity with machine learning and behavioral analytics to detect anomalies. Understanding its operation helps organizations respond swiftly and maintain visibility in multi-cloud environments.
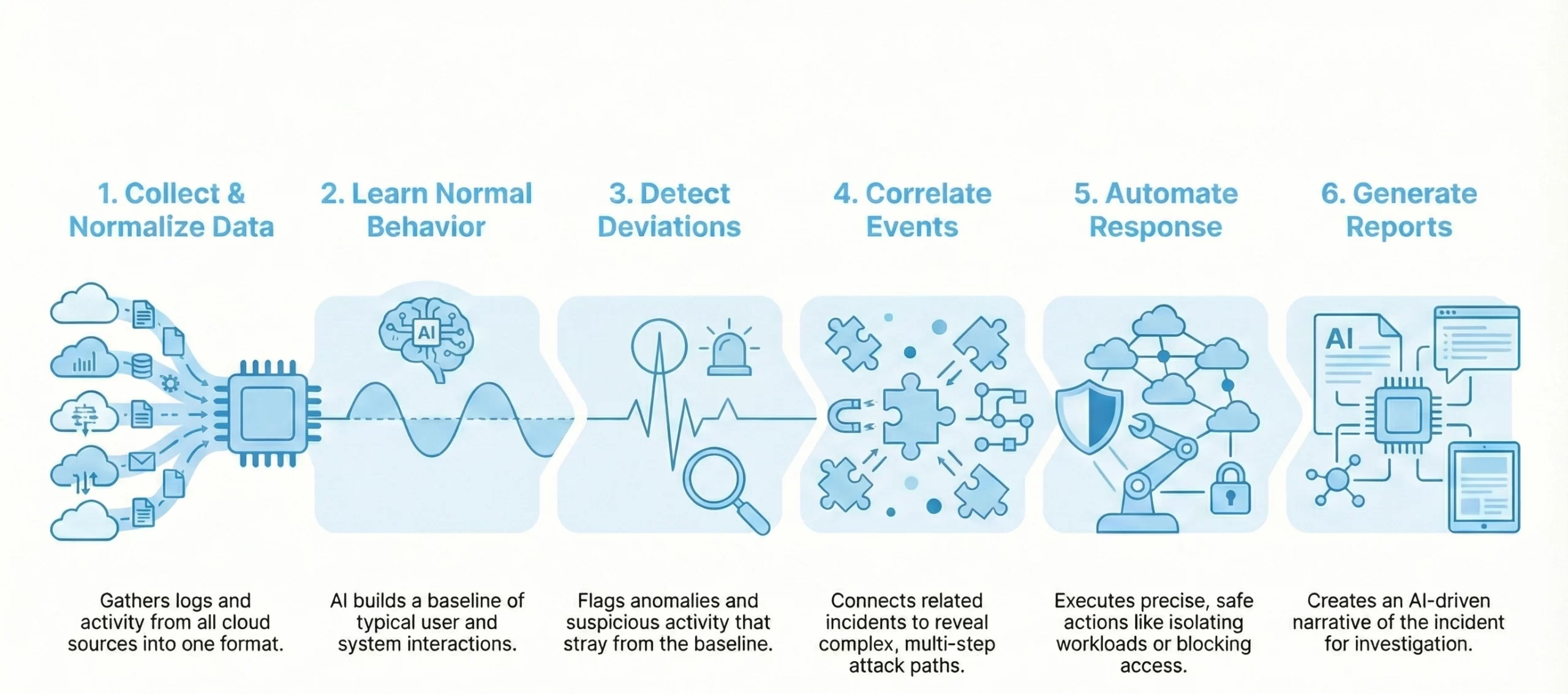
1. Collects & Normalizes Cloud Telemetry
The AI cloud threat monitor begins by gathering raw telemetry from cloud logs, workload activity, identity actions, network flows and API events. It then normalizes this data into a unified format, ensuring consistent analysis across AWS, Azure, Google Cloud and hybrid environments.
2. Learns Normal Behavior Using Cloud-Native AI Models
The system builds behavioral baselines by studying how users, identities, services and workloads typically interact. AI models learn API usage patterns, permission movements, authentication rhythms and workload lifecycles, forming a dynamic understanding of “normal” for each environment.
3. Detects Suspicious Activity via Behavioral Analysis
Once baselines are established, the platform evaluates new events using deviation scoring. It flags anomalies such as misconfigurations, privilege escalation attempts, unusual API bursts, abnormal authentication behavior or unexpected resource interactions, identifying threats that bypass rule-based tools.
4. Correlates Signals Across Cloud Accounts and Services
The AI engine connects related events to uncover multi-step attacks. It correlates identity behavior, API calls, workload changes and configuration drift across clouds, revealing stealthy attack paths that span regions, accounts or services.
5. Responds Automatically With Precise, Cloud-Safe Actions
When the system identifies high-risk behavior, it can execute automated responses such as restricting access, isolating workloads, blocking malicious API calls or halting suspicious processes. These actions are context-aware, minimizing disruption to legitimate cloud activity.
6. Generates AI-Guided Investigation Reports
Finally, the platform builds an AI-driven incident narrative that explains what happened, why it was flagged, how the threat evolved and which resources were affected. This accelerates investigation, improves team awareness and strengthens long-term cloud security posture.
Why 52% GenAI Cloud Threat Concerns Demand an AI Cloud Threat Monitor Tool?
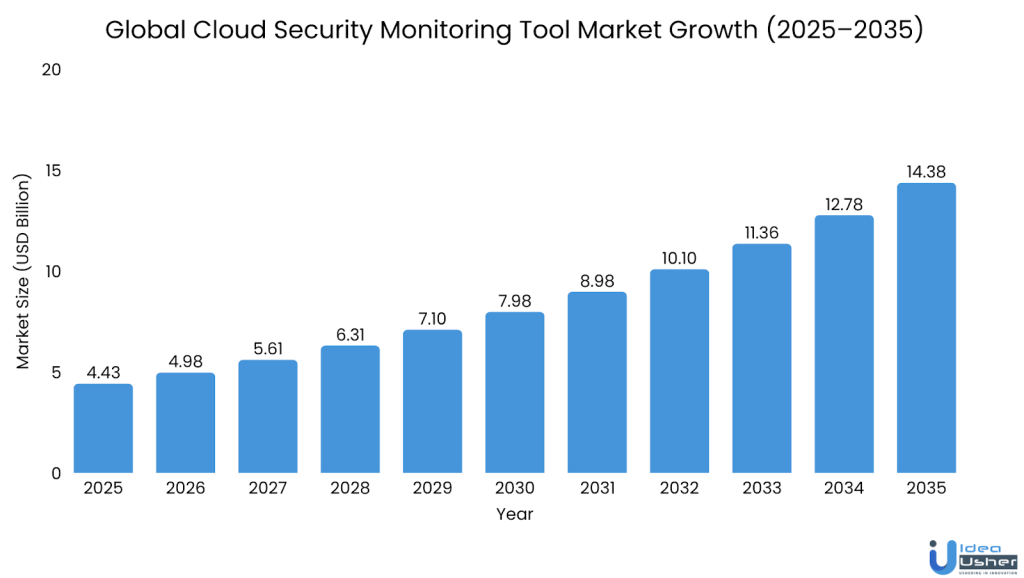
The global cloud security monitoring market, worth USD 4.43 billion in 2025, is projected to reach USD 14.38 billion by 2035 with a 12.5% CAGR. This growth is driven by the shift to cloud architectures, increasing complexity, and the need for real-time, AI-powered threat monitoring.
PwC’s report shows cloud threats are the top cybersecurity concern, with 52% expecting catastrophic GenAI attacks within a year. Meanwhile, 69% plan to use GenAI for cyber defense, indicating a shift toward automated security. This contrast highlights the growing urgency for AI-driven platforms that can detect and respond to emerging cloud risks in real time.
A. Enterprises Brace for GenAI-Accelerated Threats
Nearly 70% of IT leaders are incorporating AI into their cybersecurity strategies. Companies that leverage AI extensively for proactive prevention experience 46% lower costs from data breaches than those that don’t, saving over $2.2 million.
- Organizations expect GenAI to supercharge attacker capabilities, forcing rapid upgrades to cloud monitoring infrastructure.
- Security teams need behavior-aware AI capable of detecting novel, AI-generated attack patterns traditional tools fail to recognize.
- The shift toward GenAI defense validates market readiness for platforms with autonomous detection, multi-cloud correlation and real-time threat reasoning.
- Enterprises preparing for AI-driven threats are actively seeking monitoring tools that reduce investigation time, strengthen identity protections and neutralize threats before they escalate.
- This creates a fast-growing segment where buyers prioritize next-generation AI solutions over conventional monitoring tools.
B. Rising Breach Severity Is Accelerating the Need for AI Cloud Monitoring
Nearly 36%of businesses faced data breaches exceeding USD 1 million last year, with healthcare breach costs reaching USD 5.3 million, 25% higher than average. These rising losses are accelerating demand for an AI cloud threat monitoring tool and faster incident response.
- The surge in high-cost breaches shows that attackers are exploiting cloud misconfigurations, identity misuse and API vulnerabilities at scale.
- Industries like healthcare face heightened exposure due to regulated data, making AI-powered cloud monitoring essential for compliance and operational continuity.
- Organizations suffering million-dollar breaches seek platforms that cut detection time, prevent lateral movement and flag misconfigurations instantly.
- AI-driven systems provide the biggest financial impact by lowering breach severity through real-time anomaly detection and automated containment.
- This cost pressure accelerates procurement cycles, making the market exceptionally favorable for new, cloud-native AI monitoring solutions.

GenAI Cloud Attacks Are Surging & AI Monitoring Stops Them
GenAI is enabling faster, more adaptive cyberattacks that evade traditional defenses. AI cloud monitoring counters this by using behavioral analysis and real-time intelligence to detect anomalies, limit attack spread, and strengthen cloud security resilience.

1. GenAI Creates Hard-to-Detect Cloud Attacks
GenAI enables attackers to generate polymorphic malware, dynamic phishing campaigns and automated privilege escalation sequences that mutate continuously. These attacks blend seamlessly into normal cloud activity, making them extremely difficult for traditional tools to detect or correlate at scale.
2. AI Monitoring Reveals Hidden Behavioral Threats
AI cloud monitoring platforms rely on behavioral deviation analysis to detect abnormal identity movements, suspicious API usage, and irregular workload activity, even when actions appear legitimate. By learning expected cloud behavior, these models surface subtle anomalies that GenAI-crafted attacks attempt to disguise.
3. GenAI Automates Multi-Stage Intrusions
Attackers can now chain reconnaissance, credential testing, lateral movement and data extraction using autonomous GenAI workflows. These sequences unfold rapidly across accounts and regions, overwhelming manual detection systems and alert-driven workflows.
4. AI Correlates Threat Signals Across Clouds
Unlike legacy tools, AI correlates identity behavior, API calls, configuration changes and workload interactions across the entire cloud ecosystem. This exposes multi-step GenAI-driven intrusions by connecting signals that would appear harmless in isolation.
5. GenAI Boosts Phishing & Account Compromise
GenAI-generated messages dramatically increase credential compromise rates with 51% of cloud incidents linked to phishing. These campaigns can impersonate systems, vendors or internal teams with near-perfect accuracy.
6. AI Identifies Drift & Configuration Risks Early
AI continuously analyzes configuration changes, permission drift and deployment patterns. It identifies exposure points before attackers do, helping organizations maintain a hardened cloud posture even as environments evolve.
Key Features of an AI Cloud Threat Monitoring Tool
AI cloud threat monitoring tools combine real-time threat detection, behavioral analytics, and automated response to protect cloud environments. These key features help organizations enhance security, reduce risks, and streamline cloud operations effectively.

1. AI Real-Time Cloud Telemetry Ingestion
The platform ingests continuous cloud telemetry using AI-driven stream analytics that interpret workload signals, identity activity and network flows. This enables instant visibility into emerging behavioral changes across multi-cloud environments without relying on preconfigured rules or manual monitoring.
2. Behavioral Baselines for Cloud Resources
The system uses self-learning AI models to understand normal behavior for users, services, containers and serverless functions. These adaptive baselines evolve automatically with workload changes, helping surface early anomalies that traditional configuration-based systems overlook.
3. AI Anomaly Detection
AI models detect suspicious behavior by evaluating behavioral deviation patterns, contextual attributes and correlated signals across cloud networks, identity systems and storage layers. This enables precise discovery of insider misuse, privilege escalation and unknown attack sequences.
4. AI Identity & Access Behavior Analysis
The platform uses AI-powered identity scoring to evaluate login behavior, privilege shifts and access paths. It detects unauthorized access attempts and lateral identity movement by comparing live authentication behavior with learned patterns of normal cloud usage.
5. Autonomous Threat Correlation Engine
An AI correlation engine connects signals across services, identities and regions using multi-signal inference models. This reveals multi-step threats and coordinated attack paths that remain invisible in isolated cloud monitoring solutions.
6. AI-Driven Threat Pattern Recognition
AI models identify recurring cloud attack patterns, emerging tactics and unusual behavioral clusters. This supports earlier detection of coordinated attacks and helps predict risks before they escalate into full incidents.
7. AI Automated Response & Containment
The platform applies AI-guided containment actions such as restricting access, isolating workloads or blocking malicious traffic. These precision responses reduce dwell time, stabilize operations and allow teams to maintain control during fast-moving threats.
8. Misconfiguration & Drift Detection
AI continuously analyzes cloud policies to identify configuration drift, excessive permissions and hidden exposures. Using risk-weighted AI assessment, the system highlights vulnerabilities created through workload changes or manual adjustments.
9. Cloud Threat Investigation Workflows
The tool produces automated investigation insights using AI-based event sequencing and contextual reasoning. These narratives help analysts quickly understand root causes, attack progression and recommended remediation steps.
10. AI Cloud Risk Prioritization
AI analyzes cloud exposures, misconfigurations, and identity risks, scoring them based on potential impact and likelihood. This risk prioritization enables security teams to focus on high-value threats, streamline response efforts, and minimize security blind spots across complex cloud environments.

How to Build an AI Cloud Threat Monitor Platform?
Building an AI cloud threat monitor requires machine learning, anomaly detection, and automated response to secure cloud workloads. This guide covers key steps to develop a scalable, multi-cloud security platform.
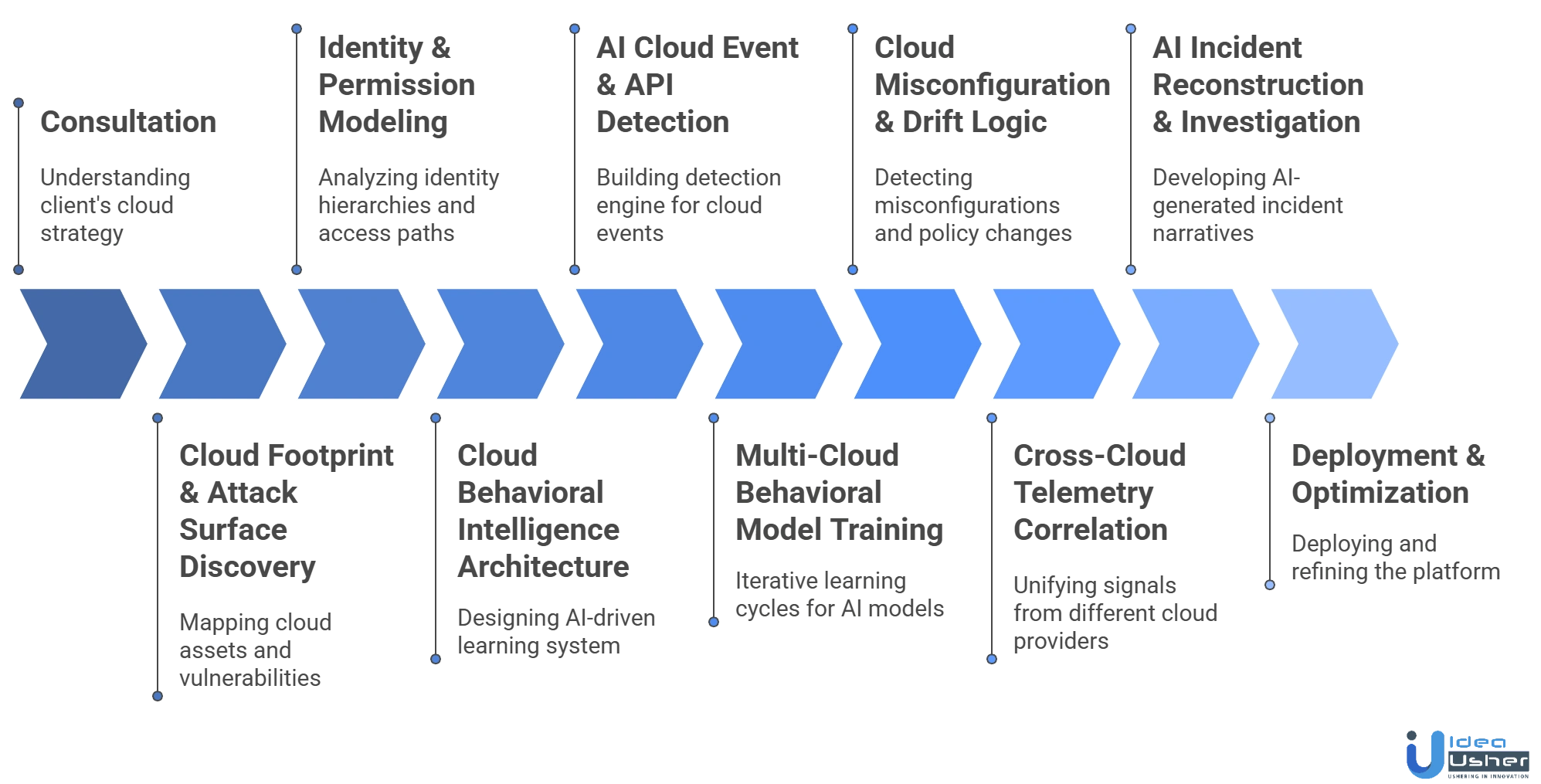
1. Consultation
We begin by understanding the client’s cloud strategy, workload distribution and identity structure. During consultation, we define monitoring priorities, expected AI outcomes and cloud environments that require deeper visibility, allowing us to design a platform aligned with their operational and security objectives.
2. Cloud Footprint & Attack Surface Discovery
Our developers map the client’s cloud footprint across accounts, regions and services. We identify exposed assets, external entry points and shadow resources. This creates an accurate view of the cloud attack surface that supports AI-guided threat modeling and targeted monitoring strategies.
3. Identity & Permission Modeling
We analyze identity hierarchies, permission paths and privilege relationships across cloud accounts. Our developers produce a blueprint for AI-driven access behavior analysis, ensuring the platform understands how users and services should interact and can detect drift or unauthorized access.
4. Cloud Behavioral Intelligence Architecture
We design the architecture that learns cloud behavior through self-learning AI models. This includes mapping workload lifecycles, API rhythm patterns and identity activity flows. The result is a behavioral intelligence layer that adapts to cloud elasticity and service variability.
5. AI Cloud Event & API Detection
Our team builds the detection engine that interprets cloud events using context-aware deviation scoring. It examines workload actions, API usage, authentication trends and configuration changes to identify emerging threats that blend into normal cloud operations.
6. Multi-Cloud Behavioral Models Training
We train AI models using real telemetry from multiple clouds and refine them through iterative learning cycles. This allows the models to understand legitimate differences between regions, accounts and services while remaining sensitive to threats that deviate from natural cloud behavior.
7. Cloud Misconfiguration & Drift Logic
Our developers create logic that detects misconfigurations, permission drift and risky policy changes. Using AI-assisted configuration analysis, the platform identifies exposures caused by human error, rapid deployment changes or unmanaged cloud services.
8. Cross-Cloud Telemetry Correlation
We implement a correlation layer that unifies signals from different cloud providers into one analytics workflow. This enables cross-cloud threat discovery, connecting identity behavior, workload activity and API anomalies across environments that typically operate in isolation.
9. AI Incident Reconstruction & Investigation
We develop investigation workflows that use AI to reconstruct incidents based on cloud events, identity movement and resource interactions. These AI-generated narratives help security teams understand root causes and attack progressions with clarity and reduced manual investigation time.
10. Deployment & Continuous Optimization
We deploy the platform across the client’s cloud environment and optimize it continuously. Through adaptive intelligence refinement, the system evolves with new cloud services, changing identities and shifting workloads, maintaining long-term accuracy and operational stability.
Cost to Build an AI Cloud Threat Monitor Platform
The cost of building an AI cloud threat monitor depends on AI model complexity, infrastructure scale, and integration requirements. These factors help organizations plan budgets for a robust, enterprise-ready cloud security solution.
| Development Phase | Description | Estimated Cost |
| Consultation | Defines client needs and cloud visibility goals through AI-focused discovery. | $3,000 – $6,000 |
| Cloud Footprint & Attack Surface Discovery | Maps cloud accounts, services and exposed assets for threat-aware planning. | $7,000 – $12,000 |
| Identity & Permission Modeling | Analyzes access paths and roles for AI-driven identity monitoring. | $16,000 – $30,000 |
| Cloud Behavioral Intelligence Architecture | Designs architecture for behavioral baselining across dynamic cloud workloads. | $12,000 – $18,000 |
| AI Cloud Event and API Engine | Builds engine for context-aware anomaly detection across cloud events. | $13,000 – $20,000 |
| Multi-Cloud Behavioral Models | Strengthens models through iterative cloud behavior learning cycles. | $11,000 – $18,000 |
| Cloud Misconfiguration & Drift Logic | Creates logic to detect policy drift, misconfigurations and exposures. | $12,000 – $17,000 |
| Cross-Cloud Telemetry Correlation Layer | Implements unified analytics for cross-cloud threat correlation. | $10,000 – $15,000 |
| AI Incident & Investigation Workflow | Develops workflows for AI-based incident narratives and analysis. | $12,000 – $19,000 |
| Deployment & AI Optimization | Deploys platform and performs adaptive AI refinement in real cloud environments. | $9,000 – $15,000 |
Total Estimated Cost: $66,000 – $126,000
Note: Development costs depend on cloud complexity, telemetry, compliance, identity, and AI automation. Multi-cloud setups and behavioral tuning also raise costs.
Consult with IdeaUsher for a personalized cost estimate and custom roadmap to develop a scalable, AI cloud threat monitoring platform tailored to your cloud architecture and security goals.
Cost-Affecting to Consider During Development
Several factors, including data quality, system complexity, compliance, and AI model depth, influence the overall cost of developing an AI cloud threat monitor.
1. Cloud Architecture Complexity
Extensive cloud infrastructures with multiple regions, accounts and distributed services require deeper mapping and behavior-aware modeling, increasing development time and planning effort for accurate AI-driven monitoring.
2. Identity & Access Structure
Large or fragmented IAM environments demand detailed permission modeling and AI-based access behavior analysis, which expands engineering needs for accuracy and ongoing behavior validation.
3. Cloud Telemetry Volume & Diversity
High-volume telemetry from API logs, workloads and identity events requires scalable AI pipelines to maintain real-time analysis, increasing ingestion, processing and anomaly-evaluation complexity.
4. AI Model Sophistication
Advanced capabilities such as context-aware deviation scoring, autonomous investigation and multi-cloud behavioral learning require extensive model training, tuning cycles and scenario validation.
5. Misconfiguration & Drift Detection Depth
Developing logic that detects misconfigurations, excessive permissions and policy drift demands continuous configuration behavior analysis, increasing development time and rule refinement.

Suggested Technologies for AI Cloud Threat Monitoring Tool Development
Creating an AI cloud threat monitor requires machine learning, cloud-native architectures, and real-time data processing. Choosing suitable technologies enables scalable threat detection, precise risk analysis, and efficient security operations.
| Technology Category | Suggested Technologies | Purpose / Why It’s Needed |
| AI & ML Frameworks | TensorFlow, PyTorch, Scikit-learn | Powers behavioral modeling and AI-based anomaly detection across cloud environments. |
| Cloud Telemetry Processing Systems | Apache Kafka, Apache Flink | Supports real-time cloud signal ingestion and scalable event processing. |
| Behavioral & Anomaly Libraries | River ML, PyOD, ADTK | Enables behavior deviation scoring and subtle anomaly recognition. |
| Cloud Logging & Event Management Tools | AWS CloudWatch, Azure Monitor, Google Cloud Logging | Provides raw events required for AI-driven cloud behavior analysis. |
| Threat Intelligence & Correlation Platforms | MISP, OpenCTI | Adds external context for smarter AI threat decisions across cloud environments. |
| Identity & Access Monitoring Tools | Open Policy Agent, Keycloak | Supports identity behavior evaluation and detection of permission misuse. |
| Cloud Configuration & Posture Analysis Tools | Cloud Custodian, Open Policy Agent (OPA), Checkov | Helps detect configuration drift and risky cloud policies. |
| MLOps & Model Monitoring Platforms | MLflow, Kubeflow, Seldon | Enables continuous AI lifecycle management and stable model performance. |
| Security Data Lakes | Snowflake, BigQuery, OpenSearch | Stores high-volume telemetry for behavioral training and cross-cloud correlation. |
| Containerization & Orchestration Tools | Docker, Kubernetes | Ensures scalable deployment and efficient AI model execution across cloud workloads. |
Challenges & How Our Developers Solve Those?
Developing an AI cloud threat monitor faces challenges like data complexity, false positives, and model scalability. Our developers tackle these with advanced algorithms, optimized data pipelines, and adaptive AI solutions for reliable, real-time detection.
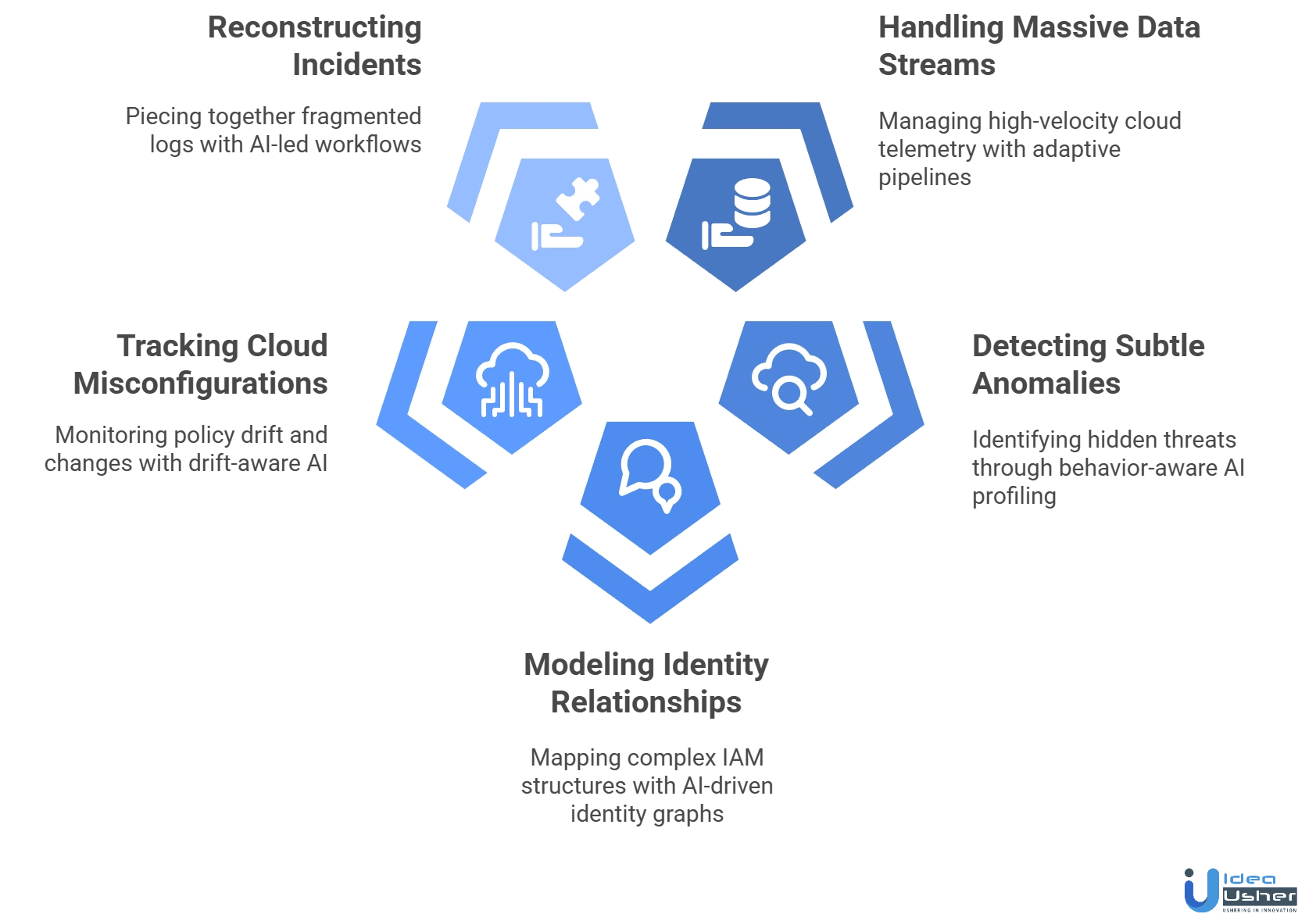
1. Handling Massive Cloud Telemetry Streams
Challenge: Cloud workloads generate enormous, fast-moving telemetry that becomes difficult to normalize, enrich and analyze without losing behavioral fidelity.
Solution: We design adaptive ingestion pipelines that manage high-velocity cloud signals, preserving behavioral details and enabling our AI models to evaluate events in real time without performance bottlenecks.
2. Detecting Subtle Cloud Anomalies
Challenge: Cloud attacks often hide within normal workload activity, making subtle anomalies difficult to isolate using traditional detection methods.
Solution: We use behavior-aware AI profiling that learns workload lifecycles and API rhythm patterns, allowing our platform to spot micro-deviations that signal unauthorized access, privilege abuse or stealthy threat movement.
3. Complex Identity & Permission Relationships
Challenge: Cloud IAM structures contain layered roles, dynamic permissions and cross-account access that are difficult to model accurately.
Solution: We build AI-driven identity graphs that map privilege paths, evaluate behavior patterns and uncover risky movements, helping our platform detect identity misuse before it becomes a full incident.
4. Tracking Cloud Misconfigurations & Drift
Challenge: Frequent deployment changes cause policy drift and misconfigurations that introduce security gaps without immediate visibility.
Solution: Our developers create drift-aware AI logic that monitors cloud configurations continuously, highlights emerging exposure points and detects unsafe permission or policy changes in real time.
5. Reconstructing Cloud Incidents Accurately
Challenge: Cloud incidents involve fragmented logs, distributed services and identity events that are difficult to piece together manually.
Solution: We build AI-led investigation workflows that assemble event sequences, map identity interactions and provide clear incident narratives to help teams understand root causes quickly.
Revenue Models of AI Cloud Threat Monitoring Tool
AI cloud threat monitoring tools generate revenue through subscriptions, licensing, and managed security services. These models help businesses optimize monetization while delivering scalable, enterprise-grade cloud security solutions.

1. Subscription-Based SaaS Model
This is the primary revenue engine where clients pay monthly or annual fees for continuous access to AI-driven cloud monitoring, behavioral analytics and automated threat detection. It ensures predictable recurring revenue and long-term customer retention.
2. Tiered Pricing Structure
Offering multiple tiers allows organizations to choose the monitoring depth. Lower tiers may include basic visibility, while higher tiers include autonomous response, identity analytics and multi-cloud coverage. This model maximizes revenue by aligning price with cloud environment complexity.
3. Usage-Based Pricing
Pricing scales based on telemetry volume, cloud accounts, workloads or API activity. As companies expand their cloud footprint, revenue grows naturally. This model fits enterprises with fluctuating cloud usage and rewards platforms with efficient, high-quality AI processing.
4. Enterprise Licensing Deals
Large organizations may adopt full-platform licensing that covers all regions, accounts and cloud users. These contracts generate high upfront revenue and create long-term lock-in through broad operational integration across teams and departments.
5. Professional Services & Fees
Complex onboarding, cloud footprint mapping, configuration tuning and AI model calibration often require specialized engineering. These one-time or milestone-based services create an additional revenue stream while improving platform performance for the client.
Top AI Cloud Threat Monitoring Tools in the Market
AI cloud threat monitoring tools help organizations detect anomalies, assess risk, and respond to threats across complex cloud environments. These platforms combine machine learning, behavioral analytics, and real-time monitoring to secure modern cloud workloads.
1. Darktrace

Darktrace uses self-learning AI to monitor cloud assets, identities, and workloads in real time. By understanding normal behavior, it detects unknown and novel threats, models attack paths for risk prioritization, and provides AI-assisted automated response across hybrid and multi-cloud environments.
2. SentinelOne
SentinelOne’s AI-powered CNAPP monitors cloud workloads, containers, and serverless environments. Its AI models detect runtime threats and unusual behavior while enabling automated threat response, reducing manual intervention and improving overall cloud security posture.
3. AccuKnox
AccuKnox integrates AI with zero-trust policies to monitor hybrid and multi-cloud environments. Its platform identifies anomalous activity, unauthorized access, and misconfigurations, enabling proactive threat detection and policy-based enforcement for enterprise-grade cloud security.
4. Fortinet
Fortinet applies behavior-based AI & machine learning to establish normal cloud activity baselines and detect insider risks, misconfigurations, and unusual behavior. Its adaptive AI correlates data across users, workloads, and containers, helping security teams focus on high-priority alerts.
5. Vectra AI
Vectra AI leverages machine learning and behavioral analytics to create baselines of normal cloud activity across AWS, Azure, and Microsoft 365. Its AI detects anomalous patterns like credential misuse, insider threats, and lateral movement, enabling faster threat identification and context-aware response.
Conclusion
Building an AI cloud threat monitor is about gaining clear visibility into complex cloud environments and responding with confidence. The focus should remain on accurate data collection, contextual risk analysis, and alerts that respect human judgment. An effective AI cloud threat monitor tool supports security teams by reducing noise while highlighting what truly matters. When designed with transparency, scalability, and governance in mind, it becomes a reliable layer of defense that evolves alongside cloud infrastructure and strengthens trust across technical and business stakeholders across modern hybrid architectures and shared responsibility.
Why Choose IdeaUsher for Your AI Cloud Threat Monitor?
IdeaUsher develops AI-powered cloud security platforms that continuously monitor cloud environments, detect suspicious behavior, and prevent breaches before they impact business operations.
Why Work with Us?
- Real-Time Cloud Monitoring: Our tools track user activity, API calls, and configuration changes to detect abnormal patterns immediately.
- Predictive Risk Analysis: AI models predict potential vulnerabilities and prioritize threats based on severity.
- Proven Enterprise Deployments: We have delivered cloud threat monitoring solutions that safeguard multi-cloud infrastructures across sectors.
- Seamless Integration: Platforms integrate with existing cloud services like AWS, Azure, and GCP for minimal disruption.
Explore our portfolio to see how we’ve developed AI solutions for numerous enterprises across various industries.
Reach out today to build a proactive AI cloud security solution.
Work with Ex-MAANG developers to build next-gen apps schedule your consultation now
FAQs
An AI cloud threat monitor integrates data from multiple cloud providers using unified schemas and APIs. This approach ensures consistent visibility and threat detection across AWS, Azure, and Google Cloud environments.
False alerts are reduced by using contextual analysis, behavioral baselines, and adaptive learning models. An effective AI cloud threat monitor correlates events across services, helping security teams focus on genuine threats rather than isolated anomalies.
Market readiness depends on scalability, cloud provider compatibility, security accuracy, and compliance support. A well-designed AI cloud threat monitor tool must integrate smoothly into existing workflows while demonstrating measurable risk reduction for customers.
An AI cloud threat monitor uses audit logs, network flows, API activity, identity events, and configuration data. These inputs allow the system to detect misconfigurations, unauthorized access, and unusual behavior across cloud workloads.