Every security team knows the feeling when everything seems calm until an alert appears and something starts to drift out of place. Data is moving in an unexpected direction, and the system is behaving in a way that raises concerns. By the time patterns begin to form, the threat may already be active. Modern attacks move faster than traditional tools can keep up, creating a growing blind spot.
AI-driven threat detection platforms respond to this with adaptive learning, continuous behavioral baselining, and automated correlation that links small events into real intelligence. Machine learning models examine large streams of signals in real time and convert subtle anomalies into meaningful indicators. Over time, the system will become more precise and more context-aware, enabling it to surface threats that static tools rarely catch.
Over the years, we’ve built numerous AI-driven cybersecurity solutions that leverage advanced technologies, including behavioral threat intelligence and big data streaming architectures. Using this expertise, we’re writing this blog to outline the steps to develop an AI threat detection platform. Let’s start!
Key Market Takeaways for AI Threat Detection Platforms
According to KBV Research, the AI-driven threat detection market is gaining momentum as organizations seek tools that can keep pace with rapidly evolving cyber risks. Industry projections indicate the space will reach about $22.2 billion by 2031, supported by a 23.3% CAGR, as security teams move away from rigid, rules-based systems toward platforms that interpret vast streams of telemetry and surface genuine threats more accurately. As cloud infrastructure, SaaS adoption, and remote work expand the attack surface, solutions that can learn normal behavior and detect anomalies in real time are becoming indispensable.
Source: KBV Research
Leading platforms reflect this shift. Darktrace uses self-learning technology to map typical patterns across networks, identities, and cloud environments, enabling it to detect and block anomalous activity that may indicate ransomware, insider misuse, or supply-chain infiltration.
SentinelOne’s Singularity platform brings a behavioral lens to endpoints, workloads, and IoT devices, delivering automated prevention and response to help teams contain threats quickly without extensive manual involvement.
What Is an AI Threat Detection Platform?
An AI threat detection platform is a security system that uses machine learning, behavioural models, and advanced data correlation to spot cyber threats as they unfold. Instead of relying on signatures or predefined rules, it learns how users, devices, and applications typically behave within an environment.
When something deviates from that baseline, the platform can raise an alert, score the risk, or even take action.
Its purpose is to move security teams away from slow, reactive processes and into a world where detection is faster, prioritisation is sharper, and previously invisible threats, such as insider misuse or zero-day attacks, become far easier to detect and stop.
AI-Native vs. Traditional Tools
| Aspect | Traditional SIEM / Antivirus | AI-Native Threat Detection Platform |
| Detection Logic | Works from rules and signatures it has seen before | Builds behavioural baselines and detects patterns it has never seen |
| Response to New Threats | Needs updates and manual rule creation | Learns and adapts autonomously in real time |
| Alert Volume | High noise, mostly low-value alerts | Low noise, alerts ranked by real impact |
| Data Handling | Data sits in silos with limited correlation | Unified data model that connects endpoints, cloud, identity, and network |
| Primary Strength | Known malware and compliance logging | Unknown threats, insider activity, lateral movement, zero-days |
| Human Dependency | Heavy reliance on analyst triage | AI-driven triage with human oversight |
Types of AI Threat Detection Platforms
Modern environments are attacked from every angle, such as endpoint, network, cloud, and identity. An enterprise AI platform typically integrates these perspectives, so investigations and responses are linked rather than scattered across tools.
1. Network-Based Threat Detection
This part of the platform analyzes network traffic to detect intrusions, data theft, anomalous communication patterns, and lateral movement.
How AI Strengthens It
AI analyzes normal traffic patterns, who communicates with which system, when, and in what volume. Using this baseline, it can detect:
- Slow, hidden data leaks
- Command-and-control beaconing to suspicious external hosts
- Lateral movement that breaks expected segmentation rules
- Encrypted threats by analysing flow metadata instead of payloads
Example Platform: Darktrace
Darktrace’s “Enterprise Immune System” builds a behavioural profile for every user and device. It famously detected the WannaCry ransomware in seconds by identifying its unusual propagation pattern, long before signature-based tools responded.
2. Endpoint and Device Behaviour Analytics
Traditional EDR collects logs; AI-driven EDR interprets behaviour. It monitors processes, scripts, system calls, registry activity, and memory to detect attacks that leave no malware file behind.
How AI Strengthens It
- Detects malicious scripting activity through behaviour rather than signatures
- Recognises ransomware encryption patterns before full damage is done
- Builds process trees to identify suspicious parent-child execution paths
- Spots in-memory techniques such as injection and reflective loading
Example Platform: CrowdStrike Falcon
Falcon uses behavioural analytics based on Indicators of Attack, focusing on the attacker’s sequence of actions rather than known malware samples. This helped identify elements of the SolarWinds attack by detecting unusual DLL loading and credential access behaviour.
3. Cloud and SaaS Threat Detection
As workloads shift to AWS, Azure, GCP, and SaaS applications, cloud-native threats become harder to detect with traditional tools.
How AI Strengthens It
AI can detect:
- Misconfigurations like a storage bucket suddenly becoming publicly accessible
- Compromised cloud identities performing abnormal tasks
- SaaS data theft or unusual sharing activity
- Hybrid attacks that connect on-prem behaviour with cloud actions
Example Platform: Wiz
Wiz uses an AI-enhanced graph engine to map relationships between identities, workloads, data, and configurations. It quickly reveals attack paths, such as when stolen developer credentials on GitHub directly lead to unauthorised access in AWS.
4. Identity and Access Behaviour Monitoring
UEBA tools analyze how people and service accounts typically behave and flag activity that does not match their established profiles.
How AI Strengthens It
UEBA models build a living profile of each user by learning their typical login times and locations, the devices and applications they rely on, how they interact with data day-to-day, and the level of access they typically need. With this baseline in place, even small deviations stand out quickly and can signal early signs of compromise.
AI then detects anomalies such as:
- Impossible travel logins
- Sudden access to critical systems
- Stolen sessions are behaving unpredictably.
- Dormant accountsare becoming active without cause.
Example Platform: Varonis
Varonis monitors access to sensitive data stores and uses behavioural analytics to detect misuse. If an employee who normally touches a handful of files suddenly attempts to download thousands, the platform quickly flags this as potential insider activity.
How Do AI Threat Detection Platforms Work?
AI threat detection platforms monitor how your systems normally behave, quietly build patterns that may reveal subtle risks, and flag anything that drifts from that baseline in a meaningful way.
They correlate identity, activity network flows, and endpoint signals to uncover threats that would otherwise be hidden within routine traffic. When something truly stands out, the system can guide a rapid response, often with a level of precision that humans struggle to match.
1. Gathering the Raw Truth
What the platform collects
AI can’t reason without visibility. The first step is vacuuming up telemetry from every layer of the organization:
- Network: flow data, DNS lookups, packet metadata
- Endpoints: process creation, file modifications, registry changes
- Cloud services: audit logs, configuration deltas, API activity
- Identity systems: authentication logs, SSO events, VPN sessions
Every source speaks its own dialect. One system logs a login event completely differently from another.
Why normalization matters
If every log stays in its native format, no machine or human could stitch them into a coherent picture. The platform translates everything into a shared security language: users, hosts, files, actions, timestamps, and relationships.
The result is often represented as a security knowledge graph, a living map of “who touched what, when, and how.” Every layer of AI sits on this foundation.
2. Learning the Organization’s Rhythm
This is where the platform stops acting like a rule engine and starts acting like an observer.
What the AI studies
Across a few weeks, it quietly watches the environment and builds thousands of micro-models:
- When each user typically logs in
- How specific service accounts normally behave
- Typical east–west traffic volumes
- Usual administrative actions
- Normal cloud API usage patterns
It’s not memorizing rules. It’s building a multidimensional understanding of normalcy.
As the business evolves, such as new hires, seasonal workloads, or tool changes, the baseline shifts with it.
3. Real-Time Judgment
When a new activity appears, the system checks, “Is this meaningfully different from the behavior I’ve learned?”
A single odd event rarely means trouble. Threat activity almost always shows up as a pattern of small deviations.
A simple example
On their own, each event below seems mildly suspicious:
- An employee downloads more files than usual
- Their login originates from a new country.
- Encrypted outbound traffic suddenly spikes
- Their workstation launches an unusual PowerShell script.
Individually, these are four low-severity anomalies. Together, they form a coordinated story of credential theft and data exfiltration.
The platform’s strength is the ability to connect hints across identity, network, and endpoint data at a scale no human analyst can match.
4. Adding Meaning
Raw detection is never enough. An analyst still needs to understand why the event matters.
The system automatically enriches detections with context:
- MITRE ATT&CK mapping that identifies which attack techniques the behavior resembles
- Threat-intelligence lookups that flag suspicious IPs, domains, or file hashes
- Business impact assessment that highlights sensitive data or critical systems involved
- Attack-path tracing that visualizes how one compromised asset was used to reach another
Instead of a vague alert like “Unusual activity detected,” analysts receive a narrative such as:
“High-risk incident. Lateral movement consistent with known APT tradecraft. A compromised service account accessed customer PII and attempted exfiltration.”
This turns noise into clarity.
5. Closing the Loop
Once the platform identifies a real issue, it helps take action quickly and safely.
Response options
Guided Investigation: Providing analysts with “next best actions” and automated evidence collection.
Semi-Automated Playbooks: “Click here to disable this user account and isolate this endpoint temporarily.”
Fully Autonomous Response: For high-confidence, high-velocity threats (like ransomware encryption in progress), the platform can automatically:
- Quarantine infected endpoints
- Block malicious network connections.
- Disable compromised credentials
- Revoke excessive permissions
Over time, the system learns from the outcomes of these responses and uses that feedback to refine its detections.
The Human–AI Alliance
AI isn’t here to replace analysts. It clears the noise so analysts can focus on work that requires judgment and intuition.
A typical morning for a modern SOC analyst might look like this:
- 8:00 AM – Logs in to find three well-formed incidents instead of hundreds of raw alerts
- 8:15 AM – Reviews an incident narrative and approves containment actions that already executed
- 8:30 AM – Investigates a complex case using a visual attack timeline
- 9:00 AM – Performs proactive threat hunting guided by AI-identified high-risk assets
Analysts spend more time solving meaningful problems and less time battling alert fatigue.
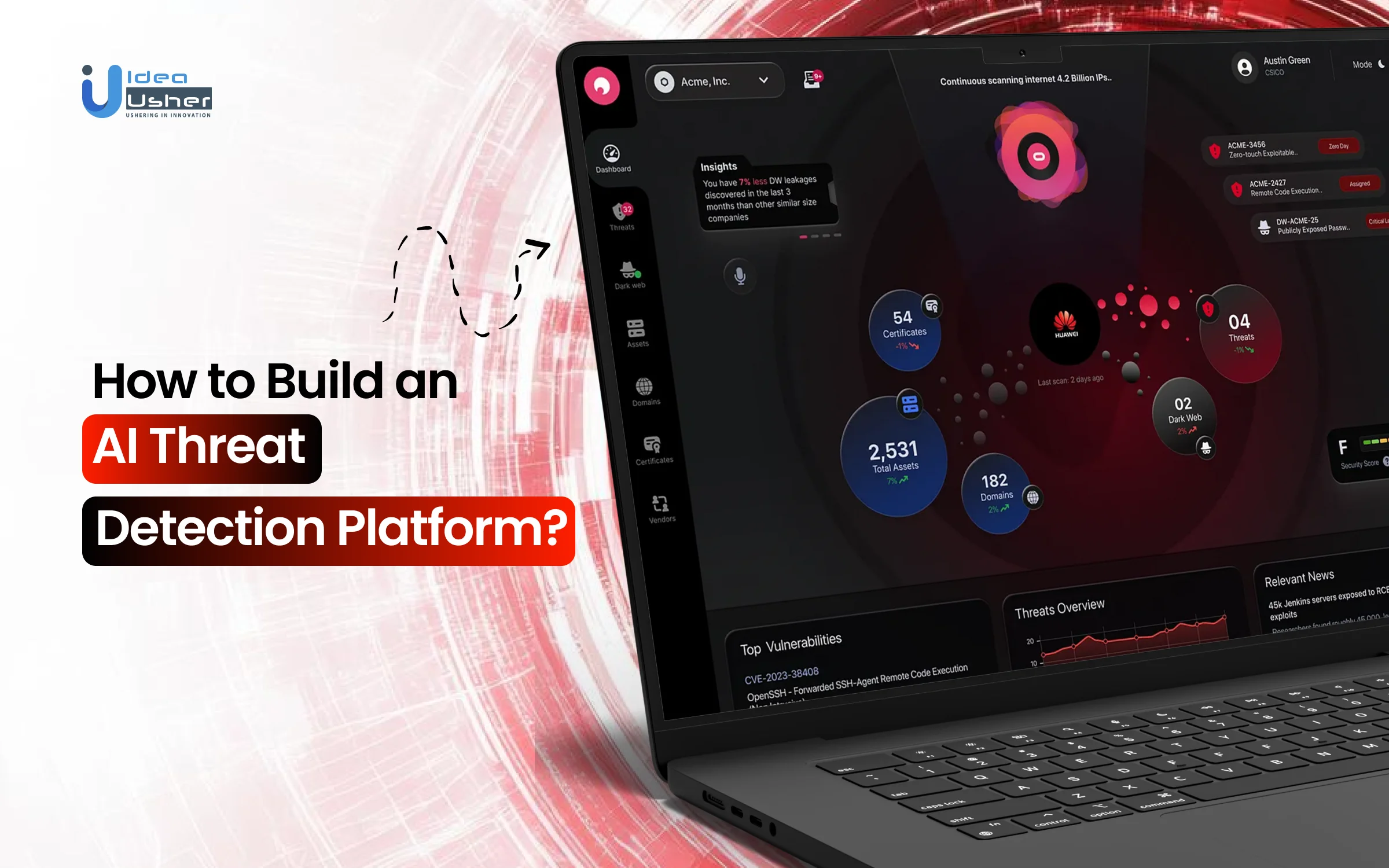
How to Build an AI Threat Detection Platform?
A strong AI threat detection platform starts with an event-driven design so the system can track activity in real time and surface signals that matter. Detection models then analyze behavioural patterns and may quickly flag deviations that would not occur in a stable environment. We have built multiple AI threat detection platforms for enterprises, and this is the approach we follow.
1. AI-Native Architecture
We begin by designing an event-driven, streaming-first architecture that captures every meaningful security signal, separating the data, model, and response layers so each can evolve independently, while ensuring full multi-tenant readiness for clients requiring secure, scalable enterprise deployment.
2. Unified Security Lakehouse
We bring together logs, telemetry, and threat intelligence into a unified lakehouse, apply normalization and enrichment pipelines to add structure and context, and map all incoming activity to the MITRE ATT&CK framework so detections remain consistent and easy for client SOC teams to interpret.
3. Multi-Model Detection Engines
We build specialized AI engines, including UEBA models, unsupervised anomaly detectors, and deep learning models for malware and phishing, and maintain continuous retraining workflows so each model stays aligned with the client’s environment and evolves alongside emerging attack techniques.
4. Threat Scoring & Correlation
We create context-aware scoring models that weigh user behavior, asset importance, and historical activity, then correlate events across domains to surface meaningful attack paths, ensuring client SOC teams can prioritize incidents that truly matter.
5. Automated Response
We integrate automated playbooks for isolation, blocking, and containment, use reinforcement-learning concepts to refine response choices over time, and maintain human-in-the-loop controls so each client retains full governance over how automation operates in their environment.
6. Governance & Compliance
We deliver explainable AI dashboards, detailed audit trails, and compliance-ready reporting aligned with NIST, ISO, and SOC frameworks, helping clients meet regulatory expectations while maintaining full visibility into how the platform makes decisions.
Successful Business Models for AI Threat Detection Platforms
AI-driven security has expanded at an extraordinary pace, and four business models have emerged as the most reliable engines of growth. For buyers, understanding these models helps clarify what they are paying for. For founders, they serve as blueprints for how revenue scales in this sector.
1. Endpoint-Centric Subscription Model
In this model, companies pay an annual subscription fee based on the number of devices, such as laptops, servers, mobile phones, and other endpoints, that the platform protects. This simple per-endpoint structure has made it the most widely adopted monetization method in AI security, responsible for roughly two-thirds of the market’s revenue.
Typical Pricing Tiers
- Basic Tier: $50–$100 per endpoint per year
- Advanced (EDR/XDR) Tier: $150–$250 per endpoint
- Fully Managed Tier: $300–$400+ per endpoint with 24/7 SOC support
CrowdStrike Falcon is a flagship example. In 2023, the company surpassed $3 billion in annual recurring revenue while protecting about 90 million endpoints across more than 23,000 customers.
Their steadily rising average contract value shows that this model scales naturally as organizations grow.
2. Consumption-Based Cloud Platform Model
Instead of charging by device count, this model bills customers based on the amount of data the platform processes, the number of users protected, or the compute resources consumed. Cloud-native vendors favor this approach, and it has grown approximately three times faster than traditional licensing models in recent years.
Common Pricing Approaches
- Data Ingest: $1.50–$4.00 per GB of security data processed
- Per User: $15–$45 per user per month for SaaS security layers
- Hybrid Plans: Combinations of usage volume and feature tiers
Microsoft Defender XDR benefits from the scale of the Azure ecosystem. Although Microsoft does not break out Defender-specific revenue, the company’s security business now exceeds $20 billion annually.
Consumption-based offerings account for roughly 40 percent of that growth, and AI-enhanced detection tools often command premium pricing.
3. Enterprise Licensing Agreement Model
ELAs bundle multiple technologies into one multi-year contract that covers an organization’s complete security environment. They are aimed at very large enterprises and commonly generate $5 to $50 million per year with contract terms that span three to five years.
Typical ELA Structure
- Minimum Commitments: $3 million to $10 million annually
- Bulk Discounts: 20 to 40 percent for organization-wide deployment
- Innovation Clauses: Guaranteed access to new AI capabilities during the contract
- Total Contract Value: Often between $15 million and $250 million over the full term
Fortinet has aggressively expanded through ELAs, reporting year-over-year enterprise agreement growth of 35%. In 2023, Fortinet generated $5.3 billion in revenue, with long-term commitments representing about 40 percent of total revenue. Their AI-enhanced features often strengthen both adoption and renewal rates.
Why 63% Believe AI Boosts Cyber Threat Detection?
According to studies, 63% of cybersecurity professionals believe AI enhances threat detection, which makes sense given how quickly threats evolve. AI can process large volumes of network data in real time and often identifies patterns that a human analyst might miss.
1. AI Handles Huge Data Volumes
Enterprise networks generate large volumes of data, including logs, authentication events, connection records, and file access trails. A single organization may generate millions of events per day, far beyond what even a well-staffed SOC can review.
AI systems thrive under this load.
They can:
- Analyze nonstop without fatigue
- Identify patterns in massive datasets
- Surface anomalies instantly
This ability to scale beyond human limits is one of the biggest reasons professionals view AI as essential rather than optional.
2. Detecting Unknown Threats
Traditional security tools depend on signatures, which are definitions of known malware or attack patterns. This model breaks down when attackers use zero-day exploits or hide inside normal-looking activity.
AI takes a different approach. By learning what normal looks like for every device and user, it can flag behavior that deviates from the baseline such as:
- A user logging in from another country at an unusual hour
- A server reaching out to an unrecognized domain
- A privileged account accessing far more data than usual
This behavioral analysis gives AI an advantage against stealthy intrusions and significantly enhances professional confidence.
3. Reducing Alert Overload
Most SOC analysts experience overwhelming alert volume. Thousands of notifications appear each day and many are repetitive or low risk. Critical warnings get buried.
AI improves this dynamic by:
- Correlating related alerts
- Assigning risk scores
- Presenting a clear sequence of events
Analysts see fewer, higher-quality incidents with context such as, “High likelihood of credential compromise. Lateral movement attempt detected.”
This shift from noise to clarity is one of the most valuable day-to-day benefits.
4. AI Cuts Detection Time
Historically, attackers could remain undetected within a network for weeks or even months. The longer they stay, the more data they steal and the more damage they cause.
AI shortens this window significantly. It analyzes activity in real time, correlates signals across multiple systems, and can trigger automated responses immediately.
Actions such as isolating a suspicious endpoint or blocking a malicious connection occur within minutes rather than days. Speed is one of the strongest reasons professionals see AI as a game-changer.
Challenges to Building an AI Threat Detection Platform
After building AI-driven security platforms for numerous clients across industries, we have identified a consistent set of challenges that organizations face. More importantly, we have developed proven strategies to address each one. The following outlines the most common obstacles and how to navigate them successfully.
1. High False Positives and Alert Noise
AI models often generate excessive alerts, overwhelming SOC teams and leading to alert fatigue. This typically stems from imbalanced data, a lack of contextual threat intelligence, or overly generalized detection rules.
How to solve it:
- Employ advanced feature engineering and contextual enrichment to reduce noise.
- Integrate threat intelligence feeds to distinguish benign anomalies from real threats.
- Continuously tune models using feedback loops from analysts.
- Apply ensemble modeling and threshold optimization to improve signal quality.
The result is dramatically lower false-positive rates and a more focused, accurate detection engine.
2. Data Quality and Integration Complexity
Security data arrives from diverse sources such as firewalls, endpoints, cloud logs, and identity systems, each with its own format, schema, and reliability issues. Poor data quality can cripple even the most advanced AI models.
How to solve it:
- Standardize data ingestion using flexible pipelines such as Kafka, Fluentd, and Logstash.
- Implement automated data validation, deduplication, and normalization.
- Use schema registries and metadata catalogs to maintain consistency across pipelines.
- Employ enrichment layers to enhance raw logs with contextual information.
High-quality and integrated data enables AI models to operate at maximum accuracy.
3. Model Drift and Accuracy Degradation
Threat landscapes evolve constantly. New malware strains, attack vectors, and adversarial tactics appear regularly. Without consistent monitoring, models become stale and lose detection accuracy over time.
How to solve it:
- Establish continuous monitoring of model performance using Prometheus and Grafana.
- Automate retraining workflows using MLflow and CI/CD pipelines.
- Detect data distribution shifts and behavioral anomalies to trigger proactive updates.
- Maintain versioning and rollback strategies to ensure operational resilience.
This keeps your AI platform aligned with emerging threats and real-world behavior changes.
4. Enterprise Trust in AI-Driven Decisions
Security teams must be able to explain why the AI flagged an event. Without transparency, stakeholders hesitate to rely on automated decisions, especially in high-risk environments.
How to solve it:
- Implement explainable AI techniques such as SHAP and LIME.
- Provide feature-level insights that show what influenced each prediction.
- Offer confidence scores, model rationale summaries, and auditor-friendly logs.
- Build human-in-the-loop workflows to combine analyst expertise with machine intelligence.
When detection is explainable and auditable, organizations can develop confidence in AI-assisted security operations.
5. Scaling Performance Without Latency Issues
AI threat detection must operate in real time. As data volumes grow, poorly optimized pipelines can lead to slow inference times or processing bottlenecks and this compromises security visibility.
How to solve it:
- Use distributed compute technologies such as Kubernetes, Spark Streaming, and cloud autoscaling.
- Deploy optimized model formats such as ONNX for fast, low-latency inference.
- Implement GPU or accelerator-based processing for deep learning models.
- Break monolithic detection logic into microservices to improve throughput.
With the right architecture, the platform can scale to billions of events per day while maintaining sub-second detection performance.
Tools & APIs to Build an AI Threat Detection Platform
Building an effective AI-driven threat detection platform requires a modern, scalable, and observability-focused technology stack. The following tools and frameworks enable seamless data ingestion, advanced machine learning, real-time detection, and enterprise-grade deployment.
1. Data Ingestion & Streaming
Apache Kafka
Kafka serves as the backbone of real-time data ingestion. It enables high-throughput, low-latency streaming of logs, network telemetry, authentication records, and security events from distributed sources. Its fault-tolerant architecture ensures continuous data availability and supports event-driven threat detection workloads.
Apache Spark Streaming
Spark Streaming provides powerful distributed processing of large-scale data streams. By applying machine learning models directly to streaming pipelines, the platform can analyze millions of events per second, detect anomalies in real time, and scale elastically with growing traffic.
Fluentd / Logstash
These log forwarders unify data collection from servers, applications, cloud resources, and security devices. With flexible parsing and enrichment capabilities, Fluentd and Logstash ensure incoming data is normalized and structured, ready for downstream analytics.
2. AI & Machine Learning Frameworks
TensorFlow / PyTorch
Modern deep learning models for intrusion detection, behavioral analytics, and anomaly detection are commonly built using TensorFlow or PyTorch. These frameworks offer flexibility, GPU acceleration, and extensive ecosystem support for building and training custom neural networks.
Scikit-learn
Ideal for classical machine learning approaches, including clustering, isolation forests, and statistical anomaly detection. Scikit-learn enables rapid experimentation and is well-suited for lightweight models deployed at the edge or within microservices.
MLflow
MLflow enables end-to-end model lifecycle management, including experiment tracking, versioning, packaging, and deployment. It ensures reproducibility and provides transparency into how threat-detection models evolve.
3. Security & Threat Intelligence
MITRE ATT&CK Framework
An essential foundation for mapping adversary tactics, techniques, and procedures (TTPs). Integrating MITRE ATT&CK helps the platform contextualize alerts, classify threats, and generate actionable security insights.
OpenCTI
OpenCTI (Open Cyber Threat Intelligence) centralizes threat intelligence from multiple sources. It enriches detection pipelines with real-time indicators of compromise (IOCs), threat actor profiles, campaigns, and vulnerability data.
Commercial Threat Intelligence APIs
Integrations with commercial feeds, such as Recorded Future, CrowdStrike, or VirusTotal, provide high-fidelity intel to boost detection accuracy. These APIs offer insights on malicious domains, hashes, IP reputation, malware behavior, and emerging global threats.
4. Explainability & Monitoring
SHAP (SHapley Additive exPlanations)
SHAP helps security analysts understand why a model flagged a particular event as suspicious. It provides interpretable, feature-level insights that build trust and support regulatory compliance.
LIME (Local Interpretable Model-Agnostic Explanations)
LIME supplements explainable AI by producing human-readable explanations for individual model predictions. This is critical for auditing detection decisions and making AI outputs transparent to SOC teams.
Prometheus / Grafana
Prometheus captures system metrics, model performance indicators, and behavioral drift signals. Grafana visualizes these metrics through real-time dashboards, enabling proactive monitoring of the entire threat-detection ecosystem.
5. Infrastructure & Deployment
Kubernetes
Kubernetes orchestrates containerized services and machine learning workloads across distributed environments. It ensures scalability, high availability, automated rollouts, and self-healing for the detection services.
Docker
Docker standardizes the runtime environment for machine learning models, data pipelines, and microservices. Containerization ensures portability across cloud, hybrid, and on-premise deployments.
AWS / Azure / GCP
Cloud platforms provide the compute, storage, networking, and managed AI services needed to operate at enterprise scale. They offer serverless pipelines, GPU instances, managed Kubernetes clusters, and advanced security toolsets for rapid, global deployment.
Top 5 AI Threat Detection Platforms in the USA
We took a deep look at the current security landscape, and we found several AI threat detection platforms in the USA that truly stand out. Each one brings unique technical strengths that could support different defensive needs..
1. CrowdStrike Falcon
CrowdStrike Falcon is an AI-native cybersecurity platform that uses behavioral analytics and machine learning models to detect and stop threats across endpoints, cloud workloads, identities, and data. It continuously analyzes billions of events in real time and identifies anomalies that suggest malicious activity.
2. SentinelOne Singularity
SentinelOne’s Singularity platform delivers autonomous endpoint protection by applying AI models directly on devices to detect, block, and remediate threats without human intervention. It correlates behavioral signals across the environment to identify malware, fileless attacks, and lateral movement.
3. Vectra AI
Vectra AI focuses on network and identity threat detection, using machine learning to analyze traffic patterns and user behavior across cloud, SaaS, and on-premises networks. It identifies attacker tactics, such as privilege escalation, command-and-control activity, and lateral movement, in real time.
4. Darktrace
Darktrace uses self-learning AI to build a baseline understanding of normal activity within an organization and then autonomously detects anomalies that may indicate cyber threats. It monitors networks, email, cloud workloads, and IoT devices and adapts to evolving environments.
5. Anomali
Anomali combines AI-driven analytics with global threat intelligence feeds to detect hidden or emerging threats across enterprise environments. It correlates large volumes of logs, telemetry, and intelligence sources to uncover suspicious patterns that traditional tools overlook.
Conclusion
AI threat detection platforms are quickly becoming the backbone of modern cybersecurity because they combine behavioral intelligence with explainable AI and automated response, enabling teams to shift from reacting to threats to actively outmaneuvering them. With the right technical stack and an implementation partner capable of building at scale, an enterprise can launch a platform that delivers reliable protection, clear decision logic, and long-term value without adding unnecessary complexity.
Looking to Develop an AI Threat Detection Platform?
IdeaUsher can guide you through every stage of building an AI threat detection platform by developing a robust architecture that aligns with your data and security goals. Our team also develops models that learn from real behavior and can respond quickly when patterns shift.
Our team of ex-MAANG/FAANG engineers brings over 500,000+ hours of coding excellence to your security stack. We don’t just integrate AI, we engineer intelligent, adaptive systems that:
- Detect the unknown using behavioral AI, not just outdated signatures
- Correlate threats across clouds, networks, and identities in real time
- Automate response to shrink threat lifecycle from days to minutes
- Explain every alert so your team trusts and acts faster
Check out our latest projects to see how we’ve helped companies like yours transform security from a cost center into a competitive advantage.
Work with Ex-MAANG developers to build next-gen apps schedule your consultation now
FAQs
A1: AI threat detection platforms leverage behavioral analysis and predictive modeling to surface threats that a rules-based SIEM would often miss, enabling the system to respond to evolving attack patterns rather than waiting for a known event to trigger an alert.
A2: Yes, they can, because the platform evaluates patterns that drift from established baselines, allowing it to flag activity that does not match any known signature while still keeping the signal accurate enough for rapid investigation.
A3: Explainability should be a core requirement because security teams need to understand why a model made a decision, and this clarity can reduce false positives and help analysts respond with greater confidence during high-pressure events.
A4: Most projects run for four to nine months since the timeline depends on how many data sources must be integrated and how deep the automated response layer will go, and this range usually gives teams space to test the system under real workloads.