Cyber threats no longer announce themselves in obvious ways, and they often slip in quietly until the impact is already visible. Security teams feel constant pressure because alerts pile up faster than anyone can review, and traditional tools rarely provide the clarity needed to act with confidence. Attackers now use automation and scale to move faster than legacy systems can. An AI engine like CrowdStrike changes this dynamic by replacing static rules with adaptive intelligence that learns from every interaction and supports capabilities like continuous endpoint monitoring and identity threat protection.
It analyzes behavior across devices, uses cloud scale to correlate millions of signals, and applies features such as real-time threat scoring to build context that actually matters. This allows the system to identify threats as they form rather than after they succeed.
We’ve built many AI-driven cybersecurity and threat intelligence solutions, powered by behavioral AI systems and cloud-native security architectures. As we have this expertise, we’re sharing this blog to discuss the steps to create an AI engine like CrowdStrike. Let’s start!
Key Market Takeaways for AI Cybersecurity Platforms
According to GrandView Research, the AI-driven cybersecurity market is expanding rapidly as organizations face increasing volumes of complex cyber threats. Valued at a little over USD 25 billion in 2024, it is on track to reach nearly USD 94 billion by 2030, supported by a 24.4% CAGR and the growing need to secure cloud, remote work, and OT environments with adaptive, autonomous tools.
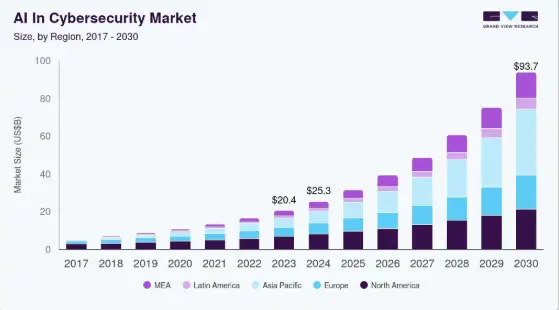
Source: GrandView Research
Platforms such as CrowdStrike Falcon and Darktrace demonstrate how AI is reshaping security operations. CrowdStrike combines endpoint, identity, and cloud workload protection with large-scale behavioral analytics and natural-language assistants to speed investigations and automate routine tasks.
Darktrace uses self-learning AI to model normal behavior across digital environments and contain both known and unknown threats within seconds.
Partnerships are amplifying this momentum. Darktrace’s integrations with Microsoft and AWS, supported by industry recognitions and marketplace alignment, make it easier for enterprises to embed autonomous detection and response into their existing cloud ecosystems and strengthen overall resilience.

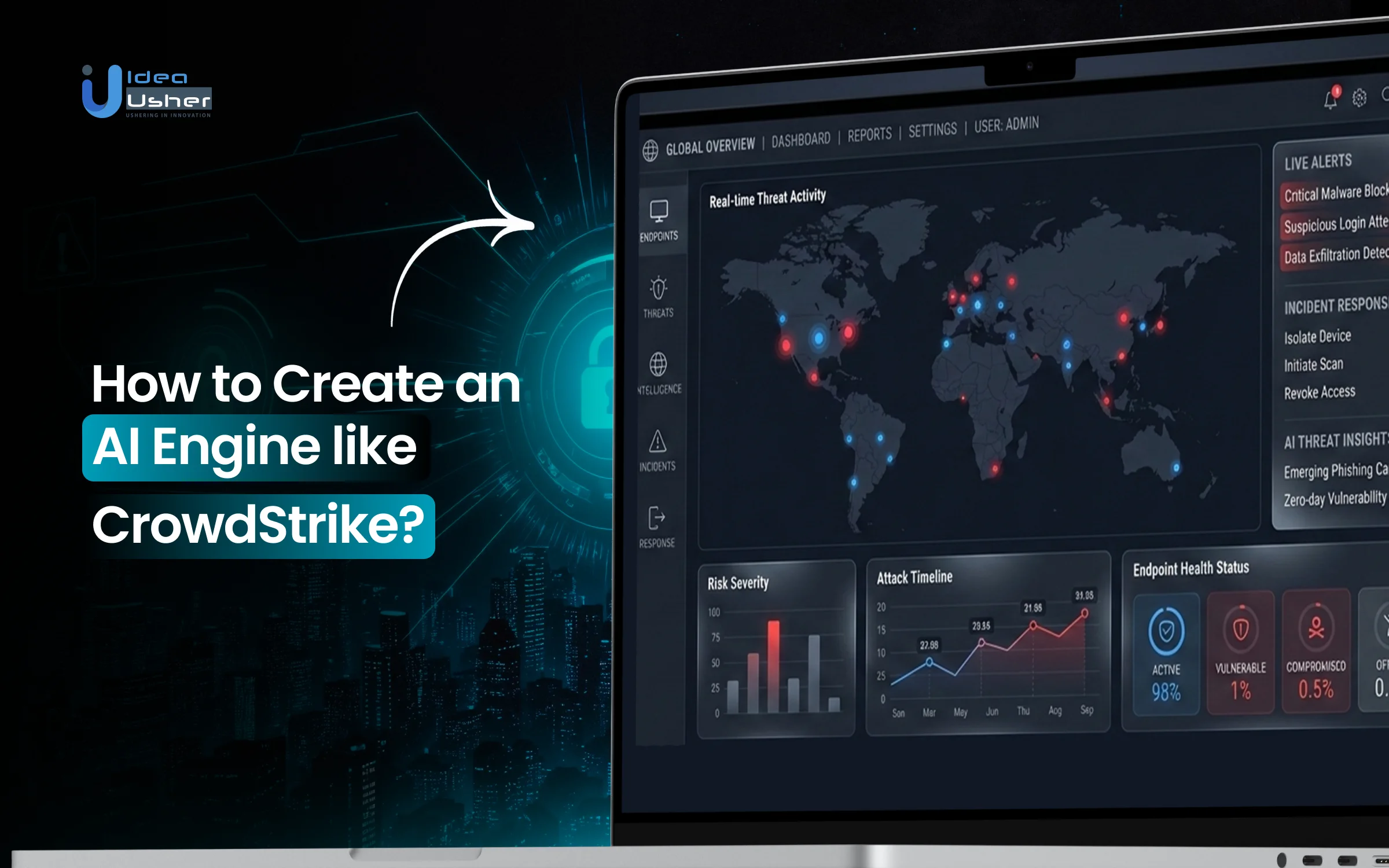
What is the CrowdStrike Platform?
The CrowdStrike Falcon platform is an AI-native cybersecurity solution that unifies endpoint protection, detection, response, and threat intelligence across devices, identities, cloud workloads, and data through a single lightweight agent and cloud console. It stops breaches by leveraging real-time telemetry, machine learning, and crowdsourced threat data from millions of endpoints.
Here are some of its standout features,
Next Gen Antivirus
Falcon’s antivirus engine focuses on behaviour rather than signatures, enabling it to detect ransomware, malware, and zero-day activity as soon as they begin. It deploys quickly across an environment and provides strong protection without slowing down devices.
Device Control
This feature helps organisations manage how external devices are used by monitoring USB drives, SD cards, and similar hardware. It allows policy-based restrictions that reduce the risk of accidental data leaks or intentional data theft.
Mobile Device Protection
Falcon extends its protection to Android and iOS by analysing device behaviour and blocking attempts to access corporate data in unsafe ways. It gives teams a consistent layer of security across both mobile and traditional endpoints.
Firewall Management
Centralised firewall controls let security teams push and update host firewall rules from one console. This ensures that all endpoints adhere to the same policies and reduces gaps that attackers could exploit.
Endpoint Detection and Response
Falcon EDR provides real-time visibility into device activity, highlights suspicious activity, and can isolate a compromised system when needed. It helps analysts investigate faster and contain threats before they spread.
Threat Intelligence and Hunting
This module provides global insights into attacker tactics and supports in-depth investigations that uncover subtle or hidden intrusions. It enables teams to hunt rather than wait for alerts proactively.
Identity Protection
Identity protection focuses on user accounts by monitoring logins, access patterns, and privilege escalations in real time. It quickly flags signs of compromise and helps stop attackers from moving laterally through the organisation.
How Does the CrowdStrike Platform Work?
The platform works by placing a lightweight sensor on each system, which streams rich security signals to a cloud engine that processes events at a massive scale. That engine maps activity in real time and may uncover patterns that reveal threats long before they become visible to traditional tools.
From there, the platform can guide or automate a response that acts quickly and steadily to contain the risk.
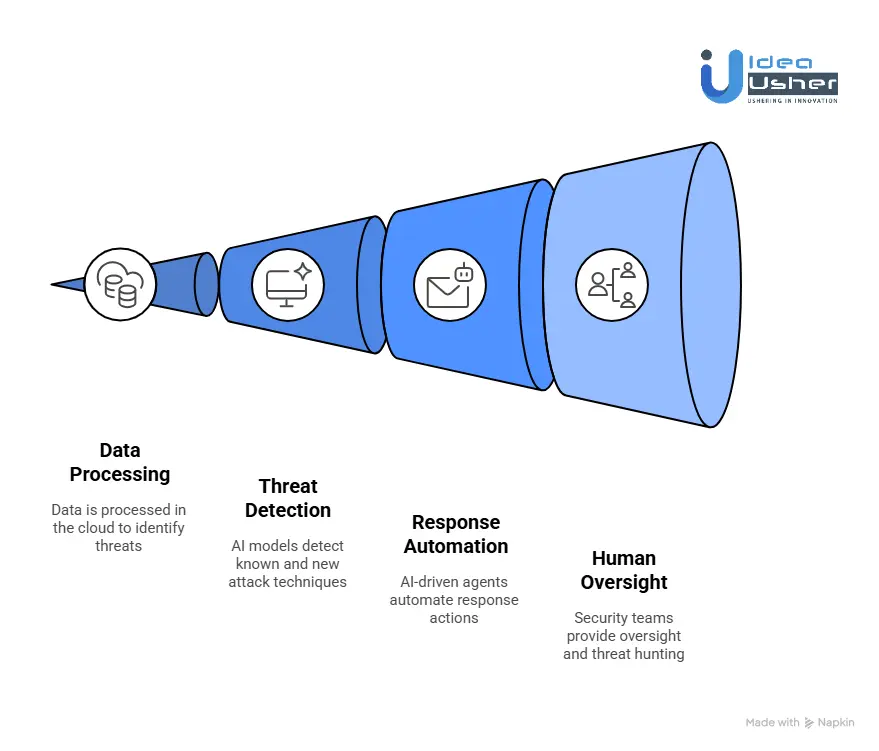
1. The Single Lightweight Agent
At the heart of the Falcon platform is a small, efficient agent that runs on endpoints, servers, and mobile devices without slowing them down. This sensor collects detailed telemetry on processes, network activity, identity events, and cloud workloads, then securely sends it to the Falcon cloud.
Because one agent handles what would normally require several tools, organisations avoid performance issues and remove the complexity of juggling multiple security applications.
2. The CrowdStrike Security Cloud
All sensor data flows into the CrowdStrike Security Cloud, which serves as the platform’s central intelligence system. Its core is the Threat Graph, a real-time engine that processes massive volumes of events every week and continuously links them to reveal attacker behaviour or unusual relationships across endpoints, identities, and cloud workloads.
The platform’s AI models train on this expanding dataset along with insights from CrowdStrike’s threat intelligence team, allowing the system to recognise both familiar malware and subtle, never-before-seen attack techniques.
3. The Platform’s Core Functions
CrowdStrike’s unified design enables every security module to share context instantly, so detection, investigation, and response operate from a single understanding of what is happening across the environment.
| Platform Function | How It Works on the Falcon Platform |
| Endpoint Protection (EPP/EDR) | The endpoint agent blocks malware and ransomware in real time and streams detailed activity data to the cloud. Analysts and automated systems can explore the Threat Graph to investigate issues with full visibility. |
| Next-Gen SIEM | Logs and security data from across the organisation flow into Falcon, where AI evaluates them in relation to the Threat Graph to surface real threats instead of raw log noise, shifting SIEM from storage to active prevention. |
| Cloud Security (CNAPP) | Cloud workloads are protected through agent-based runtime security, while cloud configurations and identities are scanned without an agent. All cloud risk is viewed and managed from the same console for consistent oversight. |
| Identity Protection | Human and machine identities are monitored for unusual behaviour, and alerts are correlated with endpoint and cloud activity to stop attacks that rely on compromised credentials. |
4. From Detection to Autonomous Action
CrowdStrike’s AI engine has evolved from pure analysis into active defense.
Charlotte AI
A conversational assistant that lets security teams investigate incidents with natural language queries and generate reports instantly, removing repetitive tasks and shortening response times.
Charlotte Agentic SOAR
AI-driven agents that can carry out multi-step response workflows such as isolating systems or disabling compromised accounts. These actions still operate under human oversight but scale incident response far beyond manual capacity.
5. The Human Element
Falcon is strengthened by dedicated security teams operating within the platform.
- Falcon Complete (Managed Detection and Response): CrowdStrike’s specialists monitor environments around the clock, investigate alerts, and take direct action to stop threats, supported by a breach prevention guarantee.
- Falcon OverWatch: A global threat hunting team that searches for stealthy activity that automated systems might miss, ensuring even advanced intrusions are found early.
What is the Business Model of the CrowdStrike Platform?
CrowdStrike runs its security platform as a cloud-delivered SaaS offering, meaning customers subscribe to the Falcon platform rather than buying on-premises hardware or software. Falcon’s strength lies in its AI-driven architecture and behavioural analytics, providing enterprises with real-time protection, threat intelligence, and response capabilities through a single, scalable service.
Subscription Revenue
Most of CrowdStrike’s revenue comes from subscriptions to the Falcon platform, where customers select modules such as endpoint protection, identity security, cloud workload defence, and threat intelligence. In FY2025, this stream generated about $3.76 billion, making it the core of the company’s financial engine.
Professional Services
CrowdStrike also offers hands-on security services, including incident response, breach support, and proactive assessments. These services generated approximately $192 million in FY2025 and complement the subscription business by providing customers with direct access to expert support.
Financial Performance
CrowdStrike’s FY2025 results show strong momentum across the board.
- Total Revenue: $3.95 billion, up 29% from the previous year
- Annual Recurring Revenue (ARR): $4.24 billion, a 23% year-over-year increase
- Operating Cash Flow: $1.38 billion, with free cash flow at $1.07 billion
- Subscription Gross Margin: 80% on a non-GAAP basis, reflecting the efficiency of its cloud delivery model.
- Customer Retention: 97% gross retention in Q4 FY2025, showing that customers stay and continue expanding their use of the platform
Funding History and Valuation
Since launching in 2011, CrowdStrike has raised several funding rounds to fuel growth. A major milestone came in 2018 with a $200 million Series F, valuing the company at more than $3 billion. The company went public in June 2019, raising $612 million at a market cap of around $6.5 billion.
As of January 31, 2025, CrowdStrike reported $4.32 billion in cash and equivalents, giving it significant flexibility for acquisitions and platform expansion.
Future Projections
CrowdStrike aims to reach $10 billion in ARR by FY2031, a target driven by ongoing demand for cloud native security and continued expansion of Falcon modules such as Next-Gen SIEM, cloud security, and identity protection.
The company is also investing heavily in AI-native operations and consolidation of security tools, positioning itself as a central platform for modern SOC teams.

How to Build an AI Engine Like CrowdStrike?
Building an AI engine like CrowdStrike starts with a clear focus on behavior, so you can detect attacks before signatures exist. You would design a unified telemetry layer that collects high-fidelity signals and feeds scalable models that reason over sequences in near-real time. We have built numerous AI engines, including CrowdStrike, for our clients. Here is how we do it.
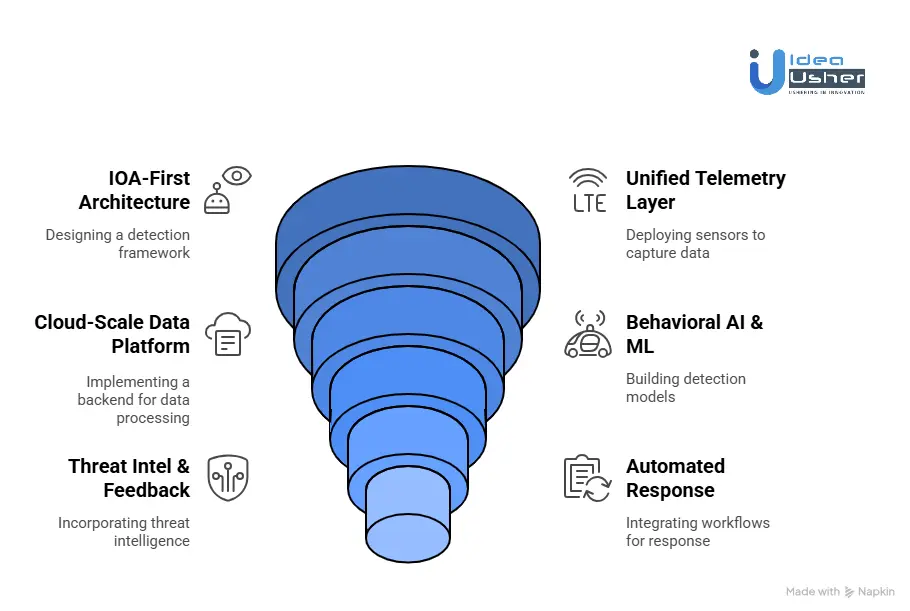
1. IOA-First Architecture
We begin by architecting an IOA-driven detection framework that focuses on attacker intent, defines behavioral models aligned with the client’s risk profile, maps detections to MITRE ATT&CK, and establishes real-time correlation logic to uncover attacks before they escalate.
2. Unified Telemetry Layer
Next, we deploy lightweight endpoint and cloud sensors that capture rich behavioral telemetry across devices and workloads, using kernel- and API-level hooks and smart local filtering to collect only the most relevant, high-signal data for analysis.
3. Cloud-Scale Data Platform
We then implement a cloud-scale backend capable of ingesting telemetry in real time, organizing it in a graph-based architecture that reveals relationships between entities, and enabling rapid indexing and search so analysts and automated systems can investigate threats instantly.
4. Behavioral AI & ML
Our team builds sequence-based, context-aware detection models tailored to client environments, integrates anomaly and intent detection to detect unknown threats, and maintains continuous retraining pipelines to keep models aligned with emerging attacker techniques.
5. Threat Intel & Feedback
We incorporate both global and client-specific threat intelligence, feed insights into our IOA engineering workflows, and apply structured human-in-the-loop validation to refine detections, ensuring our models remain accurate, actionable, and aligned with real-world attacks.
6. Automated Response
Finally, we integrate advanced SOAR workflows and autonomous investigation agents that collect evidence, analyze patterns, and initiate responses, while preserving human oversight to deliver a safe, reliable automated defense at scale.
Why 95% People Trust AI-Powered Cybersecurity?
According to recent reports, 95% of users agree that AI-powered cybersecurity improves the speed and effectiveness of prevention, detection, response, and recovery. You might notice this because AI can process threats faster than any human team, and it will often reveal risks that you would not catch on your own. This is why many experts will continue to rely on AI since it consistently strengthens security in real time.
1. Speed and Scale
Modern organizations generate overwhelming amounts of security data, including logs, identity events, and network traffic. No analyst could manually process this information fast enough to catch threats in time.
AI systems can analyze these streams instantly. They identify suspicious patterns in real time, reducing attacker dwell time from days or weeks to minutes. This speed is one of the clearest reasons why security professionals trust AI, since faster detection directly limits the damage an attacker can cause.
2. From Reactive to Proactive
Traditional defenses often alerted teams only after harm was already done. AI changes that approach by identifying threats earlier in their lifecycle.
- Behavior-based detection learns what normal activity looks like for users, devices, and systems. When behavior shifts in a subtle or unusual way, AI flags it long before a breach becomes visible.
- Automated threat hunting searches for weak indicators of compromise across the entire environment. This gives analysts insight they could not uncover manually at scale.
This proactive stance provides a stronger, more resilient security posture.
3. Reducing Alert Fatigue
Security teams once faced thousands of low-value alerts each day. Important warnings were often buried under noise, leading to missed threats and constant overload.
AI helps by performing the work that consumes most of an analyst’s time:
- It prioritizes alerts that require immediate attention.
- It correlates scattered activity into clear, meaningful incidents.
- It filters out false positives that previously wasted valuable hours.
The result is an effective partnership between people and technology. AI handles large-scale data processing while analysts concentrate on investigations and strategic defense. Many teams recover more than half of their time for high-impact work.
4. Continuous Learning
Cyber attackers evolve constantly. AI’s ability to learn continuously makes it well-suited for this environment.
- AI models use global threat intelligence to update quickly as new attack techniques emerge worldwide.
- Because AI focuses on behaviors rather than signatures, it can identify zero-day threats and entirely new attack methods that legacy tools would never recognize.
This type of adaptive defense enables organizations to stay ahead of emerging risks rather than react after the fact.
What are the Monetary Benefits of AI Engines like CrowdStrike?
When companies evaluate platforms such as CrowdStrike, the conversation often starts with technology. However, the real impact shows up on the financial side. Modern AI-driven security platforms deliver measurable ROI by reducing breach-related losses, lowering security operations costs, and improving a company’s risk profile with insurers.
For a mid-sized organization with around 1,000 employees, the three-year financial gain typically ranges from $3.2 million to $5.7 million.
1. Breach Cost Avoidance
The largest economic advantage comes from avoiding security incidents that would otherwise cause direct financial losses, legal exposure, and long-term business disruption.
Understanding Breach Cost Exposure
IBM’s 2023 research estimates the global average cost of a data breach at $4.45 million, with sectors such as healthcare and finance trending 40 to 60 percent above this figure.
Key cost components include:
- Detection and escalation: ~$1.58M (forensics, investigation, internal escalation)
- Lost business: ~$1.30M (customer churn, lost revenue, downtime)
- Notification and legal: ~$0.74M (regulatory compliance, legal defense)
- Post-breach recovery: ~$0.83M (restoration work, customer support, credit monitoring)
How AI Platforms Shift Breach Probability and Expected Loss
AI security engines significantly reduce the likelihood that an intrusion turns into a costly breach.
| Security Posture | Annual Breach Probability | Expected Annual Loss (based on $4.45M breach) |
| Traditional Tools | ~8.7% | ~$387,150 |
| AI Security Engine | Approx. 2–4% | ~$88,900–$195,800 |
Annual cost avoided: $191,350 to $298,250
Three-year impact for a 1,000-employee company: ~$574,000 to $895,000 in avoided breach costs
2. Operational Efficiency and Labor Savings
AI engines reduce manual labor required for threat analysis, alert triage, and incident response. This directly cuts security operations costs and helps existing teams cover more ground without adding headcount.
SOC Productivity Improvements
| Task | Traditional Approach | With AI | Time Saved | Annual Financial Impact (per analyst, $120K salary) |
| Threat investigation | 60–90 minutes per alert | 10–15 minutes | 75–85% | ~$68,000 |
| False-positive review | ~50% of alerts invalid | 80–90% reduction | ~80% | ~$42,000 |
| Incident containment | 4–6 hours manual | 15–30 minutes automated | 85–90% | ~$55,000 per incident |
Combined Efficiency Impact
For a five-person SOC investigating ~50 high-priority alerts per week:
- Traditional annual labor cost: ~$600,000
- AI-driven manual effort reduction: ~40–60%
- Annual labor savings: $240,000 to $360,000
- Three-year savings: $720,000 to $1,080,000
These savings can be redeployed into strategic initiatives rather than routine triage.
3. Cyber Insurance Savings and Risk Profile Improvement
Cyber insurance premiums have surged in recent years. Insurers now heavily factor in a company’s security posture, tooling, and incident response maturity. AI platforms often meet or exceed the security controls required by carriers.
Insurance Impact Factors
| Factor | Without AI Platform | With AI Platform | Premium Impact |
| EDR/XDR capability | May fall short of carrier requirements | Meets and exceeds modern standards | 15–25% reduction |
| MFA coverage | Partial or inconsistent | Fully enforced | 10–15% reduction |
| 24/7 monitoring | Limited | Fully supported | 10–20% reduction |
| Overall risk score | Higher | Significantly reduced | 5–10% reduction |
Premium Reduction Estimate
- Typical cyber policy for a midsize business: ~$250,000 per year
- Premium reduction with AI tooling: 25–40%
- Annual savings: $62,500 to $100,000
- Three-year savings: $187,500 to $300,000
4. Industry Validation and Independent ROI Studies
Independent economic analyses have consistently shown that AI-driven security platforms generate strong financial returns.
SentinelOne Business Value Report (2023)
Organizations using SentinelOne saw major efficiency gains, with threat investigations completed up to 90% faster and manual security tasks reduced by about 80%. These improvements contributed to a strong three-year ROI of roughly 197% across surveyed customers.
Palo Alto Networks Cortex XDR Validation
Evaluations of Cortex XDR showed faster overall security operations, including a 51% improvement in threat detection speed and a 44% reduction in response time. Combined with a 70% boost in SOC productivity, the platform delivered clear operational value.
Forrester TEI on Microsoft Defender
Microsoft Defender helped reduce SOC staffing needs by about 25% and cut incident response times by half. Over three years, these efficiencies translated into a risk-adjusted net present value of approximately $5.34 million.
Common Challenges to Create an AI Engine like CrowdStrike
Through our work with many organizations, we’ve seen that the hard part isn’t building an AI model but turning it into a system that runs nonstop, scales globally, stays fast on endpoints, and earns team trust. Massive datasets, false positives, performance constraints, and reliable automation are what differentiate demos from real production systems.
1. Challenge #1: Handling Massive Data Volumes
Security platforms don’t deal with small datasets. They ingest enormous streams of telemetry from thousands of endpoints every hour. Traditional databases stall under this pressure. Batch processing introduces delays that attackers can exploit. If you can’t process data in real time, you can’t defend modern environments.
Our Battle-Tested Solutions
Scalable Cloud-Native Architecture
We design platforms that expand automatically without intervention.
- Multi-region deployments absorb regional failures with zero data loss
- Autoscaling pipelines grow with traffic instead of collapsing under it
- Serverless components handle unpredictable surges during active attacks
A practical insight. Managing Kafka or Kinesis with automatically scaling partitions is essential. Manual tuning might work in a lab, but it collapses instantly in production.
Stream-First Data Design
Security decisions must be made while data is moving. We use a dual-path approach.
- Hot path for sub-second prevention decisions
- Warm path for deeper analysis within a few seconds
Storage matters more than most teams realize. Columnar formats like Parquet or ORC with ZSTD compression make large-scale threat hunting dramatically faster later in the pipeline.
Challenge #2: Reducing False Positives
Early-stage AI engines often flag everything suspicious. SOC teams quickly drown in alerts and start ignoring them. False positives don’t just waste time. They create openings for real threats to slip through unnoticed.
Our Precision Engineering Approach
High-Fidelity Indicators of Attack (IOAs)
We go beyond anomalies to detect the intent behind behavior.
For example:
- A file download alone isn’t suspicious.
- A file download followed by PowerShell execution that disables logging is a clear attack chain.
Every rule maps cleanly to MITRE ATT&CK so alerts are specific and actionable instead of vague.
Confidence-Based Response Logic
We design a tiered system that aligns responses with certainty.
- Above 95 percent confidence: Fully autonomous prevention
- Between 80 and 95 percent: Alert plus recommended action
- Below 80 percent: Logged for context only
One of our most effective innovations is time-based decay. Something that appears dangerous at first glance may become harmless once more context is available. The system adapts instead of overreacting.
Challenge #3: Maintaining Endpoint Performance
A security agent that slows down devices becomes an enemy to users. High CPU usage leads to complaints. Complaints lead to uninstallations. Once that happens, security coverage disappears entirely.
Our Performance-Obsessed Engineering
Smart Sensor Engineering
We focus on efficiency at the operating system level.
- Native drivers built in C or Rust to avoid heavy user-space polling
- Intelligent sampling for event-heavy systems without losing forensic value
- Tight memory budgets that keep the sensor under 50 MB even on busy machines
Success is measured by silence. If users never notice the agent, we’ve done our job.
Cloud Offloading Strategies
The endpoint determines what to send.
- Small local ML models filter routine events before they ever leave the device.
- Network impact drops sharply thanks to batching, compression, and differential updates.
The result is an agent that delivers full visibility without slowing down a single user.

Tools & APIs to Create an AI Engine like CrowdStrike
Building an AI-powered security platform with capabilities similar to CrowdStrike requires far more than strong algorithms. It demands a well-designed ecosystem of tools, frameworks, and cloud-native infrastructure that work together seamlessly. No single technology achieves this alone.
1. Data Streaming and Processing
Real-Time Ingestion Layer
Apache Kafka and AWS Kinesis
These services act as high-speed highways for security telemetry. When millions of events are flowing in every second from global endpoints, the ingestion layer must be dependable, scalable, and fast. Kafka is ideal for high-throughput, fault-tolerant streaming across distributed systems. Kinesis offers a straightforward AWS-native option with smooth integration into the broader cloud ecosystem.
Stream Processing Engines
Apache Flink and Spark Streaming
Raw telemetry becomes valuable only when the platform can interpret it the moment it arrives. Stream processors sift through massive volumes of data in motion, highlight anomalies, filter noise, and generate meaningful signals before the data is even written to storage.
2. AI and Machine Learning
Core ML Frameworks
Python, PyTorch, TensorFlow
Python remains the primary language for security data science. PyTorch is ideal for rapid experimentation and research-focused model development. TensorFlow excels in production environments where stability, serving capabilities, and large-scale performance are essential.
Pro tip: TensorFlow Extended is a powerful choice for building automated end-to-end ML pipelines, including data validation, retraining, serving infrastructure, and monitoring.
Specialized Security ML
Graph Machine Learning Frameworks
Security data is not just a collection of events. It is an interconnected web of processes, network connections, user sessions, and system behaviors. Graph ML is uniquely suited for capturing these relationships and identifying patterns that traditional models overlook.
Key application: Use graph models to learn “normal” behavioral structures within environments. When a process unexpectedly spawns an unfamiliar child or establishes an unusual outbound connection, the model detects deviation in the relationship graph rather than just the event itself. This is crucial for identifying lateral movement and stealthy multi-stage attacks.
2. Threat Intelligence
Adversary Framework
MITRE ATT&CK
This framework provides a comprehensive library of adversarial behaviors. It becomes the foundation for detection engineering and model training. Designing your detections around ATT&CK’s Tactics, Techniques, and Procedures ensures broad and consistent defensive coverage.
Implementation strategy: Encode ATT&CK techniques as model features. When your detection engine recognizes activity related to “Credential Dumping, it should understand how that fits into a broader narrative of lateral movement or privilege escalation.
Continuous Intelligence Integration
Threat Intelligence Feeds and APIs
AI models degrade without constant exposure to new indicators, malware families, and attacker playbooks. Threat feeds from OTX, Abuse.ch, and commercial intelligence providers provide the platform with fresh IOCs, behavioral signatures, and emerging threat-actor insights.
Architecture consideration: Build a threat intelligence platform (TIP) layer to aggregate, normalize, and enrich raw intel before it reaches your detection engines. This ensures clean, actionable intelligence flows into automated and human workflows.
3. Cloud and Infrastructure
Cloud Platforms
AWS, Azure, GCP
CrowdStrike succeeded by embracing cloud-native design from day one. Choose a primary cloud provider based on your organization’s skills but architect with multi-cloud flexibility in mind.
Essential services:
- Object storage (S3 and equivalents) for long-term telemetry archives
- Managed Kubernetes clusters (EKS, GKE, AKS) for microservices
- Accelerator instances for high-performance ML workloads
Container Orchestration
Kubernetes and Docker
Modern AI engines are composed of hundreds of modular services. Kubernetes manages these components, ensuring automatic scaling, health checks, service discovery, fault recovery, and smooth deployment of new models.
Critical for ML Ops:
Use Kubernetes to support canary releases for ML models. Route a small portion of traffic to new versions, validate stability and accuracy, then graduate them to full production.
4. Security and Observability
Telemetry Standardization
OpenTelemetry
Before monitoring customers, the platform must monitor itself. OpenTelemetry standardizes the collection of traces, metrics, and logs from every service within your ecosystem. This visibility is vital for tracking model performance, spotting pipeline bottlenecks, and identifying drift.
Key insight: Apply the same behavioral monitoring you use on endpoints to your own ML systems. This ensures long-term reliability and transparency.
SOC Integration
SIEM and Analyst Workflows
Even the strongest AI engine must fit into the workflow of human analysts. Integrate with SIEM platforms such as Splunk, Microsoft Sentinel, and IBM QRadar using their APIs and standard formats like CEF or OpenDXL.
Do not overlook: Build two-way integration. Analysts must be able to submit feedback on false positives or false negatives. This feedback should automatically influence future model tuning and retraining.
Conclusion
Building an AI engine like CrowdStrike is really about creating a real-time security platform that blends intelligence-driven models with data flows that adapt under pressure. When you approach it this way, you see how enterprises could launch products that stand out and hold long-term revenue value. With the right technical partner, this goal becomes far more achievable, and you gain a path to deploy a platform that responds quickly and learns continuously.
Looking to Develop an AI Engine like CrowdStrike?
IdeaUsher can guide you through the architecture of an AI security engine by helping you design scalable detection pipelines and efficient response workflows. Their team can also build modular machine learning systems that will adapt quickly as threats evolve.
With over 500,000 hours of coding experience, our team of ex-MAANG and FAANG developers deconstructs the core of systems like CrowdStrike.
- The Single Lightweight Sensor: We build unified, low-impact agents that collect forensic telemetry without slowing systems down.
- The Real-Time Threat Graph: We architect cloud-native data lakes that process billions of events, turning raw data into actionable intelligence.
- Behavioral AI Over Static Detection: We train models on Indicators of Attack (IOA), not just known threats, to stop zero-day and fileless attacks.
- Human-in-the-Loop MLOps: We design a continuous feedback loop in which threat intelligence continually refines your AI, keeping it ahead of adversaries.
Check out our latest projects to see how we deliver enterprise-grade, intelligent systems.
Work with Ex-MAANG developers to build next-gen apps schedule your consultation now
FAQs
A1: Yes, it is possible: an enterprise can design a modular detection pipeline that learns from endpoint signals in real time and refines threat models as new behaviors emerge. You would need a robust data pipeline and a team that can build models that adapt quickly, enabling the engine to act before an attack spreads.
A2: An MVP might take about six to nine months because you must define the telemetry model, and you must validate threat detection logic in controlled environments before you release anything widely. After the MVP launch, the system will continue to evolve as you provide more behavioral data and tune response actions.
A3: It is not limited to large teams, as MSSPs and SaaS vendors can deploy a focused version that analyzes endpoint behavior and provides automated remediation. Smaller platform startups might also use this model, as it allows them to build a lean detection engine that scales gradually while still delivering strong value.
A4: A behavior-driven engine evaluates patterns as they unfold so it can respond autonomously, while older SIEM or EDR tools usually wait for log-based alerts that arrive too late. This shift means the system may predict lateral movement and stop it early, which gives defenders a far more proactive posture.